AZ-500 : Microsoft Azure Security Technologies : Part 05
-
SIMULATION
You need to ensure that only devices connected to a 131.107.0.0/16 subnet can access data in the rg1lod10598168 Azure Storage account.
To complete this task, sign in to the Azure portal.
- See the explanation below.
Explanation:Step 1:
1. In Azure portal go to the storage account you want to secure. Here: rg1lod10598168
2. Click on the settings menu called Firewalls and virtual networks.
3. To deny access by default, choose to allow access from Selected networks. To allow traffic from all networks, choose to allow access from All networks.
4. Click Save to apply your changes.Step 2:
1. Go to the storage account you want to secure. Here: rg1lod10598168
2. Click on the settings menu called Firewalls and virtual networks.
3. Check that you’ve selected to allow access from Selected networks.
4. To grant access to a virtual network with a new network rule, under Virtual networks, click Add existing virtual network, select Virtual networks and Subnets options. Enter the 131.107.0.0/16 subnet and then click Add.Note: When network rules are configured, only applications requesting data over the specified set of networks can access a storage account. You can limit access to your storage account to requests originating from specified IP addresses, IP ranges or from a list of subnets in an Azure Virtual Network (VNet).
-
HOTSPOT
You create resources in an Azure subscription as shown in the following table.
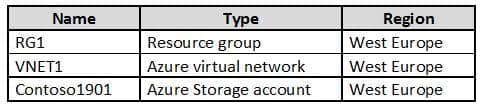
AZ-500 Microsoft Azure Security Technologies Part 05 Q02 167 VNET1 contains two subnets named Subnet1 and Subnet2. Subnet1 has a network ID of 10.0.0.0/24. Subnet2 has a network ID of 10.1.1.0/24.
Contoso1901 is configured as shown in the exhibit. (Click the Exhibit tab.)
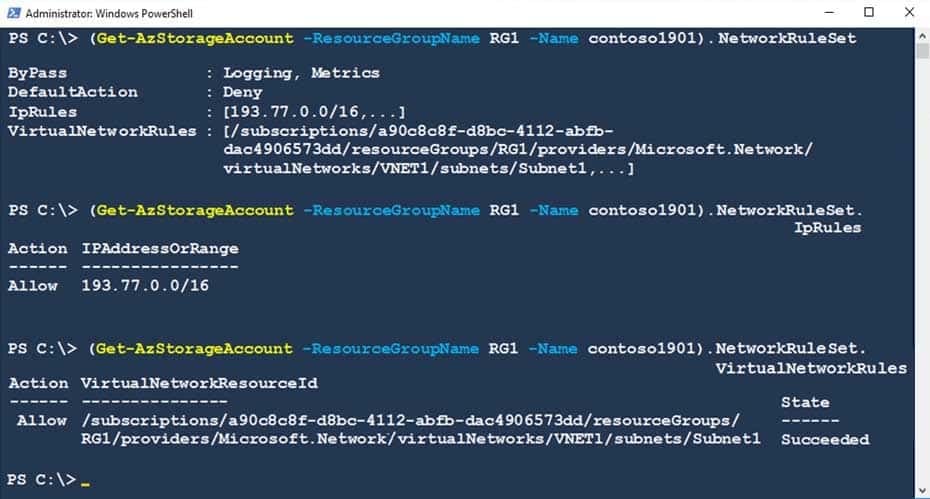
AZ-500 Microsoft Azure Security Technologies Part 05 Q02 168 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

AZ-500 Microsoft Azure Security Technologies Part 05 Q02 169 Question 
AZ-500 Microsoft Azure Security Technologies Part 05 Q02 169 Answer Explanation:Box 1: Yes
Access from Subnet1 is allowed.Box 2: No
No access from Subnet2 is allowed.Box 3: Yes
Access from IP address 193.77.10.2 is allowed. -
You have an Azure subscription that contains the virtual machines shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 05 Q03 170 All the virtual networks are peered.
You deploy Azure Bastion to VNET2.
Which virtual machines can be protected by the bastion host?
- VM1, VM2, VM3, and VM4
- VM1, VM2, and VM3 only
- VM2 and VM4 only
- VM2 only
-
You have Azure Resource Manager templates that you use to deploy Azure virtual machines.
You need to disable unused Windows features automatically as instances of the virtual machines are provisioned.
What should you use?
- device configuration policies in Microsoft Intune
- Azure Automation State Configuration
- security policies in Azure Security Center
- device compliance policies in Microsoft Intune
Explanation:You can use Azure Automation State Configuration to manage Azure VMs (both Classic and Resource Manager), on-premises VMs, Linux machines, AWS VMs, and on-premises physical machines.
Note: Azure Automation State Configuration provides a DSC pull server similar to the Windows Feature DSC-Service so that target nodes automatically receive configurations, conform to the desired state, and report back on their compliance. The built-in pull server in Azure Automation eliminates the need to set up and maintain your own pull server. Azure Automation can target virtual or physical Windows or Linux machines, in the cloud or on-premises.
-
You have an Azure subscription named Sub1. Sub1 contains a virtual network named VNet1 that contains one subnet named Subnet1.
Subnet1 contains an Azure virtual machine named VM1 that runs Ubuntu Server 18.04.
You create a service endpoint for MicrosoftStorage in Subnet1.
You need to ensure that when you deploy Docker containers to VM1, the containers can access Azure Storage resources by using the service endpoint.
What should you do on VM1 before you deploy the container?
- Create an application security group and a network security group (NSG).
- Edit the docker-compose.yml file.
- Install the container network interface (CNI) plug-in.
Explanation:The Azure Virtual Network container network interface (CNI) plug-in installs in an Azure Virtual Machine. The plug-in supports both Linux and Windows platform.
The plug-in assigns IP addresses from a virtual network to containers brought up in the virtual machine, attaching them to the virtual network, and connecting them directly to other containers and virtual network resources. The plug-in doesn’t rely on overlay networks, or routes, for connectivity, and provides the same performance as virtual machines.
The following picture shows how the plug-in provides Azure Virtual Network capabilities to Pods:
AZ-500 Microsoft Azure Security Technologies Part 05 Q05 171 -
You have Azure Resource Manager templates that you use to deploy Azure virtual machines.
You need to disable unused Windows features automatically as instances of the virtual machines are provisioned.
What should you use?
- device configuration policies in Microsoft Intune
- an Azure Desired State Configuration (DSC) virtual machine extension
- application security groups
- device compliance policies in Microsoft Intune
Explanation:
The primary use case for the Azure Desired State Configuration (DSC) extension is to bootstrap a VM to the Azure Automation State Configuration (DSC) service. The service provides benefits that include ongoing management of the VM configuration and integration with other operational tools, such as Azure Monitoring. Using the extension to register VM’s to the service provides a flexible solution that even works across Azure subscriptions. -
DRAG DROP
You have an Azure subscription that contains the virtual networks shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 05 Q07 172 The Azure virtual machines on SpokeVNetSubnet0 can communicate with the computers on the on-premises network.
You plan to deploy an Azure firewall to HubVNet.
You create the following two routing tables:
– RT1: Includes a user-defined route that points to the private IP address of the Azure firewall as a next hop address
– RT2: Disables BGP route propagation and defines the private IP address of the Azure firewall as the default gatewayYou need to ensure that traffic between SpokeVNetSubnet0 and the on-premises network flows through the Azure firewall.
To which subnet should you associate each route table? To answer, drag the appropriate subnets to the correct route tables. Each subnet may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

AZ-500 Microsoft Azure Security Technologies Part 05 Q07 173 Question 
AZ-500 Microsoft Azure Security Technologies Part 05 Q07 173 Answer -
HOTSPOT
You have an Azure subscription. The subscription contains Azure virtual machines that run Windows Server 2016.
You need to implement a policy to ensure that each virtual machine has a custom antimalware virtual machine extension installed.
How should you complete the policy? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
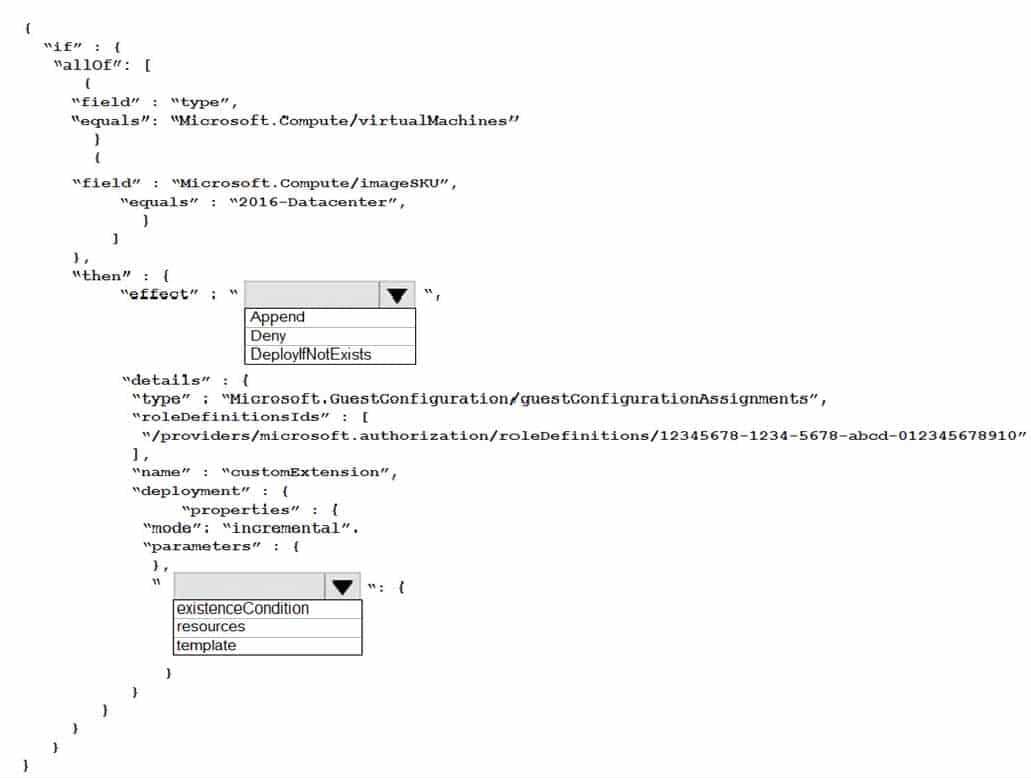
AZ-500 Microsoft Azure Security Technologies Part 05 Q08 174 Question 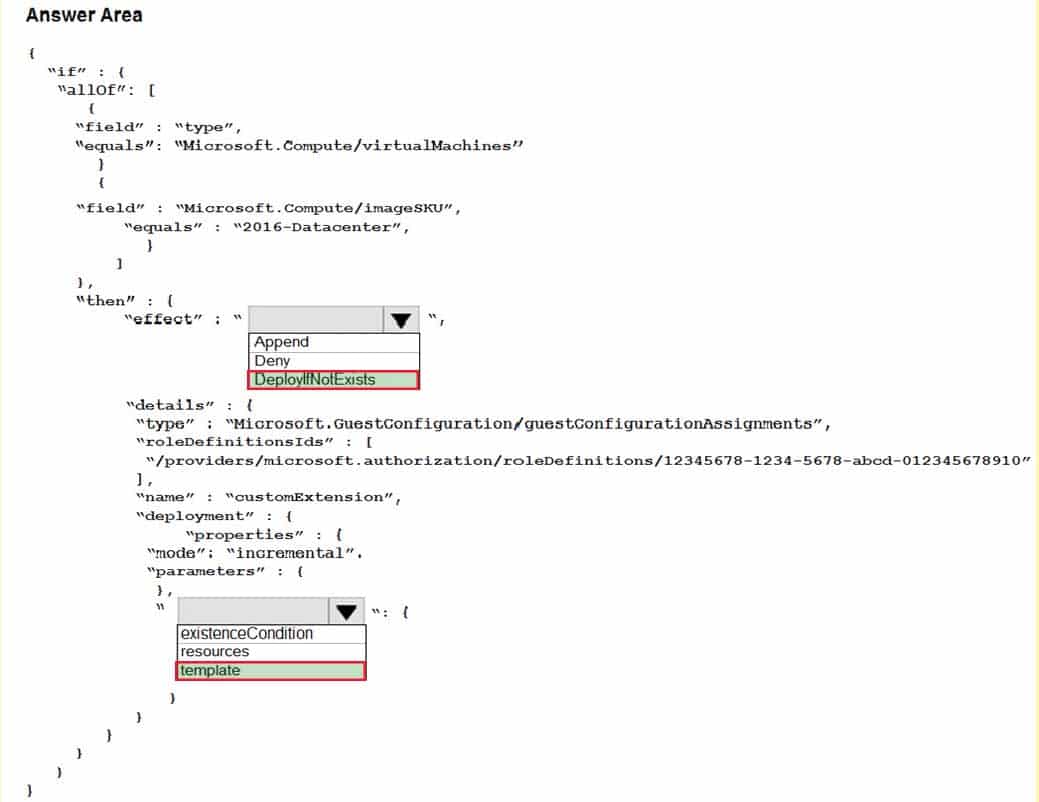
AZ-500 Microsoft Azure Security Technologies Part 05 Q08 174 Answer Explanation:Box 1: DeployIfNotExists
DeployIfNotExists executes a template deployment when the condition is met.Box 2: Template
The details property of the DeployIfNotExists effects has all the subproperties that define the related resources to match and the template deployment to execute.
Deployment [required]This property should include the full template deployment as it would be passed to the Microsoft.Resources/deployment
-
You are configuring an Azure Kubernetes Service (AKS) cluster that will connect to an Azure Container Registry.
You need to use the auto-generated service principal to authenticate to the Azure Container Registry.
What should you create?
- an Azure Active Directory (Azure AD) group
- an Azure Active Directory (Azure AD) role assignment
- an Azure Active Directory (Azure AD) user
- a secret in Azure Key Vault
Explanation:
When you create an AKS cluster, Azure also creates a service principal to support cluster operability with other Azure resources. You can use this auto-generated service principal for authentication with an ACR registry. To do so, you need to create an Azure AD role assignment that grants the cluster’s service principal access to the container registry. -
You have an Azure subscription that contains the Azure virtual machines shown in the following table.
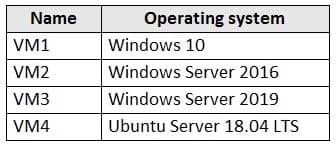
AZ-500 Microsoft Azure Security Technologies Part 05 Q10 175 You create an MDM Security Baseline profile named Profile1.
You need to identify to which virtual machines Profile1 can be applied.
Which virtual machines should you identify?
- VM1 only
- VM1, VM2, and VM3 only
- VM1 and VM3 only
- VM1, VM2, VM3, and VM4
-
SIMULATION
You need to ensure that connections from the Internet to VNET1\subnet0 are allowed only over TCP port 7777. The solution must use only currently deployed resources.
To complete this task, sign in to the Azure portal.
- See the explanation below.
Explanation:You need to configure the Network Security Group that is associated with subnet0.
1. In the Azure portal, type Virtual Networks in the search box, select Virtual Networks from the search results then select VNET1. Alternatively, browse to Virtual Networks in the left navigation pane.
2. In the properties of VNET1, click on Subnets. This will display the subnets in VNET1 and the Network Security Group associated to each subnet. Note the name of the Network Security Group associated to Subnet0.
3. Type Network Security Groups into the search box and select the Network Security Group associated with Subnet0.
4. In the properties of the Network Security Group, click on Inbound Security Rules.
5. Click the Add button to add a new rule.
6. In the Source field, select Service Tag.
7. In the Source Service Tag field, select Internet.
8. Leave the Source port ranges and Destination field as the default values (* and All).
9. In the Destination port ranges field, enter 7777.
10. Change the Protocol to TCP.
11. Leave the Action option as Allow.
12. Change the Priority to 100.
13. Change the Name from the default Port_8080 to something more descriptive such as Allow_TCP_7777_from_Internet. The name cannot contain spaces.
14. Click the Add button to save the new rule. -
SIMULATION
You need to prevent administrators from performing accidental changes to the Homepage app service plan.
To complete this task, sign in to the Azure portal.
- See the explanation below.
Explanation:You need to configure a ‘lock’ for the app service plan. A read-only lock ensures that no one can make changes to the app service plan without first deleting the lock.
1. In the Azure portal, type App Service Plans in the search box, select App Service Plans from the search results then select Homepage. Alternatively, browse to App Service Plans in the left navigation pane.
2. In the properties of the app service plan, click on Locks.
3. Click the Add button to add a new lock.
4. Enter a name in the Lock name field. It doesn’t matter what name you provide for the exam.
5. For the Lock type, select Read-only.
6. Click OK to save the changes. -
SIMULATION
You need to ensure that a user named Danny11597200 can sign in to any SQL database on a Microsoft SQL server named web11597200 by using SQL Server Management Studio (SSMS) and Azure Active Directory (Azure AD) credentials.
To complete this task, sign in to the Azure portal.
- See the explanation below.
Explanation:You need to provision an Azure AD Admin for the SQL Server.
1. In the Azure portal, type SQL Server in the search box, select SQL Server from the search results then select the server named web11597200. Alternatively, browse to SQL Server in the left navigation pane.
2. In the SQL Server properties page, click on Active Directory Admin.
3. Click the Set Admin button.
4. In the Add Admin window, search for and select Danny11597200.
5. Click the Select button to add Danny11597200.
6. Click the Save button to save the changes. -
SIMULATION
You need to configure a Microsoft SQL server named Web11597200 only to accept connections from the Subnet0 subnet on the VNET01 virtual network.
To complete this task, sign in to the Azure portal.
- See the explanation below.
Explanation:You need to allow access to Azure services and configure a virtual network rule for the SQL Server.
1. In the Azure portal, type SQL Server in the search box, select SQL Server from the search results then select the server named web11597200. Alternatively, browse to SQL Server in the left navigation pane.
2. In the properties of the SQL Server, click Firewalls and virtual networks.
3. In the Virtual networks section, click on Add existing. This will open the Create/Update virtual network rule window.
4. Give the rule a name such as Allow_VNET01-Subnet0 (it doesn’t matter what name you enter for the exam).
5. In the Virtual network box, select VNET01.
6. In the Subnet name box, select Subnet0.
7. Click the OK button to save the rule.
8. Back in the Firewall / Virtual Networks window, set the Allow access to Azure services option to On. -
You have Azure Resource Manager templates that you use to deploy Azure virtual machines.
You need to disable unused Windows features automatically as instances of the virtual machines are provisioned.
What should you use?
- device configuration policies in Microsoft Intune
- an Azure Desired State Configuration (DSC) virtual machine extension
- security policies in Azure Security Center
- Azure Logic Apps
Explanation:
The primary use case for the Azure Desired State Configuration (DSC) extension is to bootstrap a VM to the Azure Automation State Configuration (DSC) service. The service provides benefits that include ongoing management of the VM configuration and integration with other operational tools, such as Azure Monitoring. Using the extension to register VM’s to the service provides a flexible solution that even works across Azure subscriptions. -
HOTSPOT
You have an Azure subscription that contains the virtual machines shown in the following table.
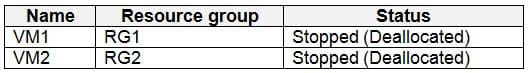
AZ-500 Microsoft Azure Security Technologies Part 05 Q16 176 You create the Azure policies shown in the following table.
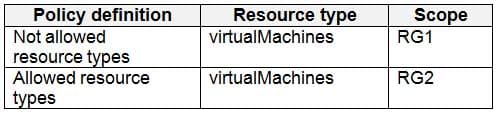
AZ-500 Microsoft Azure Security Technologies Part 05 Q16 177 You create the resource locks shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 05 Q16 178 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

AZ-500 Microsoft Azure Security Technologies Part 05 Q16 179 Question 
AZ-500 Microsoft Azure Security Technologies Part 05 Q16 179 Answer -
HOTSPOT
You have an Azure subscription that contains an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant contains the users shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 05 Q17 180 You create a resource group named RG1.
Which users can modify the permissions for RG1 and which users can create virtual networks in RG1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-500 Microsoft Azure Security Technologies Part 05 Q17 181 Question 
AZ-500 Microsoft Azure Security Technologies Part 05 Q17 181 Answer Explanation:Box 1: Only an owner can change permissions on resources.
Box 2: A Contributor can create/modify/delete anything in the subscription but cannot change permissions. -
SIMULATION
You need to configure network connectivity between a virtual network named VNET1 and a virtual network named VNET2. The solution must ensure that virtual machines connected to VNET1 can communicate with virtual machines connected to VNET2.
To complete this task, sign in to the Azure portal and modify the Azure resources.
- See the explanation below.
Explanation:You need to configure VNet Peering between the two networks. The questions states, “The solution must ensure that virtual machines connected to VNET1 can communicate with virtual machines connected to VNET2”. It doesn’t say the VMs on VNET2 should be able to communicate with VMs on VNET1. Therefore, we need to configure the peering to allow just the one-way communication.
1. In the Azure portal, type Virtual Networks in the search box, select Virtual Networks from the search results then select VNET1. Alternatively, browse to Virtual Networks in the left navigation pane.
2. In the properties of VNET1, click on Peerings.
3. In the Peerings blade, click Add to add a new peering.
4. In the Name of the peering from VNET1 to remote virtual network box, enter a name such as VNET1-VNET2 (this is the name that the peering will be displayed as in VNET1)
5. In the Virtual Network box, select VNET2.
6. In the Name of the peering from remote virtual network to VNET1 box, enter a name such as VNET2-VNET1 (this is the name that the peering will be displayed as in VNET2).
There is an option Allow virtual network access from VNET to remote virtual network. This should be left as Enabled.
7. For the option Allow virtual network access from remote network to VNET1, click the slider button to Disabled.
8. Click the OK button to save the changes. -
SIMULATION
You need to deploy an Azure firewall to a virtual network named VNET3.
To complete this task, sign in to the Azure portal and modify the Azure resources.
This task might take several minutes to complete. You can perform other tasks while the task completes.
- See the explanation below.
Explanation:To add an Azure firewall to a VNET, the VNET must first be configured with a subnet named AzureFirewallSubnet (if it doesn’t already exist).
Configure VNET3.
1. In the Azure portal, type Virtual Networks in the search box, select Virtual Networks from the search results then select VNET3. Alternatively, browse to Virtual Networks in the left navigation pane.
2. In the Overview section, note the Location (region) and Resource Group of the virtual network. We’ll need these when we add the firewall.
3. Click on Subnets.
4. Click on + Subnet to add a new subnet.
5. Enter AzureFirewallSubnet in the Name box. The subnet must be named AzureFirewallSubnet.
6. Enter an appropriate IP range for the subnet in the Address range box.
7. Click the OK button to create the subnet.Add the Azure Firewall.
1. In the settings of VNET3 click on Firewall.
2. Click the Click here to add a new firewall link.
3. The Resource group will default to the VNET3 resource group. Leave this default.
4. Enter a name for the firewall in the Name box.
5. In the Region box, select the same region as VNET3.
6. In the Public IP address box, select an available public IP address if one exists, or click Add new to add a new public IP address.
7. Click the Review + create button.
8. Review the settings and click the Create button to create the firewall. -
SIMULATION
You need to configure a virtual network named VNET2 to meet the following requirements:
– Administrators must be prevented from deleting VNET2 accidentally.
– Administrators must be able to add subnets to VNET2 regularly.To complete this task, sign in to the Azure portal and modify the Azure resources.
- See the explanation below.
Explanation:Locking prevents other users in your organization from accidentally deleting or modifying critical resources, such as Azure subscription, resource group, or resource.
Note: In Azure, the term resource refers to an entity managed by Azure. For example, virtual machines, virtual networks, and storage accounts are all referred to as Azure resources.
1. In the Azure portal, type Virtual Networks in the search box, select Virtual Networks from the search results then select VNET2. Alternatively, browse to Virtual Networks in the left navigation pane.
2. In the Settings blade for virtual network VNET2, select Locks.
AZ-500 Microsoft Azure Security Technologies Part 05 Q20 182 3. To add a lock, select Add.
AZ-500 Microsoft Azure Security Technologies Part 05 Q20 183 4. For Lock type select Delete lock, and click OK