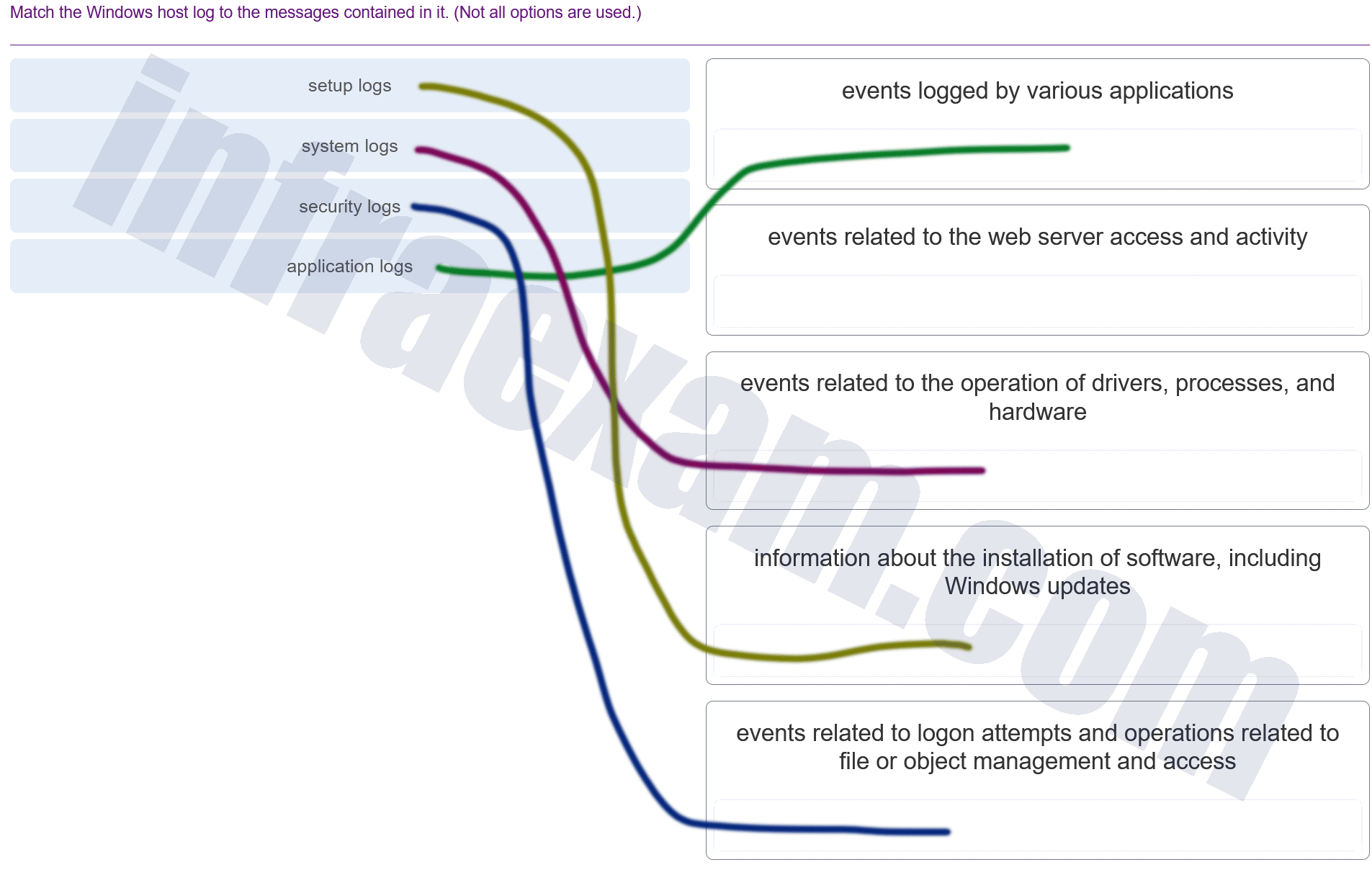
Explanation & Hint:
- Setup logs: These typically contain information related to the installation of software, including Windows updates. This would likely be the line connecting to the text about installation information.
- System logs: These are generally used to store events related to the operation of drivers, processes, and hardware, which corresponds to one of the provided descriptions.
- Security logs: These logs would record events such as logon attempts and operations related to file or object management and access, as security logs deal with audit records for security-related events.
- Application logs: These logs contain events logged by various applications, not just web server access and activity, which would be specifically tracked in web server logs.
|