Match the antimalware approach to the description.
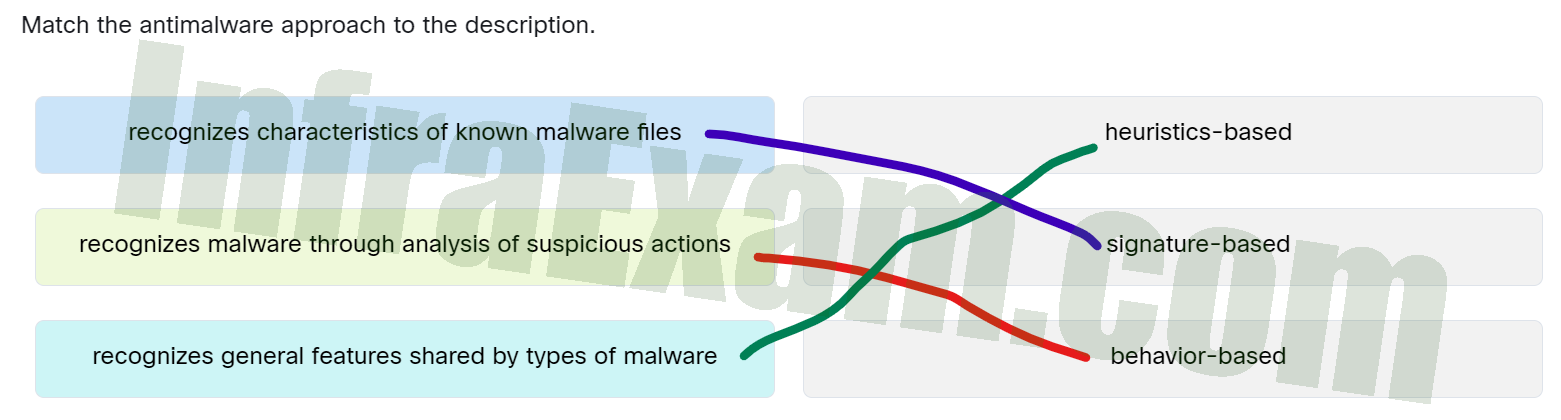
- recognizes malware through analysis of suspicious actions ==> Behavior-based
- recognizes general features shared by types of malware ==> Heuristics-based
- recognizes characteristics of known malware files ==> Signature-based
Explanation & Hint: Place the options in the following order:
Recognizes characteristics of known malware files Signature-based Recognizes general features shared by types of malware Heuristics-based Recognizes malware through analysis of suspicious actions Behavior-based
For more Questions and Answers:
Cybersecurity Essentials 3.0 Checkpoint Exam: OS and Endpoint Security Module 7 – 10 Exam Answers Full 100%
Match the antimalware approach to the description.
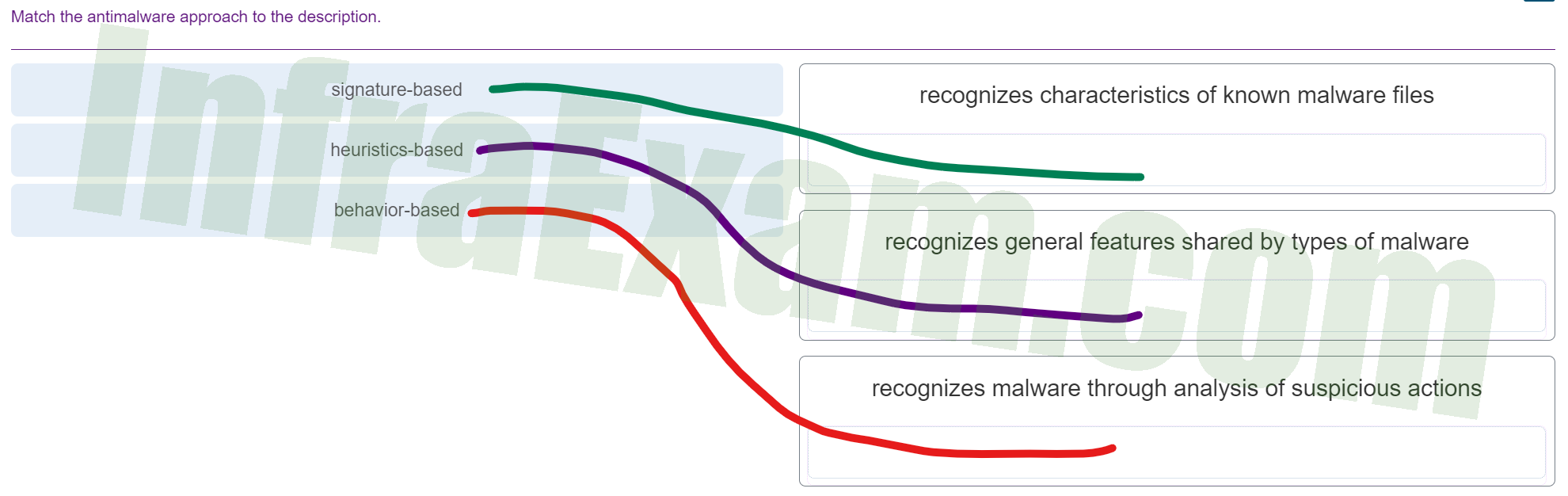
- signature-based ==> recognizes characteristics of known malware files
- heuristics-based ==> recognizes general features shared by types of malware
- behavior-based ==> recognizes malware through analysis of suspicious actions
|
Explanation & Hint:
|