SSCP : System Security Certified Practitioner (SSCP) : Part 06
-
A one-way hash provides which of the following?
- Confidentiality
- Availability
- Integrity
- Authentication
Explanation:
A one-way hash is a function that takes a variable-length string a message, and compresses and transforms it into a fixed length value referred to as a hash value. It provides integrity, but no confidentiality, availability or authentication.
Source: WALLHOFF, John, CBK#5 Cryptography (CISSP Study Guide), April 2002 (page 5). -
Which of the following statements pertaining to stream ciphers is correct?
- A stream cipher is a type of asymmetric encryption algorithm.
- A stream cipher generates what is called a keystream.
- A stream cipher is slower than a block cipher.
- A stream cipher is not appropriate for hardware-based encryption.
Explanation:A stream cipher is a type of symmetric encryption algorithm that operates on continuous streams of plain text and is appropriate for hardware-based encryption.
Stream ciphers can be designed to be exceptionally fast, much faster than any block cipher. A stream cipher generates what is called a keystream (a sequence of bits used as a key).
Stream ciphers can be viewed as approximating the action of a proven unbreakable cipher, the one-time pad (OTP), sometimes known as the Vernam cipher. A one-time pad uses a keystream of completely random digits. The keystream is combined with the plaintext digits one at a time to form the ciphertext. This system was proved to be secure by Claude Shannon in 1949. However, the keystream must be (at least) the same length as the plaintext, and generated completely at random. This makes the system very cumbersome to implement in practice, and as a result the one-time pad has not been widely used, except for the most critical applications.
A stream cipher makes use of a much smaller and more convenient key — 128 bits, for example. Based on this key, it generates a pseudorandom keystream which can be combined with the plaintext digits in a similar fashion to the one-time pad. However, this comes at a cost: because the keystream is now pseudorandom, and not truly random, the proof of security associated with the one-time pad no longer holds: it is quite possible for a stream cipher to be completely insecure if it is not implemented properly as we have seen with the Wired Equivalent Privacy (WEP) protocol.
Encryption is accomplished by combining the keystream with the plaintext, usually with the bitwise XOR operation.
Source: DUPUIS, Clement, CISSP Open Study Guide on domain 5, cryptography, April 1999.
More details can be obtained on Stream Ciphers in RSA Security’s FAQ on Stream Ciphers. -
Which of the following statements pertaining to block ciphers is incorrect?
- It operates on fixed-size blocks of plaintext.
- It is more suitable for software than hardware implementations.
- Plain text is encrypted with a public key and decrypted with a private key.
- Some Block ciphers can operate internally as a stream.
Explanation:Block ciphers do not use public cryptography (private and public keys).
Block ciphers is a type of symmetric-key encryption algorithm that transforms a fixed-size block of plaintext (unencrypted text) data into a block of ciphertext (encrypted text) data of the same length. They are appropriate for software implementations and can operate internally as a stream. See more info below about DES in Output Feedback Mode (OFB), which makes use internally of a stream cipher.The output feedback (OFB) mode makes a block cipher into a synchronous stream cipher. It generates keystream blocks, which are then XORed with the plaintext blocks to get the ciphertext. Just as with other stream ciphers, flipping a bit in the ciphertext produces a flipped bit in the plaintext at the same location. This property allows many error correcting codes to function normally even when applied before encryption.
Reference(s) used for this question:
Wikipedia on Block Cipher mode at: https://en.wikipedia.org/wiki/Block_cipher_mode_of_operation
and
http://www.itl.nist.gov/fipspubs/fip81.htm -
What principle focuses on the uniqueness of separate objects that must be joined together to perform a task? It is sometimes referred to as “what each must bring” and joined together when getting access or decrypting a file. Each of which does not reveal the other?
- Dual control
- Separation of duties
- Split knowledge
- Need to know
Explanation:Split knowledge involves encryption keys being separated into two components, each of which does not reveal the other. Split knowledge is the other complementary access control principle to dual control.
In cryptographic terms, one could say dual control and split knowledge are properly implemented if no one person has access to or knowledge of the content of the complete cryptographic key being protected by the two rocesses.
The sound implementation of dual control and split knowledge in a cryptographic environment necessarily means that the quickest way to break the key would be through the best attack known for the algorithm of that key. The principles of dual control and split knowledge primarily apply to access to plaintext keys.
Access to cryptographic keys used for encrypting and decrypting data or access to keys that are encrypted under a master key (which may or may not be maintained under dual control and split knowledge) do not require dual control and split knowledge. Dual control and split knowledge can be summed up as the determination of any part of a key being protected must require the collusion between two or more persons with each supplying unique cryptographic materials that must be joined together to access the protected key.
Any feasible method to violate the axiom means that the principles of dual control and split knowledge are not being upheld.
Split knowledge is the unique “what each must bring” and joined together when implementing dual control. To illustrate, a box containing petty cash is secured by one combination lock and one keyed lock. One employee is given the combination to the combo lock and another employee has possession of the correct key to the keyed lock.
In order to get the cash out of the box both employees must be present at the cash box at the same time. One cannot open the box without the other. This is the aspect of dual control.
On the other hand, split knowledge is exemplified here by the different objects (the combination to the combo lock and the correct physical key), both of which are unique and necessary, that each brings to the meeting. Split knowledge focuses on the uniqueness of separate objects that must be joined together.
Dual control has to do with forcing the collusion of at least two or more persons to combine their split knowledge to gain access to an asset. Both split knowledge and dual control complement each other and are necessary functions that implement the segregation of duties in high integrity cryptographic environments.
The following are incorrect answers:
Dual control is a procedure that uses two or more entities (usually persons) operating in concert to protect a system resource, such that no single entity acting alone can access that resource. Dual control is implemented as a security procedure that requires two or more persons to come together and collude to complete a process. In a cryptographic system the two (or more) persons would each supply a unique key, that when taken together, performs a cryptographic process. Split knowledge is the other complementary access control principle to dual control.Separation of duties – The practice of dividing the steps in a system function among different individuals, so as to keep a single individual from subverting the process.
The need-to-know principle requires a user having necessity for access to, knowledge of, or possession of specific information required to perform official tasks or services.Reference(s) used for this question:
Schneiter, Andrew (2013-04-15). Official (ISC)2 Guide to the CISSP CBK, Third Edition : Cryptography (Kindle Locations 1621-1635). . Kindle Edition.
and
Schneiter, Andrew (2013-04-15). Official (ISC)2 Guide to the CISSP CBK, Third Edition : Cryptography (Kindle Locations 1643-1650). . Kindle Edition.
and
Shon Harris, CISSP All In One (AIO), 6th Edition , page 126 -
What level of assurance for a digital certificate verifies a user’s name, address, social security number, and other information against a credit bureau database?
- Level 1/Class 1
- Level 2/Class 2
- Level 3/Class 3
- Level 4/Class 4
Explanation:Users can obtain certificates with various levels of assurance. Here is a list that describe each of them:
– Class 1/Level 1 for individuals, intended for email, no proof of identity
For example, level 1 certificates verify electronic mail addresses. This is done through the use of a personal information number that a user would supply when asked to register. This level of certificate may also provide a name as well as an electronic mail address; however, it may or may not be a genuine name (i.e., it could be an alias). This proves that a human being will reply back if you send an email to that name or email address.– Class 2/Level 2 is for organizations and companies for which proof of identity is required
Level 2 certificates verify a user’s name, address, social security number, and other information against a credit bureau database.– Class 3/Level 3 is for servers and software signing, for which independent verification and checking of identity and authority is done by the issuing certificate authority
Level 3 certificates are available to companies. This level of certificate provides photo identification to accompany the other items of information provided by a level 2 certificate.– Class 4 for online business transactions between companies
– Class 5 for private organizations or governmental securityReferences:
http://en.wikipedia.org/wiki/Digital_certificate veriSign introduced the concept of classes of digital certificates:
Also see:
Source: TIPTON, Harold F. & KRAUSE, Micki, Information Security Management Handbook, 4th edition (volume 1), 2000, CRC Press, Chapter 3, Secured Connections to External Networks (page 54). -
Which of the following is best at defeating frequency analysis?
- Substitution cipher
- Polyalphabetic cipher
- Transposition cipher
- Ceasar Cipher
Explanation:Simple substitution and transposition ciphers are vulnerable to attacks that perform frequency analysis.
In every language, there are words and patterns that are used more than others.Some patterns common to a language can actually help attackers figure out the transformation between plaintext and ciphertext, which enables them to figure out the key that was used to perform the transformation. Polyalphabetic ciphers use different alphabets to defeat frequency analysis.
The ceasar cipher is a very simple substitution cipher that can be easily defeated and it does show repeating letters.
Out of list presented, it is the Polyalphabetic cipher that would provide the best protection against simple frequency analysis attacks.
Source: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, McGraw-Hill/Osborne, 2002, Chapter 8: Cryptography (page 507).
And : DUPUIS, Clement, CISSP Open Study Guide on domain 5, cryptography, April 1999. -
A code, as is pertains to cryptography:
- Is a generic term for encryption.
- Is specific to substitution ciphers.
- Deals with linguistic units.
- Is specific to transposition ciphers.
Explanation:Historically, a code refers to a cryptosystem that deals with linguistic units: words, phrases, sentences, and so forth. Codes are only useful for specialized circumstances where the message to transmit has an already defined equivalent ciphertext word.
Source: DUPUIS, Cl?ment, CISSP Open Study Guide on domain 5, cryptography, April 1999. -
Cryptography does NOT help in:
- Detecting fraudulent insertion.
- Detecting fraudulent deletion.
- Detecting fraudulent modification.
- Detecting fraudulent disclosure.
Explanation:Cryptography is a detective control in the fact that it allows the detection of fraudulent insertion, deletion or modification. It also is a preventive control is the fact that it prevents disclosure, but it usually does not offers any means of detecting disclosure.
Source: DUPUIS, Clement, CISSP Open Study Guide on domain 5, cryptography, April 1999.
-
What is used to bind a document to its creation at a particular time?
- Network Time Protocol (NTP)
- Digital Signature
- Digital Timestamp
- Certification Authority (CA)
Explanation:While a digital signature binds a document to the possessor of a particular key, a digital timestamp binds a document to its creation at a particular time.
Trusted timestamping is the process of securely keeping track of the creation and modification time of a document. Security here means that no one — not even the owner of the document — should be able to change it once it has been recorded provided that the timestamper’s integrity is never compromised.
The administrative aspect involves setting up a publicly available, trusted timestamp management infrastructure to collect, process and renew timestamps or to make use of a commercially available time stamping service.
A modern example of using a Digital Timestamp is the case of an industrial research organization that may later need to prove, for patent purposes, that they made a particular discovery on a particular date; since magnetic media can be altered easily, this may be a nontrivial issue. One possible solution is for a researcher to compute and record in a hardcopy laboratory notebook a cryptographic hash of the relevant data file. In the future, should there be a need to prove the version of this file retrieved from a backup tape has not been altered, the hash function could be recomputed and compared with the hash value recorded in that paper notebook.
According to the RFC 3161 standard, a trusted timestamp is a timestamp issued by a trusted third party (TTP) acting as a Time Stamping Authority (TSA). It is used to prove the existence of certain data before a certain point (e.g. contracts, research data, medical records,…) without the possibility that the owner can backdate the timestamps. Multiple TSAs can be used to increase reliability and reduce vulnerability.
The newer ANSI ASC X9.95 Standard for trusted timestamps augments the RFC 3161 standard with data-level security requirements to ensure data integrity against a reliable time source that is provable to any third party. This standard has been applied to authenticating digitally signed data for regulatory compliance, financial transactions, and legal evidence.
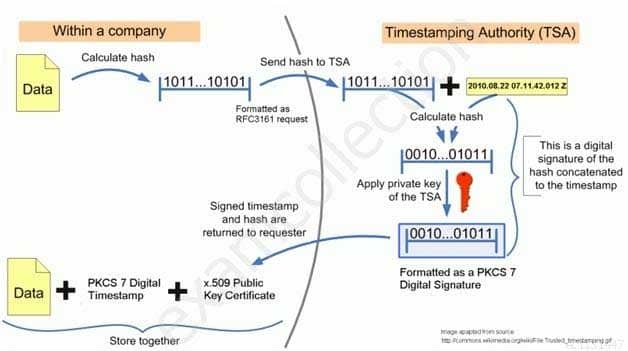
SSCP System Security Certified Practitioner (SSCP) Part 06 Q09 006 Digital TimeStamp
The following are incorrect answers:
Network Time Protocol (NTP) is used to achieve high accuracy time synchronization for computers across a network.
A Certification Authority (CA) is the entity responsible for the issuance of digital certificates.
A Digital Signature provides integrity and authentication but does not bind a document to a specific time it was created.Reference used for this question:
http://en.m.wikipedia.org/wiki/File:Trusted_timestamping.gif
and
http://en.wikipedia.org/wiki/Trusted_timestamping -
What is the effective key size of DES?
- 56 bits
- 64 bits
- 128 bits
- 1024 bits
Explanation:Data Encryption Standard (DES) is a symmetric key algorithm. Originally developed by IBM, under project name Lucifer, this 128-bit algorithm was accepted by the NIST in 1974, but the total key size was reduced to 64 bits, 56 of which make up the effective key, plus and extra 8 bits for parity. It somehow became a national cryptographic standard in 1977, and an American National Standard Institute (ANSI) standard in 1978. DES was later replaced by the Advanced Encryption Standard (AES) by the NIST.
Source: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, McGraw-Hill/Osborne, 2002, chapter 8: Cryptography (page 525).
-
Which of the following offers confidentiality to an e-mail message?
- The sender encrypting it with its private key.
- The sender encrypting it with its public key.
- The sender encrypting it with the receiver’s public key.
- The sender encrypting it with the receiver’s private key.
Explanation:An e-mail message’s confidentiality is protected when encrypted with the receiver’s public key, because he is the only one able to decrypt the message. The sender is not supposed to have the receiver’s private key. By encrypting a message with its private key, anybody possessing the corresponding public key would be able to read the message. By encrypting the message with its public key, not even the receiver would be able to read the message.
Source: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, McGraw-Hill/Osborne, 2002, chapter 8: Cryptography (page 517).
-
Which of the following standards concerns digital certificates?
- X.400
- X.25
- X.509
- X.75
Explanation:X.509 is used in digital certificates. X.400 is used in e-mail as a message handling protocol. X.25 is a standard for the network and data link levels of a communication network and X.75 is a standard defining ways of connecting two X.25 networks.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 4: Cryptography (page 164). -
Which of the following offers security to wireless communications?
- S-WAP
- WTLS
- WSP
- WDP
Explanation:Wireless Transport Layer Security (WTLS) is a communication protocol that allows wireless devices to send and receive encrypted information over the Internet. S-WAP is not defined. WSP (Wireless Session Protocol) and WDP (Wireless Datagram Protocol) are part of Wireless Access Protocol (WAP).
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 4: Cryptography (page 173).
-
Which of the following service is not provided by a public key infrastructure (PKI)?
- Access control
- Integrity
- Authentication
- Reliability
Explanation:A Public Key Infrastructure (PKI) provides confidentiality, access control, integrity, authentication and non-repudiation.
It does not provide reliability services.
Reference(s) used for this question:
TIPTON, Hal, (ISC)2, Introduction to the CISSP Exam presentation. -
In a Public Key Infrastructure, how are public keys published?
- They are sent via e-mail.
- Through digital certificates.
- They are sent by owners.
- They are not published.
Explanation:Public keys are published through digital certificates, signed by certification authority (CA), binding the certificate to the identity of its bearer.
A bit more details:
Although “Digital Certificates” is the best (or least wrong!) in the list of answers presented, for the past decade public keys have been published (ie: made known to the World) by the means of a LDAP server or a key distribution server (ex.: http://pgp.mit.edu/). An indirect publishing method is through OCSP servers (to validate digital signatures’ CRL)Reference used for this question:
TIPTON, Hal, (ISC)2, Introduction to the CISSP Exam presentation.
and
http://technet.microsoft.com/en-us/library/dd361898.aspx -
Which of the following is not a DES mode of operation?
- Cipher block chaining
- Electronic code book
- Input feedback
- Cipher feedback
Explanation:Output feedback (OFB) is a DES mode of operation, not input feedback.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 4: Cryptography (page 149).
-
What size is an MD5 message digest (hash)?
- 128 bits
- 160 bits
- 256 bits
- 128 bytes
Explanation:MD5 is a one-way hash function producing a 128-bit message digest from the input message, through 4 rounds of transformation. MD5 is specified as an Internet Standard (RFC1312).
Reference(s) used for this question:
TIPTON, Hal, (ISC)2, Introduction to the CISSP Exam presentation. -
Which of the following is the most secure form of triple-DES encryption?
- DES-EDE3
- DES-EDE1
- DES-EEE4
- DES-EDE2
Explanation:Triple DES with three distinct keys is the most secure form of triple-DES encryption. It can either be DES-EEE3 (encrypt-encrypt-encrypt) or DES-EDE3 (encrypt-decrypt-encrypt). DES-EDE1 is not defined and would mean using a single key to encrypt, decrypt and encrypt again, equivalent to single DES. DES-EEE4 is not defined and DES-EDE2 uses only 2 keys (encrypt with first key, decrypt with second key, encrypt with first key again).
Source: DUPUIS, Cl?ment, CISSP Open Study Guide on domain 5, cryptography, April 1999. -
Which of the following is not a disadvantage of symmetric cryptography when compared with Asymmetric Ciphers?
- Provides Limited security services
- Has no built in Key distribution
- Speed
- Large number of keys are needed
Explanation:Symmetric cryptography ciphers are generally fast and hard to break. So speed is one of the key advantage of Symmetric ciphers and NOT a disadvantage. Symmetric Ciphers uses simple encryption steps such as XOR, substitution, permutation, shifting columns, shifting rows, etc… Such steps does not required a large amount of processing power compare to the complex mathematical problem used within Asymmetric Ciphers.
Some of the weaknesses of Symmetric Ciphers are:
The lack of automated key distribution. Usually an Asymmetric cipher would be use to protect the symmetric key if it needs to be communicated to another entity securely over a public network. In the good old day this was done manually where it was distributed using the Floppy Net sometimes called the Sneaker Net (you run to someone’s office to give them the key).As far as the total number of keys are required to communicate securely between a large group of users, it does not scale very well. 10 users would require 45 keys for them to communicate securely with each other. If you have 1000 users then you would need almost half a million key to communicate secure. On Asymmetric ciphers there is only 2000 keys required for 1000 users. The formula to calculate the total number of keys required for a group of users who wishes to communicate securely with each others using Symmetric encryption is Total Number of Users (N) * Total Number of users minus one Divided by 2 or N (N-1)/2
Symmetric Ciphers are limited when it comes to security services, they cannot provide all of the security services provided by Asymmetric ciphers. Symmetric ciphers provides mostly confidentiality but can also provide integrity and authentication if a Message Authentication Code (MAC) is used and could also provide user authentication if Kerberos is used for example. Symmetric Ciphers cannot provide Digital Signature and Non-Repudiation.
Reference used for theis question:
WALLHOFF, John, CBK#5 Cryptography (CISSP Study Guide), April 2002 (page 2). -
Which of the following is more suitable for a hardware implementation?
- Stream ciphers
- Block ciphers
- Cipher block chaining
- Electronic code book
Explanation:A stream cipher treats the message as a stream of bits or bytes and performs mathematical functions on them individually. The key is a random value input into the stream cipher, which it uses to ensure the randomness of the keystream data. They are more suitable for hardware implementations, because they encrypt and decrypt one bit at a time. They are intensive because each bit must be manipulated, which works better at the silicon level. Block ciphers operate a the block level, dividing the message into blocks of bits. Cipher Block chaining (CBC) and Electronic Code Book (ECB) are operation modes of DES, a block encryption algorithm.
Source: WALLHOFF, John, CBK#5 Cryptography (CISSP Study Guide), April 2002 (page 2).