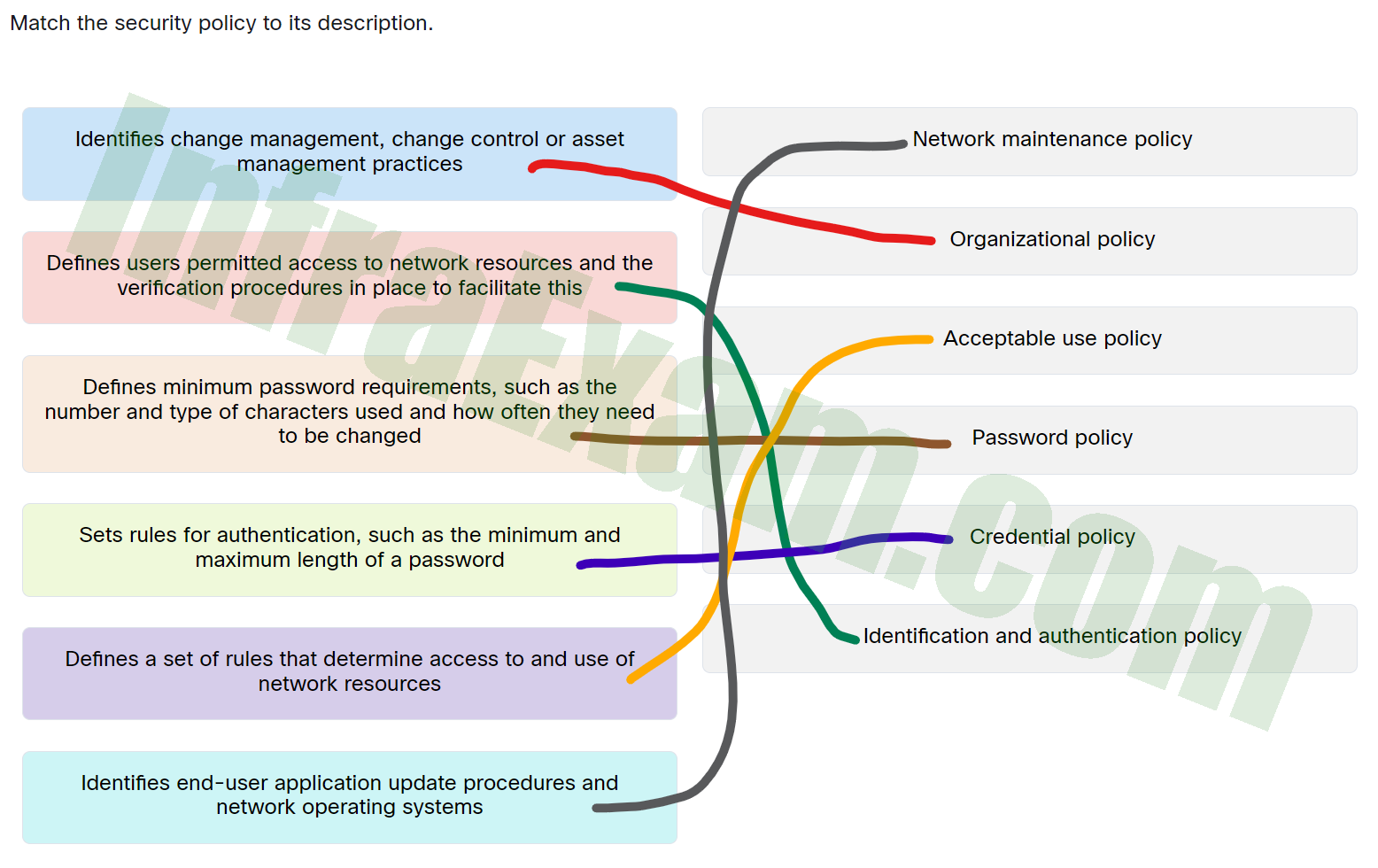
| Identifies change management,change control or asset management practices. |
Organizational policy |
| Identifies end-user application update procedures and network operating systems. |
Network maintenance policy |
| Sets rules for authentication,such as the minimum and maximum length of a password. |
Credential policy |
| Defines minimum password requirements,such as the number and type of characters used and how often they need to be changed. |
Password policy |
| Defines users permitted access to network resources and the verification procedures in place to facilitate this. |
Identification and authentication policy |
| Defines a set of rules that determine access to and use of network resources. |
Acceptable use policy |