SSCP : System Security Certified Practitioner (SSCP) : Part 20
-
Which of the following protocols operates at the session layer (layer 5)?
- RPC
- IGMP
- LPD
- SPX
Explanation:
Remotre Procedure Call (RPC) is the only of the above choices to operate at the session layer (layer 5).
All of the other answers were wrong.
LPD operates at layer 7
SPX operates at layer 4
IGMP operates at layer 3.Reference:
WALLHOFF, John, CBK#2 Telecommunications and Network Security (CISSP Study Guide), April 2002 (page 1). -
Which layer of the TCP/IP protocol stack corresponds to the ISO/OSI Network layer (layer 3)?
- Host-to-host layer
- Internet layer
- Network access layer
- Session layer
Explanation:The Internet layer in the TCP/IP protocol stack corresponds to the network layer (layer 3) in the OSI/ISO model. The host-to-host layer corresponds to the transport layer (layer 4) in the OSI/ISO model. The Network access layer corresponds to the data link and physical layers (layers 2 and 1) in the OSI/ISO model. The session layer is not defined in the TCP/IP protocol stack.
Source: WALLHOFF, John, CBK#2 Telecommunications and Network Security (CISSP Study Guide), April 2002 (page 1).
-
How many bits of a MAC address uniquely identify a vendor, as provided by the IEEE?
- 6 bits
- 12 bits
- 16 bits
- 24 bits
Explanation:The MAC address is 48 bits long, 24 of which identify the vendor, as provided by the IEEE. The other 24 bits are provided by the vendor.
A media access control address (MAC address) is a unique identifier assigned to network interfaces for communications on the physical network segment. MAC addresses are used for numerous network technologies and most IEEE 802 network technologies, including Ethernet. Logically, MAC addresses are used in the media access control protocol sublayer of the OSI reference model.
MAC addresses are most often assigned by the manufacturer of a network interface card (NIC) and are stored in its hardware, such as the card’s read-only memory or some other firmware mechanism. If assigned by the manufacturer, a MAC address usually encodes the manufacturer’s registered identification number and may be referred to as the burned-in address. It may also be known as an Ethernet hardware address (EHA), hardware address or physical address. This is can be contrasted to a programmed address, where the host device issues commands to the NIC to use an arbitrary address. An example is many SOHO routers, where the ISP grants access to only one MAC address (used previously to inserting the router) so the router must use that MAC address on its Internet-facing NIC. Therefore the router administrator configures a MAC address to override the burned-in one.
A network node may have multiple NICs and each must have one unique MAC address per NIC.
See diagram below from Wikipedia showing the format of a MAC address. :
MAC Address format
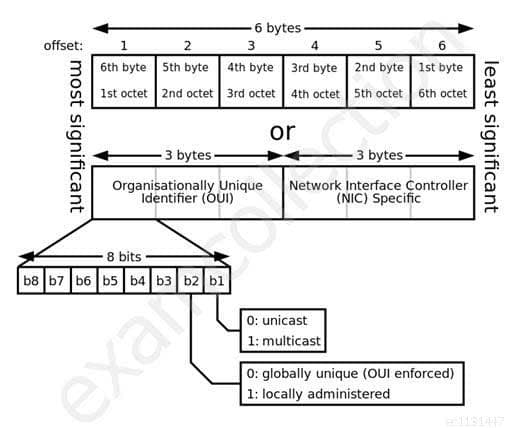
SSCP System Security Certified Practitioner (SSCP) Part 20 Q03 010 Reference(s) used for this question:
http://en.wikipedia.org/wiki/MAC_address -
Which Network Address Translation (NAT) is the most convenient and secure solution?
- Hiding Network Address Translation
- Port Address Translation
- Dedicated Address Translation
- Static Address Translation
Explanation:Static network address translation offers the most flexibility, but it is not normally practical given the shortage of IP version 4 addresses. Hiding network address translation is was an interim step in the development of network address translation technology, and is seldom used because port address translation offers additional features above and beyond those present in hiding network address translation while maintaining the same basic design and engineering considerations. PAT is often the most convenient and secure solution.
Source: WACK, John et al., NIST Special publication 800-41, Guidelines on Firewalls and Firewall Policy, January 2002 (page 18).
-
The Logical Link Control sub-layer is a part of which of the following?
- The ISO/OSI Data Link layer
- The Reference monitor
- The Transport layer of the TCP/IP stack model
- Change management control
Explanation:The OSI/ISO Data Link layer is made up of two sub-layers; (1) the Media Access Control layer refers downward to lower layer hardware functions and (2) the Logical Link Control refers upward to higher layer software functions. Other choices are distracters.
Source: ROTHKE, Ben, CISSP CBK Review presentation on domain 2, August 1999.
-
Which of the following services relies on UDP?
- FTP
- Telnet
- DNS
- SMTP
Explanation:DNS relies on connectionless UDP whereas services like FTP, Telnet and SMTP rely on TCP.
Source: ROTHKE, Ben, CISSP CBK Review presentation on domain 2, August 1999.
-
Which of the following statements pertaining to link encryption is false?
- It encrypts all the data along a specific communication path.
- It provides protection against packet sniffers and eavesdroppers.
- Information stays encrypted from one end of its journey to the other.
- User information, header, trailers, addresses and routing data that are part of the packets are encrypted.
Explanation:When using link encryption, packets have to be decrypted at each hop and encrypted again.
Information staying encrypted from one end of its journey to the other is a characteristic of end-to-end encryption, not link encryption.
Link Encryption vs. End-to-End EncryptionLink encryption encrypts the entire packet, including headers and trailers, and has to be decrypted at each hop.
End-to-end encryption does not encrypt the IP Protocol headers, and therefore does not need to be decrypted at each hop.
Reference: All in one, Page 735 & Glossary
and
Source: WALLHOFF, John, CBK#5 Cryptography (CISSP Study Guide), April 2002 (page 6). -
Which of the following statements pertaining to firewalls is incorrect?
- Firewalls create bottlenecks between the internal and external network.
- Firewalls allow for centralization of security services in machines optimized and dedicated to the task.
- Firewalls protect a network at all layers of the OSI models.
- Firewalls are used to create security checkpoints at the boundaries of private networks.
Explanation:Firewalls can protect a network at multiple layers of the OSI models, however most of the firewalls do not have the ability to monitor the payload of the packets and see if an application level attack is taking place.
Today there are a new breed of firewall called Unified Threat Managers or UTM. They are a collection of products on a single computer and not necessarily a typical firewall. A UTM can address all of the layers but typically a firewall cannot.
Firewalls are security checkpoints at the boundaries of internal networks through which every packet must pass and be inspected, hence they create bottlenecks between the internal and external networks. But since external connections are relatively slow compared to modern computers, the latency caused by this bottleneck can almost be transparent.
By implementing the concept of border security, they centralize security services in machines optimized and dedicated to the task, thus relieving the other hosts on the network from that function.
Source: STREBE, Matthew and PERKINS, Charles, Firewalls 24seven, Sybex 2000, Chapter 1: Understanding Firewalls.
-
Which of the following ports does NOT normally need to be open for a mail server to operate?
- Port 110
- Port 25
- Port 119
- Port 143
Explanation:Port 119 is normally used for the Network News Transfer Protocol. It is thus not need for a mail server, which would normally listen to ports 25 (SMTP), 110 (POP3) and 143 (IMAP).
Source: STREBE, Matthew and PERKINS, Charles, Firewalls 24seven, Sybex 2000, Chapter 1: Understanding Firewalls. -
Which of the following statements is NOT true of IPSec Transport mode?
- It is required for gateways providing access to internal systems
- Set-up when end-point is host or communications terminates at end-points
- If used in gateway-to-host communication, gateway must act as host
- When ESP is used for the security protocol, the hash is only applied to the upper layer protocols contained in the packet
Explanation:Source: TIPTON, Harold F. & KRAUSE, MICKI, Information Security Management Handbook, 4th Edition, Volume 2, 2001, CRC Press, NY, Pages 166-167. -
All following observations about IPSec are correct except:
- Default Hashing protocols are HMAC-MD5 or HMAC-SHA-1
- Default Encryption protocol is Cipher Block Chaining mode DES, but other algorithms like ECC (Elliptic curve cryptosystem) can be used
- Support two communication modes – Tunnel mode and Transport mode
- Works only with Secret Key Cryptography
Explanation:Source: TIPTON, Harold F. & KRAUSE, MICKI, Information Security Management Handbook, 4th Edition, Volume 2, 2001, CRC Press, NY, Pages 166-167. -
Which of the following is the primary reason why a user would choose a dial-up modem connection to the Internet when they have a faster, secure Internet connection through the organization’s network?
- To access web sites that blocked by the organization’s proxy server.
- To set up public services using the organization’s resources.
- To check their personal e-mail.
- To circumvent the organization’s security policy.
Explanation:All the choices above represent examples of circumventing the organization’s security policy, which is the primary reason why a user would be using a dial-up Internet connection when a secure connection is available through the organization’s network.
Source: STREBE, Matthew and PERKINS, Charles, Firewalls 24seven, Sybex 2000, Chapter 1: Understanding Firewalls. -
Which of the following can best eliminate dial-up access through a Remote Access Server as a hacking vector?
- Using a TACACS+ server.
- Installing the Remote Access Server outside the firewall and forcing legitimate users to authenticate to the firewall.
- Setting modem ring count to at least 5.
- Only attaching modems to non-networked hosts.
Explanation:Containing the dial-up problem is conceptually easy: by installing the Remote Access Server outside the firewall and forcing legitimate users to authenticate to the firewall, any access to internal resources through the RAS can be filtered as would any other connection coming from the Internet.
The use of a TACACS+ Server by itself cannot eliminate hacking.
Setting a modem ring count to 5 may help in defeating war-dialing hackers who look for modem by dialing long series of numbers.
Attaching modems only to non-networked hosts is not practical and would not prevent these hosts from beiIP Spoofingng hacked.
Source: STREBE, Matthew and PERKINS, Charles, Firewalls 24seven, Sybex 2000, Chapter 2: Hackers.
-
Which of the following is an extension to Network Address Translation that permits multiple devices providing services on a local area network (LAN) to be mapped to a single public IP address?
- IP Spoofing
- IP subnetting
- Port address translation
- IP Distribution
Explanation:Port Address Translation (PAT), is an extension to network address translation (NAT) that permits multiple devices on a local area network (LAN) to be mapped to a single public IP address. The goal of PAT is to conserve IP addresses or to publish multiple hosts with service to the internet while having only one single IP assigned on the external side of your gateway.
Most home networks use PAT. In such a scenario, the Internet Service Provider (ISP) assigns a single IP address to the home network’s router. When Computer X logs on the Internet, the router assigns the client a port number, which is appended to the internal IP address. This, in effect, gives Computer X a unique address. If Computer Z logs on the Internet at the same time, the router assigns it the same local IP address with a different port number. Although both computers are sharing the same public IP address and accessing the Internet at the same time, the router knows exactly which computer to send specific packets to because each computer has a unique internal address.
Port Address Translation is also called porting, port overloading, port-level multiplexed NAT and single address NAT.
Shon Harris has the following example in her book:
The company owns and uses only one public IP address for all systems that need to communicate outside the internal network. How in the world could all computers use the exact same IP address? Good question. Here’s an example: The NAT device has an IP address of 127.50.41.3. When computer A needs to communicate with a system on the Internet, the NAT device documents this computer’s private address and source port number (10.10.44.3; port 43,887). The NAT device changes the IP address in the computer’s packet header to 127.50.41.3, with the source port 40,000. When computer B also needs to communicate with a system on the Internet, the NAT device documents the private address and source port number (10.10.44.15; port 23,398) and changes the header information to 127.50.41.3 with source port 40,001. So when a system responds to computer A, the packet first goes to the NAT device, which looks up the port number 40,000 and sees that it maps to computer A’s real information. So the NAT device changes the header information to address 10.10.44.3 and port 43,887 and sends it to computer A for processing. A company can save a lot more money by using PAT, because the company needs to buy only a few public IP addresses, which are used by all systems in the network.As mentioned on Wikipedia:
NAT is also known as Port Address Translation: is a feature of a network device that translate TCP or UDP communications made between host on a private network and host on a public network. I allows a single public IP address to be used by many host on private network which is usually a local area network LANNAT effectively hides all TCP/IP-level information about internal hosts from the Internet.
The following were all incorrect answer:
IP Spoofing – In computer networking, the term IP address spoofing or IP spoofing refers to the creation of Internet Protocol (IP) packets with a forged source IP address, called spoofing, with the purpose of concealing the identity of the sender or impersonating another computing system.
Subnetting – Subnetting is a network design strategy that segregates a larger network into smaller components. While connected through the larger network, each subnetwork or subnet functions with a unique IP address. All systems that are assigned to a particular subnet will share values that are common for both the subnet and for the network as a whole.
A different approach to network construction can be thought of as subnetting in reverse. Known as CIDR, or Classless Inter-Domain Routing, this approach also creates a series of subnetworks. Rather than dividing an existing network into small components, CIDR takes smaller components and connects them into a larger network. This can often be the case when a business is acquired by a larger corporation. Instead of doing away with the network developed and used by the newly acquired business, the corporation chooses to continue operating that network as a subsidiary or an added component of the corporation’s network. In effect, the system of the purchased entity becomes a subnet of the parent company’s network.
IP Distribution – This is a generic term which could mean distribution of content over an IP network or distribution of IP addresses within a Company. Sometimes people will refer to this as Internet Protocol address management (IPAM) is a means of planning, tracking, and managing the Internet Protocol address space used in a network. Most commonly, tools such as DNS and DHCP are used in conjunction as integral functions of the IP address management function, and true IPAM glues these point services together so that each is aware of changes in the other (for instance DNS knowing of the IP address taken by a client via DHCP, and updating itself accordingly). Additional functionality, such as controlling reservations in DHCP as well as other data aggregation and reporting capability, is also common. IPAM tools are increasingly important as new IPv6 networks are deployed with larger address pools, different subnetting techniques, and more complex 128-bit hexadecimal numbers which are not as easily human-readable as IPv4 addresses.
Reference(s) used for this question:
STREBE, Matthew and PERKINS, Charles, Firewalls 24seven, Sybex 2000, Chapter 1: Understanding Firewalls.Schneiter, Andrew (2013-04-15). Official (ISC)2 Guide to the CISSP CBK, Third Edition : Telecommunications and Network Security, Page 350.
Harris, Shon (2012-10-25). CISSP All-in-One Exam Guide, 6th Edition (Kindle Locations 12765-12774). Telecommunications and Network Security, Page 604-606
http://searchnetworking.techtarget.com/definition/Port-Address-Translation-PAT
http://en.wikipedia.org/wiki/IP_address_spoofing
http://www.wisegeek.com/what-is-subnetting.htm
http://en.wikipedia.org/wiki/IP_address_management -
At which OSI/ISO layer is an encrypted authentication between a client software package and a firewall performed?
- Network layer
- Session layer
- Transport layer
- Data link layer
Explanation:
Encrypted authentication is a firewall feature that allows users on an external network to authenticate themselves to prove that they are authorized to access resources on the internal network. Encrypted authentication is convenient because it happens at the transport layer between a client software and a firewall, allowing all normal application software to run without hindrance.
Source: STREBE, Matthew and PERKINS, Charles, Firewalls 24seven, Sybex 2000, Chapter 1: Understanding Firewalls. -
Which of the following is a method of multiplexing data where a communication channel is divided into an arbitrary number of variable bit-rate digital channels or data streams. This method allocates bandwidth dynamically to physical channels having information to transmit?
- Time-division multiplexing
- Asynchronous time-division multiplexing
- Statistical multiplexing
- Frequency division multiplexing
Explanation:Statistical multiplexing is a type of communication link sharing, very similar to dynamic bandwidth allocation (DBA). In statistical multiplexing, a communication channel is divided into an arbitrary number of variable bit-rate digital channels or data streams. The link sharing is adapted to the instantaneous traffic demands of the data streams that are transferred over each channel. This is an alternative to creating a fixed sharing of a link, such as in general time division multiplexing (TDM) and frequency division multiplexing (FDM). When performed correctly, statistical multiplexing can provide a link utilization improvement, called the statistical multiplexing gain.
Generally, the methods for multiplexing data include the following :
Time-division multiplexing (TDM): information from each data channel is allocated bandwidth based on pre-assigned time slots, regardless of whether there is data to transmit. Time-division multiplexing is used primarily for digital signals, but may be applied in analog multiplexing in which two or more signals or bit streams are transferred appearing simultaneously as sub-channels in one communication channel, but are physically taking turns on the channel. The time domain is divided into several recurrent time slots of fixed length, one for each sub-channel. A sample byte or data block of sub-channel 1 is transmitted during time slot 1, sub-channel 2 during time slot 2, etc. One TDM frame consists of one time slot per sub-channel plus a synchronization channel and sometimes error correction channel before the synchronization. After the last sub-channel, error correction, and synchronization, the cycle starts all over again with a new frame, starting with the second sample, byte or data block from sub-channel 1, etc.
Asynchronous time-division multiplexing (ATDM): information from data channels is allocated bandwidth as needed, via dynamically assigned time slots. ATM provides functionality that is similar to both circuit switching and packet switching networks: ATM uses asynchronous time-division multiplexing, and encodes data into small, fixed-sized packets (ISO-OSI frames) called cells. This differs from approaches such as the Internet Protocol or Ethernet that use variable sized packets and frames. ATM uses a connection-oriented model in which a virtual circuit must be established between two endpoints before the actual data exchange begins. These virtual circuits may be “permanent”, i.e. dedicated connections that are usually preconfigured by the service provider, or “switched”, i.e. set up on a per-call basis using signalling and disconnected when the call is terminated.
Frequency division multiplexing (FDM): information from each data channel is allocated bandwidth based on the signal frequency of the traffic. In telecommunications, frequency-division multiplexing (FDM) is a technique by which the total bandwidth available in a communication medium is divided into a series of non-overlapping frequency sub-bands, each of which is used to carry a separate signal. This allows a single transmission medium such as the radio spectrum, a cable or optical fiber to be shared by many signals.
Reference used for this question:
http://en.wikipedia.org/wiki/Statistical_multiplexing
and
http://en.wikipedia.org/wiki/Frequency_division_multiplexing
and
Information Systems Audit and Control Association, Certified Information Systems Auditor 2002 review manual, Chapter 3: Technical Infrastructure and Operational Practices (page 114). -
Which of the following is NOT a defined ISO basic task related to network management?
- Fault management
- Accounting resources
- Security management
- Communications management
Explanation:ISO has defined five basic tasks related to network management :
Fault management: Detects the devices that present some kind of fault.
Configuration management: Allows users to know, define and change remotely the configuration of any device.
Accounting resources: Holds the records of the resource usage in the WAN.
Performance management: Monitors usage levels and sets alarms when a threshold has been surpassed.
Security management: Detects suspicious traffic or users and generates alarms accordingly.Source: Information Systems Audit and Control Association, Certified Information Systems Auditor 2002 review manual, Chapter 3: Technical Infrastructure and Operational Practices (page 137).
-
Which of the following statements pertaining to packet filtering is incorrect?
- It is based on ACLs.
- It is not application dependant.
- It operates at the network layer.
- It keeps track of the state of a connection.
Explanation:Packet filtering is used in the first generation of firewalls and does not keep track of the state of a connection. Stateful packet filtering does.
Source: WALLHOFF, John, CISSP Summary 2002, April 2002, CBK#2 Telecommunications and Network Security (page 6) -
Which of the following best defines source routing?
- The packets hold the forwarding information so they don’t need to let bridges and routers decide what is the best route or way to get to the destination.
- The packets hold source information in a fashion that source address cannot be forged.
- The packets are encapsulated to conceal source information.
- The packets hold information about redundant paths in order to provide a higher reliability.
Explanation:With source routing, the packets hold the forwarding information so that they can find their way to the destination themselves without bridges and routers dictating their paths.
In computer networking, source routing allows a sender of a packet to specify the route the packet takes through the network.
With source routing the entire path to the destination is known to the sender and is included when sending data. Source routing differs from most other routing in that the source makes most or all of the routing decisions for each router along the way.
Source:
WALLHOFF, John, CISSP Summary 2002, April 2002, CBK#2 Telecommunications and Network Security (page 5)Wikipedia at http://en.wikipedia.org/wiki/Dynamic_Source_Routing
-
Encapsulating Security Payload (ESP) provides some of the services of Authentication Headers (AH), but it is primarily designed to provide:
- Confidentiality
- Cryptography
- Digital signatures
- Access Control
Explanation:Source: TIPTON, Harold F. & KRAUSE, MICKI, Information Security Management Handbook, 4th Edition, Volume 2, 2001, CRC Press, NY, page 164.