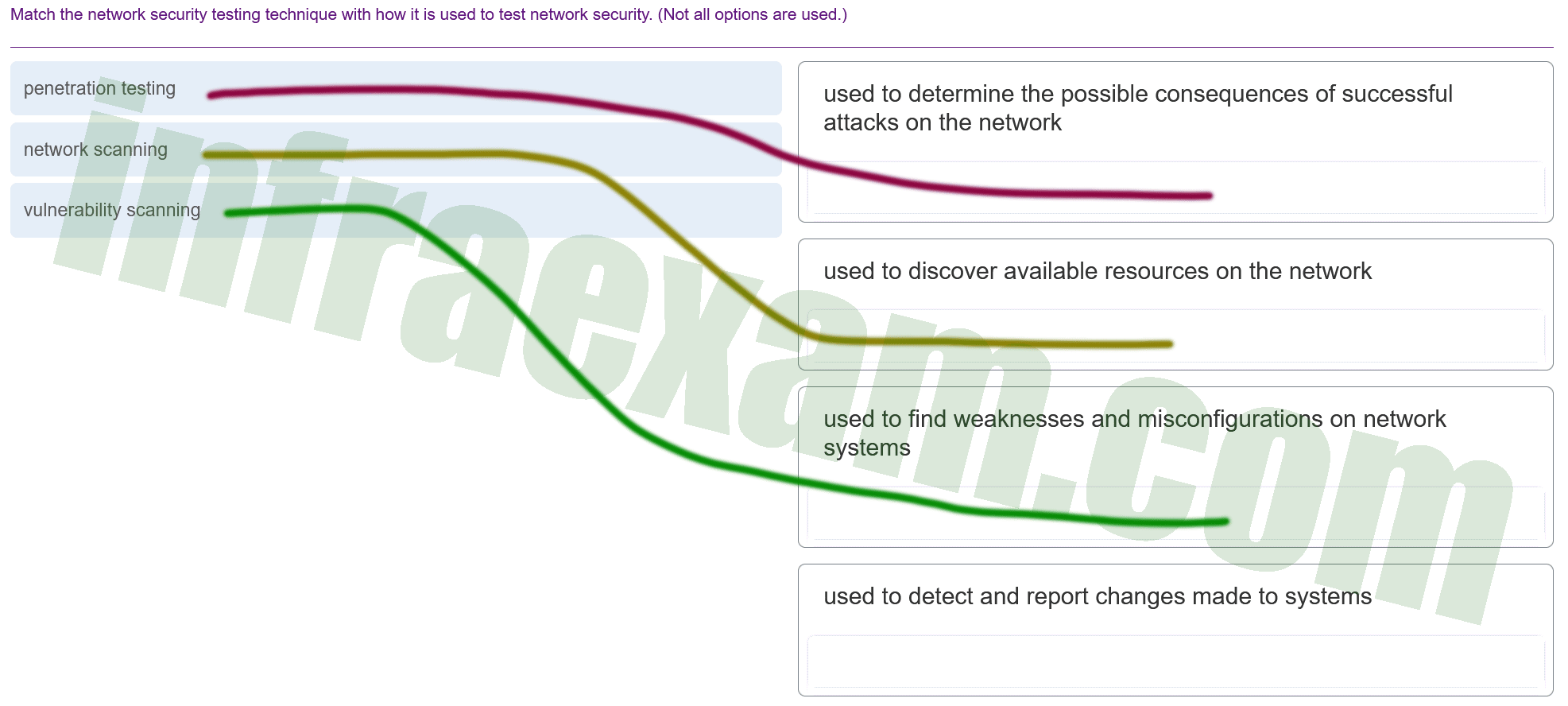
Match the network security testing technique with how it is used to test network security. (Not all options are used.)
| Answers Explanation & Hints:
Network scanning tools are used to probe network devices, servers and hosts for open TCP or UDP ports. Vulnerability scanning tools are used to discover security weaknesses in a network or computer system. Penetration testing tools are used to determine the possible outcome of a successful attack on a network or computer system. |