98-368 : Mobility and Devices Fundamentals : Part 02
-
Your new Windows 8.1 computer is connected to your home wireless network.
You want to share music and photos on your new computer with other members of your family. You want to avoid setting up separate user accounts for each member of your family. A single password for all the shared files will suffice.
Which Windows 8.1 networking feature satisfies these requirements?
- Network Discovery
- HomeGroup
- Virtual Private Network
- Broadband (PPPoE)
Explanation:A homegroup makes it easier to share files and printers on a home network. You can share pictures, music, videos, documents, and printers with other people in your homegroup. Other people can’t change the files that you share, unless you give them permission to do so.
-
This question requires that you evaluate the underlined text to determine if it is correct.
You manage Windows 8.1 desktop and laptop computers in your university’s computer lab.
The university’s IT team recently implemented an active directory environment.
You need to join the desktop and laptop computers to a new Active Directory domain.
You should use the “Network and Internet” Control Panel applet to achieve this goal.
Instructions: Review the underlined text. If it makes the statement correct, select “No change is needed”. If the statement is incorrect, select the answer choice than makes the statement correct.
- No change is needed
- User Accounts
- Administrative Tools
- System
Explanation:Join a domain, workgroup, or homegroup
1. Open System by swiping in from the right edge of the screen, tapping Search (or if you’re using a mouse, pointing to the upper-right corner of the screen, moving the mouse pointer down, and then clicking Search), entering System in the search box, and tapping or clicking System.
2. Under Computer name, domain, and workgroup settings, click Change settings. You might be asked for an admin password or to confirm your choice.
3. Click Network ID and follow the steps on your screen. -
You have several Windows 8.1 Pro computers in your college dorm.
You want to share music library files across these computers in a simple way by using a single password for access.
What should you do?
- Share the folder with the Everyone group
- Change the permissions of all music files to Everyone read
- Share the music library through a HomeGroup and join each computer to it
- Rename each computer to a single, common name and enable the Administrator
Explanation:A homegroup is a group of PCs on a home network that can share devices (such as printers), and libraries (such as your Documents, Pictures, Music, and Video libraries). Using a homegroup makes sharing easier. Your homegroup is protected with a password, which you can change at any time.
-
Your sister is taking a video editing class at school. She purchased a 2-TB USB hard drive to store video files. She wants to connect it to her Windows 8.1 computer at home and to a Mac OSX 10.3 computer at school. Video file will exceed 5 GB in size.
You need to prepare a new hard drive by formatting it with the appropriate file system.
Which file system should you choose?
- FAT
- ReFS
- NTFS
- FAT32
Explanation:Mac OSX 10.3 supports NTFS.
NTFS supports large files well above 5 GB.Incorrect answers:
Not A: FAT does not support a 5 GB file size.
Not B: ReFS is only supported by Microsoft Windows.
Not C:
Not D: FAT32 works fine if file sizes are smaller than 4GB. -
This question requires that you evaluate the underlined text to determine if it is correct.
You have a Windows 8.1 computer in a WorkGroup. To share the C:\Work folder and make it available to offline users, you need to use the “public” share option.
Instructions: Review the underlined text. If it makes the statement correct, select “No change is needed”. If the statement is incorrect, select the answer choice than makes the statement correct.
- No change is needed
- advanced
- HomeGroup
- basic
Explanation:In the advanced sharing dialog box Click on “Caching” button. In “Offline settings” dialog box, you can set up caching for files and programs which are offline.
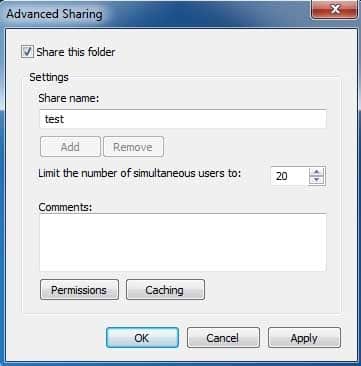
98-368 Part 02 Q05 004 You have the following options:
i) Only the files and programs that users specify are available offline: If you select this option then, users specify the files and programs which can be accessed offline. It is the default option.
ii) No files or programs from the share are available offline: If you select this option then, caching will be turned off.
iii) All files and programs that users open from the share are automatically available offline: If you select this option then, caching is turned on for all files and programs and they can be accessed offline. Check option “Optimize for performance”. -
You are a desktop support engineer for an advertising company that uses Windows 8.1 workstations.
An employee who manages video content for the company website recently lost important video files due to a single-drive failure on a Windows 8.1 workstation.
You need to prevent a single-drive failure from occurring again on this employee’s workstation, which only has a capacity for three physical hard drivers. Additionally, the employee requires optimal performance when manipulating and streaming video files.
Which Storage Space solution should you implement?
- three-way mirror
- parity spaces
- simple spaces
- two-way mirror
Explanation:Parity spaces (also known as RAID-5) are designed for storage efficiency and protect your files from drive failure by keeping more than one copy. Parity spaces are best for archival data and streaming media, like music and videos. This storage layout requires at least three drives to protect you from a single drive failure and at least seven drives to protect you from two drive failures.
-
HOTSPOT
You are setting up secure communications for a website that is hosted on a Windows 10 computer.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

98-368 Part 02 Q07 006 Question 
98-368 Part 02 Q07 006 Answer Explanation:* Secure Sockets Layer (SSL) is a cryptographic protocol designed to provide communications security over a computer network, such as secure connections to websites.
* SSL is used for encryption but not for authentication.
* There is SSL for the web server, but the client does not have a SSL certificate.
SSL Certificates are small data files that digitally bind a cryptographic key to an organization’s details. When installed on a web server, it activates the padlock and the https protocol (over port 443) and allows secure connections from a web server to a browser. -
This question requires that you evaluate the underlined text to determine if it is correct.
The “Simple Spaces” resiliency type in Windows 8.1 Storage Spaces requires at least five drives in order to protect a system from a single-drive failure.
Instructions: Review the underlined text. If it makes the statement correct, select “No change is needed”. If the statement is incorrect, select the answer choice than makes the statement correct.
- No change is needed
- two-way mirror
- Parity Spaces
- three-way mirror
Explanation:Two-way mirror spaces require at least two drives, and three-way mirror spaces require at least five.
Mirror spaces are designed for increased performance and protect your files from drive failure by keeping more than one copy. Two-way mirror spaces make two copies of your files and can tolerate one drive failure, while three-way mirror spaces can tolerate two drive failures.
-
The president of your university asks you to set up a service website for students who live in dorms. The website’s official launch date is in two days, and you do not have the resources needed to set up the server infrastructure and develop the system.
You need a cloud-based solution than can have the servers and storage available in two days.
Which Microsoft cloud solution achieves this goal?
- Microsoft Intune
- Microsoft Azure
- Achieve Directory
- Microsoft OneDrive
Explanation:Microsoft Azure is a cloud computing platform and infrastructure, created by Microsoft, for building, deploying and managing applications and services through a global network of Microsoft-managed datacenters.
Microsoft Azure services include: Websites: High density hosting of websites. -
This question requires that you evaluate the underlined text to determine if it is correct.
The “ExFAT” file system can automatically verify and auto correct data to avoid file system errors.
Instructions: Review the underlined text. If it makes the statement correct, select “No change is needed”. If the statement is incorrect, select the answer choice than makes the statement correct.
- No change is needed
- NTFS
- FAT32
- ReFS
Explanation:Resilient File System (ReFS) is a Microsoft proprietary file system introduced with Windows Server 2012 with the intent of becoming the “next generation” file system after NTFS. ReFS key design advantages are intended to include automatic integrity checking and data scrubbing, removing the need for chkdsk and protecting against data degradation.
Incorrect answers:
Not A: exFAT (Extended File Allocation Table) is a Microsoft file system optimized for flash drives. exFAT can be used where the NTFS file system is not a feasible solution (due to data structure overhead), or where the file size limit of the standard FAT32 file system is unacceptable. -
What are two ways to lower the risk of a virus or malware infection? Choose two.
- Enable the Windows firewall
- Use only HTTPS while web surfing
- Keep the system updated
- Install a download manager
-
DRAG DROP
You are setting up the networking for a single-site motel. For three different classes of users, you need to specify the most privileged network segment each can access.
Match each network to the class of users that cam access it.
Instructions: To answer, drag the appropriate network from the column of the left to the class of users on the right. Each network may be used once, more than once, or not at all. Each correct match is worth one point.
98-368 Part 02 Q12 007 Question 
98-368 Part 02 Q12 007 Answer Explanation:* Guest have only public access.
* Only the Employees have access to the private network.
* An extranet is a private network that uses Internet technology and the public telecommunication system to securely share part of a business’s information or operations with suppliers, vendors, partners, customers, or other businesses. -
What is an example of the way in which a Trojan horse commonly spreads to other computers?
- It inserts copies of itself into other computer programs
- It traverses a network by exploiting a vulnerability
- It pretends to be a document from a friend
- It downloads from an infected web page
Explanation:Trojan horses are commonly found on websites that offer free software, such as shareware programs. These communal gathering spots on the Web give Trojan horse writers a degree of anonymity along with the chance of attacking as many random victims as possible. Since website operators rarely have time to thoroughly examine every file posted, an occasional Trojan horse can slip through the checking procedures unnoticed.
-
When you copy a file from one NTFS file system partition to a different NTFS partition, what happens to the file permissions of the copied file?
- They are the combined permissions of the original file and destination folder
- They inherit the permissions of the destination folder
- They remain the same as the original
- They are removed, and only the creator is given full control
Explanation:When you copy a protected file to a folder on the same, or a different volume, it inherits the permissions of the target directory.
-
Which type of information about users does biometrics evaluate?
- phrases a user has memorized
- where a user is located
- physical characteristics of a user
- objects a user carries with him or her
Explanation:Biometrics refers to authentication techniques that rely on measurable physical characteristics that can be automatically checked.
Note: There are several types of biometric identification schemes:
face: the analysis of facial characteristics
fingerprint: the analysis of an individual’s unique fingerprints
hand geometry: the analysis of the shape of the hand and the length of the fingers
retina: the analysis of the capillary vessels located at the back of the eye
iris: the analysis of the colored ring that surrounds the eye’s pupil
signature: the analysis of the way a person signs his name.
vein: the analysis of pattern of veins in the back if the hand and the wrist
voice: the analysis of the tone, pitch, cadence and frequency of a person’s voice. -
This question requires that you evaluate the underlined text to determine if it is correct.
When you access a file located on a shared resource, the “most restrictive” permissions take precedence.
Instructions: Review the underlined text. If it makes the statement correct, select “No change is needed”. If the statement is incorrect, select the answer choice than makes the statement correct.
- No change is needed.
- ACL
- NTFS
- share
Explanation:When using share permissions and NTFS permissions together, if there is a conflict in the configuration, the most restrictive permission prevails.
-
Which is a feature Active Directory Rights Management Services (AD RMS)?
- manages Digital Rights Media (DRM) for digital media
- provides a permissions system that works with any cloud-based storage solution
- manages share and file permissions on all servers in enterprise
- allow users to define who can open, modify, print, or forward a document
Explanation:Windows Rights Management Services (also called Rights Management Services, Active Directory Rights Management Services or RMS) is a form of Information Rights Management used on Microsoft Windows that uses encryption and a form of selective functionality denial for limiting access to documents such as corporate e-mail, Word documents, and web pages, and the operations authorized users can perform on them. Companies can use this technology to encrypt information stored in such document formats, and through policies embedded in the documents, prevent the protected content from being decrypted except by specified people or groups, in certain environments, under certain conditions, and for certain periods of time.
-
You have an external monitor connected to a laptop computer that is running Windows 10. The monitors are configured to provide a panoramic display that continues across both monitors.
You want to move the system tray to the secondary monitor. Both monitors must continue to display screen data.
Which Display setting you select?
- Custom scaling
- Show only on 2
- Extend desktop to this display
- Make this my main display
-
Your parents want you to help them protect a tax return file that is on their computer. You use BitLocker to encrypt the hard drive that contains the file. You then make a backup copy of the file.
What will occur if you attempt to copy the backup copy to a USB flash drive?
- The backup copy will remain encrypted
- BitLocker will encrypt the USB flash drive
- BitLocker will prevent you from moving the file
- The backup copy will be decrypted
-
HOTSPOT
A computer running Microsoft Windows 10 Pro includes the following disk partitions:
– Drive C: internal hard disk formatted as NTFS.
– Drive D: internal hard disk formatted as NTFS.
– Drive F: USB disk formatted as FAT32.You enable encrypting file system (EFS) encryption on a folder on drive C:.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
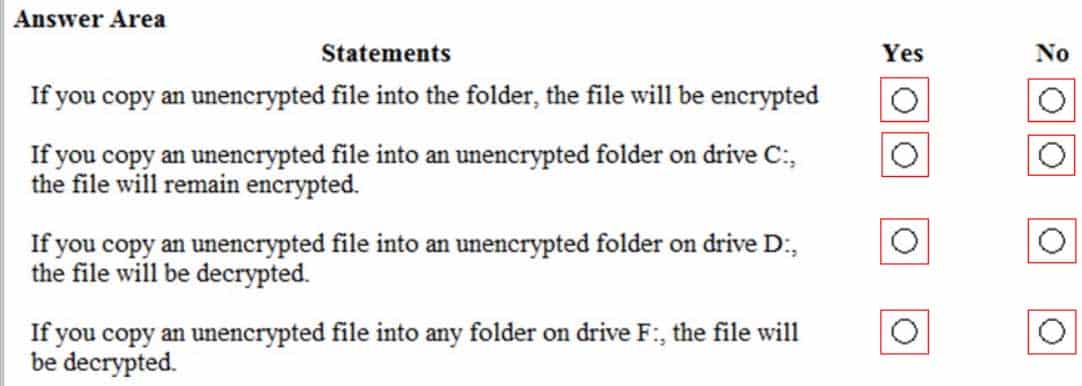
98-368 Part 02 Q20 008 Question 
98-368 Part 02 Q20 008 Answer