AZ-303 : Microsoft Azure Architect Technologies : Part 07
-
You have an Azure subscription that contains an Azure key vault named KeyVault1 and the virtual machines shown in the following table.
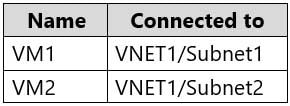
AZ-303 Microsoft Azure Architect Technologies Part 07 Q01 134 KeyVault1 has an access policy that provides several users with Create Key permissions.
You need to ensure that the users can only register secrets in KeyVault1 from VM1.
What should you do?
- Create a network security group (NSG) that is linked to Subnet1.
- Configure the Firewall and virtual networks settings for KeyVault1.
- Modify the access policy for KeyVault1.
- Configure KeyVault1 to use a hardware security module (HSM).
Explanation:
You grant data plane access by setting Key Vault access policies for a key vault.
Note 1: Grant our VM’s system-assigned managed identity access to the Key Vault.
1. Select Access policies and click Add new.
2. In Configure from template, select Secret Management.
3. Choose Select Principal, and in the search field enter the name of the VM you created earlier. Select the VM in the result list and click Select.
4. Click OK to finishing adding the new access policy, and OK to finish access policy selection.Note 2: Access to a key vault is controlled through two interfaces: the management plane and the data plane. The management plane is where you manage Key Vault itself. Operations in this plane include creating and deleting key vaults, retrieving Key Vault properties, and updating access policies. The data plane is where you work with the data stored in a key vault. You can add, delete, and modify keys, secrets, and certificates.
-
HOTSPOT
You have an Azure subscription named Subscription1 that contains a virtual network named VNet1.
You add the users in the following table.
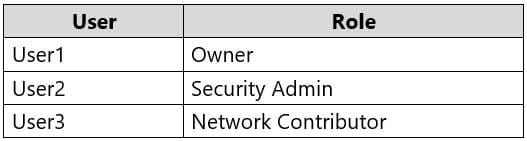
AZ-303 Microsoft Azure Architect Technologies Part 07 Q02 135 Which user can perform each configuration? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
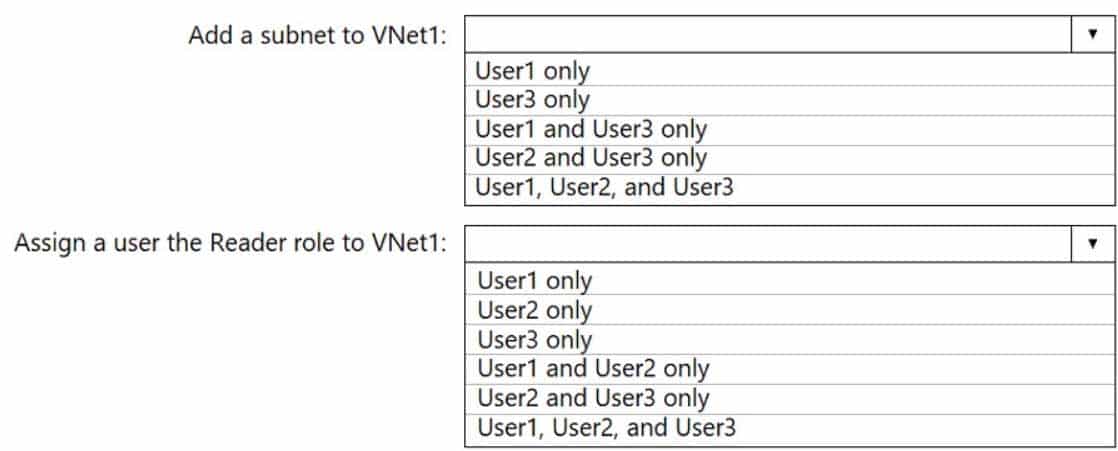
AZ-303 Microsoft Azure Architect Technologies Part 07 Q02 136 Question 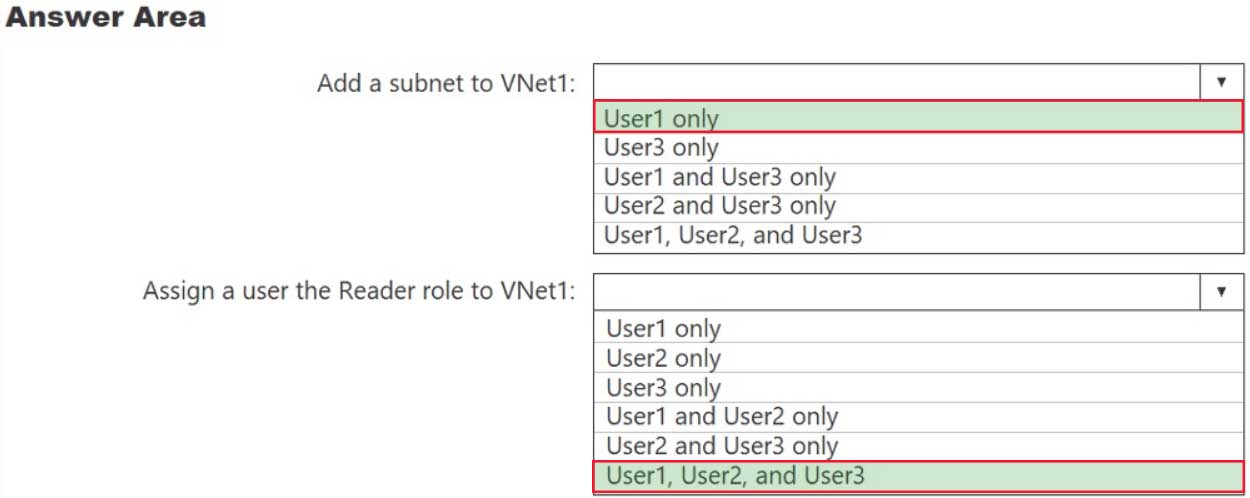
AZ-303 Microsoft Azure Architect Technologies Part 07 Q02 136 Answer Explanation:Box 1: User1 only.
User1: The Owner Role lets you manage everything, including access to resources.
Not User3: The Network Contributor role lets you manage networks, but not access to them.Box 2: User1 and User2 only
The Security Admin role: In Security Center only: Can view security policies, view security states, edit security policies, view alerts and recommendations, dismiss alerts and recommendations. -
You have an Azure subscription that contains the Azure SQL Database servers shown in the following table.

AZ-303 Microsoft Azure Architect Technologies Part 07 Q03 137 The SQL Database servers have the elastic pools shown in the following table.

AZ-303 Microsoft Azure Architect Technologies Part 07 Q03 138 SQL1 has the SQL databases shown in the following table.

AZ-303 Microsoft Azure Architect Technologies Part 07 Q03 139 What will occur if you add DB1 to Pool1?
- The vCores on DB1 will decrease to two.
- The maximum data size of Pool1 will increase to 22 GB.
- The maximum data size of DB1 will decrease to 6 GB.
- The vCores on Pool1 will increase to four.
-
HOTSPOT
Your network contains an Active Directory domain that is synced to Azure Active Directory (Azure AD) as shown in the following exhibit.
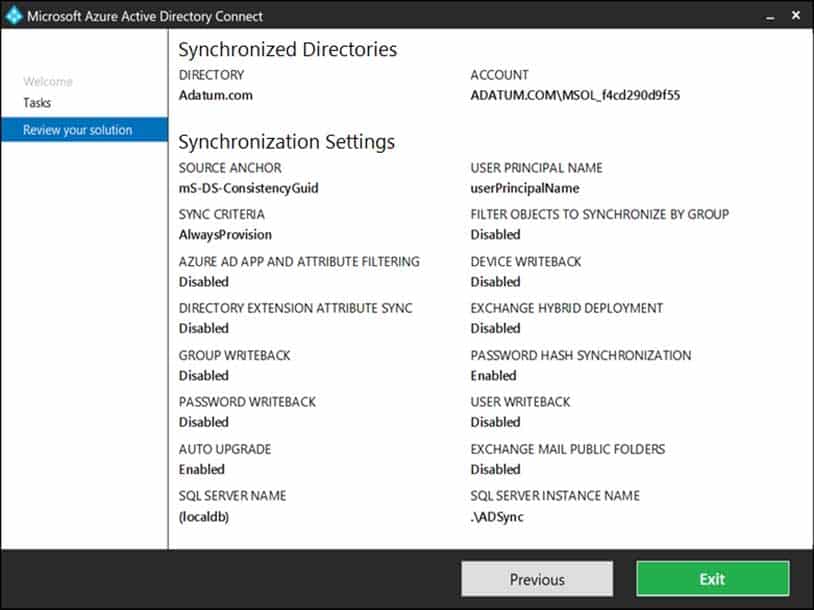
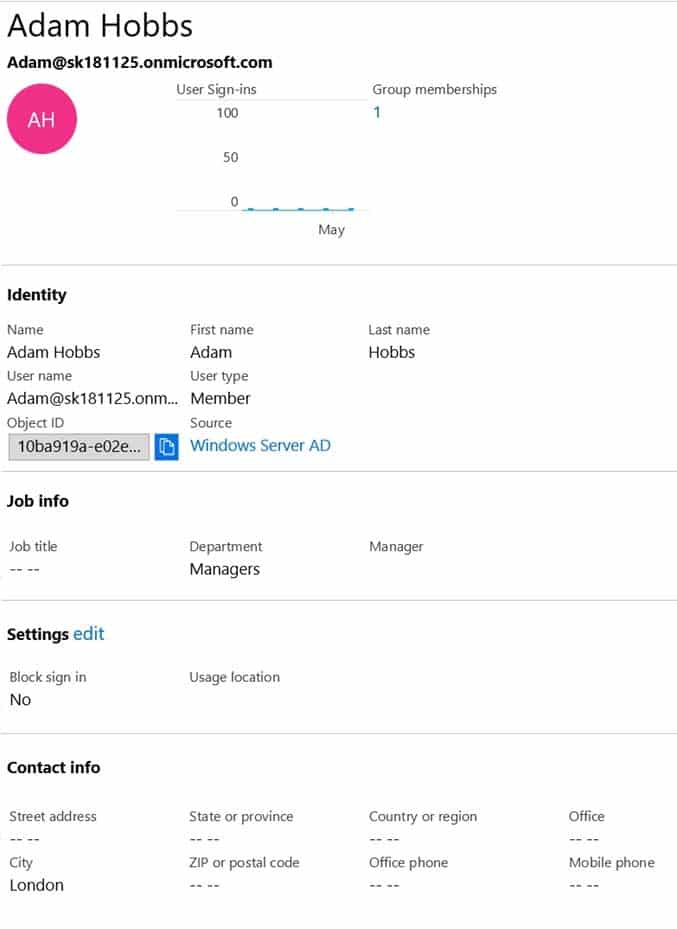
AZ-303 Microsoft Azure Architect Technologies Part 07 Q04 140 You have a user account configured as shown in the following exhibit.
AZ-303 Microsoft Azure Architect Technologies Part 07 Q04 141 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
AZ-303 Microsoft Azure Architect Technologies Part 07 Q04 142 Question 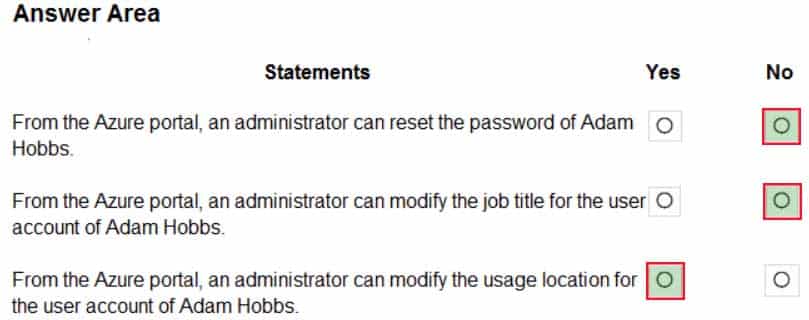
AZ-303 Microsoft Azure Architect Technologies Part 07 Q04 142 Answer Explanation:Box 1: No
Password writeback is disabled.Note: Having a cloud-based password reset utility is great but most companies still have an on-premises directory where their users exist. How does Microsoft support keeping traditional on-premises Active Directory (AD) in sync with password changes in the cloud? Password writeback is a feature enabled with Azure AD Connect that allows password changes in the cloud to be written back to an existing on-premises directory in real time.
Box 2: No
Box 3: Yes
Yes, there is an Edit link for Location Info. -
HOTSPOT
You have an Azure subscription named Subscription1.
In Subscription1, you create an alert rule named Alert1.
The Alert1 action group is configured as shown in the following exhibit.
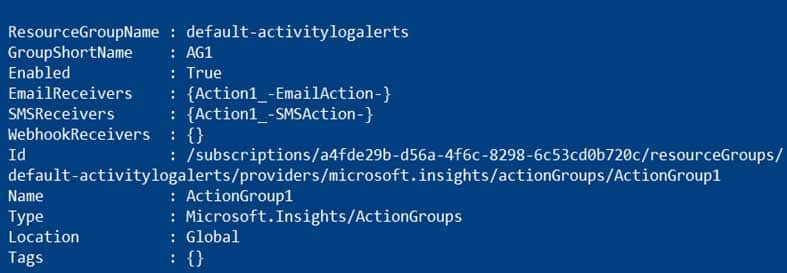
AZ-303 Microsoft Azure Architect Technologies Part 07 Q05 143 Alert1 alert criteria is triggered every minute.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
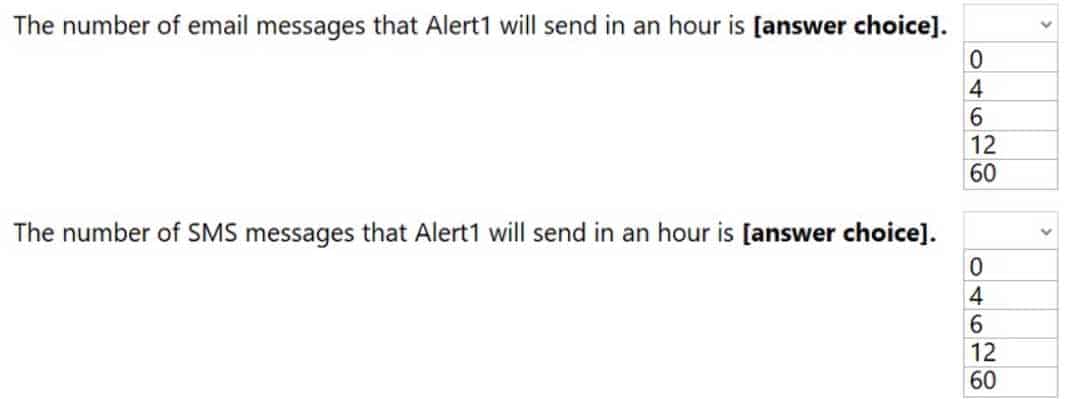
AZ-303 Microsoft Azure Architect Technologies Part 07 Q05 144 Question 
AZ-303 Microsoft Azure Architect Technologies Part 07 Q05 144 Answer Explanation:Box 1: 60
One alert per minute will trigger one email per minute.Box 2: 12
No more than 1 SMS every 5 minutes can be send, which equals 12 per hour.Note: Rate limiting is a suspension of notifications that occurs when too many are sent to a particular phone number, email address or device. Rate limiting ensures that alerts are manageable and actionable.
The rate limit thresholds are:
SMS: No more than 1 SMS every 5 minutes.
Voice: No more than 1 Voice call every 5 minutes.
Email: No more than 100 emails in an hour.
Other actions are not rate limited. -
You download an Azure Resource Manager template based on an existing virtual machine. The template will be used to deploy 100 virtual machines.
You need to modify the template to reference an administrative password. You must prevent the password from being stored in plain text.
What should you create to store the password?
- an Azure Key Vault and an access policy
- Azure Active Directory (AD) Identity Protection and an Azure policy
- a Recovery Services vault and a backup policy
- an Azure Storage account and an access policy
-
You have an Azure Storage account named storage1 that is accessed by several applications.
An administrator manually rotates the access keys for storage1.
After the rotation, the applications fail to access the storage account.
A developer manually modifies the applications to resolve the issue.
You need to implement a solution to rotate the access keys automatically. The solution must minimize the need to update the applications once the solution is implemented.
What should you include in the solution?
- an Azure AD enterprise application
- Azure Key Vault
- Azure Logic Apps
- an Azure Desired State Configuration (DSC) extension
Explanation:
Microsoft recommends that you use Azure Key Vault to manage your access keys, and that you regularly rotate and regenerate your keys. Using Azure Key Vault makes it easy to rotate your keys without interruption to your applications. You can also manually rotate your keys. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription.
You have an on-premises file server named Server1 that runs Windows Server 2019.
You manage Server1 by using Windows Admin Center.
You need to ensure that if Server1 fails, you can recover Server1 files from Azure.
Solution: You create an Azure Storage account and an Azure Storage Sync service. You configure Azure File Sync for Server1.
Does this meet the goal?
- Yes
- No
Explanation:Use Azure File Sync to centralize your organization’s file shares in Azure Files, while keeping the flexibility, performance, and compatibility of an on-premises file server. Azure File Sync transforms Windows Server into a quick cache of your Azure file share.
Azure Files offers fully managed file shares in the cloud that are accessible via the industry standard Server Message Block (SMB) protocol. Azure file shares can be mounted concurrently by cloud or on-premises deployments of Windows, Linux, and macOS. Additionally, Azure file shares can be cached on Windows Servers with Azure File Sync for fast access near where the data is being used.
Azure file shares can be used to:
Replace or supplement on-premises file servers:
Azure Files can be used to completely replace or supplement traditional on-premises file servers or NAS devices. Popular operating systems such as Windows, macOS, and Linux can directly mount Azure file shares wherever they are in the world. Azure file shares can also be replicated with Azure File Sync to Windows Servers, either on-premises or in the cloud, for performance and distributed caching of the data where it’s being used. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription.
You have an on-premises file server named Server1 that runs Windows Server 2019.
You manage Server1 by using Windows Admin Center.
You need to ensure that if Server1 fails, you can recover Server1 files from Azure.
Solution: From the Azure portal, you create a Recovery Services vault. On Server1, you install the Azure Backup agent and you successfully perform a backup.
Does this meet the goal?
- Yes
- No
Explanation:Instead use Azure Storage Sync service and configure Azure File.
Use Azure File Sync to centralize your organization’s file shares in Azure Files, while keeping the flexibility, performance, and compatibility of an on-premises file server. Azure File Sync transforms Windows Server into a quick cache of your Azure file share.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription.
You have an on-premises file server named Server1 that runs Windows Server 2019.
You manage Server1 by using Windows Admin Center.
You need to ensure that if Server1 fails, you can recover Server1 files from Azure.
Solution: You register Windows Admin Center in Azure and configure Azure Backup.
Does this meet the goal?
- Yes
- No
Explanation:Instead use Azure Storage Sync service and configure Azure File.
Use Azure File Sync to centralize your organization’s file shares in Azure Files, while keeping the flexibility, performance, and compatibility of an on-premises file server. Azure File Sync transforms Windows Server into a quick cache of your Azure file share.
-
HOTSPOT
You need to design an authentication solution that will integrate on-premises Active Directory and Azure Active Directory (Azure AD). The solution must meet the following requirements:
– Active Directory users must not be able to sign in to Azure AD-integrated apps outside of the sign-in hours configured in the Active Directory user accounts.
– Active Directory users must authenticate by using multi-factor authentication (MFA) when they sign in to Azure AD-integrated apps.
– Administrators must be able to obtain Azure AD-generated reports that list the Active Directory users who have leaked credentials.
– The infrastructure required to implement and maintain the solution must be minimized.What should you include in the solution? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-303 Microsoft Azure Architect Technologies Part 07 Q11 145 Question 
AZ-303 Microsoft Azure Architect Technologies Part 07 Q11 145 Answer Explanation:Box 1: Pass-through Authentication with Azure AD Seamless SSO
Azure AD Seamless SSO versus Active Directory Federation Services
Companies with a security requirement to immediately enforce on-premises user account states,
password policies, and sign-in hours might use Azure AD Pass-through Authentication.
You can combine Pass-through Authentication with the Seamless Single Sign-On feature.Note: Azure AD supports the following authentication methods for hybrid identity solutions.
– Azure AD password hash synchronization
– Azure AD Pass-through AuthenticationBox 2: Azure MFA
One key benefit with Azure AD Pass-through Authentication is that it works seamlessly with Azure MFA. -
You have resources in three Azure regions. Each region contains two virtual machines. Each virtual machine has a public IP address assigned to its network interface and a locally installed application named App1.
You plan to implement Azure Front Door-based load balancing across all the virtual machines.
You need to ensure that App1 on the virtual machines will only accept traffic routed from Azure Front Door.
What should you implement?
- Azure Private Link
- service endpoints
- network security groups (NSGs) with service tags
- network security groups (NSGs) with application security groups
Explanation:
Configure IP ACLing for your backends to accept traffic from Azure Front Door’s backend IP address space and Azure’s infrastructure services only. Refer the IP details below for ACLing your backend:
– Refer AzureFrontDoor.Backend section in Azure IP Ranges and Service Tags for Front Door’s IPv4 backend IP address range or you can also use the service tag AzureFrontDoor.Backend in your network security groups. -
You have an Azure key vault named KV1.
You need to ensure that applications can use KV1 to provision certificates automatically from an external certification authority (CA).
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- From KV1, create a certificate issuer resource.
- Obtain the CA account credentials.
- Obtain the root CA certificate.
- From KV1, create a certificate signing request (CSR).
- From KV1, create a private key,
Explanation:C: Obtain the root CA certificate (step 4 in the picture below)
D: From KV1, create a certificate signing request (CSR) (step 2 in the picture below)
Note:
Creating a certificate with a CA not partnered with Key Vault
This method allows working with other CAs than Key Vault’s partnered providers, meaning your organization can work with a CA of its choice.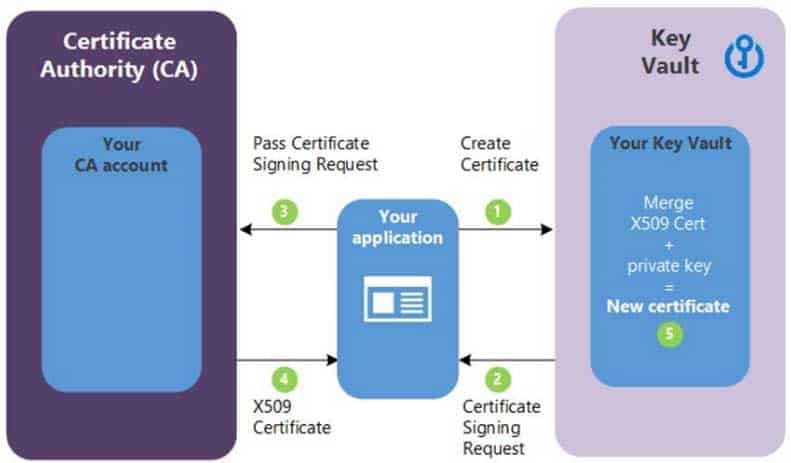
AZ-303 Microsoft Azure Architect Technologies Part 07 Q13 146 The following step descriptions correspond to the green lettered steps in the preceding diagram.
1. In the diagram above, your application is creating a certificate, which internally begins by creating a key in your key vault.
2. Key Vault returns to your application a Certificate Signing Request (CSR).
3. Your application passes the CSR to your chosen CA.
4. Your chosen CA responds with an X509 Certificate.
5. Your application completes the new certificate creation with a merger of the X509 Certificate from your CA. -
You create the following Azure role definition.
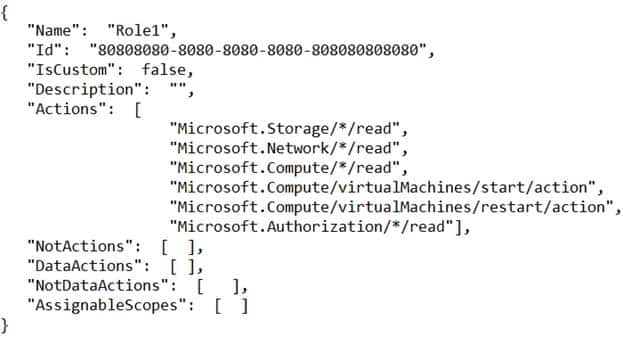
AZ-303 Microsoft Azure Architect Technologies Part 07 Q14 147 You need to create Role1 by using the role definition.
Which two values should you modify before you create Role1? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- AssignableScopes
- Description
- DataActions
- IsCustom
- Id
Explanation:Part of example:
“IsCustom”: true,“AssignableScopes”: [
“/subscriptions/{subscriptionId1}”,
“/subscriptions/{subscriptionId2}”,
“/subscriptions/{subscriptionId3}”The following shows what a custom role looks like as displayed in JSON format. This custom role can be used for monitoring and restarting virtual machines.
{
“Name”: “Virtual Machine Operator”,
“Id”: “88888888-8888-8888-8888-888888888888”,
“IsCustom”: true,
“Description”: “Can monitor and restart virtual machines.”,
“Actions”: [
“Microsoft.Storage/*/read”,
“Microsoft.Network/*/read”,
“Microsoft.Compute/*/read”,
“Microsoft.Compute/virtualMachines/start/action”,
“Microsoft.Compute/virtualMachines/restart/action”,
“Microsoft.Authorization/*/read”,
“Microsoft.ResourceHealth/availabilityStatuses/read”,
“Microsoft.Resources/subscriptions/resourceGroups/read”,
“Microsoft.Insights/alertRules/*”,
“Microsoft.Insights/diagnosticSettings/*”,
“Microsoft.Support/*”
],
“NotActions”: [],
“DataActions”: [],
“NotDataActions”: [],
“AssignableScopes”: [
“/subscriptions/{subscriptionId1}”,
“/subscriptions/{subscriptionId2}”,
“/subscriptions/{subscriptionId3}”
]
} -
You have the following Azure Active Directory (Azure AD) tenants:
– Contoso.onmicrosoft.com: Linked to a Microsoft 365 tenant and syncs to an Active Directory forest named contoso.com by using password hash synchronization
– Contosoazure.onmicrosoft.com: Linked to an Azure subscription named Subscription1You need to ensure that you can assign the users in contoso.com access to the resources in Subscription1.
What should you do?
- Create an Azure management group that contains Subscription1.
- Configure contoso.onmicrosoft.com to use pass-through authentication.
- Create guest accounts for all the contoso.com users in contosoazure.onmicrosoft.com.
- Configure Active Directory Federation Services (AD FS) federation between contosoazure.onmicrosoft.com and contoso.com.
-
You are developing an application that will enable users to download content from an Azure Storage account.
The users must only be able to download the content for a period of seven days.
You need to recommend an authentication solution to access the storage account.
What should you include in the recommendation?
- shared access signature (SAS) tokens
- identity-based authentication that uses Active Directory Domain Services (AD DS)
- storage access key
- identity-based authentication that uses Azure Active Directory (Azure AD)
-
HOTSPOT
You have an on-premises server that runs Windows Server 2019 and hosts a web app named App1.
You have an Azure subscription named Subscription1.
You plan to migrate App1 to Subsciption1 by using Azure Migrate.
To which type of Azure service will App1 be migrated, and what should you provide during the migration? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
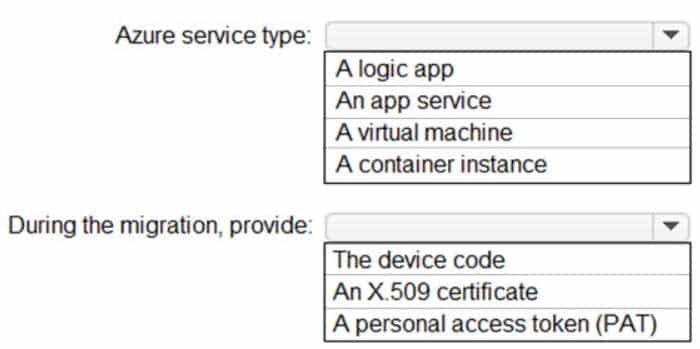
AZ-303 Microsoft Azure Architect Technologies Part 07 Q17 148 Question 
AZ-303 Microsoft Azure Architect Technologies Part 07 Q17 148 Answer -
You create the user-assigned managed identities shown in the following table.

AZ-303 Microsoft Azure Architect Technologies Part 07 Q18 149 You create a virtual machine that has the following configurations:
– Name: VM1
– Location: West US
– Resource group: RG1Which managed identities can you add to VM1?
- Identity1 only
- Identity1 and Identity2 only
- Identity1 and Identity3 only
- Identity1, Identity2, and Identity3
-
You have an Azure key vault named KV1 and an Azure web app named WebApp1. WebApp1 runs in a Shared App Service plan.
You need to grant WebApp1 permissions to KV1.
What should you do?
- Change to a Standard App Service plan.
- Add a certificate to WebApp1.
- Change to a Basic App Service plan.
- Add a managed identity to WebApp1.
-
HOTSPOT
You have an Azure subscription that contains 20 virtual machines. The virtual machines run Windows Server 2019.
You need to enable Update Management and deploy the required agents to the virtual machines.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
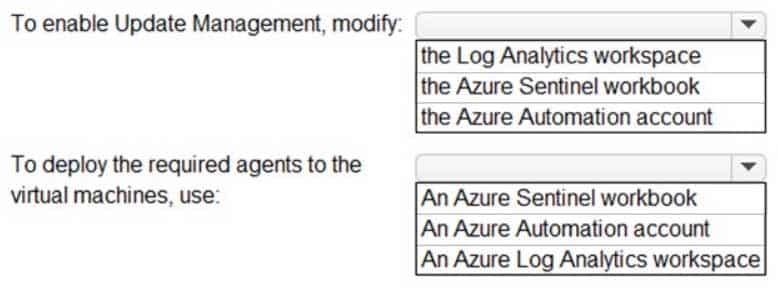
AZ-303 Microsoft Azure Architect Technologies Part 07 Q20 150 Question 
AZ-303 Microsoft Azure Architect Technologies Part 07 Q20 150 Answer