| Explanation & Hint:
Place the options in the following order:
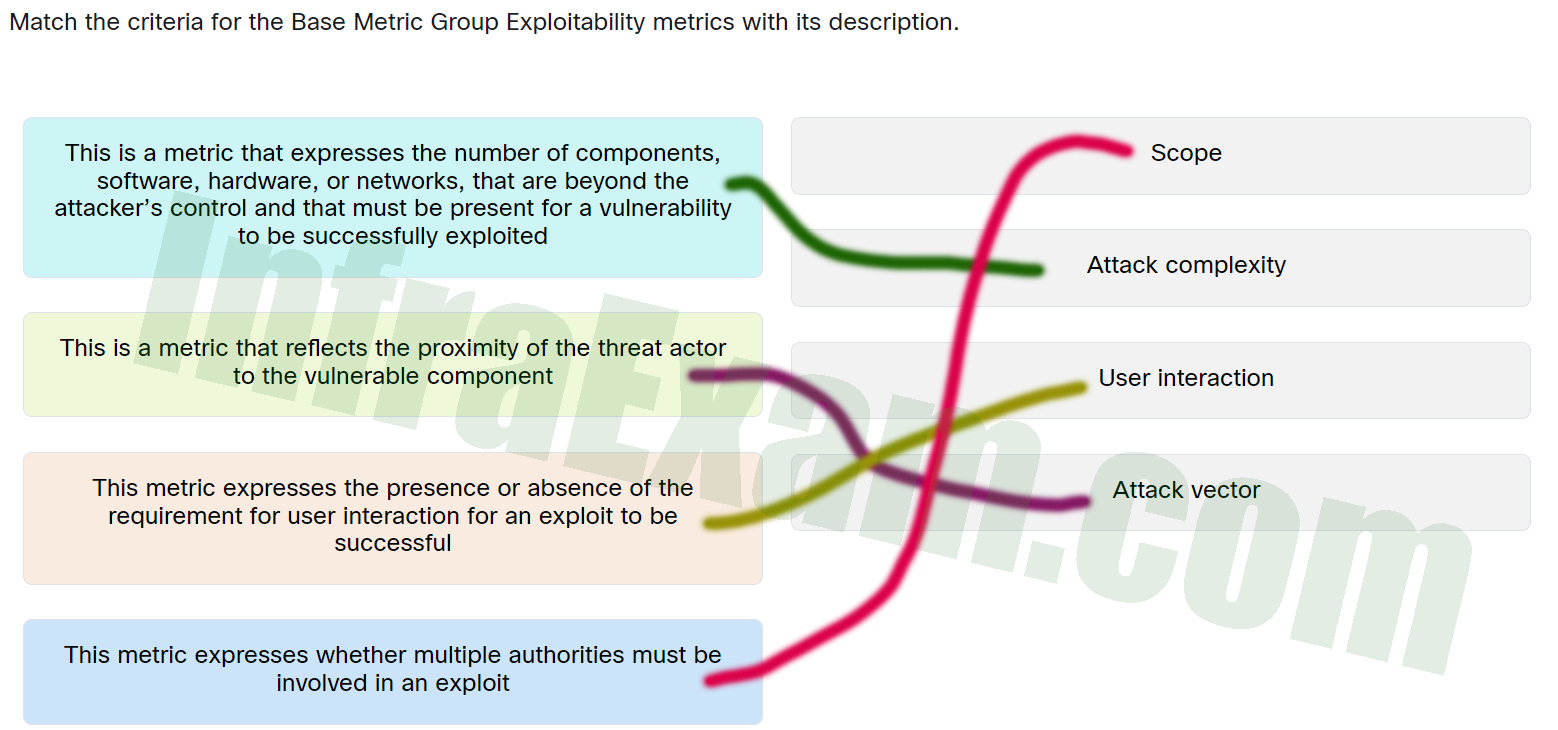
| This metric expresses whether multiple authorities must be involved in an exploit. |
Scope |
| This is a metric that expresses the number of components,software,hardware,or networks,that are beyond the attacker’s control and that must be present for a vulnerability to be successfully exploited. |
Attack complexity |
| This is a metric that reflects the proximity of the threat actor to the vulnerable component. |
Attack vector |
| This metric expresses the presence or absence of the requirement for user interaction for an exploit to be successful. |
User interaction |
|