98-367 : Security Fundamentals : Part 06
-
You are trying to establish communications between a client computer and a server. The server is not responding.
You confirm that both the client and the server have network connectivity.
Which should you check next?
- Microsoft Update
- Data Execution Prevention
- Windows Firewall
- Active Directory Domains and Trusts
-
You are an intern and are working remotely.
You need a solution that meets the following requirements:
– Allows you to access data on the company network securely
– Gives you the same privileges and access as if you were in the officeWhat are two connection methods you could use? (Choose two.)
- Forward Proxy
- Virtual Private Network (VPN)
- Remote Access Service (RAS)
- Roaming Profiles
-
Network Access Protection (NAP) enables administrators to control access to network resources based on a computer’s:
- Encryption level
- Warranty
- Physical location
- Configuration
Explanation:
Network Access Protection (NAP) is a new set of operating system components included with the Windows Server® 2008 and Windows Vista® operating systems that provides a platform to help ensure that client computers on a private network meet administrator-defined requirements for system health. NAP policies define the required configuration and update status for a client computer’s operating system and critical software. For example, computers might be required to have antivirus software with the latest signatures installed, current operating system updates installed, and a host-based firewall enabled. By enforcing compliance with health requirements, NAP can help network administrators mitigate some of the risk caused by improperly configured client computers that might be exposed to viruses and other malicious software. -
Which technology enables you to filter communications between a program and the Internet?
- RADIUS server
- Antivirus software
- Software firewall
- BitLocker To Go
Explanation:
There are two types of firewalls the Hardware Firewall and the Software Firewall. A Software Firewall is a software program and a Hardware Firewall is a piece of hardware. Both have the same objective of filtering communications over a system. -
This question requires that you evaluate the underlined text to determine if it is correct.
The first line of defense against attacks from the Internet is a software firewall.Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed” if the underlined text makes the statement correct.
- hardware firewall
- virus software
- radius server
- No change is needed
-
Which attack listens to network traffic of a computer resource?
- Resource gathering
- Denial of service
- ARP poisoning
- Eavesdropping
- Logic bomb
Explanation:
Eavesdropping
In general, the majority of network communications occur in an unsecured or “cleartext” format, which allows an attacker who has gained access to data paths in your network to “listen in” or interpret (read) the traffic. When an attacker is eavesdropping on your communications, it is referred to as sniffing or snooping. The ability of an eavesdropper to monitor the network is generally the biggest security problem that administrators face in an enterprise. Without strong encryption services that are based on cryptography, your data can be read by others as it traverses the network. -
Which of the following describes a VLAN?
- It connects multiple networks and routes data packets.
- It is a logical broadcast domain across physical subnets.
- It is a subnetwork that reveals a company’s externally facing resources to the public network.
- It allows different network protocols to communicate between different network segments.
Explanation:
VLAN (Virtual Local Network) is a logically separate IP subnetwork which allow multiple IP networks and subnets to exist on the same-switched network.
VLAN is a logical broadcast domain that can span multiple physical LAN segments. It is a modern way administrators configure switches into virtual local-area networks (VLANs) to improve network performance by separating large Layer 2 broadcast domains into smaller ones. -
A network sniffer is software or hardware that:
- Records user activity and transmits it to the server
- Captures and analyzes network communication
- Protects workstations from intrusions
- Catalogs network data to create a secure index
Explanation:
A network sniffer is a computer tool that captures network data in the form of low-level packets. Network sniffers can be used for technical troubleshooting and analyzing the communication. -
What is a service set identifier (SSID)?
- A wireless encryption standard
- The wireless LAN transmission type
- The broadcast name of an access point
- A wireless security protocol
Explanation:
SSID (service set identifier) is a function performed by an Access Point that transmits its name so that wireless stations searching for a network connection can ‘discover’ it. It’s what allows your wireless adapter’s client manager program or Windows built-in wireless software to give you a list of the Access Points in range. -
To implement WPA2 Enterprise, you would need a/an:
- RADIUS server
- SSL server
- WEP server
- VPN server
-
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
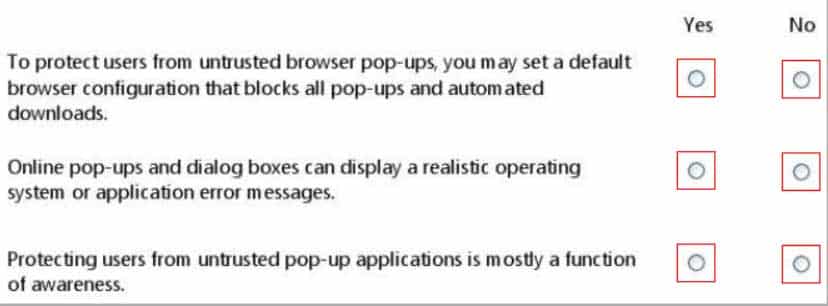
98-367 Part 06 Q11 033 Question 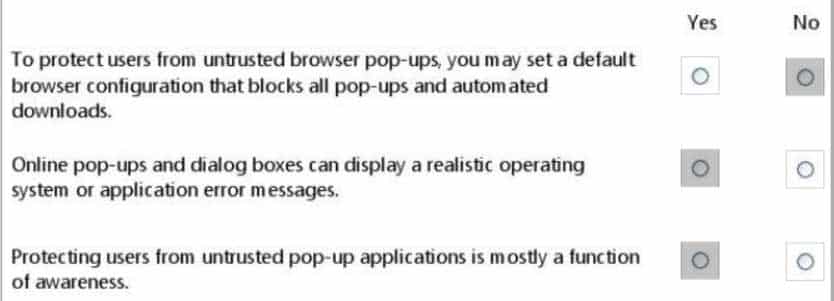
98-367 Part 06 Q11 033 Answer -
You would implement a wireless intrusion prevention system to:
- Prevent wireless interference
- Detect wireless packet theft
- Prevent rogue wireless access points
- Enforce SSID broadcasting
-
The manager of a coffee shop hires you to securely set up WiFi in the shop.
To keep computer users from seeing each other, what should you use with an access point?
- Client bridge mode
- Client isolation mode
- MAC address filtering
- Client mode
Explanation:
Wireless Client Isolation is a unique security feature for wireless networks. When Client Isolation is enabled any and all devices connected to the wireless LAN will be unable to talk to each other. -
E-mail bombing attacks a specific entity by:
- Redirecting all e-mail to another entity
- Sending high volumes of e-mail
- Tracing e-mail to the destination address
- Triggering high levels of security alerts
Explanation:
In Internet usage, an email bomb is a form of net abuse consisting of sending huge volumes of email to an address in an attempt to overflow the mailbox or overwhelm the server where the email address is hosted in a denial-of-service attack. -
How does the sender policy framework (SPF) aim to reduce spoofed email?
- It provides a list of IP address ranges for particular domains so senders can be verified.
- It includes an XML policy file with each email that confirms the validity of the message.
- It lists servers that may legitimately forward mail for a particular domain.
- It provides an encryption key so that authenticity of an email message can be validated
-
Windows Server Update Services (WSUS) is a tool that:
- Updates data stored in Windows servers
- Manages the services that run on a server
- Updates licensing for Windows servers
- Manages updates for Microsoft software
Explanation:
Windows Server Update Services (WSUS) enables information technology administrators to deploy the latest Microsoft product updates to computers that are running the Windows operating system. By using WSUS, administrators can fully manage the distribution of updates that are released through Microsoft Update to computers in their network. -
Which two characteristics should you recommend for a user’s domain password? (Choose two.)
- Hard to guess
- Includes Unicode characters
- Easy to remember
- Easy to increment
-
To protect systems from buffer overflow errors, you can use:
- Antivirus software
- Data Execution Prevention
- A proxy server
- An Intruder Prevention System
-
You sign up for an online bank account. Every 6 months, the bank requires you to change your password. You have changed your password 5 times in the past. Instead of coming up with a new password, you decide to use one of your past passwords, but the bank’s password history prevents you on doing so.
Select the correct answer if the underlined text does not make the statement correct Select “No change is needed” if the underlined text makes the statement correct.
- Minimum password age
- Maximum password duration
- Password complexity
- No change is needed.
-
You need to prevent unauthorized users from reading a specific file on a portable computer if the portable computer is stolen.
What should you implement?
- File-level permissions
- Advanced Encryption Standard (AES)
- Folder-level permissions
- Distributed File System (DFS)
- BitLocker
Subscribe
0 Comments
Newest