CISSP : Certified Information Systems Security Professional : Part 10
-
Why would a security architect specify that a default route pointing to a sinkhole be injected into internal networks?
- To have firewalls route all network traffic
- To detect the traffic destined to non-existent network destinations
- To exercise authority over the network department
- To re-inject the route into external networks
-
What is the BEST location in a network to place Virtual Private Network (VPN) devices when an internal review reveals network design flaws in remote access?
- In a dedicated Demilitarized Zone (DMZ)
- At the Internet Service Provider (ISP)
- In its own separate Virtual Local Area Network (VLAN)
- Outside the external firewall
-
Which of the following provides the GREATEST level of data security for a Virtual Private Network (VPN) connection?
- Internet Protocol Payload Compression (IPComp)
- Internet Protocol Security (IPSec)
- Extensible Authentication Protocol (EAP)
- Remote Authentication Dial-In User Service (RADIUS)
-
What technique used for spoofing the origin of an email can successfully conceal the sender’s Internet Protocol (IP) address?
- Virtual Private Network (VPN)
- Change In-Reply-To data
- Onion routing
- Web crawling
-
An organization allows ping traffic into and out of their network. An attacker has installed a program on the network that uses the payload portion of the ping packet to move data into and out of the network. What type of attack has the organization experienced?
- Data leakage
- Unfiltered channel
- Data emanation
- Covert channel
-
In a dispersed network that lacks central control, which of the following is the PRIMARY course of action to mitigate exposure?
- Implement security policies and standards, data backups, and audit controls
- Implement management policies, audit control, and data backups
- Implement security policies and standards, access controls, and access limitations
- Implement remote access policies, shared workstations, and log management
-
Which of the following actions should be taken by a security professional when a mission critical computer network attack is suspected?
- Isolate the network, log an independent report, fix the problem, and redeploy the computer
- Isolate the network, install patches, and report the occurrence
- Prioritize, report and investigate the occurrence
- Turn the router off, perform forensic analysis, apply the appropriate fix, and log incidents
-
Point-to-Point Protocol (PPP) was designed to specifically address what issue?
- A common design flaw in telephone modems
- Speed and reliability issues between dial-up users and Internet Service Providers (ISP)
- Compatibility issues with personal computers and web browsers
- The security of dial-up connections to remote networks
-
Which of the following protocols will allow the encrypted transfer of content on the Internet?
- Server Message Block (SMB)
- Secure copy
- Hypertext Transfer Protocol (HTTP)
- Remote copy
-
Which of the following is included in the Global System for Mobile Communications (GSM) security framework?
- Public-Key Infrastructure (PKI)
- Symmetric key cryptography
- Digital signatures
- Biometric authentication
-
Which of the following is a Key Performance Indicator (KPI) for a security training and awareness program?
- The number of security audits performed
- The number of attendees at security training events
- The number of security training materials created
- The number of security controls implemented
-
Which of the following BEST describes a Protection Profile (PP)?
- A document that expresses an implementation independent set of security requirements for an Information Technology (IT) product that meets specific consumer needs
- A document that is used to develop an Information Technology (IT) security product from its security requirements definition
- A document that expresses an implementation dependent set of security requirements which contains only the security functional requirements
- A document that represents evaluated products where there is a one-to-one correspondence between a PP and a Security Target (ST)
-
An organization lacks a data retention policy. Of the following, who is the BEST person to consult for such requirement?
- Application Manager
- Database Administrator
- Privacy Officer
- Finance Manager
-
Which of the following is the PRIMARY issue when analyzing detailed log information?
- Logs may be unavailable when required
- Timely review of the data is potentially difficult
- Most systems and applications do not support logging
- Logs do not provide sufficient details of system and individual activities
-
Which Redundant Array of Independent Disks (RAID) Level does the following diagram represent?
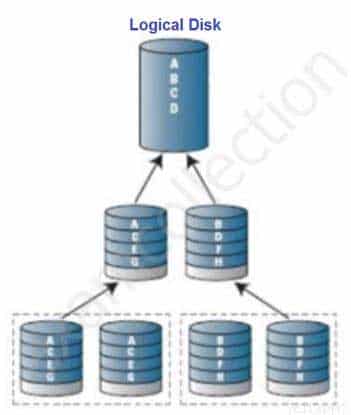
CISSP Certified Information Systems Security Professional Part 10 Q15 001 - RAID 0
- RAID 1
- RAID 5
- RAID 10
-
Which of the following MUST be done when promoting a security awareness program to senior management?
- Show the need for security; identify the message and the audience
- Ensure that the security presentation is designed to be all-inclusive
- Notify them that their compliance is mandatory
- Explain how hackers have enhanced information security
-
Which of the following BEST describes the objectives of the Business Impact Analysis (BIA)?
- Identifying the events and environmental factors that can adversely affect an organization
- Identifying what is important and critical based on disruptions that can affect the organization
- Establishing the need for a Business Continuity Plan (BCP) based on threats that can affect an organization
- Preparing a program to create an organizational awareness for executing the Business Continuity Plan (BCP)
-
Which of the following is considered the PRIMARY security issue associated with encrypted e-mail messages?
- Key distribution
- Storing attachments in centralized repositories
- Scanning for viruses and other malware
- Greater costs associated for backups and restores
-
Which one of the following would cause an immediate review and possible change to the security policies of an organization?
- Change in technology
- Change in senior management
- Change to organization processes
- Change to organization goals
-
A system with Internet Protocol (IP) address 10.102.10.2 has a physical address of 00:00:08:00:12:13:14:2f. The following static entry is added to its Address Resolution Protocol (ARP) table: 10.102.10.6: 00:00:08:00:12:13:14:2f.
What form of attack could this represent?
- A Denial of Service (DoS) attack against the gateway router because the router can no longer accept packets from 10.102.10.2
- A transport layer attack that prevents the resolution of 10.102.10.6 address
- A Denial of Service (DoS) attack against 10.102.10.2 because it cannot respond correctly to ARP requests
- A masquerading attack that sends packets intended for 10.102.10.6 to 10.102.10.2
Subscribe
0 Comments
Newest