Match the attack to the definition.
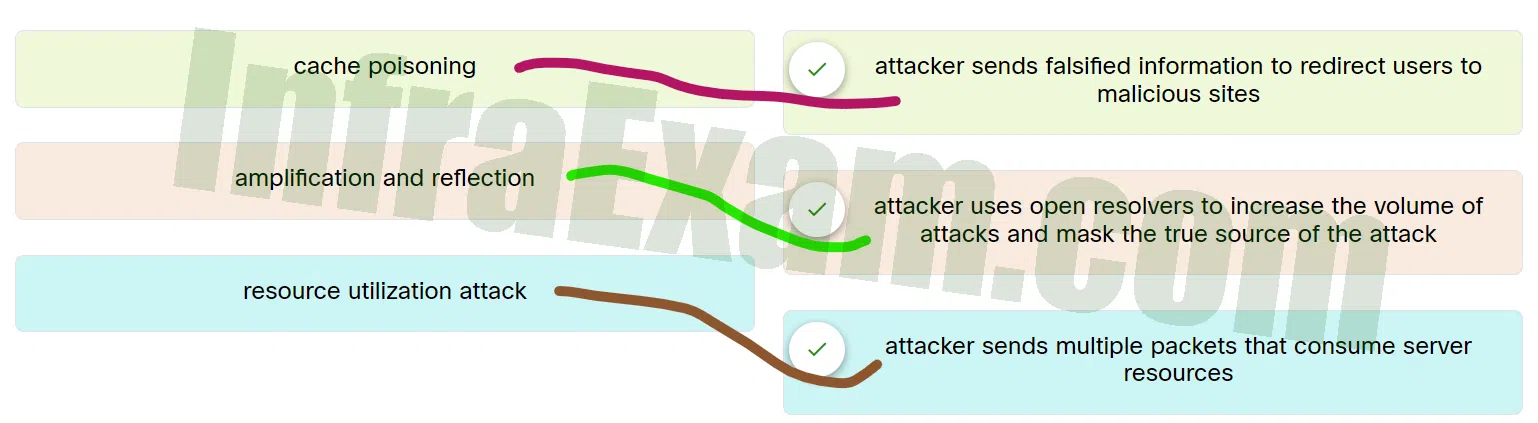
- cache poisoning ==> Attacker sends falsified information to redirect users to malicious sites
- resource utilization attack ==> Attacker sends multiple packets that consume server resources
- amplification and reflection ==> Attacker uses open resolvers to increase the volume of attacks and mask the true source of the attack
| Explanation & Hint:
Place the options in the following order:
|