SSCP : System Security Certified Practitioner (SSCP) : Part 07
-
Which of the following would best describe a Concealment cipher?
- Permutation is used, meaning that letters are scrambled.
- Every X number of words within a text, is a part of the real message.
- Replaces bits, characters, or blocks of characters with different bits, characters or blocks.
- Hiding data in another message so that the very existence of the data is concealed.
Explanation:
When a concealment cipher is used, every X number of words within a text, is a part of the real message. The message is within another message.
A concealment cipher is a message within a message. If my other super-secret spy buddy and I decide our key value is every third word, then when I get a message from him, I will pick out every third word and write it down. Suppose he sends me a message that reads, “The saying, ‘The time is right’ is not cow language, so is now a dead subject.” Because my key is every third word, I come up with “The right cow is dead.” This again means nothing to me, and I am now turning in my decoder ring.
Concealment ciphers include the plaintext within the ciphertext. It is up to the recipient to know which letters or symbols to exclude from the ciphertext in order to yield the plaintext. Here is an example of a concealment cipher:
i2l32i5321k34e1245ch456oc12ol234at567eRemove all the numbers, and you’ll have i like chocolate. How about this one?
Larry even appears very excited. No one worries.
The first letter from each word reveals the message leave now. Both are easy, indeed, but many people have crafted more ingenious ways of concealing the messages. By the way, this type of cipher doesn’t even need ciphertext, such as that in the above examples.
Consider the invisible drying ink that kids use to send secret messages. In a more extreme example, a man named Histiaeus, during 5th century B.C., shaved the head of a trusted slave, then tattooed the message onto his bald head. When the slave’s hair grew back, Histiaeus sent the slave to the message’s intended recipient, Aristagoros, who shaved the slave’s head and read the message instructing him to revolt.
The following answers are incorrect:
A transposition cipher uses permutations.
A substitution cipher replaces bits, characters, or blocks of characters with different bits, characters or blocks.
Steganography refers to hiding the very existence of the message.Source: WALLHOFF, John, CBK#5 Cryptography (CISSP Study Guide), April 2002 (page 1).
and also see:
http://www.go4expert.com/forums/showthread.php?t=415 -
Which of the following is best provided by symmetric cryptography?
- Confidentiality
- Integrity
- Availability
- Non-repudiation
Explanation:When using symmetric cryptography, both parties will be using the same key for encryption and decryption. Symmetric cryptography is generally fast and can be hard to break, but it offers limited overall security in the fact that it can only provide confidentiality.
Source: WALLHOFF, John, CBK#5 Cryptography (CISSP Study Guide), April 2002 (page 2). -
Which of the following is not an example of a block cipher?
- Skipjack
- IDEA
- Blowfish
- RC4
Explanation:RC4 is a proprietary, variable-key-length stream cipher invented by Ron Rivest for RSA Data Security, Inc. Skipjack, IDEA and Blowfish are examples of block ciphers.
Source: SHIREY, Robert W., RFC2828: Internet Security Glossary, may 2000. -
The Diffie-Hellman algorithm is used for:
- Encryption
- Digital signature
- Key agreement
- Non-repudiation
Explanation:The Diffie-Hellman algorithm is used for Key agreement (key distribution) and cannot be used to encrypt and decrypt messages.
Source: WALLHOFF, John, CBK#5 Cryptography (CISSP Study Guide), April 2002 (page 4).Note: key agreement, is different from key exchange, the functionality used by the other asymmetric algorithms.
References:
AIO, third edition Cryptography (Page 632)
AIO, fourth edition Cryptography (Page 709) -
How many rounds are used by DES?
- 16
- 32
- 64
- 48
Explanation:DES is a block encryption algorithm using 56-bit keys and 64-bit blocks that are divided in half and each character is encrypted one at a time. The characters are put through 16 rounds of transposition and substitution functions. Triple DES uses 48 rounds.
Source: WALLHOFF, John, CBK#5 Cryptography (CISSP Study Guide), April 2002 (page 3). -
What is the key size of the International Data Encryption Algorithm (IDEA)?
- 64 bits
- 128 bits
- 160 bits
- 192 bits
Explanation:The International Data Encryption Algorithm (IDEA) is a block cipher that operates on 64 bit blocks of data with a 128-bit key. The data blocks are divided into 16 smaller blocks and each has eight rounds of mathematical functions performed on it. It is used in the PGP encryption software.
Source: WALLHOFF, John, CBK#5 Cryptography (CISSP Study Guide), April 2002 (page 3). -
Which of the following algorithms is a stream cipher?
- RC2
- RC4
- RC5
- RC6
Explanation:RC2, RC4, RC5 and RC6 were developed by Ronal Rivest from RSA Security.
In the RC family only RC4 is a stream cipher.
RC4 allows a variable key length.
RC2 works with 64-bit blocks and variable key lengths,
RC5 has variable block sizes, key length and number of processing rounds.
RC6 was designed to fix a flaw in RC5.
Source: ANDRESS, Mandy, Exam Cram CISSP, Coriolis, 2001, Chapter 6: Cryptography (page 103). -
In a SSL session between a client and a server, who is responsible for generating the master secret that will be used as a seed to generate the symmetric keys that will be used during the session?
- Both client and server
- The client’s browser
- The web server
- The merchant’s Certificate Server
Explanation:Once the merchant server has been authenticated by the browser client, the browser generates a master secret that is to be shared only between the server and client. This secret serves as a seed to generate the session (private) keys. The master secret is then encrypted with the merchant’s public key and sent to the server. The fact that the master secret is generated by the client’s browser provides the client assurance that the server is not reusing keys that would have been used in a previous session with another client.
Source: ANDRESS, Mandy, Exam Cram CISSP, Coriolis, 2001, Chapter 6: Cryptography (page 112).
Also: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, McGraw-Hill/Osborne, 2001, page 569. -
Which of the following is NOT a known type of Message Authentication Code (MAC)?
- Keyed-hash message authentication code (HMAC)
- DES-CBC
- Signature-based MAC (SMAC)
- Universal Hashing Based MAC (UMAC)
Explanation:There is no such thing as a Signature-Based MAC. Being the wrong choice in the list, it is the best answer to this question.
WHAT IS A Message Authentication Code (MAC)?
In Cryptography, a MAC (Message Authentication Code) also known as a cryptographic checksum, is a small block of data that is generated using a secret key and then appended to the message. When the message is received, the recipient can generate their own MAC using the secret key, and thereby know that the message has not changed either accidentally or intentionally in transit. Of course, this assurance is only as strong as the trust that the two parties have that no one else has access to the secret key.
A MAC is a small representation of a message and has the following characteristics:A MAC is much smaller than the message generating it.
Given a MAC, it is impractical to compute the message that generated it.
Given a MAC and the message that generated it, it is impractical to find another message generating the same MAC.See the graphic below from Wikipedia showing the creation of a MAC value:
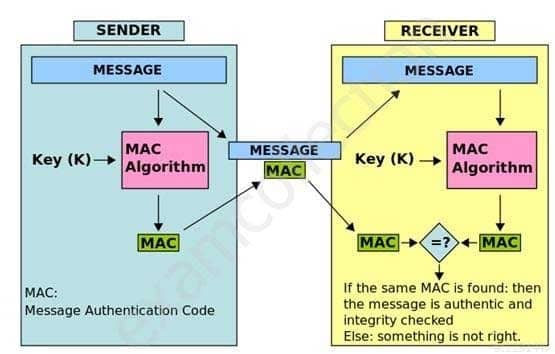
SSCP System Security Certified Practitioner (SSCP) Part 07 Q09 007 Message Authentication Code MAC HMAC
In the example above, the sender of a message runs it through a MAC algorithm to produce a MAC data tag. The message and the MAC tag are then sent to the receiver. The receiver in turn runs the message portion of the transmission through the same MAC algorithm using the same key, producing a second MAC data tag. The receiver then compares the first MAC tag received in the transmission to the second generated MAC tag. If they are identical, the receiver can safely assume that the integrity of the message was not compromised, and the message was not altered or tampered with during transmission.However, to allow the receiver to be able to detect replay attacks, the message itself must contain data that assures that this same message can only be sent once (e.g. time stamp, sequence number or use of a one-time MAC). Otherwise an attacker could — without even understanding its content — record this message and play it back at a later time, producing the same result as the original sender.
NOTE: There are many ways of producing a MAC value. Below you have a short list of some implementation.The following were incorrect answers for this question:
They were all incorrect answers because they are all real type of MAC implementation.
In the case of DES-CBC, a MAC is generated using the DES algorithm in CBC mode, and the secret DES key is shared by the sender and the receiver. The MAC is actually just the last block of ciphertext generated by the algorithm. This block of data (64 bits) is attached to the unencrypted message and transmitted to the far end. All previous blocks of encrypted data are discarded to prevent any attack on the MAC itself. The receiver can just generate his own MAC using the secret DES key he shares to ensure message integrity and authentication. He knows that the message has not changed because the chaining function of CBC would significantly alter the last block of data if any bit had changed anywhere in the message. He knows the source of the message (authentication) because only one other person holds the secret key.A Keyed-hash message authentication code (HMAC) is a specific construction for calculating a message authentication code (MAC) involving a cryptographic hash function in combination with a secret cryptographic key. As with any MAC, it may be used to simultaneously verify both the data integrity and the authentication of a message. Any cryptographic hash function, such as MD5, SHA-1, may be used in the calculation of an HMAC; the resulting MAC algorithm is termed HMAC-MD5 or HMAC-SHA1 accordingly. The cryptographic strength of the HMAC depends upon the cryptographic strength of the underlying hash function, the size of its hash output, and on the size and quality of the key.
A message authentication code based on universal hashing, or UMAC, is a type of message authentication code (MAC) calculated choosing a hash function from a class of hash functions according to some secret (random) process and applying it to the message. The resulting digest or fingerprint is then encrypted to hide the identity of the hash function used. As with any MAC, it may be used to simultaneously verify both the data integrity and the authenticity of a message. UMAC is specified in RFC 4418, it has provable cryptographic strength and is usually a lot less computationally intensive than other MACs.
What is the MicMac (confusion) with MIC and MAC?
The term message integrity code (MIC) is frequently substituted for the term MAC, especially in communications, where the acronym MAC traditionally stands for Media Access Control when referring to Networking. However, some authors use MIC as a distinctly different term from a MAC; in their usage of the term the MIC operation does not use secret keys. This lack of security means that any MIC intended for use gauging message integrity should be encrypted or otherwise be protected against tampering. MIC algorithms are created such that a given message will always produce the same MIC assuming the same algorithm is used to generate both. Conversely, MAC algorithms are designed to produce matching MACs only if the same message, secret key and initialization vector are input to the same algorithm. MICs do not use secret keys and, when taken on their own, are therefore a much less reliable gauge of message integrity than MACs. Because MACs use secret keys, they do not necessarily need to be encrypted to provide the same level of assurance.Reference(s) used for this question:
Hernandez CISSP, Steven (2012-12-21). Official (ISC)2 Guide to the CISSP CBK, Third Edition ((ISC)2 Press) (Kindle Locations 15799-15815). Auerbach Publications. Kindle Edition.
and
http://en.wikipedia.org/wiki/Message_authentication_code
and
http://tools.ietf.org/html/rfc4418 -
What is the maximum key size for the RC5 algorithm?
- 128 bits
- 256 bits
- 1024 bits
- 2040 bits
Explanation:RC5 is a fast block cipher created by Ron Rivest and analyzed by RSA Data Security, Inc.
It is a parameterized algorithm with a variable block size, a variable key size, and a variable number of rounds.
Allowable choices for the block size are 32 bits (for experimentation and evaluation purposes only), 64 bits (for use a drop-in replacement for DES), and 128 bits.
The number of rounds can range from 0 to 255, while the key can range from 0 bits to 2040 bits in size.
Please note that some sources such as the latest Shon Harris book mentions that RC5 maximum key size is of 2048, not 2040 bits. I would definitively use RSA as the authoritative source which specifies a key of 2040 bits. It is an error in Shon’s book.The OIG book says:
RC5 was developed by Ron Rivest of RSA and is deployed in many of RSA’s products. It is a very adaptable product useful for many applications, ranging from software to hardware implementations. The key for RC5 can vary from 0 to 2040 bits, the number of rounds it executes can be adjusted from 0 to 255, and the length of the input words can also be chosen from 16-, 32-, and 64-bit lengths.The following answers were incorrect choices:
All of the other answers were wrong.
Reference(s) used for this question:
Schneiter, Andrew (2013-04-15). Official (ISC)2 Guide to the CISSP CBK, Third Edition : Cryptography (Kindle Locations 1098-1101). . Kindle Edition.Harris, Shon (2012-10-25). CISSP All-in-One Exam Guide, 6th Edition (Kindle Locations 16744-16747). McGraw-Hill. Kindle Edition.
http://www.rsa.com/rsalabs/node.asp?id=2251, What are RC5 and RC6, RSA The Security Division of EMC.
From Rivest himself, see http://people.csail.mit.edu/rivest/Rivest-rc5rev.pdf
Also see the draft IETF IPSEC standard which clearly mention that it is in fact 2040 bits as a MAXIMUM key size:
http://www.tools.ietf.org/html/draft-ietf-ipsec-esp-rc5-cbc-00
http://en.wikipedia.org/wiki/RC5, Mention a maximum key size of 2040 as well. -
Which of the following is not an encryption algorithm?
- Skipjack
- SHA-1
- Twofish
- DEA
Explanation:The SHA-1 is a hashing algorithm producing a 160-bit hash result from any data. It does not perform encryption.
In cryptography, SHA-1 is a cryptographic hash function designed by the United States National Security Agency and published by the United States NIST as a U.S. Federal Information Processing Standard.
SHA stands for “secure hash algorithm”. The four SHA algorithms are structured differently and are distinguished as SHA-0, SHA-1, SHA-2, and SHA-3. SHA-1 is very similar to SHA-0, but corrects an error in the original SHA hash specification that led to significant weaknesses. The SHA-0 algorithm was not adopted by many applications. SHA-2 on the other hand significantly differs from the SHA-1 hash function.
SHA-1 is the most widely used of the existing SHA hash functions, and is employed in several widely used applications and protocols.
In 2005, cryptanalysts found attacks on SHA-1 suggesting that the algorithm might not be secure enough for ongoing use. NIST required many applications in federal agencies to move to SHA-2 after 2010 because of the weakness. Although no successful attacks have yet been reported on SHA-2, they are algorithmically similar to SHA-1.
In 2012, following a long-running competition, NIST selected an additional algorithm, Keccak, for standardization as SHA-3
NOTE:
A Cryptographic Hash Function is not the same as an Encryption Algorithm even thou both are Algorithms. An algorithm is defined as a step-by-step procedure for calculations. Hashing Algorithm do not encrypt the data. People sometimes will say they encrypted a password with SHA-1 but really they simply created a Message Digest of the password using SHA-1, putting the input through a series of steps to come out with the message digest or hash value.A cryptographic hash function is a hash function; that is, an algorithm that takes an arbitrary block of data and returns a fixed-size bit string, the (cryptographic) hash value, such that any (accidental or intentional) change to the data will (with very high probability) change the hash value. The data to be encoded are often called the “message,” and the hash value is sometimes called the message digest or simply digest.
Encryption Algorithms are reversible but Hashing Algorithms are not meant to be reversible if the input is large enough.
The following are incorrect answers:
The Skipjack algorithm is a Type II block cipher with a block size of 64 bits and a key size of 80 bits that was developed by NSA and formerly classified at the U.S. Department of Defense “Secret” level.
Twofish is a freely available 128-bit block cipher designed by Counterpane Systems (Bruce Schneier et al.).
DEA is a symmetric block cipher, defined as part of the U.S. Government’s Data Encryption Standard (DES). DEA uses a 64-bit key, of which 56 bits are independently chosen and 8 are parity bits, and maps a 64-bit block into another 64-bit block.
Reference(s) used for this question:
http://en.wikipedia.org/wiki/SHA-1
and
SHIREY, Robert W., RFC2828: Internet Security Glossary, may 2000.
and
Counterpane Labs, at http://www.counterpane.com/twofish.html. -
What key size is used by the Clipper Chip?
- 40 bits
- 56 bits
- 64 bits
- 80 bits
Explanation:The Clipper Chip is a NSA designed tamperproof chip for encrypting data and it uses the SkipJack algorithm. Each Clipper Chip has a unique serial number and a copy of the unit key is stored in the database under this serial number. The sending Clipper Chip generates and sends a Law Enforcement Access Field (LEAF) value included in the transmitted message. It is based on a 80-bit key and a 16-bit checksum.
Source: WALLHOFF, John, CBK#5 Cryptography (CISSP Study Guide), April 2002 (page 1). -
Which of the following is less likely to be used today in creating a Virtual Private Network?
- L2TP
- PPTP
- IPSec
- L2F
Explanation:L2F (Layer 2 Forwarding) provides no authentication or encryption. It is a Protocol that supports the creation of secure virtual private dial-up networks over the Internet.
At one point L2F was merged with PPTP to produce L2TP to be used on networks and not only on dial up links.
IPSec is now considered the best VPN solution for IP environments.
Source: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, McGraw-Hill/Osborne, 2002, Chapter 8: Cryptography (page 507).
-
Which of the following was not designed to be a proprietary encryption algorithm?
- RC2
- RC4
- Blowfish
- Skipjack
Explanation:Blowfish is a symmetric block cipher with variable-length key (32 to 448 bits) designed in 1993 by Bruce Schneier as an unpatented, license-free, royalty-free replacement for DES or IDEA. See attributes below:
Block cipher: 64-bit block
Variable key length: 32 bits to 448 bits
Designed by Bruce Schneier
Much faster than DES and IDEA
Unpatented and royalty-free
No license required
Free source code availableRivest Cipher #2 (RC2) is a proprietary, variable-key-length block cipher invented by Ron Rivest for RSA Data Security, Inc.
Rivest Cipher #4 (RC4) is a proprietary, variable-key-length stream cipher invented by Ron Rivest for RSA Data Security, Inc.
The Skipjack algorithm is a Type II block cipher [NIST] with a block size of 64 bits and a key size of 80 bits that was developed by NSA and formerly classified at the U.S. Department of Defense “Secret” level. The NSA announced on June 23, 1998, that Skipjack had been declassified.References:
RSA Laboratories
http://www.rsa.com/rsalabs/node.asp?id=2250RFC 2828 – Internet Security Glossary
http://www.faqs.org/rfcs/rfc2828.html -
The absence of a safeguard, or a weakness in a system that may possibly be exploited is called a(n)?
- Threat
- Exposure
- Vulnerability
- Risk
Explanation:A vulnerability is a weakness in a system that can be exploited by a threat.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, 2001, John Wiley & Sons, Page 237. -
Which of the following statements pertaining to disk mirroring is incorrect?
- Mirroring offers better performance in read operations but writing hinders system performance.
- Mirroring is a hardware-based solution only.
- Mirroring offers a higher fault tolerance than parity.
- Mirroring is usually the less cost-effective solution.
Explanation:With mirroring, the system writes the data simultaneously to separate drives or arrays.
The advantage of mirroring are minimal downtime, simple data recovery, and increased performance in reading from the disk.
The disadvantage of mirroring is that both drives or disk arrays are processing in the writing to disks function, which can hinder system performance.
Mirroring has a high fault tolerance and can be implemented either through a hardware RAID controller or through the operating system. Since it requires twice the disk space than actual data, mirroring is the less cost-efficient data redundancy strategy.
Source: SWANSON, Marianne, & al., National Institute of Standards and Technology (NIST), NIST Special Publication 800-34, Contingency Planning Guide for Information Technology Systems, December 2001 (page 45).
-
Which of the following is an example of an active attack?
- Traffic analysis
- Scanning
- Eavesdropping
- Wiretapping
Explanation:Scanning is definitively a very active attack. The attacker will make use of a scanner to perform the attack, the scanner will send a very large quantity of packets to the target in order to illicit responses that allows the attacker to find information about the operating system, vulnerabilities, misconfiguration and more. The packets being sent are sometimes attempting to identify if a known vulnerability exist on the remote hosts.
A passive attack is usually done in the footprinting phase of an attack. While doing your passive reconnaissance you never send a single packet to the destination target. You gather information from public databases such as the DNS servers, public information through search engines, financial information from finance web sites, and technical infomation from mailing list archive or job posting for example.
An attack can be active or passive.
An “active attack” attempts to alter system resources or affect their operation.A “passive attack” attempts to learn or make use of information from the system but does not affect system resources. (E.g., see: wiretapping.)
The following are all incorrect answers because they are all passive attacks:
Traffic Analysis – Is the process of intercepting and examining messages in order to deduce information from patterns in communication. It can be performed even when the messages are encrypted and cannot be decrypted. In general, the greater the number of messages observed, or even intercepted and stored, the more can be inferred from the traffic. Traffic analysis can be performed in the context of military intelligence or counter-intelligence, and is a concern in computer security.
Eavesdropping – Eavesdropping is another security risk posed to networks. Because of the way some networks are built, anything that gets sent out is broadcast to everyone. Under normal circumstances, only the computer that the data was meant for will process that information. However, hackers can set up programs on their computers called “sniffers” that capture all data being broadcast over the network. By carefully examining the data, hackers can often reconstruct real data that was never meant for them. Some of the most damaging things that get sniffed include passwords and credit card information.
In the cryptographic context, Eavesdropping and sniffing data as it passes over a network are considered passive attacks because the attacker is not affecting the protocol, algorithm, key, message, or any parts of the encryption system. Passive attacks are hard to detect, so in most cases methods are put in place to try to prevent them rather than to detect and stop them. Altering messages, modifying system files, and masquerading as another individual are acts that are considered active attacks because the attacker is actually doing something instead of sitting back and gathering data. Passive attacks are usually used to gain information prior to carrying out an active attack.”
Wiretapping – Wiretapping refers to listening in on electronic communications on telephones, computers, and other devices. Many governments use it as a law enforcement tool, and it is also used in fields like corporate espionage to gain access to privileged information. Depending on where in the world one is, wiretapping may be tightly controlled with laws that are designed to protect privacy rights, or it may be a widely accepted practice with little or no protections for citizens. Several advocacy organizations have been established to help civilians understand these laws in their areas, and to fight illegal wiretapping.
Reference(s) used for this question:
HARRIS, Shon, All-In-One CISSP Certification Exam Guide, 6th Edition, Cryptography, Page 865
and
http://en.wikipedia.org/wiki/Attack_%28computing%29
and
http://www.wisegeek.com/what-is-wiretapping.htm
and
https://pangea.stanford.edu/computing/resources/network/security/risks.php
and
http://en.wikipedia.org/wiki/Traffic_analysis -
What can be defined as a momentary low voltage?
- Spike
- Sag
- Fault
- Brownout
Explanation:A sag is a momentary low voltage. A spike is a momentary high voltage. A fault is a momentary power out and a brownout is a prolonged power supply that is below normal voltage.
Source: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, McGraw-Hill/Osborne, 2002, chapter 6: Physical security (page 299) -
A contingency plan should address:
- Potential risks.
- Residual risks.
- Identified risks.
- All answers are correct.
Explanation:Because it is rarely possible or cost effective to eliminate all risks, an attempt is made to reduce risks to an acceptable level through the risk assessment process. This process allows, from a set of potential risks (whether likely or not), to come up with a set of identified, possible risks.
The implementation of security controls allows reducing the identified risks to a smaller set of residual risks. Because these residual risks represent the complete set of situations that could affect system performance, the scope of the contingency plan may be reduced to address only this decreased risk set.
As a result, the contingency plan can be narrowly focused, conserving resources while ensuring an effective system recovery capability.
Source: SWANSON, Marianne, & al., National Institute of Standards and Technology (NIST), NIST Special Publication 800-34, Contingency Planning Guide for Information Technology Systems, December 2001 (page 7). -
Which of the following focuses on sustaining an organization’s business functions during and after a disruption?
- Business continuity plan
- Business recovery plan
- Continuity of operations plan
- Disaster recovery plan
Explanation:A business continuity plan (BCP) focuses on sustaining an organization’s business functions during and after a disruption. Information systems are considered in the BCP only in terms of their support to the larger business processes. The business recovery plan (BRP) addresses the restoration of business processes after an emergency. The BRP is similar to the BCP, but it typically lacks procedures to ensure continuity of critical processes throughout an emergency or disruption. The continuity of operations plan (COOP) focuses on restoring an organization’s essential functions at an alternate site and performing those functions for up to 30 days before returning to normal operations. The disaster recovery plan (DRP) applies to major, usually catastrophic events that deny access to the normal facility for an extended period. A DRP is narrower in scope than an IT contingency plan in that it does not address minor disruptions that do not require relocation.
Source: SWANSON, Marianne, & al., National Institute of Standards and Technology (NIST), NIST Special Publication 800-34, Contingency Planning Guide for Information Technology Systems, December 2001 (page 8).