SSCP : System Security Certified Practitioner (SSCP) : Part 24
-
Which one of the following is usually not a benefit resulting from the use of firewalls?
- reduces the risks of external threats from malicious hackers.
- prevents the spread of viruses.
- reduces the threat level on internal system.
- allows centralized management and control of services.
Explanation:
This is not a benefit of a firewall. Most firewalls are limited when it comes to preventing the spread of viruses.
This question is testing your knowledge of Malware and Firewalls. The keywords within the questions are “usually” and “virus”. Once again to come up with the correct answer, you must stay within the context of the question and really ask yourself which of the 4 choices is NOT usually done by a firewall.
Some of the latest Appliances such as Unified Threat Management (UTM) devices does have the ability to do virus scanning but most first and second generation firewalls would not have such ability. Remember, the questions is not asking about all possible scenarios that could exist but only about which of the 4 choices presented is the BEST.
For the exam you must know your general classes of Malware. There are generally four major classes of malicious code that fall under the general definition of malware:
1. Virus: Parasitic code that requires human action or insertion, or which attaches itself to another program to facilitate replication and distribution. Virus-infected containers can range from e-mail, documents, and data file macros to boot sectors, partitions, and memory fobs. Viruses were the first iteration of malware and were typically transferred by floppy disks (also known as “sneakernet”) and injected into memory when the disk was accessed or infected files were transferred from system to system.
2. Worm: Self-propagating code that exploits system or application vulnerabilities to replicate. Once on a system, it may execute embedded routines to alter, destroy, or monitor the system on which it is running, then move on to the next system. A worm is effectively a virus that does not require human interaction or other programs to infect systems.
3. Trojan Horse: Named after the Trojan horse of Greek mythology (and serving a very similar function), a Trojan horse is a general term referring to programs that appear desirable, but actually contain something harmful. A Trojan horse purports to do one thing that the user wants while secretly performing other potentially malicious actions. For example, a user may download a game file, install it, and begin playing the game. Unbeknownst to the user, the application may also install a virus, launch a worm, or install a utility allowing an attacker to gain unauthorized access to the system remotely, all without the user’s knowledge.
4. Spyware: Prior to its use in malicious activity, spyware was typically a hidden application injected through poor browser security by companies seeking to gain more information about a user’s Internet activity. Today, those methods are used to deploy other malware, collect private data, send advertising or commercial messages to a system, or monitor system input, such as keystrokes or mouse clicks.
The following answers are incorrect:
reduces the risks of external threats from malicious hackers. This is incorrect because a firewall can reduce the risks of external threats from malicious hackers.
reduces the threat level on internal system. This is incorrect because a firewall can reduce the threat level on internal system.
allows centralized management and control of services. This is incorrect because a firewall can allow centralize management and control of services.
Reference(s) used for this question:
Hernandez CISSP, Steven (2012-12-21). Official (ISC)2 Guide to the CISSP CBK, Third Edition ((ISC)2 Press) (Kindle Locations 3989-4009). Auerbach Publications. Kindle Edition. -
Which of the following OSI layers provides routing and related services?
- Network Layer
- Presentation Layer
- Session Layer
- Physical Layer
Explanation:The Network Layer performs network routing functions.
The following answers are incorrect:
Presentation Layer. Is incorrect because the Presentation Layer transforms the data to provide a standard interface for the Application layer.
Session Layer. Is incorrect because the Session Layer controls the dialogues/connections (sessions) between computers.
Physical Layer. is incorrect because the Physical Layer defines all the electrical and physical specifications for devices.
-
You are running a packet sniffer on a network and see a packet containing a long string of “0x90 0x90 0x90 0x90….” in the middle of it traveling to an x86-based machine as a target. This could be indicative of what activity being attempted?
- Over-subscription of the traffic on a backbone.
- A source quench packet.
- A FIN scan.
- A buffer overflow attack.
Explanation:A series of the same control characters, hexadecimal code, imbedded in the string is usually an indicator of a buffer overflow attack.
The Intel x86 processors use the hexadecimal number 90 to represent NOP (no operation). Many buffer overflow attacks use long strings of control characters and this is representative of that type of attack.
A buffer overflow takes place when too much data are accepted as input to a specific process. A buffer is an allocated segment of memory. A buffer can be overflowed arbitrarily with too much data, but for it to be of any use to an attacker, the code inserted into the buffer must be of a specific length, followed up by commands the attacker wants executed. So, the purpose of a buffer overflow may be either to make a mess, by shoving arbitrary data into various memory segments, or to accomplish a specific task, by pushing into the memory segment a carefully crafted set of data that will accomplish a specific task. This task could be to open a command shell with administrative privilege or execute malicious code.
Common threats to system availability, integrity, and confidentiality include hardware failure, misuse of system privileges, buffer overflows and other memory attacks, denial of service, reverse engineering, and system hacking.
Since many vulnerabilities result from insecure design and most threats are well known, it is the responsibility of the security architect to ensure that their designs are addressing security requirements appropriately while also ensuring that the system can continue to perform its intended function.
The following answers are incorrect:
Over-subscription of the traffic on a backbone. Is incorrect because if there was Over-subscription of the traffic on a backbone, that would typically result in not being able to send or receive any packets, more commonly known as Denial of Service or DoS.A source quench packet. This is incorrect because a source quench packet is an ICMP message that contains the internet header plus 64 bits of the original datagram.
A FIN scan. This is incorrect because a FIN scan is when a packet with the FIN flag set is sent to a specific port and the results are then analyzed.
Reference(s) used for this question:
Harris, Shon (2012-10-25). CISSP All-in-One Exam Guide, 6th Edition, Security Architecture and Design, Page 332, for people using the Kindle edition you will find it at Kindle Locations 7310-7315.
Schneiter, Andrew (2013-04-15). Official (ISC)2 Guide to the CISSP CBK, Third Edition : Security Architecture and Design (Kindle Locations 1403-1407). . Kindle Edition.
Wikipedia http://en.wikipedia.org/wiki/Port_scanner
ICMP http://security.maruhn.com/iptables-tutorial/x1078.html
Wikipedia http://en.wikipedia.org/wiki/Buffer_overflow -
A packet containing a long string of NOP’s followed by a command is usually indicative of what?
- A syn scan.
- A half-port scan.
- A buffer overflow attack.
- A packet destined for the network’s broadcast address.
Explanation:A series of the same control, hexidecimal, characters imbedded in the string is usually an indicator of a buffer overflow attack. A NOP is a instruction which does nothing (No Operation – the hexadecimal equivalent is 0x90)
The following answers are incorrect:
A syn scan. This is incorrect because a SYN scan is when a SYN packet is sent to a specific port and the results are then analyzed.
A half-port scan. This is incorrect because the port scanner generates a SYN packet. If the target port is open, it will respond with a SYN-ACK packet. The scanner host responds with a RST packet, closing the connection before the handshake is completed. Also known as a Half Open Port scan.
A packet destined for the network’s broadcast address. This is incorrect because this type of packet would not contain a long string of NOP characters.
-
What is the proper term to refer to a single unit of Ethernet data at the link layer of the DoD TCP model ?
- Ethernet Segment.
- Ethernet Datagram.
- Ethernet Frame.
- Ethernet Packet.
Explanation:Ethernet is frame based network technology.
See below a few definitions from RFC 1122:SEGMENT
A segment is the unit of end-to-end transmission in the TCP protocol. A segment consists of a TCP header followed by application data. A segment is transmitted by encapsulation inside an IP datagram.PACKET
A packet is the unit of data passed across the interface between the internet layer and the link layer. It includes an IP header and data. A packet may be a complete IP datagram or a fragment of an IP datagram.FRAME
A frame is the unit of transmission in a link layer protocol, and consists of a link-layer header followed by a packet.The following answers are incorrect:
Ethernet segment. Is incorrect because Ethernet segment is a distractor, TCP segment would be the correct terminology. Ethernet is a frame based network technology,
Ethernet datagram. Is incorrect because Ethernet datagram is a distractor, IP datagram would be the correct terminology. Ethernet is a frame based network technology
Ethernet packet. Is incorrect because Ethernet packet is a distractor, a Packet is a group of information so would not be a “single unit”. Ethernet is a frame based network technology.
Look at the diagrams below that were extracted from my Security+ Computer Based Tutorial.
TCP/IP Data Structures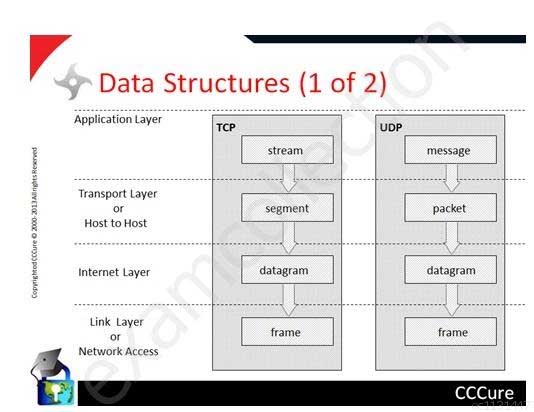
SSCP System Security Certified Practitioner (SSCP) Part 24 Q05 026 IMPORTANT NOTE:
The names used on the diagram above are from RFC 1122 which describe the DOD Model.
Vendors and Books may use slightly different names or even number of layers.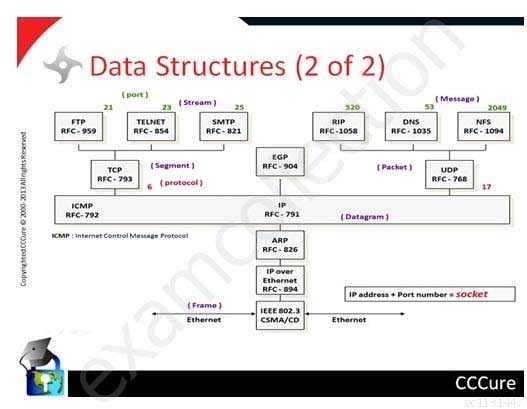
SSCP System Security Certified Practitioner (SSCP) Part 24 Q05 027 TCP/IP Data Structure
The following Reference(s) were used for this question:
Wikipedia http://en.wikipedia.org/wiki/Ethernet -
What is the proper term to refer to a single unit of IP data?
- IP segment.
- IP datagram.
- IP frame.
- IP fragment.
Explanation:IP is a datagram based technology.
DIFFERENCE BETWEEN PACKETS AND DATAGRAMAs specified at: http://en.wikipedia.org/wiki/Packet_(information_technology)
In general, the term packet applies to any message formatted as a packet, while the term datagram is generally reserved for packets of an “unreliable” service.
A “reliable” service is one that notifies the user if delivery fails, while an “unreliable” one does not notify the user if delivery fails. For example, IP provides an unreliable service.
Together, TCP and IP provide a reliable service, whereas UDP and IP provide an unreliable one. All these protocols use packets, but UDP packets are generally called datagrams.
If a network does not guarantee packet delivery, then it becomes the host’s responsibility to provide reliability by detecting and retransmitting lost packets. Subsequent experience on the ARPANET indicated that the network itself could not reliably detect all packet delivery failures, and this pushed responsibility for error detection onto the sending host in any case. This led to the development of the end-to-end principle, which is one of the Internet’s fundamental design assumptions.
The following answers are incorrect:
IP segment. Is incorrect because IP segment is a detractor, the correct terminology is TCP segment. IP is a datagram based technology.
IP frame. Is incorrect because IP frame is a detractor, the correct terminology is Ethernet frame. IP is a datagram based technology.IP fragment. Is incorrect because IP fragment is a detractor.
References:
Wikipedia http://en.wikipedia.org/wiki/Internet_Protocol -
Which of the following is an IP address that is private (i.e. reserved for internal networks, and not a valid address to use on the Internet)?
- 172.12.42.5
- 172.140.42.5
- 172.31.42.5
- 172.15.42.5
Explanation:This is a valid Class B reserved address. For Class B networks, the reserved addresses are 172.16.0.0 – 172.31.255.255.
The private IP address ranges are defined within RFC 1918:
RFC 1918 private ip address range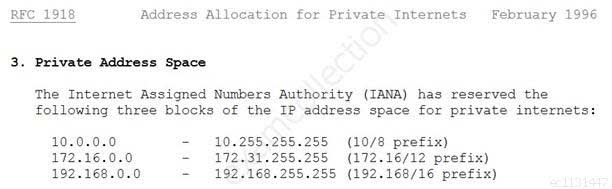
SSCP System Security Certified Practitioner (SSCP) Part 24 Q07 028 The following answers are incorrect:
172.12.42.5 Is incorrect because it is not a Class B reserved address.
172.140.42.5 Is incorrect because it is not a Class B reserved address.
172.15.42.5 Is incorrect because it is not a Class B reserved address. -
Which of the following is an IP address that is private (i.e. reserved for internal networks, and not a valid address to use on the Internet)?
- 10.0.42.5
- 11.0.42.5
- 12.0.42.5
- 13.0.42.5
Explanation:This is a valid Class A reserved address. For Class A, the reserved addresses are 10.0.0.0 – 10.255.255.255.
The following answers are incorrect:
11.0.42.5 Is incorrect because it is not a Class A reserved address.
12.0.42.5 Is incorrect because it is not a Class A reserved address.
13.0.42.5 Is incorrect because it is not a Class A reserved address.The private IP address ranges are defined within RFC 1918:
RFC 1918 private ip address range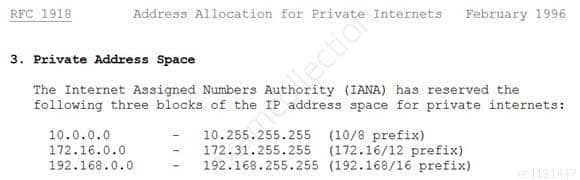
SSCP System Security Certified Practitioner (SSCP) Part 24 Q08 029 References:
3Com http://www.3com.com/other/pdfs/infra/corpinfo/en_US/501302.pdf
AIOv3 Telecommunications and Networking Security (page 438) -
In the days before CIDR (Classless Internet Domain Routing), networks were commonly organized by classes. Which of the following would have been true of a Class B network?
- The first bit of the IP address would be set to zero.
- The first bit of the IP address would be set to one and the second bit set to zero.
- The first two bits of the IP address would be set to one, and the third bit set to zero.
- The first three bits of the IP address would be set to one.
Explanation:Each Class B network address has a 16-bit network prefix, with the two highest order bits set to 1-0.
The following answers are incorrect:
The first bit of the IP address would be set to zero. Is incorrect because, this would be a Class A network address.
The first two bits of the IP address would be set to one, and the third bit set to zero. Is incorrect because, this would be a Class C network address.
The first three bits of the IP address would be set to one. Is incorrect because, this is a distractor. Class D & E have the first three bits set to 1. Class D the 4th bit is 0 and for Class E the 4th bit to 1.
Classless Internet Domain Routing (CIDR)
High Order bits are shown in bold below.For Class A, the addresses are 0.0.0.0 – 127.255.255.255
The lowest Class A address is represented in binary as 00000000.00000000.0000000.00000000For Class B networks, the addresses are 128.0.0.0 – 191.255.255.255.
The lowest Class B address is represented in binary as 10000000.00000000.00000000.00000000For Class C, the addresses are 192.0.0.0 – 223.255.255.255
The lowest Class C address is represented in binary as 11000000.00000000.00000000.00000000For Class D, the addresses are 224.0.0.0 – 239.255.255.255 (Multicast)
The lowest Class D address is represented in binary as 11100000.00000000.00000000.00000000For Class E, the addresses are 240.0.0.0 – 255.255.255.255 (Reserved for future usage)
The lowest Class E address is represented in binary as 11110000.00000000.00000000.00000000
Classful IP Address Format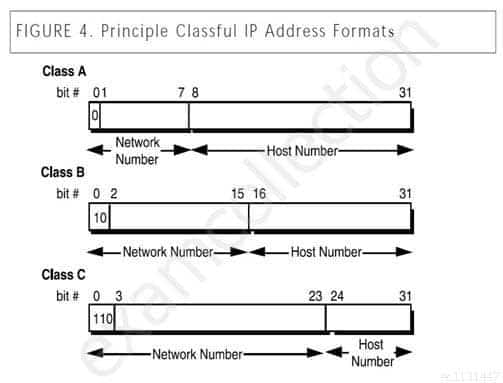
SSCP System Security Certified Practitioner (SSCP) Part 24 Q09 030 References:
3Com http://www.3com.com/other/pdfs/infra/corpinfo/en_US/501302.pdf
AIOv3 Telecommunications and Networking Security (page 438) -
Which of the following is an IP address that is private (i.e. reserved for internal networks, and not a valid address to use on the Internet)?
- 192.168.42.5
- 192.166.42.5
- 192.175.42.5
- 192.1.42.5
Explanation:This is a valid Class C reserved address. For Class C, the reserved addresses are 192.168.0.0 – 192.168.255.255.
The private IP address ranges are defined within RFC 1918:
RFC 1918 private ip address range
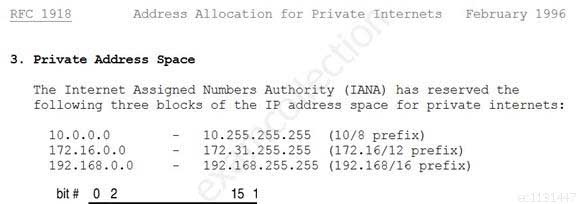
SSCP System Security Certified Practitioner (SSCP) Part 24 Q10 031 The following answers are incorrect:
192.166.42.5 Is incorrect because it is not a Class C reserved address.
192.175.42.5 Is incorrect because it is not a Class C reserved address.
192.1.42.5 Is incorrect because it is not a Class C reserved address. -
Which layer defines how packets are routed between end systems?
- Session layer
- Transport layer
- Network layer
- Data link layer
Explanation:The network layer (layer 3) defines how packets are routed and relayed between end systems on the same network or on interconnected networks. Message routing, error detection and control of node traffic are managed at this level.
Reference(s) used for this question:
KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 82). -
Which OSI/ISO layers are TCP and UDP implemented at?
- Application layer
- Presentation layer
- Session layer
- Transport layer
Explanation:TCP and UDP are implemented at the transport layer (layer 4). Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 82). -
Which type of attack involves the alteration of a packet at the IP level to convince a system that it is communicating with a known entity in order to gain access to a system?
- TCP sequence number attack
- IP spoofing attack
- Piggybacking attack
- Teardrop attack
Explanation:An IP spoofing attack is used to convince a system that it is communication with a known entity that gives an intruder access. It involves modifying the source address of a packet for a trusted source’s address. A TCP sequence number attack involves hijacking a session between a host and a target by predicting the target’s choice of an initial TCP sequence number. Piggybacking refers to an attacker gaining unauthorized access to a system by using a legitimate user’s connection. A teardrop attack consists of modifying the length and fragmentation offset fields in sequential IP packets so the target system becomes confused and crashes after it receives contradictory instructions on how the fragments are offset on these packets.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 77). -
Which type of attack involves hijacking a session between a host and a target by predicting the target’s choice of an initial TCP sequence number?
- IP spoofing attack
- SYN flood attack
- TCP sequence number attack
- Smurf attack
Explanation:A TCP sequence number attack exploits the communication session which was established between the target and the trusted host that initiated the session. It involves hijacking the session between the host and the target by predicting the target’s choice of an initial TCP sequence number. An IP spoofing attack is used to convince a system that it is communication with a known entity that gives an intruder access. It involves modifying the source address of a packet for a trusted source’s address. A SYN attack is when an attacker floods a system with connection requests but does not respond when the target system replies to those requests. A smurf attack occurs when an attacker sends a spoofed (IP spoofing) PING (ICMP ECHO) packet to the broadcast address of a large network (the bounce site). The modified packet containing the address of the target system, all devices on its local network respond with a ICMP REPLY to the target system, which is then saturated with those replies.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 77). -
How many layers are defined within the US Department of Defense (DoD) TCP/IP Model?
- 7
- 5
- 4
- 3
Explanation:The TCP/IP protocol model is similar to the OSI model but it defines only four layers:
Application
Host-to-host
Internet
Network accessReference(s) used for this question:
http://www.novell.com/documentation/nw65/ntwk_ipv4_nw/data/hozdx4oj.html
and
KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 84).
also see:
http://en.wikipedia.org/wiki/Internet_Protocol_Suite#Layer_names_and_number_of_layers_in_the_literature -
As per RFC 1122, which of the following is not a defined layer in the DoD TCP/IP protocol model?
- Application layer
- Session layer
- Internet layer
- Link/Network Access Layer
Explanation:As per RFC, The DoD TCP/IP protocol model defines four layers, with the layers having names, not numbers, as follows:
Application (process-to-process) Layer:
This is the scope within which applications create user data and communicate this data to other processes or applications on another or the same host. The communications partners are often called peers. This is where the “higher level” protocols such as SMTP, FTP, SSH, HTTP, etc. operate.Transport (host-to-host) Layer:
The Transport Layer constitutes the networking regime between two network hosts, either on the local network or on remote networks separated by routers. The Transport Layer provides a uniform networking interface that hides the actual topology (layout) of the underlying network connections. This is where flow-control, error-correction, and connection protocols exist, such as TCP. This layer deals with opening and maintaining connections between internet hosts.Internet (internetworking) Layer:
The Internet Layer has the task of exchanging datagrams across network boundaries. It is therefore also referred to as the layer that establishes internetworking; indeed, it defines and establishes the Internet. This layer defines the addressing and routing structures used for the TCP/IP protocol suite. The primary protocol in this scope is the Internet Protocol, which defines IP addresses. Its function in routing is to transport datagrams to the next IP router that has the connectivity to a network closer to the final data destination.Link (network access) Layer:
This layer defines the networking methods with the scope of the local network link on which hosts communicate without intervening routers. This layer describes the protocols used to describe the local network topology and the interfaces needed to affect transmission of Internet Layer datagrams to next-neighbor hosts.The DoD tcp/ip model DoD model Osi Model
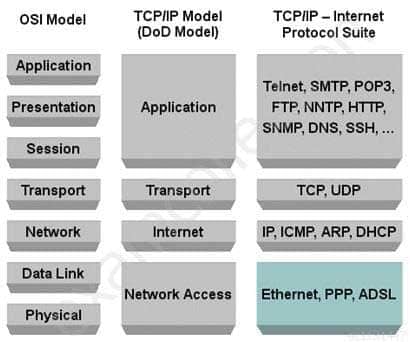
SSCP System Security Certified Practitioner (SSCP) Part 24 Q16 032 Graphic above from: http://bit.kuas.edu.tw/
REALITY VERSUS THE STANDARD
In real life today, this is getting very confusing. Many books and references will not use exactly the same names as the initial RFC that was published. For example, the Link layer is often times called Network Access. The same applies with Transport which is often times called Host-to-Host and vice versa.The following answer is incorrect:
The session layer is defined within the OSI/ISO model but not within the DOD model. Being incorrect it made it the best answer according to the question. It does not belong to the DoD TCP/IP Model.Reference(s) Used for this question:
http://www.freesoft.org/CIE/RFC/1122/
http://bit.kuas.edu.tw/~csshieh/teach/np/tcpip/ -
Which ISO/OSI layer establishes the communications link between individual devices over a physical link or channel?
- Transport layer
- Network layer
- Data link layer
- Physical layer
Explanation:The data link layer (layer 2) establishes the communications link between individual devices over a physical link or channel. It also ensures that messages are delivered to the proper device and translates the messages from layers above into bits for the physical layer (layer 1) to transmit.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 83). -
Which OSI/ISO layer is the Media Access Control (MAC) sublayer part of?
- Transport layer
- Network layer
- Data link layer
- Physical layer
Explanation:The data link layer contains the Logical Link Control sublayer and the Media Access Control (MAC) sublayer.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 83). -
A common way to create fault tolerance with leased lines is to group several T1s together with an inverse multiplexer placed:
- at one end of the connection.
- at both ends of the connection.
- somewhere between both end points.
- in the middle of the connection.
Explanation:A common way to create fault tolerance with leased lines is to group several T1s together with an inverse multiplexer placed at both ends of the connection.
In fact it would be a Multiplexer at one end and DeMultiplexer at other end or vice versa. Inverse Multiplexer at both end.
In electronics, a multiplexer (or mux) is a device that selects one of several analog or digital input signals and forwards the selected input into a single line. A multiplexer of 2n inputs has n select lines, which are used to select which input line to send to the output. Multiplexers are mainly used to increase the amount of data that can be sent over the network within a certain amount of time and bandwidth. A multiplexer is also called a data selector.
An electronic multiplexer makes it possible for several signals to share one device or resource, for example one A/D converter or one communication line, instead of having one device per input signal.
On the other hand, a demultiplexer (or demux) is a device taking a single input signal and selecting one of many data-output-lines, which is connected to the single input. A multiplexer is often used with a complementary demultiplexer on the receiving end.
An electronic multiplexer can be considered as a multiple-input, single-output switch, and a demultiplexer as a single-input, multiple-output switchReferences:
KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, 2001, John Wiley & Sons, Page 72.
and
https://secure.wikimedia.org/wikipedia/en/wiki/Multiplexer -
Frame relay uses a public switched network to provide:
- Local Area Network (LAN) connectivity.
- Metropolitan Area Network (MAN) connectivity.
- Wide Area Network (WAN) connectivity.
- World Area Network (WAN) connectivity.
Explanation:Frame relay uses a public switched network to provide Wide Area Network (WAN) connectivity.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, 2001, John Wiley & Sons, Page 73.