Match the insecure code practice to the description.
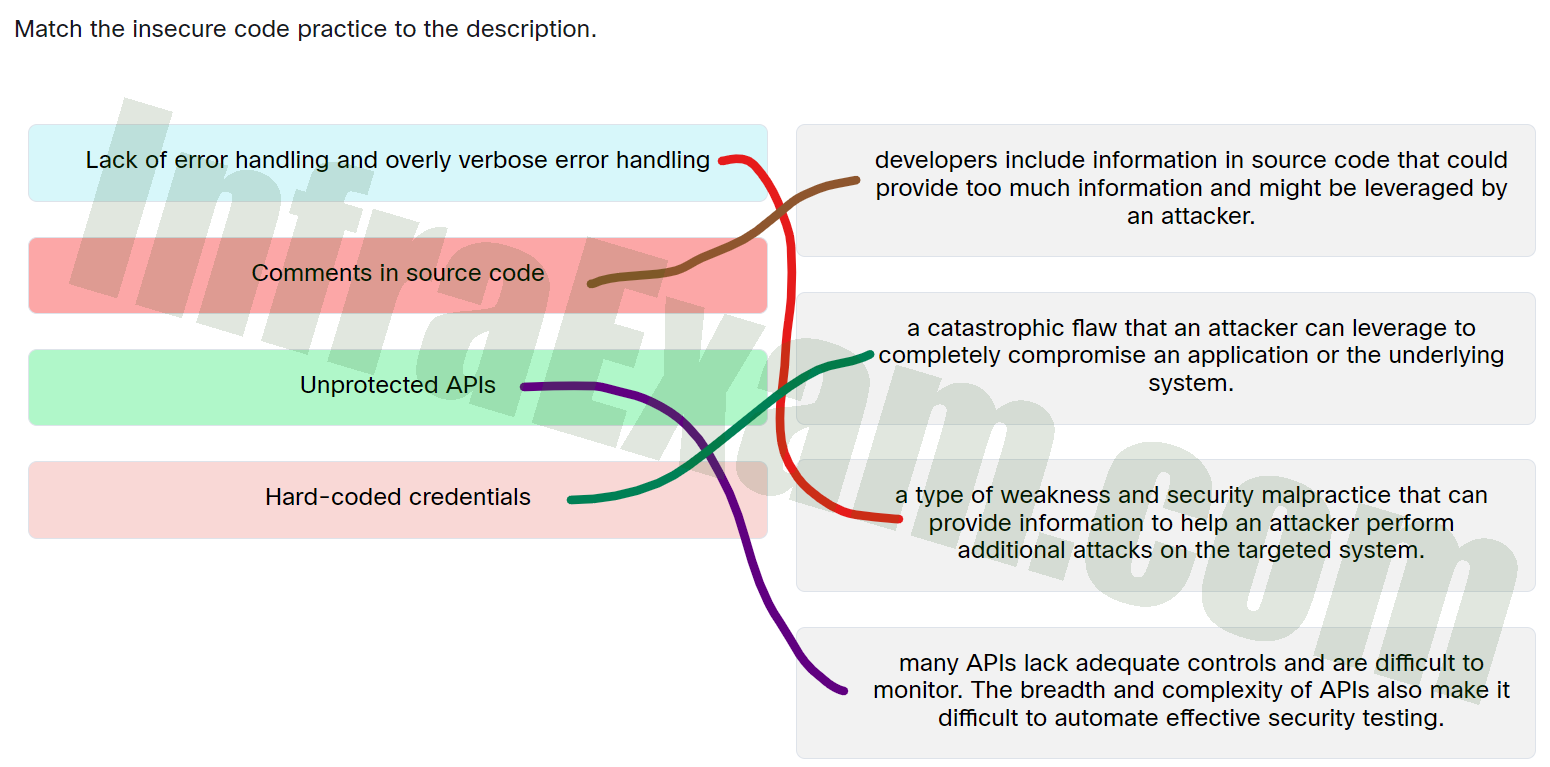
- Lack of error handling and overly verbose error handling ==> A type of weakness and security malpractice that can provide information to help an attacker perform additional attacks on the targeted system.
- Comments in source code ==> Developers include information in source code that could provide too much information and might be leveraged by an attacker.
- Unprotected APIs ==> Many APIs lack adequate controls and are difficult to monitor. The breadth and complexity of APIs also make it difficult to automate effective security testing.
- Hard-coded credentials ==> A catastrophic flaw that an attacker can leverage to completely compromise an application or the underlying system.
| Explanation & Hints:
Place the options in the following order:
|