Match the attack type with the respective description.
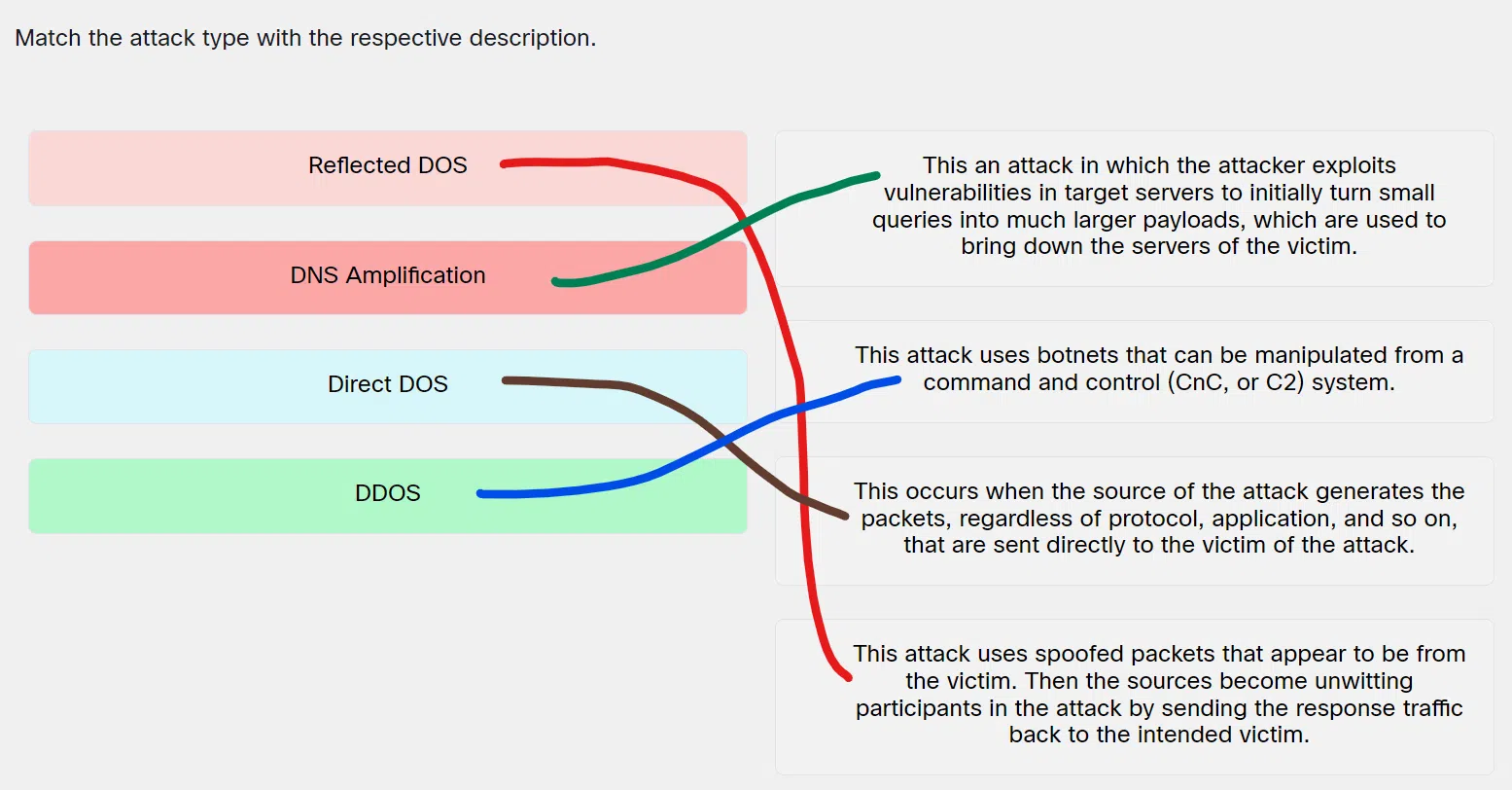
- Reflected DOS ==> This attack uses spoofed packets that appear to be from the victim. Then the sources become unwitting participants in the attack by sending the response traffic back to the intended victim.
- DNS Amplification ==> This an attack in which the attacker exploits vulnerabilities in target servers to initially turn small queries into much larger payloads, which are used to bring down the servers of the victim.
- Direct DOS ==> This occurs when the source of the attack generates the packets, regardless of protocol, application, and so on, that are sent directly to the victim of the attack.
- DDOS ==> This attack uses botnets that can be manipulated from a command and control (CnC, or C2) system.
| Explanation & Hint:
Place the options in the following order:
|
For more Questions and Answers:
5.3.3 Quiz – Exploiting Wired and Wireless Networks Answers Full 100%
Match the attack type with the respective description.
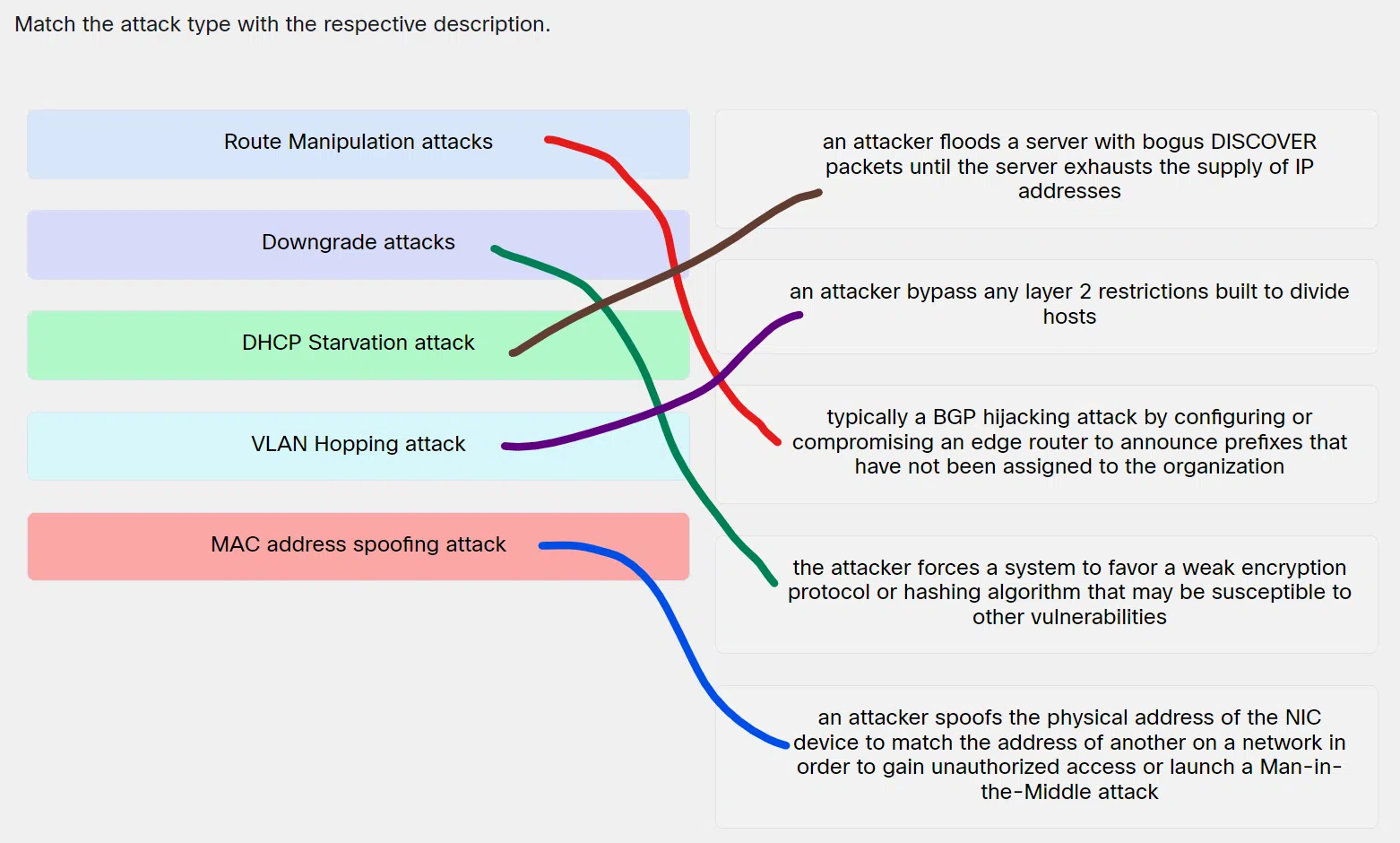
- Route Manipulation attacks ==> Typically a BGP hijacking attack by configuring or compromising an edge router to announce prefixes that have not been assigned to the organization
- Downgrade attacks ==> The attacker forces a system to favor a weak encryption protocol or hashing algorithm that may be susceptible to other vulnerabilities
- DHCP Starvation attack ==> An attacker floods a server with bogus DISCOVER packets until the server exhausts the supply of IP addresses
- VLAN Hopping attack ==> An attacker bypass any layer 2 restrictions built to divide hosts
- MAC address spoofing attack ==> An attacker spoofs the physical address of the NIC device to match the address of another on a network in order to gain unauthorized access or launch a Man-in-the-Middle attack
| Explanation & Hint:
Place the options in the following order:
|