AZ-303 : Microsoft Azure Architect Technologies : Part 05
-
HOTSPOT
You have Azure subscription that contains a virtual network named VNet1. VNet1 includes a VPN gateway, uses an IP address space of 10.0.0.0/16 and contains the subnets in the following table.
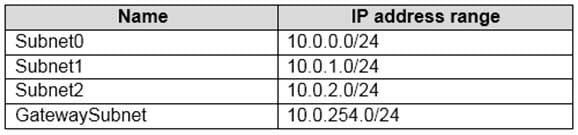
AZ-303 Microsoft Azure Architect Technologies Part 05 Q01 098 Subnet1 contains a virtual appliance named VM1 that operates as a router.
You create a routing table named RT1.
You need to route all inbound traffic from the VPN gateway to VNet1 through VM1.
How should you configure RT1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-303 Microsoft Azure Architect Technologies Part 05 Q01 099 Question 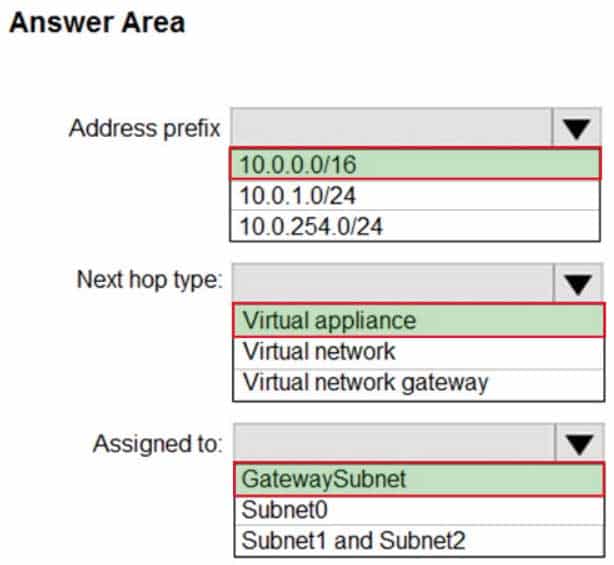
AZ-303 Microsoft Azure Architect Technologies Part 05 Q01 099 Answer -
You manage a solution in Azure that consists of a single application which runs on a virtual machine (VM). Traffic to the application has increased dramatically.
The application must not experience any downtime and scaling must be dynamically defined.
You need to define an auto-scale strategy to ensure that the VM can handle the workload.
Which three options should you recommend? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- Deploy application automatic vertical scaling.
- Create a VM availability set.
- Create a VM scale set.
- Deploy application automatic horizontal scaling.
- Deploy a custom auto-scale implementation.
-
You have an Azure subscription that contains the resource groups shown in the following table.
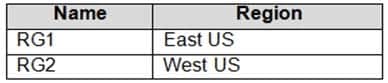
AZ-303 Microsoft Azure Architect Technologies Part 05 Q03 100 The subscription contains the storage accounts shown in the following table.

AZ-303 Microsoft Azure Architect Technologies Part 05 Q03 101 You create a Recovery Services vault named Vault1 in RG1 in the West US location.
You need to identify which storage accounts can be used to archive the diagnostics logs of Vault1.
Which storage accounts should you identify?
- Storage1 only
- Storage2 only
- Storage3 only
- Storage1 or Storage2 only
- Storage1 or Storage3 only
Explanation:
The storage needs to be in the same region as the RSV. -
You have an Azure subscription named Sub1 that has a subscription ID of 12ab3cd4-5e67-8901-f234-g5hi67jkl8m9.
In Sub1, you create an Azure Storage account named storage1 and a table named Table1.
Which URI should you use to access Table1?
- https://storage.core.windons.net/12ab3cd4-5e67-8901-f234-g5hi67jkl8m9/storagel/table1
- https://sub1.core.windows.net/storagel/table1
- https://table1.table.core.windows.net/storage1
- https://storagel.table.core.windows.net/table1
-
You monitor Azure virtual machines by using Azure Monitor.
You plan to restart the virtual machines when CPU usage exceeds 95 percent for more than 30 minutes.
You need to create an alert in Azure Monitor to restart the virtual machines. The solution must minimize administrative effort.
Which type of action should you use in the alert?
- ITSM
- Webhook
- Automation Runbook
- Logic App
Explanation:Automation runbooks allows you to automatically perform standard remediations in response to VM alerts, like restarting or stopping the VM.
Previously, during VM alert rule creation you were able to specify an Automation webhook to a runbook in order to run the runbook whenever the alert triggered. However, this required you to do the work of creating the runbook, creating the webhook for the runbook, and then copying and pasting the webhook during alert rule creation. With this new release, the process is much easier because you can directly choose a runbook from a list during alert rule creation, and you can choose an Automation account which will run the runbook or easily create an account.
-
You have an Azure subscription that contains an Azure Log Analytics workspace.
You have a resource group that contains 100 virtual machines. The virtual machines run Linux.
You need to collect events from the virtual machines to the Log Analytics workspace.
Which Agent configuration setting should you modify?
- Syslog
- Linux performance counters
- custom fields
Explanation:
Syslog is an event logging protocol that is common to Linux. Applications will send messages that may be stored on the local machine or delivered to a Syslog collector. When the Log Analytics agent for Linux is installed, it configures the local Syslog daemon to forward messages to the agent. The agent then sends the message to Azure Monitor where a corresponding record is created. -
Case study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.
Overview
Contoso, Ltd. is a manufacturing company that has offices worldwide. Contoso works with partner organizations to bring products to market.
Contoso products are manufactured by using blueprint files that the company authors and maintains.
Existing Environment
Currently, Contoso uses multiple types of servers for business operations, including the following:
– File servers
– Domain controllers
– Microsoft SQL Server serversYour network contains an Active Directory forest named contoso.com. All servers and client computers are joined to Active Directory.
You have a public-facing application named App1. App1 is comprised of the following three tiers:
– A SQL database
– A web front end
– A processing middle tierEach tier is comprised of five virtual machines. Users access the web front end by using HTTPS only.
Requirements
Planned Changes
Contoso plans to implement the following changes to the infrastructure:
– Move all the tiers of App1 to Azure.
– Move the existing product blueprint files to Azure Blob storage.
– Create a hybrid directory to support an upcoming Microsoft 365 migration project.Technical Requirements
Contoso must meet the following technical requirements:
– Move all the virtual machines for App1 to Azure.
– Minimize the number of open ports between the App1 tiers.
– Ensure that all the virtual machines for App1 are protected by backups.
– Copy the blueprint files to Azure over the Internet.
– Ensure that the blueprint files are stored in the archive storage tier.
– Ensure that partner access to the blueprint files is secured and temporary.
– Prevent user passwords or hashes of passwords from being stored in Azure.
– Use unmanaged standard storage for the hard disks of the virtual machines.
– Ensure that when users join devices to Azure Active Directory (Azure AD), the users use a mobile phone to verify their identity.
– Minimize administrative effort whenever possible.User Requirements
Contoso identifies the following requirements for users:
– Ensure that only users who are part of a group named Pilot can join devices to Azure AD.
– Designate a new user named Admin1 as the service admin for the Azure subscription.
– Admin1 must receive email alerts regarding service outages.
– Ensure that a new user named User3 can create network objects for the Azure subscription.-
HOTSPOT
You need to identify the storage requirements for Contoso.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

AZ-303 Microsoft Azure Architect Technologies Part 05 Q07 102 Question 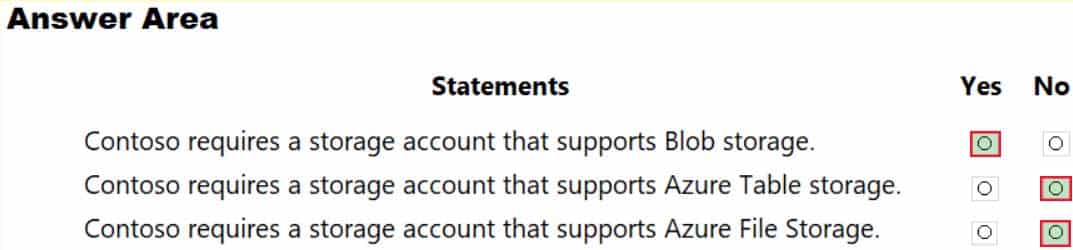
AZ-303 Microsoft Azure Architect Technologies Part 05 Q07 102 Answer Explanation:Box 1: Yes
Scenario: Move the existing product blueprint files to Azure Blob storage.Scenario: Use unmanaged standard storage for the hard disks of the virtual machines.
Page blobs are optimized for writes at random locations within a blob. They also support Unmanaged Disks.Scenario:
SQL Server Data Files in Microsoft Azure enables native support for SQL Server database files stored as blobs. It allows you to create a database in SQL Server running in on-premises or in a virtual machine in Microsoft Azure with a dedicated storage location for your data in Microsoft Azure Blob storage.Box 2: No
Box 3: No
-
You need to move the blueprint files to Azure.
What should you do?
- Use the Azure Import/Export service.
- Generate a shared access signature (SAS). Map a drive, and then copy the files by using File Explorer.
- Use Azure Storage Explorer to copy the files.
- Generate an access key. Map a drive, and then copy the files by using File Explorer.
Explanation:Scenario:
– Copy the blueprint files to Azure over the Internet.
– Ensure that the blueprint files are stored in the archive storage tier.
– Ensure that partner access to the blueprint files is secured and temporary.Copy the blueprint files to Azure over the Internet.
To mount an Azure file share, you will need the primary (or secondary) storage key. SAS keys are not currently supported for mounting.Incorrect Answers:
A: Azure Import/Export service is used to securely import large amounts of data to Azure Blob storage and Azure Files by shipping disk drives to an Azure datacenter.
B: You cannot map a drive with a SAS signature. -
You need to implement a backup solution for App1 after the application is moved.
What should you create first?
- an Azure Backup Server
- a Recovery Services vault
- a recovery plan
- a backup policy
Explanation:Scenario: Ensure that all the virtual machines for App1 are protected by backups.
You can back up Azure VMs using a couple of methods:
– Single Azure VM: You can back up an Azure VM directly from the VM settings.
– Multiple Azure VMs: You can set up a Recovery Services vault and configure backup for multiple Azure VMs.
-
-
Case Study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.Overview. General Overview
Litware, Inc. is a medium-sized finance company. Litware recently acquired a financial services company named Fabrikam, Ltd.
Overview. Physical Locations
Litware has a datacenter in Boston. Fabrikam has a datacenter in San Francisco.
Existing Environment. Identity Environment
The network of Litware contains an Active Directory forest named Litware.com that syncs to an Azure Active Directory (Azure AD) tenant named Litware.com by using Azure AD Connect.
Azure AD Seamless Single Sign-on (Azure AD Seamless SSO) is enabled for the Litware.com tenant.
Users at Litware have a UPN suffix of Litware.com
Litware has an internal certification authority (CA) that is trusted by all devices.
The network of Fabrikam contains an Active Directory forest named fabrikam.com. Users at Fabrikam have a UPN suffix of fabrikam.com.
Existing Environment. Azure Environment
Litware has an Azure subscription named Sub1 that is linked to the Litware.com tenant. Sub1 contains the resources shown in the following table.
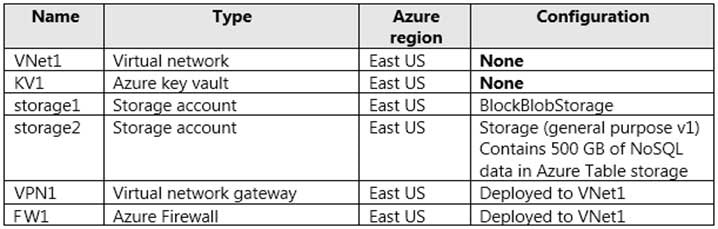
AZ-303 Microsoft Azure Architect Technologies Part 05 Q08 103 Litware has Azure Resource Manager (ARM) templates that deploy Azure Policy definitions and assignments to a management group.
Fabrikam does NOT have an Azure environment.
Existing Environment. On-Premises Environment
The on-premises network of Litware contains the resources shown in the following table.
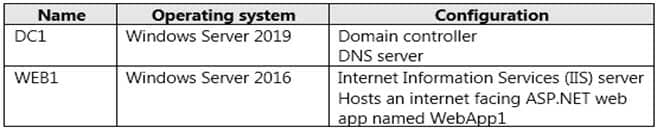
AZ-303 Microsoft Azure Architect Technologies Part 05 Q08 104 The on-premises network of Fabrikam contains a domain member server named SERVER1 that runs Windows Server 2019.
Existing Environment. Network Environment
Litware has a site-to-site VPN connection to VNet1.
The Litware and Fabrikam datacenters are not connected.
Requirements. Planned Changes
Litware plans to implement the following changes:
– Establish a trust relationship between the Litware and Fabrikam forests.
– Migrate data from the on-premises NoSQL datastores to Azure Table storage.
– Containerize WebApp1 and deploy the app to an Azure Kubernetes Service (AKS) cluster on VNet1.
– Create an Azure blueprint named BP1 and use the blueprint to provision a resource group named RG1.Requirements. Deployment Requirements
Litware identifies the following deployment requirements:
– The existing ARM templates must be used for deployments to Sub1.
– WebApp1 must be deployed to the AKS cluster without having to change the source code.Requirements. Authentication and Authorization Requirements
Litware identifies the following authentication and authorization requirements:
– The Fabrikam users must be able to authenticate to the Litware.com tenant by using Azure AD Seamless SSO.
– The Fabrikam users and the Litware users must be able to manage the Azure resources in Sub1.
– Company policy must prohibit the creation of guest user accounts in the Litware.com tenant.
– You must be able to configure deny permissions for RG1 and for the resources in RG1.
– WebApp1 running on the AKS cluster must be able to retrieve secrets from KV1.Requirements. Security Requirements
Litware identifies the following security requirements:
– On-premises Litware users must access KVI by using the private IP address of the key vault.
– Azure virtual machines must have all their disks encrypted, including the temporary disks.
– Azure Storage must encrypt all data by using keys issued by the internal CA of Litware.
– Inbound HTTPS traffic to WebApp1 must be inspected for SQL injection attacks.
– The principle of least privilege must be used.-
You need to ensure that the NoSQL data is encrypted. The solution must meet the security requirements.
What should you do first?
- Upgrade storage2 to StorageV2 (general purpose v2).
- Create a new general-purpose v2 storage account.
- Create a new Azure Blob storage account.
- Modify the Encryption settings of storage2.
-
You need to ensure that you can implement Azure AD Seamless SSO for Fabrikam. The solution must meet the following requirements:
– Support the planned changes.
– Meet the authentication and authorization requirements.What should you do?
- Create a new Azure AD tenant named fabrikam.com
- From the Fabrikam forest, configure an additional UPN suffix of Litware.com.
- From the Fabrikam forest, configure all users to have a UPN suffix of Litware.com.
- From the Litware.com tenant, add a custom domain named fabrikam com.
-
DRAG DROP
You need to ensure that the virtual machine disks are encrypted. The solution must meet the security requirements.
Which three actions should you perform in Sub1 in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
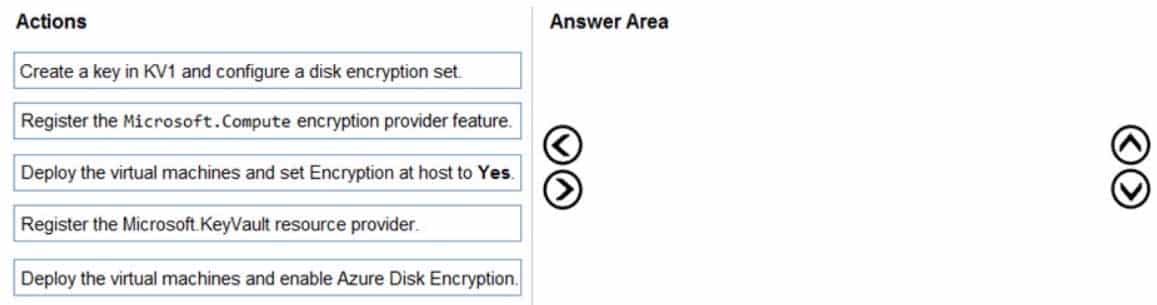
AZ-303 Microsoft Azure Architect Technologies Part 05 Q08 105 Question 
AZ-303 Microsoft Azure Architect Technologies Part 05 Q08 105 Answer -
You need to configure Azure AD Seamless SSO for Fabrikam. The solution must meet the authentication and authorization requirements.
What should you install first?
- the Azure AD Connect provisioning agent on SERVER1
- the Azure AD Connect provisioning agent on DC1
- Azure AD Connect in staging mode on SERVER1
- an Azure AD Connect primary server on SERVER1
Explanation:
The Litware and Fabrikam datacenters are not connected.
Azure AD Connect Cloud Sync provides support for synchronizing to an Azure AD tenant from a multi-forest disconnected Active Directory forest environment.
-
-
HOTSPOT
You have an Azure Active Directory (Azure AD) tenant.
You need to create a conditional access policy that requires all users to use multi-factor authentication when they access the Azure portal.
Which three settings should you configure? To answer, select the appropriate settings in the answer area.
NOTE: Each correct selection is worth one point.

AZ-303 Microsoft Azure Architect Technologies Part 05 Q09 106 Question 
AZ-303 Microsoft Azure Architect Technologies Part 05 Q09 106 Answer -
You are implementing authentication for applications in your company. You plan to implement self-service password reset (SSPR) and multifactor authentication (MFA) in Azure Active Directory (Azure AD).
You need to select authentication mechanisms that can be used for both MFA and SSPR.
Which two authentication methods should you use? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- Authenticator app
- Email addresses
- App passwords
- Short Message Service (SMS) messages
- Security questions
Explanation:The following authentication mechanisms can be used for both MFA and SSPR:
– Short Message Service (SMS) messages
– Azure AD passwords
– Microsoft Authenticator app
– Voice callIncorrect Answers:
B, E: The following authentication mechanisms are used for SSPR only:
– Email addresses
– Security questionsE: App passwords authentication mechanisms can be used for MFA only, but only in certain cases.
-
Your company has the groups shown in the following table.

AZ-303 Microsoft Azure Architect Technologies Part 05 Q11 107 The company has an Azure subscription that is associated with an Azure Active Directory (Azure AD) tenant named contoso.com.
An administrator named Admin1 attempts to enable Enterprise State Roaming for all the users in the Managers group.
Admin1 reports that the options for Enterprise State Roaming are unavailable from Azure AD.
You verify that Admin1 is assigned the Global administrator role.
You need to ensure that Admin1 can enable Enterprise State Roaming.
What should you do?
- Assign an Azure AD Privileged Identity Management (PIM) role to Admin1.
- Purchase an Azure Rights Management (Azure RMS) license for each user in the Managers group.
- Enforce Azure Multi-Factor Authentication (MFA) for Admin1.
- Purchase an Azure AD Premium P1 license for each user in the Managers group.
Explanation:
Enterprise State Roaming is available to any organization with an Azure AD Premium or Enterprise Mobility + Security (EMS) license. -
HOTSPOT
You plan to implement an access review to meet the following requirements:
The access review must be enforced until otherwise configured.
Each user or group that has access to the Azure environment must be in the scope of the access review.
The access review must be completed within two weeks.
A lack of response must not cause changes in the operational environment.An administrator creates the access review shown in the answer area.
Which two sections of the access review should you modify to meet the requirements? To answer, select the appropriate sections in the answer area.
NOTE: Each correct selection is worth one point.

AZ-303 Microsoft Azure Architect Technologies Part 05 Q12 108 question 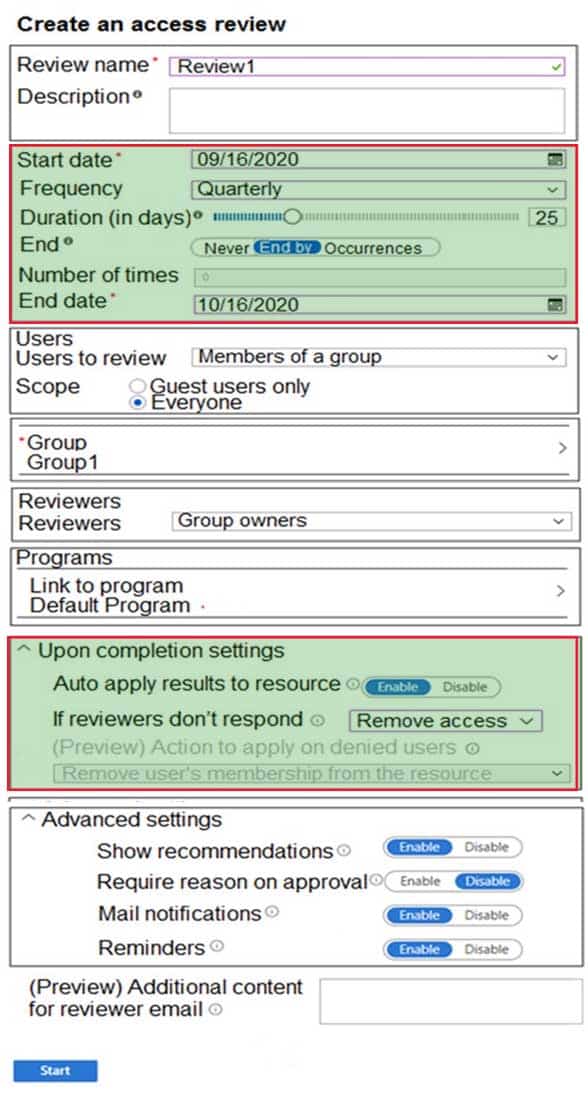
AZ-303 Microsoft Azure Architect Technologies Part 05 Q12 108 Answer Explanation:Area 1: Start date..End Date
The access review must be enforced until otherwise configured. We set End: NeverThe access review must be completed within two weeks. We set Duration (in days) to 14
Area 2: Upon completion settings
A lack of response must not cause changes in the operational environment. We set ‘If reviewers don’t respond: No change (which leave user’s access unchanged) -
HOTSPOT
You have a hierarchy of management groups and Azure subscriptions as shown in the following table.

AZ-303 Microsoft Azure Architect Technologies Part 05 Q13 109 You create the Azure resources shown in the following table.

AZ-303 Microsoft Azure Architect Technologies Part 05 Q13 110 You have the Owner role. You assign roles to users as shown in the following table.

AZ-303 Microsoft Azure Architect Technologies Part 05 Q13 111 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

AZ-303 Microsoft Azure Architect Technologies Part 05 Q13 112 Question 
AZ-303 Microsoft Azure Architect Technologies Part 05 Q13 112 Answer Explanation:Box 1: Yes
You have assigned the role, so you can remove it.Box 2: Yes
Contributor role: Grants full access to manage all resources, but does not allow you to assign roles in Azure RBAC.Box 3: No
-
You have an Azure subscription that includes the resources shown in the following table.
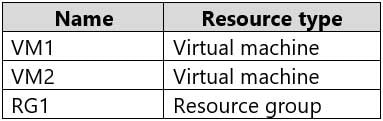
AZ-303 Microsoft Azure Architect Technologies Part 05 Q14 113 You attempt to add a role assignment to RG1 as shown in the following exhibit.
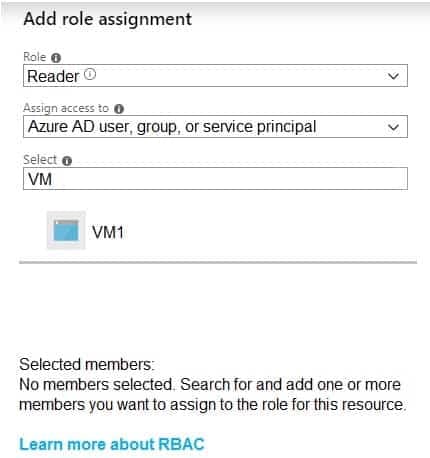
AZ-303 Microsoft Azure Architect Technologies Part 05 Q14 114 What should you do to ensure that you can assign VM2 the Reader role for the resource group?
- Configure just in time (JIT) VM access on VM2.
- Configure Access control (IAM) on VM2.
- Assign a managed identity to VM2.
- Modify the Reader role at the subscription level.
Explanation:After you’ve configured an Azure resource with a managed identity, you can give the managed identity access to another resource, just like any security principal.
Use Azure RBAC to assign a managed identity access to another resource
After you’ve enabled managed identity on an Azure resource, such as an Azure VM or Azure virtual machine scale set:
1. Sign in to the Azure portal using an account associated with the Azure subscription under which you have configured the managed identity.
2. Navigate to the desired resource on which you want to modify access control. In this example, we are giving an Azure virtual machine access to a storage account, so we navigate to the storage account.
3. Select the Access control (IAM) page of the resource, and select + Add role assignment. Then specify the Role, Assign access to, and specify the corresponding Subscription. Under the search criteria area, you should see the resource. Select the resource, and select Save. -
You have an Azure Active Directory (Azure AD) tenant linked to an Azure subscription. The tenant contains a group named Admins.
You need to prevent users, except for the members of Admins, from using the Azure portal and Azure PowerShell to access the subscription.
What should you do?
- From Azure AD, configure the User settings.
- From Azure AD, create a conditional access policy.
- From the Azure subscription, assign an Azure policy.
- From the Azure subscription, configure Access control (IAM).
Explanation:Typically, you use Conditional Access to control access to your cloud apps. You can also set up policies to control access to Azure management.
The policy you create applies to all Azure management endpoints, including the following:
– Azure portal
– Azure Resource Manager provider
– Classic Service Management APIs
– Azure PowerShell
– Visual Studio subscriptions administrator portal
– Azure DevOps
– Azure Data Factory portalTo create a policy for Azure management, you select Microsoft Azure Management under Cloud apps when choosing the app to which to apply the policy.
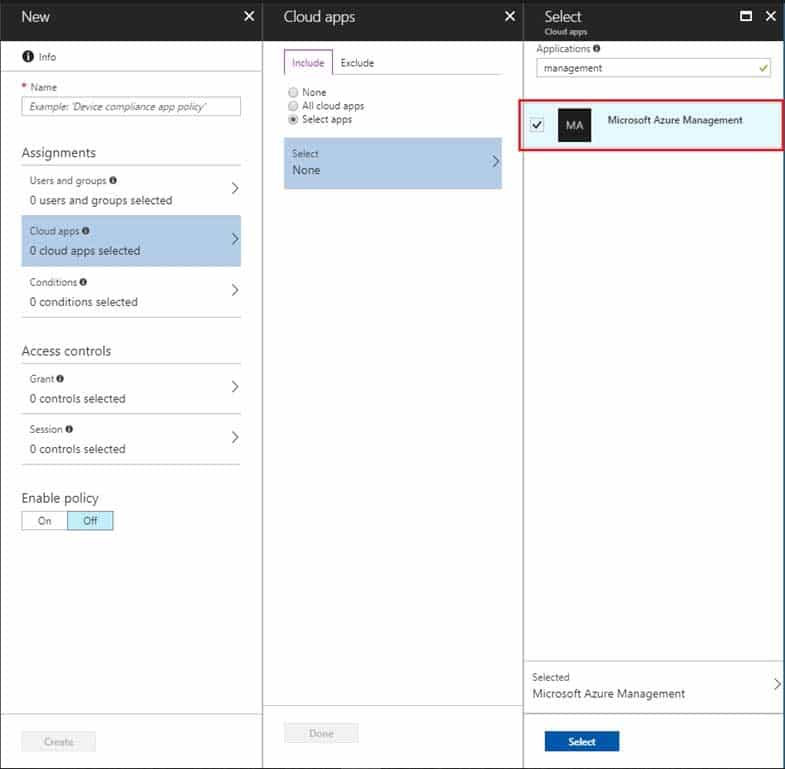
AZ-303 Microsoft Azure Architect Technologies Part 05 Q15 115 Incorrect Answers:
A: From User Settings you can only restrict access to Azure Portal, not access to Azure Powershell.Note: Microsoft allows restricting standard user access to Azure Active Directory administration portal.
1. Log in to Azure portal as Global Administrator
2. Go to Azure Active Directory | User Settings
3. Then click on Yes under Restrict access to Azure AD administration portal
AZ-303 Microsoft Azure Architect Technologies Part 05 Q15 116 -
You have Azure virtual machines deployed to three Azure regions. Each region contains a single virtual network that has four virtual machines on the same subnet. Each virtual machine runs an application named App1. App1 is accessible by using HTTPS. Currently, the virtual machines are inaccessible from the internet.
You need to use Azure Front Door to load balance requests for App1 across all the virtual machines.
Which additional Azure service should you provision?
- Azure Traffic Manager
- an internal Azure Load Balancer
- a public Azure Load Balancer
- Azure Private Link
Explanation:
Can we deploy Azure Load Balancer behind Front Door?
Azure Front Door needs a public VIP or a publicly available DNS name to route the traffic to. Deploying an Azure Load Balancer behind Front Door is a common use case. -
You have Azure virtual machines that have Update Management enabled. The virtual machines are configured as shown in the following table.

AZ-303 Microsoft Azure Architect Technologies Part 05 Q17 117 You need to ensure that all critical and security updates are applied to each virtual machine every month.
What is the minimum number of update deployments you should create?
- 4
- 6
- 2
- 1
Explanation:
One for the Windows VMs, and for each type of Linux VM. -
You have an Azure subscription.
You create a custom role in Azure by using the following Azure Resource Manager template.
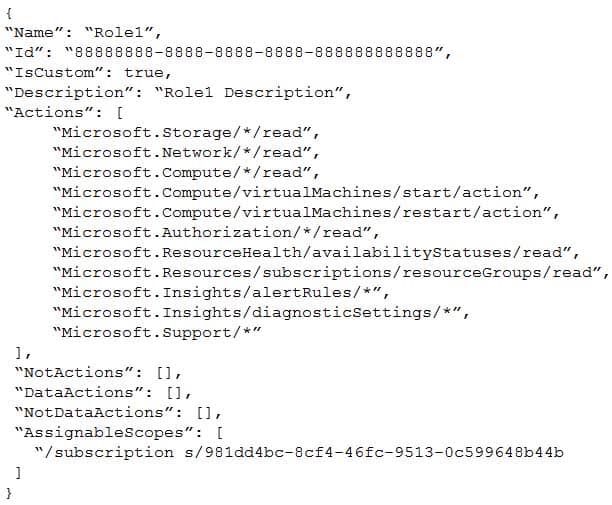
AZ-303 Microsoft Azure Architect Technologies Part 05 Q18 118 You assign the role to a user named User1.
Which action can User1 perform?
- Create virtual machines.
- Create resource groups.
- Delete virtual machines.
- Create support requests.
Explanation:
The “Microsoft.Support/*” operation will allow the user to create support tickets. -
You have an Azure SQL database named Db1 that runs on an Azure SQL server named SQLserver1.
You need to ensure that you can use the query editor on the Azure portal to query Db1.
What should you do?
- Copy the ADO.NET connection string of Db1 and paste the string to the query editor.
- Approve private endpoint connections for SQLserver1.
- Modify the Advanced Data Security settings of Db1.
- Configure the Firewalls and virtual networks settings for SQLserver1.
- DRAG DROP
You have an Azure subscription that contains the resources shown in the following table.
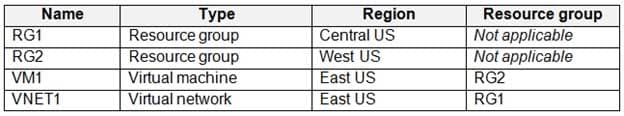
AZ-303 Microsoft Azure Architect Technologies Part 05 Q20 119 In RG2, you need to create a new virtual machine named VM2 that will connect to VNET1. VM2 will use a network interface named VM2_Interface.
In which region should you create VM2 and VM2_Interface? To answer, drag the appropriate regions to the correct targets. Each region may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
AZ-303 Microsoft Azure Architect Technologies Part 05 Q20 120 Question 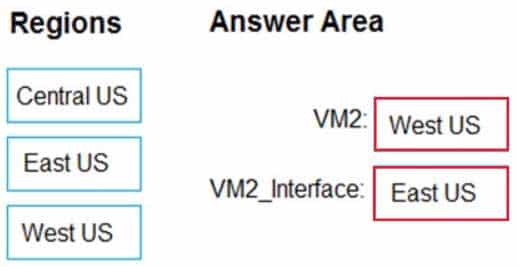
AZ-303 Microsoft Azure Architect Technologies Part 05 Q20 120 Answer Explanation:VM2: West US
In RG2, which is in West US, you need to create a new virtual machine named VM2.VM2_interface: East US
VM2 will use a network interface named VM2_Interface to connect to VNET1, which is in East US.