ITC 1.6 Quiz Module 1: Introduction to Cybersecurity Exam Answers 2025 Full 100%
ITC 1.6 Quiz Module 1: Introduction to Cybersecurity Exam Answers 2025 Full 100%
Cybersecurity is a critical field in today’s digital landscape, protecting systems, networks, and data from cyber threats. The Introduction to Cybersecurity (ITC) Module 1 Exam Quiz Answers provides foundational knowledge on key cybersecurity concepts, including cyber threats, attack vectors, risk management, and best practices for securing information. This module is essential for students and IT professionals looking to build a strong cybersecurity foundation. Below, we provide the full 100% correct answers for the ITC 1.6 Quiz Module 1 (2025 edition) to help you review and understand the key concepts covered in this exam.
-
Cybersecurity is the ongoing effort to protect individuals, organizations and governments from digital attacks by protecting networked systems and data from unauthorized use or harm.
What level of cyber protection does each of the following factors require?
- Your online identity ==> Personal
- A customer database ==> Organizational
- Economic stabilty ==> Government
Explanation & Hint: Your online identity:
- Personal: Your personal online identity should be protected at a relatively high level. This includes using strong and unique passwords, enabling two-factor authentication (2FA) whenever possible, being cautious about sharing personal information online, and regularly monitoring your online accounts for any suspicious activities. Personal cybersecurity practices are essential to safeguard your digital identity.
A customer database:
- Organizational: Customer databases held by organizations should be protected at an organizational level. This entails implementing strong security measures, including encryption, access controls, regular security audits, and compliance with data protection regulations (e.g., GDPR or HIPAA). Organizations are responsible for safeguarding customer data and ensuring it is not exposed to unauthorized access or breaches.
Economic stability:
- Government: Economic stability, at both the national and international levels, requires a high level of cybersecurity protection. Governments are responsible for protecting critical infrastructure, financial systems, and economic stability. This protection involves implementing advanced cybersecurity measures, conducting cyber threat intelligence, and establishing international cooperation to address cyber threats that could disrupt economic stability.
In summary, the required level of cyber protection varies based on the nature of the factor being protected. Personal online identities, customer databases, and economic stability systems each have distinct security needs, and the level of protection should be tailored accordingly.
-
An individual user profile on a social network site is an example of an Online identity.
Explanation & Hint: An individual user profile on a social network site is an example of an online identity. It represents the digital presence and persona of the user within the context of the social network, and it is distinct from their offline or real-world identity.
-
Your neighbor tells you that they don’t have an online identity. They have no social media accounts and only use the Internet to browse. Is your neighbor right?
- Yes
- No
Explanation & Hint: No, your neighbor is not entirely right. Even if they only use the internet to browse and do not have social media accounts, they still have a minimal online identity due to the digital traces left by their online activities.
-
Which of the following pieces of information would be classified as personal data?
Select three correct answers
- Social security number
- Driver license number
- Date and place of birth
- Job title
- IP address
Explanation & Hint: The following three pieces of information would be classified as personal data:
- Social security number: Social security numbers are considered highly sensitive personal information in many countries and are used for identification and government purposes.
- Driver license number: Like social security numbers, driver license numbers are unique identifiers issued by government authorities and are classified as personal data.
- Date and place of birth: Information about a person’s date and place of birth is considered personal data, as it can be used to identify an individual and is often used for identity verification.
Job title and IP address are typically not considered personal data on their own, as they do not directly identify an individual. However, the classification of IP addresses may vary based on regional data protection regulations and the context in which they are used.
-
What are the foundational principles for protecting information systems as outlined in the McCumber Cube?
Choose three correct answers
- Access
- Integrity
- Scalability
- Availability
- Confidentiality
- Intervention
Explanation & Hint: The McCumber Cube is a model used to assess information security in terms of three dimensions: confidentiality, integrity, and availability (often referred to as the CIA triad). So, the three foundational principles for protecting information systems according to the McCumber Cube are:
Confidentiality: Protecting information from unauthorized access or disclosure to ensure that sensitive data remains confidential.
Integrity: Ensuring the accuracy and reliability of data and information, as well as protecting it from unauthorized alterations.
Availability: Ensuring that information and resources are available and accessible to authorized users when needed.
The other options (Access, Scalability, and Intervention) are not part of the McCumber Cube’s foundational principles but may be important considerations within the broader field of information security.
-
Which of the following methods can be used to ensure confidentiality of information?
Choose three correct answers
- Backup
- Version control
- Data encryption
- File permission settings
- Two-factor authentication
- Username ID and password
Explanation & Hint: To ensure the confidentiality of information, the following three methods can be used effectively:
- Data encryption: Data encryption involves converting information into a coded form that can only be read by someone who possesses the decryption key. It is a powerful technique to protect data from unauthorized access and maintain its confidentiality.
- Two-factor authentication (2FA): Two-factor authentication requires users to provide two different forms of authentication before they can access a system or account. This added layer of security enhances confidentiality by ensuring that only authorized individuals can access the information.
- Username ID and password: While not as strong as some other methods on their own, using a combination of a username ID and password is a common way to control access to information. However, for enhanced security, it’s often recommended to complement this with additional measures like 2FA or strong password policies.
These methods, when used appropriately and in combination where necessary, help maintain the confidentiality of sensitive information.
-
Why might internal security threats cause greater damage to an organization than external security threats?
- Internal users have better hacking skills
- Internal users have direct access to the infrastructure devices
- Internal users can access the organizational data without authentication
- Internal users can access the infrastructure devices through the Internet
Explanation & Hint: Among the options provided, the primary reason internal security threats might cause greater damage to an organization than external security threats is:
Internal users have direct access to the infrastructure devices: Internal users, such as employees or contractors, often have legitimate access to an organization’s infrastructure devices, systems, and data as part of their job responsibilities. This direct access can make it easier for them to carry out malicious activities, such as data theft, system sabotage, or unauthorized configuration changes, without the need to breach external security measures. As a result, the potential for causing significant damage is higher when someone with authorized access turns malicious.
The other options may also contribute to the severity of the threat, but they are not as central as having direct access to critical infrastructure devices. For example, internal users having better hacking skills or being able to access organizational data without authentication are concerning, but these factors alone do not necessarily lead to greater damage compared to having direct access to infrastructure devices. Additionally, accessing infrastructure devices through the Internet can be a concern, but it’s not exclusive to internal threats and can also apply to external threats.
-
Which of the following is a key motivation of a white hat attacker?
- Taking advantage of any vulnerability for illegal personal gain
- Fine tuning network devices to improve their performance and efficiency
- Studying operating systems of various platforms to develop a new system
- Discovering weaknesses of networks and systems to improve the security level of these systems
Explanation & Hint: The key motivation of a white hat attacker is:
Discovering weaknesses of networks and systems to improve the security level of these systems: White hat attackers, often referred to as ethical hackers or security professionals, engage in cybersecurity activities to identify vulnerabilities and weaknesses in networks and systems. Their goal is to help organizations improve their security by finding and fixing vulnerabilities before malicious hackers can exploit them. White hat attackers work with the consent and authorization of the system or network owner and have no intention of causing harm or personal gain from their actions. Their primary motivation is to enhance security and protect against potential threats.
-
Can you identify the cyber attacker type from the following descriptions?
- Make political statements in order to raise awareness about issues that are important to them ==> Hacktivists
- Gather intelligence or commit sabotage on specific goals on behalf of their government ==> State-sponsored attackers
- Use existing tools on the Internet to launch a cyber attack ==> Script kiddies
Explanation & Hint: “Make political statements in order to raise awareness about issues that are important to them”:
Hacktivists: Hacktivists are individuals or groups who engage in hacking activities to promote a political or social cause and raise awareness about issues important to them. They often target websites, social media accounts, or online platforms to make political statements or carry out cyber protests.
“Gather intelligence or commit sabotage on specific goals on behalf of their government”:State-sponsored attackers: State-sponsored attackers are cyber threat actors who operate on behalf of a government or government agency. They are typically tasked with gathering intelligence, conducting espionage, or carrying out cyberattacks to advance their nation’s interests or security goals.
“Use existing tools on the Internet to launch a cyber attack”:Script kiddies: Script kiddies are individuals with limited hacking skills who rely on pre-existing, often readily available, hacking tools and scripts to launch cyberattacks. They typically lack the deep technical knowledge and sophistication of more advanced hackers and may engage in hacking for personal amusement or minor mischief.
-
Can you identify why each of the following organizations might be interested in your online identity?
- Internet service providers ==> They may be legally required to share your online information with government surveillance agencies or authorities
- Advertisers ==> To monitor your online activities and send targeted ads your way
- Social media platforms ==> To gather information based on your online activity, which is then shared with or sold to advertisers for a profit
- Websites ==> To track your activities using cookies in order to provide a more personalized experience
Explanation & Hint: Internet service providers: They may be legally required to share your online information with government surveillance agencies or authorities. Internet service providers, in some cases, are subject to legal requirements to share user data for national security or law enforcement purposes.
Advertisers: To monitor your online activities and send targeted ads your way. Advertisers are interested in your online identity to collect data about your interests and preferences, allowing them to deliver personalized advertisements to you.
Social media platforms: To gather information based on your online activity, which is then shared with or sold to advertisers for a profit. Social media platforms often collect extensive data on user behavior and may share or sell this data to advertisers to support their advertising revenue model.
Websites: To track your activities using cookies in order to provide a more personalized experience. Many websites use cookies and other tracking technologies to understand how you interact with their content and provide a tailored browsing experience.
-
Which of the following methods is used to check the integrity of data?
- Backup
- Hashes or checksums
- Encryption
- Authentication
Explanation & Hint: The method used to check the integrity of data is:
Hashes or checksums: Hashes or checksums are used to verify the integrity of data. A hash function generates a fixed-length string of characters (the hash) from the original data. If the data is modified in any way, even a small change, the resulting hash will be different. By comparing the computed hash with the original hash (stored securely), you can detect whether the data has been tampered with or is still intact. This method is commonly used in data integrity checks and file verification processes.
-
Stuxnet malware was designed for which primary purpose?
- To hijack and take control of targeted computers
- To cause physical damage to equipment controlled by computers
- To cause serious harm to workers in a nuclear enrichment plant
-
Explanation & Hint: Stuxnet malware was designed to cause physical damage to equipment controlled by computers, specifically targeting industrial control systems used in nuclear enrichment facilities. It disrupted the operation of centrifuges by manipulating their speed, leading to physical damage while masking the malicious activity from monitoring systems.
-
Cyberwarfare is the use of technology to penetrate and attack another nation’s computer systems and networks in an effort to cause damage or disrupt services, such as shutting down a power grid.
-
Explanation & Hint: Cyberwarfare refers to the use of technology and cyber operations by one nation-state to attack another nation’s critical infrastructure, computer systems, or networks. The goal is often to cause disruption, damage, or gain a strategic advantage in conflicts. Examples include shutting down power grids, disrupting financial systems, or interfering with military communications. Cyberwarfare is typically state-sponsored and involves sophisticated cyber operations.
Why the other options are incorrect:
- Cyberterrorism → While cyberterrorism also involves attacks on computer systems, it is conducted by non-state actors (e.g., terrorist groups) rather than governments. Cyberterrorists aim to spread fear, cause destruction, or support political/religious ideologies.
- A cyber attack → A broad term that includes any malicious digital action against a system, but it does not necessarily involve nations attacking each other. Cyberwarfare is a specific type of cyber attack conducted between nations.
- A cyber campaign → This refers to a coordinated effort involving multiple cyber operations, which can be used in espionage, warfare, or criminal activities. However, a campaign can involve multiple actions over time, whereas cyberwarfare specifically focuses on nation-state conflicts.
Conclusion:
Since the question involves a nation-state attacking another nation’s systems (such as a power grid) to cause disruption, the best answer is Cyberwarfare.
-
-
Which of the following statements describes cyberwarfare?
- Cyberwarfare is an attack carried out by a group of script kiddies
- Cyberwarfare is simulation software for Air Force pilots that allows them to practice under a simulated war scenario
- Cyberwarfare is a series of personal protective equipment developed for soldiers involved in nuclear war
- Cyberwarfare is an Internet-based conflict that involves the penetration of information systems of other nations
-
Explanation & Hint: Cyberwarfare refers to the use of digital attacks by one nation-state against another to disrupt, damage, or gain unauthorized access to critical infrastructure, government systems, or military networks. These attacks can involve tactics such as malware, denial-of-service (DoS) attacks, hacking, and cyber-espionage. The goal of cyberwarfare is often to weaken an adversary by targeting its economic, military, or governmental stability.
The other options are incorrect because:
- “Cyberwarfare is an attack carried out by a group of script kiddies” → Script kiddies are inexperienced hackers who use pre-made tools to exploit systems. While they can cause damage, their attacks are not typically considered cyberwarfare, which involves state-sponsored actors.
- “Cyberwarfare is simulation software for Air Force pilots that allows them to practice under a simulated war scenario” → While simulations are used for military training, they are not cyberwarfare. Cyberwarfare involves real-world cyber attacks on other nations.
- “Cyberwarfare is a series of personal protective equipment developed for soldiers involved in nuclear war” → Cyberwarfare deals with digital and cyber threats, not physical protective gear.
Thus, cyberwarfare is best described as an Internet-based conflict involving penetration of information systems of other nations.
-
Which of the statements correctly describes cybersecurity?
- Cybersecurity is the ongoing effort to protect individuals, organizations and governments from digital attacks
- Cybersecurity is the ongoing effort to protect individuals, organizations and governments from crimes that happen only in cyberspace
- Cybersecurity is the ongoing effort to protect computers, networks and data from malicious attacks
-
Explanation & Hint: Cybersecurity is the ongoing effort to protect individuals, organizations, and governments from digital attacks. It goes beyond just securing computers and networks—it safeguards people, businesses, and critical systems from cyber threats such as malware, phishing, and hacking.
Cyber threats constantly evolve, making cybersecurity a continuous process that involves risk management, security policies, and user awareness. Individuals need protection from identity theft and fraud, organizations must secure customer data and operations, and governments must defend national infrastructure and public services.
The term “digital attacks” covers a broad range of cyber risks that impact both technology and human behavior. Cybercriminals exploit vulnerabilities in software, weak passwords, and social engineering tactics to gain unauthorized access.
Since cyber threats can cause financial losses, data breaches, and reputational damage, cybersecurity involves multiple layers of protection, including firewalls, encryption, multi-factor authentication, and regular system updates.
Ultimately, cybersecurity is a shared responsibility. Governments set regulations, organizations implement security measures, and individuals must follow best practices to stay safe online. Without strong cybersecurity, sensitive information and critical systems remain vulnerable to ever-growing digital threats.
-
During a meeting with the Marketing department, a representative from IT discusses features of an upcoming product that will be released next year.
- unethical
- ethical
Explanation & Hint: Sharing information on a new product to the Marketing department of the same company is ethical behavior. It gives them ample lead time to begin development of a marketing plan for the new product.
-
An employee is at a restaurant with friends and describes an exciting new video game that is under development at the company the employee works for. Is the behavior of the employee ethical or unethical?
- unethical
- ethical
Explanation & Hint: It is not ethical to share a confidential product idea before it is released. Describing the game to a group of friends outside the company could leak the idea and jeopardize the new product offering.
-
Alicia, a company employee, has lost her corporate identification badge. She is in a hurry to get to a meeting and does not have time to visit Human Resources to obtain a temporary badge. You lend her your identification badge until she can obtain a replacement.
- ethical
- unethical
Explanation & Hint: Employees should never give their credentials to another employee, regardless of the situation or the familiarity with the other employee. Once your credentials are out of your sight, you have no idea what they are being used for.
-
An employee points out a design flaw in a new product to the department manager.
- unethical
- ethical
Explanation & Hint: Both the employee and the manager are within the same department and company so this behavior would be ethical.
-
An employee is laid off after fifteen years with the same company. The employee is then hired by another company within a week. In the new company, the employee shares documents and ideas for products that the employee proposed at the original company.
- ethical
- unethical
Explanation & Hint: Even though the employee was laid off, the employee probably signed a Non-Disclosure Agreement (NDA) with the original company. Any work or idea developed at the original company, regardless of who proposed the idea, is still the property of the original company. Depending on the level of severity of the breach, this could result in legal action.
-
Which method is used to check the integrity of data?
- checksum
- backup
- authentication
- encryption
Explanation & Hint: A checksum value of a block of data is calculated and transmitted with the data. After the data is received, the checksum hashing is performed again. The calculated value is compared with the transmitted value to verify the integrity of the data.
-
Which statement describes cyberwarfare?
- Cyberwarfare is an attack carried out by a group of script kiddies.
- It is Internet-based conflict that involves the penetration of information systems of other nations.
- It is simulation software for Air Force pilots that allows them to practice under a simulated war scenario.
- It is a series of personal protective equipment developed for soldiers involved in nuclear war.
Explanation & Hint: Cyberwarfare is Internet-based conflict that involves the penetration of the networks and computer systems of other nations. Organized hackers are typically involved in such an attack.
-
What are three methods that can be used to ensure confidentiality of information? (Choose three.)
- two factor authentication
- version control
- file permission settings
- username ID and password
- data encryption
- backup
Explanation & Hint: Methods including data encryption, username ID and password, and two factor authentication can be used to help ensure confidentiality of information. File permission control, version control, and backup are methods that can be used to help ensure integrity of information.
-
What is an example of “hacktivism”?
- A group of environmentalists launch a denial of service attack against an oil company that is responsible for a large oil spill.
- A teenager breaks into the web server of a local newspaper and posts a picture of a favorite cartoon character.
- A country tries to steal defense secrets from another country by infiltrating government networks.
- Criminals use the Internet to attempt to steal money from a banking company.
Explanation & Hint: Hacktivism is a term used to describe cyberattacks carried out by people who are considered political or ideological extremists. Hacktivists attack people or organizations that they believe are enemies to the hacktivist agenda.
-
What is a reason that internal security threats might cause greater damage to an organization than external security threats?
- Internal users can access the corporate data without authentication.
- Internal users have better hacking skills.
- Internal users have direct access to the infrastructure devices.
- Internal users can access the infrastructure devices through the Internet.
Explanation & Hint: Internal threats have the potential to cause greater damage than external threats because internal users have direct access to the building and its infrastructure devices. Internal users may not have better hacking skills than external attackers. Both internal users and external users can access the network devices through the Internet. A well designed security implementation should require authentication before corporate data is accessed, regardless of whether the access request is from within the corporate campus or from the outside network.
-
What is another name for confidentiality of information?
- privacy
- trustworthiness
- accuracy
- consistency
Explanation & Hint: Privacy is another name for confidentiality. Accuracy, consistency, and trustworthiness describe integrity of data.
-
What is the motivation of a white hat attacker?
- discovering weaknesses of networks and systems to improve the security level of these systems
- fine tuning network devices to improve their performance and efficiency
- studying operating systems of various platforms to develop a new system
- taking advantage of any vulnerability for illegal personal gain
Explanation & Hint: White hat attackers break into networks or computer systems in order to discover weaknesses for the purpose of improving the security of these systems. These break-ins are done with permission from the owner or the organization. Any results are reported back to the owner or the organization.
-
Match the type of cyber attackers to the description. (Not all options are used.)
- make political statements, or create fear, by causing physical or psychological damage to victims → terrorists
- gather intelligence or commit sabotage on specific goals on behalf of their government → state-sponsored attackers
- make political statements in order to create an awareness of issues that are important to them → hacktivists
Explanation & Hint: Terrorists:
- Purpose: Their primary goal is to create fear or cause physical and psychological damage to victims. They often target critical infrastructure (like power grids or transportation systems) to disrupt society and send political or ideological messages.
- Example: Attacking public systems to create chaos or manipulating digital platforms to spread propaganda and fear.
State-sponsored attackers:
- Purpose: These attackers work on behalf of a government to gather intelligence, commit sabotage, or achieve strategic goals. Their activities are usually aimed at other countries’ government agencies, defense systems, or critical infrastructure.
- Example: Conducting espionage to steal state secrets, disrupting communications during geopolitical conflicts, or influencing political processes in other countries.
Hacktivists:
- Purpose: Hacktivists use hacking as a form of protest or activism. They aim to make political statements, raise awareness about social issues, or promote causes they believe in. Their attacks are usually meant to disrupt services or deface websites to spread their message.
- Example: Defacing government websites to protest policies or launching distributed denial-of-service (DDoS) attacks against companies they believe are unethical.
-
What three items are components of the CIA triad? (Choose three.)
- confidentiality
- integrity
- intervention
- availability
- access
- scalability
Explanation & Hint: The CIA triad contains three components: confidentiality, integrity, and availability. It is a guideline for information security for an organization.
-
It’s your first day on the job, and it’s time to choose a username for your online identity. Which of the following options would you choose?
This is your first chance to gain some valuable defender points at eLearning company @Apollo, so take your time and think carefully before making your choices.
Choose two correct answers, then Submit.
- jdoe
- jdoe.IT
- jdoe1990
- jane.doe
- j.doe12
Explanation & Hint: When choosing a username, it’s important not to reveal any personal information. It should be something appropriate and respectful and should not lead strangers to think you are an easy target for cybercrimes or unwanted attention.
Some other useful tips to help you generate your username:
- Don’t use your full name or parts of your address or phone number.
- Don’t use your email username.
- Don’t use the same username and password combination, especially on financial accounts.
- Don’t choose a super-odd username and then reuse it again and again — it makes you easier to track.
- Don’t choose a username that gives clues to your passwords such as a series of numbers/letters or the first part of a two-part phrase, such as knock-knock or starlight, or the department in which you work, such as IT.
- Do choose a username that’s appropriate for the type of account, i.e., business, social or personal.
-
So, with all this information about you available online, what do hackers want? Of course, they want your money.
Can you think of an example that you have experienced yourself or that you have heard or read about, where cybercriminals have accessed or tried to access financial information online?
Share your example in the box below, then Submit. Once you have entered your example, select Show answer to reveal a summary response.
- Were you able to think of at least one example?A cybercriminal can take advantage of your relationships, accessing your online accounts and appealing to your good nature to try and trick you into wiring money to your friends or family in a time of need. For example, there have been many reported cases of hackers impersonating family members and sending messages stating that they need money wired in order to get home from abroad after losing their wallets.And while you may think that your frequent flyer air miles are not valuable to cybercriminals, think again. In 2015, cybercriminals hacked approximately 10,000 American Airlines and United accounts, booking free flights and upgrades using stolen credentials. Even though the frequent flyer miles were returned to the customers by the airlines, this example demonstrates the value of your login credentials.
-
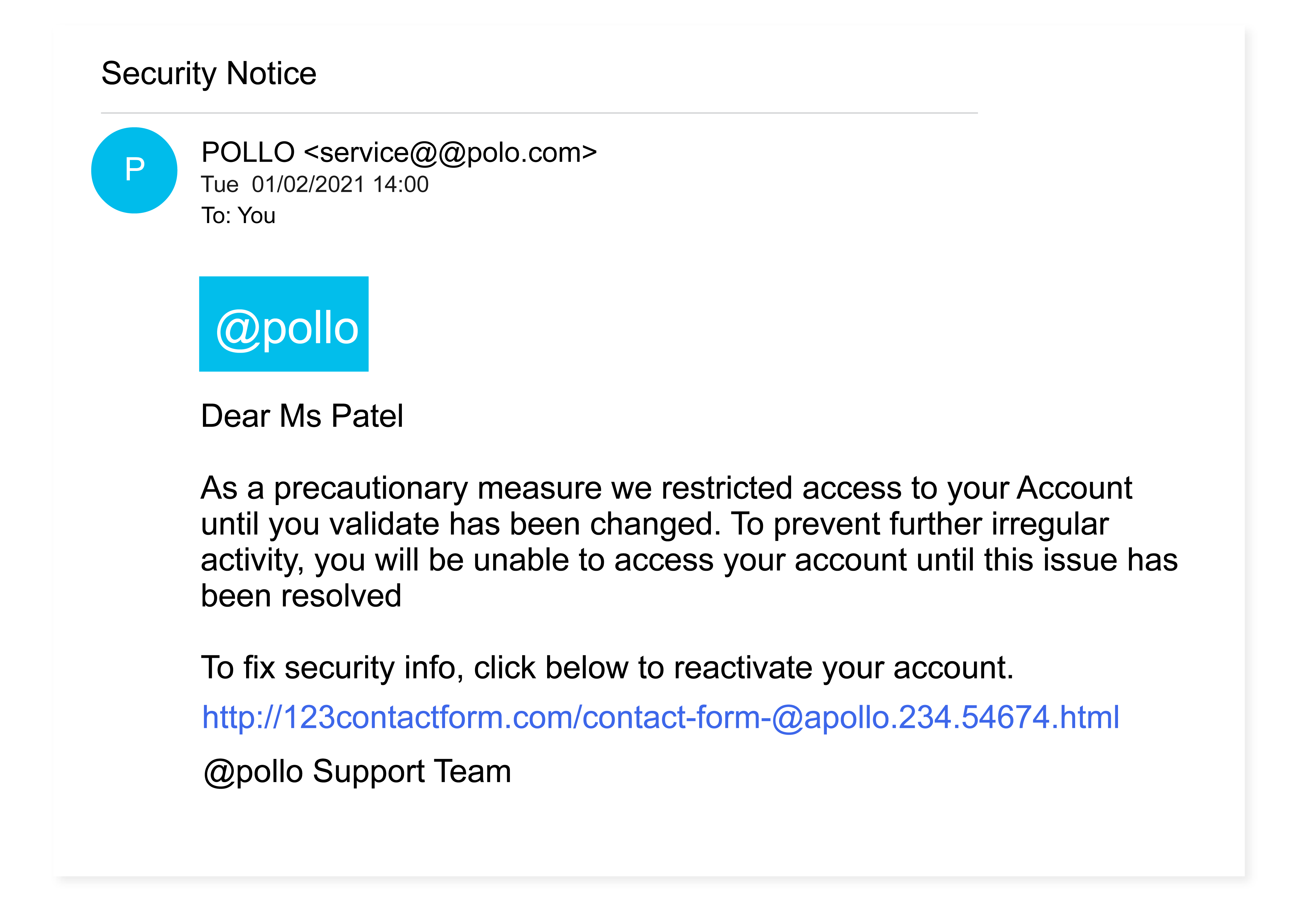
A concerned customer has forwarded on what they believe to be a fraudulent email. It looks as if it has been sent by @Apollo but something appears a little ‘phish-y.’
Security Notice Take a look at the email. Which of the following indicates that it is in fact a phishing email? Don’t forget, you have a chance to earn valuable defender points if you answer this correctly.
Select four correct answers, then Submit.
- Link URL
- Email address
- Customer name
- Graphics
- The language, spelling and grammar
Explanation & Hint: Closer inspection reveals:
- that the sender’s email domain is spelled incorrectly
- that the link URL is not pointing to @Apollo’s website
- poor language, spelling and grammar
- low quality, pixelated graphics
Phishing emails can be hard to detect. For example, they will often address you by name to appear legitimate, but hackers can easily find this information on the Internet. So, it’s important to stay alert and think before you click.
-
According to our sources, a well known hotel chain that operates across the world has reported a massive data breach, with the personal information of over three million guests exposed to hackers.
Hotel Data Breach The hotel discovered that hackers gained access to its customer database by using the login details of one of its employees.
At this point, the hotel doesn’t believe that the hackers were able to access any account passwords or financial information. Recent guests are encouraged to check the hotel chain’s web portal to see if they have been impacted by this breach.
In this example, what did the hackers take?
- The username and password of all of the hotel’s employees
- The names, email address and phone numbers of over three million hotel guests
- The hotel chain’s reputation
- The card payment information of over three million guests
Explanation & Hint: Read the news story again and consider the victims — in this case, the hotel guests. What information were the hackers able to gather about them?
-
What exploits did the hackers use in this case to gain access to valuable personal information?
Select the correct answer, then Submit.
- Taking advantage of student information not being correctly validated on the platform
- Bypassing the platform’s access control methods
- Weaknesses in the platform’s security practices
- Extracting information when the volume of student data exceeds the storage capacity of the platform’s memory buffer
-
Explanation & Hint: Hackers are taking advantage of an unsecured cloud database left exposed on the Internet. This is an example of a poor security practice.
-
Every organization is at risk of a cyber attack and therefore must take appropriate action to protect itself.
Thinking back to each of the two security breach examples outlined above, what measures could these organizations have implemented in order to have prevented these security breaches?
Write your thoughts in the box below, then Submit. Select Show answer to check your response.
- In both cases, the organizations need to invest in improved security practices.This might include:investing in cybersecurity training for all staff so that they are aware of and able to spot a cyber attack
enforcing two factor authentication for employees accessing files and applications that contain sensitive data
maintaining log files and ongoing monitoring to identify anomalous behavior that might indicate a data breach
storing the passwords of customers using a combination of salting and robust hashing algorithms
separating cloud-based resources from the public Internet into an isolated private network segment
granting employee access to personal data and internal systems only via a secure VPN connection.
- In both cases, the organizations need to invest in improved security practices.This might include:investing in cybersecurity training for all staff so that they are aware of and able to spot a cyber attack
-
Now that you know the different types of attackers and their motivations for doing what they do, can you identify what color of hat is worn by the attacker in each of the following scenarios? This is a tricky one but remember, you can earn valuable defender points if you answer correctly.
Select the correct answer from the dropdowns, then Submit.
- After hacking into ATM systems remotely using a laptop, this attacker worked with the ATM manufacturers to resolve the identified security vulnerabilities. ==> Gray hat
- This attacker transferred $10 million into their bank account using customer account and PIN credentials gathered from recordings. ==> Black hat
- This attacker’s job is to identify weaknesses in a company’s computer system. ==> White hat
- This attacker used malware to compromise a company’s system and steal credit card information that was then sold to the highest bidder. ==> Black hat
- While carrying out some research, this attacker stumbled across a security vulnerability on an organization’s network that they are authorized to access. ==> White hat
-
Remember that phishing email you received earlier from one of your customers?
An investigation into this email revealed that the user accounts and access privileges of a former employee were not fully removed from the IT systems on leaving the company. In fact, this former employee, who now works for a competitor, logged into @Apollo’s customer database only three days ago.
Has an internal or external security threat occurred here?
Select an answer, then Submit.
- Internal
- External
Explanation & Hint: This ex-employee was able to launch an attack based on insider knowledge of the organization’s network.