AZ-303 : Microsoft Azure Architect Technologies : Part 08
-
You have 10 Azure virtual machines on a subnet named Subnet1. Subnet1 is on a virtual network named VNet1.
You plan to deploy a public Azure Standard Load Balancer named LB1 to the same Azure region as the 10 virtual machines.
You need to ensure that traffic from all the virtual machines to the internet flows through LB1. The solution must block specific public IP addresses from being accessed by the virtual machines.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Add health probes to LB1.
- Add the network interfaces of the virtual machines to the backend pool of LB1.
- Add an inbound rule to LB1.
- Add an outbound rule to LB1.
- Associate a network security group (NSG) to Subnet1.
- Associate a user-defined route to Subnet1.
Explanation:
A: To allow the Load Balancer to monitor the status of your app, you use a health probe. The health probe dynamically adds or removes VMs from the Load Balancer rotation based on their response to health checks.
B: To distribute traffic to the VMs, a backend address pool contains the IP addresses of the virtual (NICs) connected to the Load Balancer.
D: A Load Balancer rule is used to define how traffic is distributed to the VMs. Only outbound traffic is allowed.
-
HOTSPOT
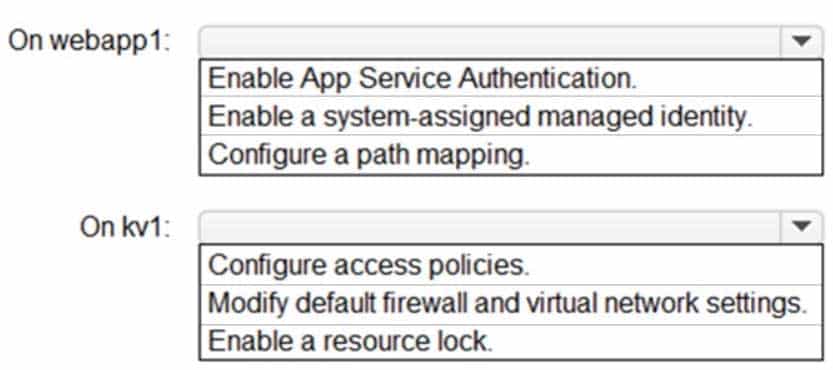
You have an Azure App Service web app named webapp1 and an Azure key vault named kv1.
You need to ensure that webapp1 can retrieve secrets stored in kv1.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
AZ-303 Microsoft Azure Architect Technologies Part 08 Q02 151 Question 
AZ-303 Microsoft Azure Architect Technologies Part 08 Q02 151 Answer Explanation:Box 1: Enable a system-assigned managed identity.
A managed identity automatically manages application credentials and can be used to authenticate to Key Vault.Box 2:
Modify the default firewall and virtual network settings.
You can reduce the exposure of your vaults by specifying which IP addresses have access to them. The virtual network service endpoints for Azure Key Vault allow you to restrict access to a specified virtual network. -
You have an Azure data factory named ADF1.
A pipeline in ADF1 must authenticate to an Azure SQL database to perform scheduled data exports.
You need to recommend an authentication solution for the connection. The solution must minimize the risks associated with stored usernames and passwords.
Which type of authentication should you recommend?
- Azure Active Directory – Universal with MFA
- Windows Authentication
- SQL Server authentication
- Managed Service Identity (MSI)
-
Case study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.
Overview
Contoso, Ltd. is a manufacturing company that has offices worldwide. Contoso works with partner organizations to bring products to market.
Contoso products are manufactured by using blueprint files that the company authors and maintains.
Existing Environment
Currently, Contoso uses multiple types of servers for business operations, including the following:
– File servers
– Domain controllers
– Microsoft SQL Server serversYour network contains an Active Directory forest named contoso.com. All servers and client computers are joined to Active Directory.
You have a public-facing application named App1. App1 is comprised of the following three tiers:
– A SQL database
– A web front end
– A processing middle tierEach tier is comprised of five virtual machines. Users access the web front end by using HTTPS only.
Requirements
Planned Changes
Contoso plans to implement the following changes to the infrastructure:
– Move all the tiers of App1 to Azure.
– Move the existing product blueprint files to Azure Blob storage.
– Create a hybrid directory to support an upcoming Microsoft 365 migration project.Technical Requirements
Contoso must meet the following technical requirements:
– Move all the virtual machines for App1 to Azure.
– Minimize the number of open ports between the App1 tiers.
– Ensure that all the virtual machines for App1 are protected by backups.
– Copy the blueprint files to Azure over the Internet.
– Ensure that the blueprint files are stored in the archive storage tier.
– Ensure that partner access to the blueprint files is secured and temporary.
– Prevent user passwords or hashes of passwords from being stored in Azure.
– Use unmanaged standard storage for the hard disks of the virtual machines.
– Ensure that when users join devices to Azure Active Directory (Azure AD), the users use a mobile phone to verify their identity.
– Minimize administrative effort whenever possible.User Requirements
Contoso identifies the following requirements for users:
– Ensure that only users who are part of a group named Pilot can join devices to Azure AD.
– Designate a new user named Admin1 as the service admin for the Azure subscription.
– Admin1 must receive email alerts regarding service outages.
– Ensure that a new user named User3 can create network objects for the Azure subscription.-
You need to recommend an identity solution that meets the technical requirements.
What should you recommend?
- password hash synchronization and single sign-on (SSO)
- federated single sign-on (SSO) and Active Directory Federation Services (AD FS)
- Pass-thorough Authentication and single sign-on (SSO)
- cloud-only user accounts
Explanation:With Pass-through Authentication the on-premises passwords are never stored in the cloud in any form.
Scenario:
– Prevent user passwords or hashes of passwords from being stored in Azure.
– Ensure that when users join devices to Azure Active Directory (Azure AD), the users use a mobile phone to verify their identity.
– Minimize administrative effort whenever possible.
-
-
Case Study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.Overview. General Overview
Litware, Inc. is a medium-sized finance company. Litware recently acquired a financial services company named Fabrikam, Ltd.
Overview. Physical Locations
Litware has a datacenter in Boston. Fabrikam has a datacenter in San Francisco.
Existing Environment. Identity Environment
The network of Litware contains an Active Directory forest named Litware.com that syncs to an Azure Active Directory (Azure AD) tenant named Litware.com by using Azure AD Connect.
Azure AD Seamless Single Sign-on (Azure AD Seamless SSO) is enabled for the Litware.com tenant.
Users at Litware have a UPN suffix of Litware.com
Litware has an internal certification authority (CA) that is trusted by all devices.
The network of Fabrikam contains an Active Directory forest named fabrikam.com. Users at Fabrikam have a UPN suffix of fabrikam.com.
Existing Environment. Azure Environment
Litware has an Azure subscription named Sub1 that is linked to the Litware.com tenant. Sub1 contains the resources shown in the following table.

AZ-303 Microsoft Azure Architect Technologies Part 08 Q05 152 Litware has Azure Resource Manager (ARM) templates that deploy Azure Policy definitions and assignments to a management group.
Fabrikam does NOT have an Azure environment.
Existing Environment. On-Premises Environment
The on-premises network of Litware contains the resources shown in the following table.

AZ-303 Microsoft Azure Architect Technologies Part 08 Q05 153 The on-premises network of Fabrikam contains a domain member server named SERVER1 that runs Windows Server 2019.
Existing Environment. Network Environment
Litware has a site-to-site VPN connection to VNet1.
The Litware and Fabrikam datacenters are not connected.
Requirements. Planned Changes
Litware plans to implement the following changes:
– Establish a trust relationship between the Litware and Fabrikam forests.
– Migrate data from the on-premises NoSQL datastores to Azure Table storage.
– Containerize WebApp1 and deploy the app to an Azure Kubernetes Service (AKS) cluster on VNet1.
– Create an Azure blueprint named BP1 and use the blueprint to provision a resource group named RG1.Requirements. Deployment Requirements
Litware identifies the following deployment requirements:
– The existing ARM templates must be used for deployments to Sub1.
– WebApp1 must be deployed to the AKS cluster without having to change the source code.Requirements. Authentication and Authorization Requirements
Litware identifies the following authentication and authorization requirements:
– The Fabrikam users must be able to authenticate to the Litware.com tenant by using Azure AD Seamless SSO.
– The Fabrikam users and the Litware users must be able to manage the Azure resources in Sub1.
– Company policy must prohibit the creation of guest user accounts in the Litware.com tenant.
– You must be able to configure deny permissions for RG1 and for the resources in RG1.
– WebApp1 running on the AKS cluster must be able to retrieve secrets from KV1.Requirements. Security Requirements
Litware identifies the following security requirements:
– On-premises Litware users must access KVI by using the private IP address of the key vault.
– Azure virtual machines must have all their disks encrypted, including the temporary disks.
– Azure Storage must encrypt all data by using keys issued by the internal CA of Litware.
– Inbound HTTPS traffic to WebApp1 must be inspected for SQL injection attacks.
– The principle of least privilege must be used.-
You migrate WebApp1 to Azure.
You need to implement a traffic filtering solution for WebApp1. The solution must meet the security requirements.
What should you do?
- Configure the Threat intelligence settings for FW1.
- Deploy an Azure Application Gateway to VNet1.
- Deploy Azure Bastion to VNet1.
- Configure an inbound rule on FW1.
-
HOTSPOT
You need to recommend a solution to provide KV1 with access to the on-premises network of Litware. The solution must meet the security requirements.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-303 Microsoft Azure Architect Technologies Part 08 Q05 154 Question 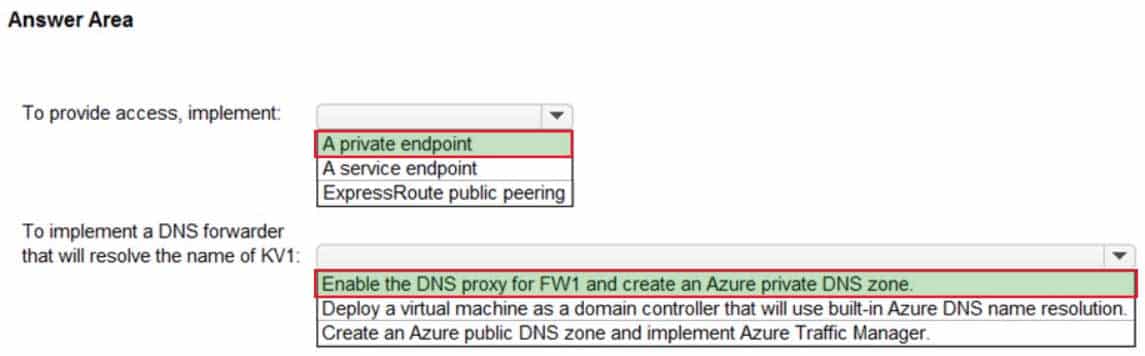
AZ-303 Microsoft Azure Architect Technologies Part 08 Q05 154 Answer -
You create and publish the BP1 blueprint.
You need to ensure that you can use BP1 to configure permissions for RG1. The solution must meet the authentication and authorization requirements.
What should you do?
- Add a read-only resource lock to Sub1.
- Assign an Azure role-based access control (Azure RBAC) role to Sub1.
- Assign an Azure role-based access control (Azure RBAC) role to BP1.
- Select the Read Only blueprint lock mode for the BP1 assignment.
-
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a server named Server1 that runs Windows Server 2019. Server1 is a container host.
You are creating a Dockerfile to build a container image.
You need to add a file named File1.txt from Server1 to a folder named C:\Folder1 in the container image.
Solution: You add the following line to the Dockerfile.
XCOPY File1.txt C:\Folder1\
You then build the container image.
Does this meet the goal?
- Yes
- No
Explanation:
Copy is the correct command to copy a file to the container image. Furthermore, the root directory is specified as ‘/’ and not as ‘C:/’. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a server named Server1 that runs Windows Server 2019. Server1 is a container host.
You are creating a Dockerfile to build a container image.
You need to add a file named File1.txt from Server1 to a folder named C:\Folder1 in the container image.
Solution: You add the following line to the Dockerfile.
ADD File1.txt C:/Folder1/
You then build the container image.
Does this meet the goal?
- Yes
- No
Explanation:
Copy is the correct command to copy a file to the container image. The ADD command can also be used. However, the root directory is specified as ‘/’ and not as ‘C:/’. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a server named Server1 that runs Windows Server 2019. Server1 is a container host.
You are creating a Dockerfile to build a container image.
You need to add a file named File1.txt from Server1 to a folder named C:\Folder1 in the container image.
Solution: You add the following line to the Dockerfile.
Copy-Item File1.txt C:\Folder1\File1.txt
You then build the container image.
Does this meet the goal?
- Yes
- No
Explanation:
Copy is the correct command to copy a file to the container image. -
HOTSPOT
You have an Azure subscription that contains the resources shown in the following table.
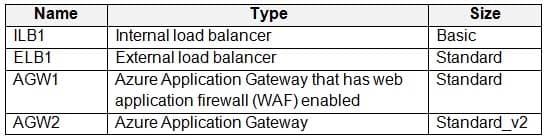
AZ-303 Microsoft Azure Architect Technologies Part 08 Q09 155 You need to deploy a load-balancing solution for two Azure web apps named App1 and App2 to meet the following requirements:
– App1 must support command injection protection.
– App2 must be able to use a static public IP address.
– App1 must have a Service Level Agreement (SLA) of 99.99 percent.
– App2 must support cookie affinity.Which resource should you use as the load-balancing solution for each app? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
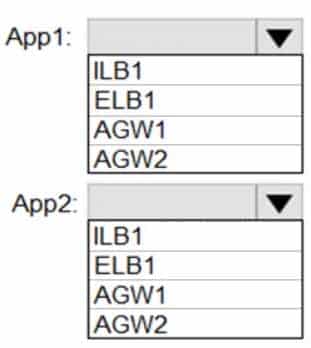
AZ-303 Microsoft Azure Architect Technologies Part 08 Q09 156 Question 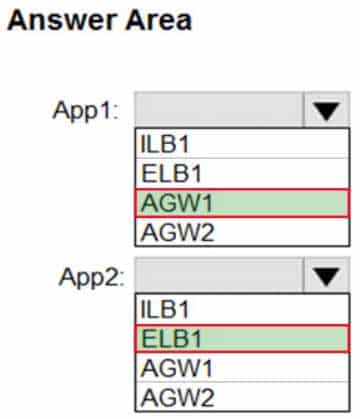
AZ-303 Microsoft Azure Architect Technologies Part 08 Q09 156 Answer Explanation:Box 1: AGW1
Azure Application Gateway offers a web application firewall (WAF) that provides centralized protection of your web applications from common exploits and vulnerabilities. Web applications are increasingly targeted by malicious attacks that exploit commonly known vulnerabilities. SQL injection and cross-site scripting are among the most common attacks.Box 2: ELB1
Public IP addresses allow Internet resources to communicate inbound to Azure resources. Public IP addresses also enable Azure resources to communicate outbound to Internet and public-facing Azure services with an IP address assigned to the resource.Note: In Azure Resource Manager, a public IP address is a resource that has its own properties. Some of the resources you can associate a public IP address resource with are:
– Virtual machine network interfaces
– Internet-facing load balancers
– VPN gateways
– Application gateways -
You have the Azure virtual networks shown in the following table.
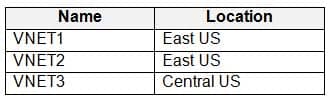
AZ-303 Microsoft Azure Architect Technologies Part 08 Q10 157 All the virtual networks are peered.
You have the virtual machines shown in the following table.

AZ-303 Microsoft Azure Architect Technologies Part 08 Q10 158 You deploy an Azure Bastion named Bastion1 to VNET1.
To which virtual machines can you connect by using Bastion1?
- VM1 only
- VM1 and VM2 only
- VM2 and VM3 only
- VM1, VM2, and VM3
Explanation:
Connect to a VM through Azure Bastion.
When you click on Connect in an Azure VM, you have an additional option called Bastion. In order to get this option, the Azure VM must belong to the same virtual network as the Azure Bastion. -
You have an Azure Kubernetes Service (AKS) cluster named Clus1 in a resource group named RG1.
An administrator plans to manage Clus1 from an Azure AD-joined device.
You need to ensure that the administrator can deploy the YAML application manifest file for a container application.
You install the Azure CLI on the device.
Which command should you run next?
-
kubectl get nodes
-
az aks enable-addons --addons virtual-node -name Clust1 --resource-group RG1
-
az aks install-cli
-
kubectl apply –f app1.yaml
Explanation:kubectl apply –f appl.yaml applies a configuration change to a resource from a file or stdin.
Incorrect Answers:
A: kubectl get nodes gets a list of all nodes.
B: az aks enable-addons enable Kubernetes addons, in this case a virtual node.
C: az aks install-cli download and install the Kubernetes command-line tool. -
-
You create an Azure Kubernetes Service (AKS) cluster that uses B2s node size. The cluster configured as shown in the exhibit. (Click the Exhibit tab.)
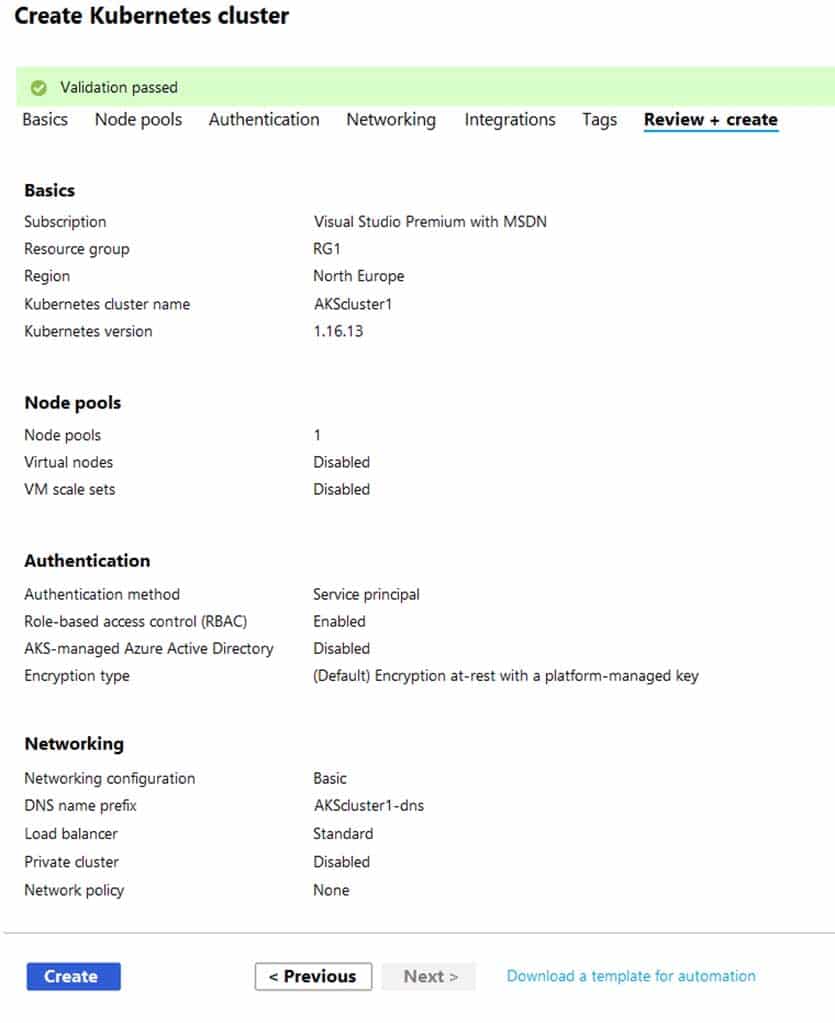
AZ-303 Microsoft Azure Architect Technologies Part 08 Q12 159 You deploy a containerized application named App1 to the agentPool node pool in AKScluster1.
You need to create a containerized application named App2 that runs on four nodes of size DS3 v2.
What should you do first?
- Upgrade the AKS cluster.
- Create a new node pool.
- Modify the autoscaling settings for the agentPool node pool.
- Enable virtual nodes for the AKS cluster.
Explanation:
Changing the agent size is not allowed. In the future Microsoft plans to support multiple node pools wherein you can create different pools with different VM sizes. -
You have an on-premises virtual machine named VM1 configured as shown in the following exhibit.

AZ-303 Microsoft Azure Architect Technologies Part 08 Q13 160 VM1 is started.
You need to create a new virtual machine image in Azure from VM1.
Which three actions should you perform before you create the new image? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Run Add-AzVhd and specify a file share as the destination.
- Convert the disk type to VHD.
- Remove the Backup (volume shadow copy) integration service.
- Generalize VM1.
- Reduce the amount of memory to 16 GB.
- Run Add-AzVhd and specify a blob service container as the destination.
Explanation:D: Sysprep removes all your personal account and security information, and then prepares the machine to be used as an image.
B, F: The Add-AzureVhd cmdlet uploads on-premises virtual hard disks, in .vhd file format, to a blob storage account as fixed virtual hard disks.
-
You create an Azure Kubernetes Service (AKS) cluster and an Azure Container Registry.
You need to perform continuous deployments of a containerized application to the AKS cluster as soon as the image updates in the registry.
What should you use to perform the deployments?
- an Azure Automation runbook
- a kubectl script from a CRON job
- an Azure Resource Manager template
- an Azure Pipelines release pipeline
Explanation:You can implement a Continuous Deployment pipeline.
Example:

AZ-303 Microsoft Azure Architect Technologies Part 08 Q14 161 What the pipeline accomplishes :
Stage 1: The code gets pushed in the Github. The Jenkins job gets triggered automatically. The Dockerfile is checked out from Github.Stage 2: Docker builds an image from the Dockerfile and then the image is tagged with the build number. Additionally, the latest tag is also attached to the image for the containers to use.
Stage 3: We have default deployment and service YAML files stored on the Jenkins server. Jenkins makes a copy of the default YAML files, make the necessary changes according to the build and put them in a separate folder.
Stage 4: kubectl was initially configured at the time of setting up AKS on the Jenkins server. The YAML files are fed to the kubectl util which in turn creates pods and services.
-
You have an Azure web app that runs in a Premium App Service plan.
Developers plan to update the app weekly.
You need to ensure that the app can be switched from the current version to the new version. The solution must meet the following requirements:
– Provide the developers with the ability to test the app in Azure prior to switching versions. Testing must use the same app instance.
– Ensure that the app version can be rolled back.
– Minimize downtime.What should you do?
- Create a deployment slot.
- Copy the App Service plan.
- Add an instance of the app to the scale set.
- Create an Azure Active Directory (Azure AD) enterprise application.
Explanation:Azure Functions deployment slots allow your function app to run different instances called “slots”. Slots are different environments exposed via a publicly available endpoint. One app instance is always mapped to the production slot, and you can swap instances assigned to a slot on demand.
There are a number of advantages to using deployment slots. The following scenarios describe common uses for slots:
– Different environments for different purposes: Using different slots gives you the opportunity to differentiate app instances before swapping to production or a staging slot.
– Easy fallbacks: After a swap with production, the slot with a previously staged app now has the previous production app. If the changes swapped into the production slot aren’t as you expect, you can immediately reverse the swap to get your “last known good instance” back.
– Prewarming -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Active Directory (Azure AD) tenant named contoso.com.
A user named Admin1 attempts to create an access review from the Azure Active Directory admin center and discovers that the Access reviews settings are unavailable. Admin1 discovers that all the other Identity Governance settings are available.
Admin1 is assigned the User administrator, Compliance administrator, and Security administrator roles.
You need to ensure that Admin1 can create access reviews in contoso.com.
Solution: You create an access package.
Does this meet the goal?
- Yes
- No
Explanation:You do not use access packages for Identity Governance. Instead use Azure AD Privileged Identity Management.
Note: PIM essentially helps you manage the who, what, when, where, and why for resources that you care about. Key features of PIM include:
Conduct access reviews to ensure users still need roles -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Active Directory (Azure AD) tenant named contoso.com.
A user named Admin1 attempts to create an access review from the Azure Active Directory admin center and discovers that the Access reviews settings are unavailable. Admin1 discovers that all the other Identity Governance settings are available.
Admin1 is assigned the User administrator, Compliance administrator, and Security administrator roles.
You need to ensure that Admin1 can create access reviews in contoso.com.
Solution: You purchase an Azure Active Directory Premium P2 license for contoso.com.
Does this meet the goal?
- Yes
- No
Explanation:Instead use Azure AD Privileged Identity Management.
Note: PIM essentially helps you manage the who, what, when, where, and why for resources that you care about. Key features of PIM include:
– Conduct access reviews to ensure users still need roles -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Active Directory (Azure AD) tenant named contoso.com.
A user named Admin1 attempts to create an access review from the Azure Active Directory admin center and discovers that the Access reviews settings are unavailable. Admin1 discovers that all the other identity Governance settings are available.
Admin1 is assigned the User administrator, Compliance administrator, and Security administrator roles.
You need to ensure that Admin1 can create access reviews in contoso.com.
Solution: You assign the Global administrator role to Admin1.
Does this meet the goal?
- Yes
- No
Explanation:Instead use Azure AD Privileged Identity Management.
Note: PIM essentially helps you manage the who, what, when, where, and why for resources that you care about. Key features of PIM include:
Conduct access reviews to ensure users still need roles -
You have an Azure Container Registry and an Azure container instance.
You pull an image from the registry, and then update the local copy of the image.
You need to ensure that the updated image can be deployed to the container instance. The solution must ensure that you can deploy the updated image or the previous version of the image.
What should you do?
-
Run the docker image push command and specify the tag parameter. -
Run the az image copy command and specify the tag parameter.
-
Run the az aks update command and specify the attach-acr parameter.
-
Run the kubectl apply command and specify the dry-run parameter.
Explanation:The command ‘docker image push’ pushes an image or a repository to a registry.
Incorrect Answers:
B: az image copy
Copies a managed image (or vm) to other regions.
–tagsC: az aks update
Updates a managed Kubernetes cluster.D: Kubectl apply
apply manages applications through files defining Kubernetes resources. It creates and updates resources in a cluster through running kubectl apply. This is the recommended way of managing Kubernetes applications on production. -
-
You have an application that is hosted across multiple Azure regions.
You need to ensure that users connect automatically to their nearest application host based on network latency.
What should you implement?
- Azure Application Gateway
- Azure Load Balancer
- Azure Traffic Manager
- Azure Bastion
Explanation:Azure Traffic Manager is a DNS-based traffic load balancer. This service allows you to distribute traffic to your public facing applications across the global Azure regions. Traffic Manager also provides your public endpoints with high availability and quick responsiveness.
Incorrect Answers:
A: Azure Application Gateway is a web traffic load balancer that enables you to manage traffic to your web applications.B: An Azure load balancer is a Layer-4 (TCP, UDP) load balancer that provides high availability by distributing incoming traffic among healthy VMs.
D: Azure Bastion is a fully managed PaaS service that provides secure and seamless RDP and SSH access to your virtual machines directly through the Azure Portal.