CISSP : Certified Information Systems Security Professional : Part 20
-
Although code using a specific program language may not be susceptible to a buffer overflow attack,
- most calls to plug-in programs are susceptible.
- most supporting application code is susceptible.
- the graphical images used by the application could be susceptible.
- the supporting virtual machine could be susceptible.
-
What is the BEST way to encrypt web application communications?
- Secure Hash Algorithm 1 (SHA-1)
- Secure Sockets Layer (SSL)
- Cipher Block Chaining Message Authentication Code (CBC-MAC)
- Transport Layer Security (TLS)
-
Which of the following are effective countermeasures against passive network-layer attacks?
- Federated security and authenticated access controls
- Trusted software development and run time integrity controls
- Encryption and security enabled applications
- Enclave boundary protection and computing environment defense
-
What is the MOST important element when considering the effectiveness of a training program for Business Continuity (BC) and Disaster Recovery (DR)?
- Management support
- Consideration of organizational need
- Technology used for delivery
- Target audience
-
DRAG DROP
Match the name of access control model with its associated restriction.
Drag each access control model to its appropriate restriction access on the right.
CISSP Certified Information Systems Security Professional Part 20 Q05 004 Question 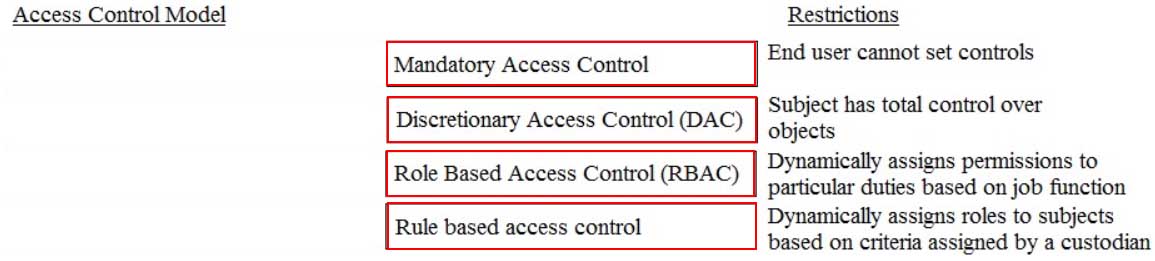
CISSP Certified Information Systems Security Professional Part 20 Q05 004 Answer -
A database administrator is asked by a high-ranking member of management to perform specific changes to the accounting system database. The administrator is specifically instructed to not track or evidence the change in a ticket. Which of the following is the BEST course of action?
- Ignore the request and do not perform the change.
- Perform the change as requested, and rely on the next audit to detect and report the situation.
- Perform the change, but create a change ticket regardless to ensure there is complete traceability.
- Inform the audit committee or internal audit directly using the corporate whistleblower process.
-
Which of the following is the MOST important goal of information asset valuation?
- Developing a consistent and uniform method of controlling access on information assets
- Developing appropriate access control policies and guidelines
- Assigning a financial value to an organization’s information assets
- Determining the appropriate level of protection
-
Which of the following is a strategy of grouping requirements in developing a Security Test and Evaluation (ST&E)?
- Tactical, strategic, and financial
- Management, operational, and technical
- Documentation, observation, and manual
- Standards, policies, and procedures
-
Which one of the following activities would present a significant security risk to organizations when employing a Virtual Private Network (VPN) solution?
- VPN bandwidth
- Simultaneous connection to other networks
- Users with Internet Protocol (IP) addressing conflicts
- Remote users with administrative rights
-
Which of the following BEST describes a chosen plaintext attack?
- The cryptanalyst can generate ciphertext from arbitrary text.
- The cryptanalyst examines the communication being sent back and forth.
- The cryptanalyst can choose the key and algorithm to mount the attack.
- The cryptanalyst is presented with the ciphertext from which the original message is determined.
-
For network based evidence, which of the following contains traffic details of all network sessions in order to detect anomalies?
- Alert data
- User data
- Content data
- Statistical data
-
Which of the following is the PRIMARY reason to perform regular vulnerability scanning of an organization network?
- Provide vulnerability reports to management.
- Validate vulnerability remediation activities.
- Prevent attackers from discovering vulnerabilities.
- Remediate known vulnerabilities.
-
Which of the following would BEST describe the role directly responsible for data within an organization?
- Data custodian
- Information owner
- Database administrator
- Quality control
-
The restoration priorities of a Disaster Recovery Plan (DRP) are based on which of the following documents?
- Service Level Agreement (SLA)
- Business Continuity Plan (BCP)
- Business Impact Analysis (BIA)
- Crisis management plan
-
The PRIMARY outcome of a certification process is that it provides documented
- interconnected systems and their implemented security controls.
- standards for security assessment, testing, and process evaluation.
- system weakness for remediation.
- security analyses needed to make a risk-based decision.
-
A security architect plans to reference a Mandatory Access Control (MAC) model for implementation. This indicates that which of the following properties are being prioritized?
- Confidentiality
- Integrity
- Availability
- Accessibility
Explanation:Mandatory Access Control (MAC) is system-enforced access control based on a subject’s clearance and an object’s labels. Subjects and Objects have clearances and labels, respectively, such as confidential, secret, and top secret. A subject may access an object only if the subject’s clearance is equal to or greater than the object’s label. Subjects cannot share objects with other subjects who lack the proper clearance, or “write down” objects to a lower classification level (such as from top secret to secret). MAC systems are usually focused on preserving the confidentiality of data.
Reference: https://www.sciencedirect.com/topics/computer-science/mandatory-access-control
-
A vulnerability in which of the following components would be MOST difficult to detect?
- Kernel
- Shared libraries
- Hardware
- System application
-
During which of the following processes is least privilege implemented for a user account?
- Provision
- Approve
- Request
- Review
-
Which of the following is a document that identifies each item seized in an investigation, including date and time seized, full name and signature or initials of the person who seized the item, and a detailed description of the item?
- Property book
- Chain of custody form
- Search warrant return
- Evidence tag
-
Which of the following is needed to securely distribute symmetric cryptographic keys?
- Officially approved Public-Key Infrastructure (PKI) Class 3 or Class 4 certificates
- Officially approved and compliant key management technology and processes
- An organizationally approved communication protection policy and key management plan
- Hardware tokens that protect the user’s private key.