SSCP : System Security Certified Practitioner (SSCP) : Part 01
-
Which of the following ASYMMETRIC encryption algorithms is based on the difficulty of FACTORING LARGE NUMBERS?
- El Gamal
- RSA
- RSA
- International Data Encryption Algorithm (IDEA)
Explanation:
Named after its inventors Ron Rivest , Adi Shamir and Leonard Adleman is based on the difficulty of factoring large prime numbers.
Factoring a number means representing it as the product of prime numbers. Prime numbers, such as 2, 3, 5, 7, 11, and 13, are those numbers that are not evenly divisible by any smaller number, except 1. A non-prime, or composite number, can be written as the product of smaller primes, known as its prime factors. 665, for example is the product of the primes 5, 7, and 19. A number is said to be factored when all of its prime factors are identified. As the size of the number increases, the difficulty of factoring increases rapidly.
The other answers are incorrect because:
El Gamal is based on the discrete logarithms in a finite field.
Elliptic Curve Cryptosystems (ECCs) computes discrete logarithms of elliptic curves.
International Data Encryption Algorithm (IDEA) is a block cipher and operates on 64 bit blocks of data and is a SYMMETRIC algorithm.
Reference : Shon Harris , AIO v3 , Chapter-8 : Cryptography , Page : 638 -
The Diffie-Hellman algorithm is primarily used to provide which of the following?
- Confidentiality
- Key Agreement
- Integrity
- Non-repudiation
ExplanationDiffie and Hellman describe a means for two parties to agree upon a shared secret in such a way that the secret will be unavailable to eavesdroppers. This secret may then be converted into cryptographic keying material for other (symmetric) algorithms. A large number of minor variants of this process exist. See RFC 2631 Diffie-Hellman Key Agreement Method for more details.
In 1976, Diffie and Hellman were the first to introduce the notion of public key cryptography, requiring a system allowing the exchange of secret keys over non-secure channels. The Diffie-Hellman algorithm is used for key exchange between two parties communicating with each other, it cannot be used for encrypting and decrypting messages, or digital signature.
Diffie and Hellman sought to address the issue of having to exchange keys via courier and other unsecure means. Their efforts were the FIRST asymmetric key agreement algorithm. Since the Diffie-Hellman algorithm cannot be used for encrypting and decrypting it cannot provide confidentiality nor integrity. This algorithm also does not provide for digital signature functionality and thus non-repudiation is not a choice.NOTE: The DH algorithm is susceptible to man-in-the-middle attacks.
KEY AGREEMENT VERSUS KEY EXCHANGE
A key exchange can be done multiple way. It can be done in person, I can generate a key and then encrypt the key to get it securely to you by encrypting it with your public key. A Key Agreement protocol is done over a public medium such as the internet using a mathematical formula to come out with a common value on both sides of the communication link, without the ennemy being able to know what the common agreement is.The following answers were incorrect:
All of the other choices were not correct choices
Reference(s) used for this question:
Shon Harris, CISSP All In One (AIO), 6th edition . Chapter 7, Cryptography, Page 812.
http://en.wikipedia.org/wiki/Diffie%E2%80%93Hellman_key_exchange
http://www.google.com/patents?vid=4200770 -
Which of the following is NOT an asymmetric key algorithm?
- RSA
- Elliptic Curve Cryptosystem (ECC)
- El Gamal
- Data Encryption System (DES)
Explanation:Data Encryption Standard (DES) is a symmetric key algorithm. Originally developed by IBM, under project name Lucifer, this 128-bit algorithm was accepted by the NIST in 1974, but the key size was reduced to 56 bits, plus 8 bits for parity. It somehow became a national cryptographic standard in 1977, and an American National Standard Institute (ANSI) standard in 1978. DES was later replaced by the Advanced Encryption Standard (AES) by the NIST. All other options are asymmetric algorithms.
Source: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, McGraw-Hill/Osborne, 2002, chapter 8: Cryptography (page 525).
Reference: DES: http://csrc.nist.gov/publications/fips/fips46-3/fips46-3.pdf -
Which of the following is NOT a symmetric key algorithm?
- Blowfish
- Digital Signature Standard (DSS)
- Triple DES (3DES)
- RC5
Explanation:Digital Signature Standard (DSS) specifies a Digital Signature Algorithm (DSA) appropriate for applications requiring a digital signature, providing the capability to generate signatures (with the use of a private key) and verify them (with the use of the corresponding public key).
Source: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, McGraw-Hill/Osborne, 2002, chapter 8: Cryptography (page 550).
Reference: DSS: http://www.itl.nist.gov/fipspubs/fip186.htm. -
In what type of attack does an attacker try, from several encrypted messages, to figure out the key used in the encryption process?
- Known-plaintext attack
- Ciphertext-only attack
- Chosen-Ciphertext attack
- Plaintext-only attack
Explanation:In a ciphertext-only attack, the attacker has the ciphertext of several messages encrypted with the same encryption algorithm. Its goal is to discover the plaintext of the messages by figuring out the key used in the encryption process. In a known-plaintext attack, the attacker has the plaintext and the ciphertext of one or more messages. In a chosen-ciphertext attack, the attacker can chose the ciphertext to be decrypted and has access to the resulting plaintext.
Source: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, McGraw-Hill/Osborne, 2002, Chapter 8: Cryptography (page 578).
-
Which encryption algorithm is BEST suited for communication with handheld wireless devices?
- ECC (Elliptic Curve Cryptosystem)
- RSA
- SHA
- RC4
Explanation:As it provides much of the same functionality that RSA provides: digital signatures, secure key distribution, and encryption. One differing factor is ECC’s efficiency. ECC is more efficient that RSA and any other asymmetric algorithm. The following answers are incorrect because : RSA is incorrect as it is less efficient than ECC to be used in handheld devices. SHA is also incorrect as it is a hashing algorithm. RC4 is also incorrect as it is a symmetric algorithm. Reference : Shon Harris AIO v3 , Chapter-8 : Cryptography , Page : 631 , 638. -
Which protocol makes USE of an electronic wallet on a customer’s PC and sends encrypted credit card information to merchant’s Web server, which digitally signs it and sends it on to its processing bank?
- SSH ( Secure Shell)
- S/MIME (Secure MIME)
- SET (Secure Electronic Transaction)
- SSL (Secure Sockets Layer)
Explanation:As protocol was introduced by Visa and Mastercard to allow for more credit card transaction possibilities. It is comprised of three different pieces of software, running on the customer’s PC (an electronic wallet), on the merchant’s Web server and on the payment server of the merchant’s bank. The credit card information is sent by the customer to the merchant’s Web server, but it does not open it and instead digitally signs it and sends it to its bank’s payment server for processing.
The following answers are incorrect because :
SSH (Secure Shell) is incorrect as it functions as a type of tunneling mechanism that provides terminal like access to remote computers.
S/MIME is incorrect as it is a standard for encrypting and digitally signing electronic mail and for providing secure data transmissions.
SSL is incorrect as it uses public key encryption and provides data encryption, server authentication, message integrity, and optional client authentication.Reference : Shon Harris AIO v3 , Chapter-8: Cryptography , Page : 667-669
-
Which of the following algorithms does NOT provide hashing?
- SHA-1
- MD2
- RC4
- MD5
Explanation:As it is an algorithm used for encryption and does not provide hashing functions , it is also commonly implemented ‘ Stream Ciphers ‘.
The other answers are incorrect because :
SHA-1 was designed by NIST and NSA to be used with the Digital Signature Standard (DSS). SHA was designed to be used in digital signatures and was developed when a more secure hashing algorithm was required for U.S. government applications.MD2 is a one-way hash function designed by Ron Rivest that creates a 128-bit message digest value. It is not necessarily any weaker than the other algorithms in the “MD” family, but it is much slower.
MD5 was also created by Ron Rivest and is the newer version of MD4. It still produces a 128-bit hash, but the algorithm is more complex, which makes it harder to break.
Reference : Shon Harris , AIO v3 , Chapter – 8 : Cryptography , Page : 644 – 645
-
Which of the following would best describe certificate path validation?
- Verification of the validity of all certificates of the certificate chain to the root certificate
- Verification of the integrity of the associated root certificate
- Verification of the integrity of the concerned private key
- Verification of the revocation status of the concerned certificate
Explanation:With the advent of public key cryptography (PKI), it is now possible to communicate securely with untrusted parties over the Internet without prior arrangement. One of the necessities arising from such communication is the ability to accurately verify someone’s identity (i.e. whether the person you are communicating with is indeed the person who he/she claims to be). In order to be able to perform identity check for a given entity, there should be a fool-proof method of “binding” the entity’s public key to its unique domain name (DN).
A X.509 digital certificate issued by a well known certificate authority (CA), like Verisign, Entrust, Thawte, etc., provides a way of positively identifying the entity by placing trust on the CA to have performed the necessary verifications. A X.509 certificate is a cryptographically sealed data object that contains the entity’s unique DN, public key, serial number, validity period, and possibly other extensions.
The Windows Operating System offers a Certificate Viewer utility which allows you to double-click on any certificate and review its attributes in a human-readable format. For instance, the “General” tab in the Certificate Viewer Window (see below) shows who the certificate was issued to as well as the certificate’s issuer, validation period and usage functions.
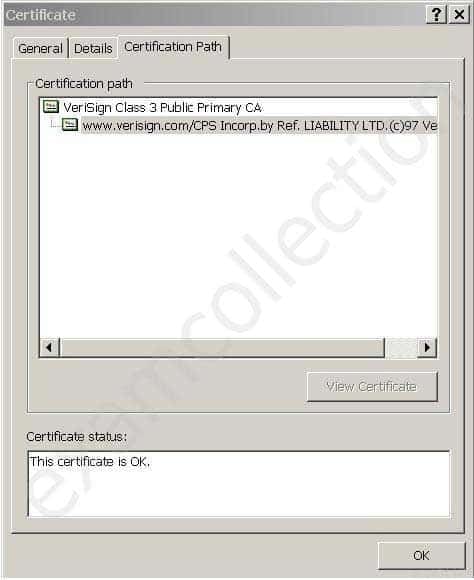
SSCP System Security Certified Practitioner (SSCP) Part 01 Q09 001 Certification Path graphic
The “Certification Path” tab contains the hierarchy for the chain of certificates. It allows you to select the certificate issuer or a subordinate certificate and then click on “View Certificate” to open the certificate in the Certificate Viewer.Each end-user certificate is signed by its issuer, a trusted CA, by taking a hash value (MD5 or SHA-1) of ASN.1 DER (Distinguished Encoding Rule) encoded object and then encrypting the resulting hash with the issuer’s private key (CA’s Private Key) which is a digital signature. The encrypted data is stored in the “signatureValue” attribute of the entity’s (CA) public certificate.
Once the certificate is signed by the issuer, a party who wishes to communicate with this entity can then take the entity’s public certificate and find out who the issuer of the certificate is. Once the issuer’s of the certificate (CA) is identified, it would be possible to decrypt the value of the “signatureValue” attribute in the entity’s certificate using the issuer’s public key to retrieve the hash value. This hash value will be compared with the independently calculated hash on the entity’s certificate. If the two hash values match, then the information contained within the certificate must not have been altered and, therefore, one must trust that the CA has done enough background check to ensure that all details in the entity’s certificate are accurate.
The process of cryptographically checking the signatures of all certificates in the certificate chain is called “key chaining”. An additional check that is essential to key chaining is verifying that the value of the “subjectKeyIdentifier” extension in one certificate matches the same in the subsequent certificate.
Similarly, the process of comparing the subject field of the issuer certificate to the issuer field of the subordinate certificate is called “name chaining”. In this process, these values must match for each pair of adjacent certificates in the certification path in order to guarantee that the path represents unbroken chain of entities relating directly to one another and that it has no missing links.
The two steps above are the steps to validate the Certification Path by ensuring the validity of all certificates of the certificate chain to the root certificate as described in the two paragraphs above.
Reference(s) used for this question:
FORD, Warwick & BAUM, Michael S., Secure Electronic Commerce: Building the Infrastructure for Digital Signatures and Encryption (2nd Edition), 2000, Prentice Hall PTR, Page 262.
and
https://www.tibcommunity.com/docs/DOC-2197 -
Which of the following can best define the “revocation request grace period”?
- The period of time allotted within which the user must make a revocation request upon a revocation reason
- Minimum response time for performing a revocation by the CA
- Maximum response time for performing a revocation by the CA
- Time period between the arrival of a revocation request and the publication of the revocation information
Explanation:The length of time between the Issuer’s receipt of a revocation request and the time the Issuer is required to revoke the certificate should bear a reasonable relationship to the amount of risk the participants are willing to assume that someone may rely on a certificate for which a proper evocation request has been given but has not yet been acted upon.
How quickly revocation requests need to be processed (and CRLs or certificate status databases need to be updated) depends upon the specific application for which the Policy Authority is rafting the Certificate Policy.
A Policy Authority should recognize that there may be risk and lost tradeoffs with respect to grace periods for revocation notices.
If the Policy Authority determines that its PKI participants are willing to accept a grace period of a few hours in exchange for a lower implementation cost, the Certificate Policy may reflect that decision. -
What does the directive of the European Union on Electronic Signatures deal with?
- Encryption of classified data
- Encryption of secret data
- Non repudiation
- Authentication of web servers
Explanation:Reference: FORD, Warwick & BAUM, Michael S., Secure Electronic Commerce: Building the Infrastructure for Digital Signatures and Encryption (2nd Edition), 2000, Prentice Hall PTR, Page 589; Directive 1999/93/EC of 13 December 1999 on a Community framework for electronic signatures. -
A X.509 public key certificate with the key usage attribute “non repudiation” can be used for which of the following?
- encrypting messages
- signing messages
- verifying signed messages
- decrypt encrypted messages
Explanation:References: RFC 2459 : Internet X.509 Public Key Infrastructure Certificate and CRL Profile; GUTMANN, P., X.509 style guide. -
What kind of Encryption technology does SSL utilize?
- Secret or Symmetric key
- Hybrid (both Symmetric and Asymmetric)
- Public Key
- Private key
Explanation:SSL use public-key cryptography to secure session key, while the session key (secret key) is used to secure the whole session taking place between both parties communicating with each other.
The SSL protocol was originally developed by Netscape. Version 1.0 was never publicly released; version 2.0 was released in February 1995 but “contained a number of security flaws which ultimately led to the design of SSL version 3.0.” SSL version 3.0, released in 1996, was a complete redesign of the protocol produced by Paul Kocher working with Netscape engineers Phil Karlton and Alan Freier.
All of the other answers are incorrect
-
What is the name of a one way transformation of a string of characters into a usually shorter fixed-length value or key that represents the original string? Such a transformation cannot be reversed?
- One-way hash
- DES
- Transposition
- Substitution
Explanation:A cryptographic hash function is a transformation that takes an input (or ‘message’) and returns a fixed-size string, which is called the hash value (sometimes termed a message digest, a digital fingerprint, a digest or a checksum).
The ideal hash function has three main properties – it is extremely easy to calculate a hash for any given data, it is extremely difficult or almost impossible in a practical sense to calculate a text that has a given hash, and it is extremely unlikely that two different messages, however close, will have the same hash.
Functions with these properties are used as hash functions for a variety of purposes, both within and outside cryptography. Practical applications include message integrity checks, digital signatures, authentication, and various information security applications. A hash can also act as a concise representation of the message or document from which it was computed, and allows easy indexing of duplicate or unique data files.
In various standards and applications, the two most commonly used hash functions are MD5 and SHA-1. In 2005, security flaws were identified in both of these, namely that a possible mathematical weakness might exist, indicating that a stronger hash function would be desirable. In 2007 the National Institute of Standards and Technology announced a contest to design a hash function which will be given the name SHA-3 and be the subject of a FIPS standard.
A hash function takes a string of any length as input and produces a fixed length string which acts as a kind of “signature” for the data provided. In this way, a person knowing the hash is unable to work out the original message, but someone knowing the original message can prove the hash is created from that message, and none other. A cryptographic hash function should behave as much as possible like a random function while still being deterministic and efficiently computable.
A cryptographic hash function is considered “insecure” from a cryptographic point of view, if either of the following is computationally feasible:
finding a (previously unseen) message that matches a given digest
finding “collisions”, wherein two different messages have the same message digest.An attacker who can do either of these things might, for example, use them to substitute an authorized message with an unauthorized one.
Ideally, it should not even be feasible to find two messages whose digests are substantially similar; nor would one want an attacker to be able to learn anything useful about a message given only its digest. Of course the attacker learns at least one piece of information, the digest itself, which for instance gives the attacker the ability to recognise the same message should it occur again.
REFERENCES:
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, 2001, John Wiley & Sons, Pages 40-41.
also see:
http://en.wikipedia.org/wiki/Cryptographic_hash_function -
Which is NOT a suitable method for distributing certificate revocation information?
- CA revocation mailing list
- Delta CRL
- OCSP (online certificate status protocol)
- Distribution point CRL
Explanation:The following are incorrect answers because they are all suitable methods.
A Delta CRL is a CRL that only provides information about certificates whose statuses have changed since the issuance of a specific, previously issued CRL.
The Online Certificate Status Protocol (OCSP) is an Internet protocol used for obtaining the revocation status of an X.509 digital certificate.
A Distribution point CRL or CRL Distribution Point, a location specified in the CRL Distribution Point (CRL DP) X.509, version 3, certificate extension when the certificate is issued.
References:
RFC 2459: Internet X.509 Public Key Infrastru
http://csrc.nist.gov/groups/ST/crypto_apps_infra/documents/sliding_window.pdf
http://www.ipswitch.eu/online_certificate_status_protocol_en.html
Computer Security Handbook By Seymour Bosworth, Arthur E. Hutt, Michel E. Kabay http://books.google.com/books?id=rCx5OfSFUPkC&printsec=frontcover&dq=Computer+Security+Handbook#PRA6-PA4,M1 -
Which of the following is true about digital certificate?
- It is the same as digital signature proving Integrity and Authenticity of the data
- Electronic credential proving that the person the certificate was issued to is who they claim to be
- You can only get digital certificate from Verisign, RSA if you wish to prove the key belong to a specific user.
- Can’t contain geography data such as country for example.
Explanation:Digital certificate helps others verify that the public keys presented by users are genuine and valid. It is a form of Electronic credential proving that the person the certificate was issued to is who they claim to be.
The certificate is used to identify the certificate holder when conducting electronic transactions.
It is issued by a certification authority (CA). It contains the name of an organization or individual, the business address, a serial number, expiration dates, a copy of the certificate holder’s public key (used for encrypting messages), and the digital signature of the certificate-issuing authority so that a recipient can verify that the certificate is real. Some digital certificates conform to a standard, X.509. Digital certificates can be kept in registries so that authenticating users can look up other users’ public keys.Digital certificates are key to the PKI process. The digital certificate serves two roles. First, it ensures the integrity of the public key and makes sure that the key remains unchanged and in a valid state. Second, it validates that the public key is tied to the stated owner and that all associated information is true and correct. The information needed to accomplish these goals is added into the digital certificate.
A Certificate Authority (CA) is an entity trusted by one or more users as an authority in a network that issues, revokes, and manages digital certificates.
A Registration Authority (RA) performs certificate registration services on behalf of a CA. The RA, a single purpose server, is responsible for the accuracy of the information contained in a certificate request. The RA is also expected to perform user validation before issuing a certificate request.A Digital Certificate is not like same as a digital signature, they are two different things, a digital Signature is created by using your Private key to encrypt a message digest and a Digital Certificate is issued by a trusted third party who vouch for your identity.
There are many other third parties which are providing Digital Certifictes and not just Verisign, RSA.
Reference(s) used for this question:
Hernandez CISSP, Steven (2012-12-21). Official (ISC)2 Guide to the CISSP CBK, Third Edition ((ISC)2 Press) (Kindle Locations 14894-14903). Auerbach Publications. Kindle Edition.Gregg, Michael; Haines, Billy (2012-02-16). CASP: CompTIA Advanced Security Practitioner Study Guide Authorized Courseware: Exam CAS-001 (p. 24). Wiley. Kindle Edition.
Please refer to http://en.wikipedia.org/wiki/Digital_certificate
What is Digital certificate: http://searchsecurity.techtarget.com/sDefinition/0,,sid14_gci211947,00.html
another deifination on http://www.webopedia.com/TERM/D/digital_certificate.html -
Which of the following keys has the SHORTEST lifespan?
- Secret key
- Public key
- Session key
- Private key
Explanation:As session key is a symmetric key that is used to encrypt messages between two users. A session key is only good for one communication session between users.
For example , If Tanya has a symmetric key that she uses to encrypt messages between Lance and herself all the time , then this symmetric key would not be regenerated or changed. They would use the same key every time they communicated using encryption. However , using the same key repeatedly increases the chances of the key being captured and the secure communication being compromised. If , on the other hand , a new symmetric key were generated each time Lance and Tanya wanted to communicate , it would be used only during their dialog and then destroyed. if they wanted to communicate and hour later , a new session key would be created and shared.
The other answers are not correct because :
Public Key can be known to anyone.
Private Key must be known and used only by the owner.
Secret Keys are also called as Symmetric Keys, because this type of encryption relies on each user to keep the key a secret and properly protected.REFERENCES:
SHON HARRIS , ALL IN ONE THIRD EDITION : Chapter 8 : Cryptography , Page : 619-620 -
Which of the following is NOT a property of the Rijndael block cipher algorithm?
- The key sizes must be a multiple of 32 bits
- Maximum block size is 256 bits
- Maximum key size is 512 bits
- The key size does not have to match the block size
Explanation:The above statement is NOT true and thus the correct answer. The maximum key size on Rijndael is 256 bits.
There are some differences between Rijndael and the official FIPS-197 specification for AES.
Rijndael specification per se is specified with block and key sizes that must be a multiple of 32 bits, both with a minimum of 128 and a maximum of 256 bits. Namely, Rijndael allows for both key and block sizes to be chosen independently from the set of { 128, 160, 192, 224, 256 } bits. (And the key size does not in fact have to match the block size).However, FIPS-197 specifies that the block size must always be 128 bits in AES, and that the key size may be either 128, 192, or 256 bits. Therefore AES-128, AES-192, and AES-256 are actually:
Key Size (bits) Block Size (bits)
AES-128 128 128
AES-192 192 128
AES-256 256 128So in short:
Rijndael and AES differ only in the range of supported values for the block length and cipher key length.
For Rijndael, the block length and the key length can be independently specified to any multiple of 32 bits, with a minimum of 128 bits, and a maximum of 256 bits.
AES fixes the block length to 128 bits, and supports key lengths of 128, 192 or 256 bits only.
References used for this question:
http://blogs.msdn.com/b/shawnfa/archive/2006/10/09/the-differences-between-rijndael-and-aes.aspx
and
http://csrc.nist.gov/CryptoToolkit/aes/rijndael/Rijndael.pdf -
Which of the following is not a property of the Rijndael block cipher algorithm?
- It employs a round transformation that is comprised of three layers of distinct and invertible transformations.
- It is suited for high speed chips with no area restrictions.
- It operates on 64-bit plaintext blocks and uses a 128 bit key.
- It could be used on a smart card.
Explanation:All other properties above apply to the Rijndael algorithm, chosen as the AES standard to replace DES.
The AES algorithm is capable of using cryptographic keys of 128, 192, and 256 bits to encrypt and decrypt data in blocks of 128 bits. Rijndael was designed to handle additional block sizes and key lengths, however they are not adopted in the AES standard.
IDEA cipher algorithm operates on 64-bit plaintext blocks and uses a 128 bit key.
Reference(s) used for this question:
http://csrc.nist.gov/publications/fips/fips197/fips-197.pdf
and
http://en.wikipedia.org/wiki/Advanced_Encryption_Standard -
What algorithm has been selected as the AES algorithm, replacing the DES algorithm?
- RC6
- Twofish
- Rijndael
- Blowfish
Explanation:On October 2, 2000, NIST announced the selection of the Rijndael Block Cipher, developed by the Belgian cryptographers Dr. Joan Daemen and Dr. Vincent Rijmen, as the proposed AES algorithm. Twofish and RC6 were also candidates. Blowfish is also a symmetric algorithm but wasn’t a finalist for a replacement for DES.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 4: Cryptography (page 152).