AZ-500 : Microsoft Azure Security Technologies : Part 06
-
You have an Azure virtual machine named VM1.
From Azure Security Center, you get the following high-severity recommendation: “Install endpoint protection solutions on virtual machine”.
You need to resolve the issue causing the high-severity recommendation.
What should you do?
- Add the Microsoft Antimalware extension to VM1.
- Install Microsoft System Center Security Management Pack for Endpoint Protection on VM1.
- Add the Network Watcher Agent for Windows extension to VM1.
- Onboard VM1 to Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP).
-
HOTSPOT
You have a file named File1.yaml that contains the following contents.

AZ-500 Microsoft Azure Security Technologies Part 06 Q02 184 You create an Azure container instance named container1 by using File1.yaml.
You need to identify where you can access the values of Variable1 and Variable2.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
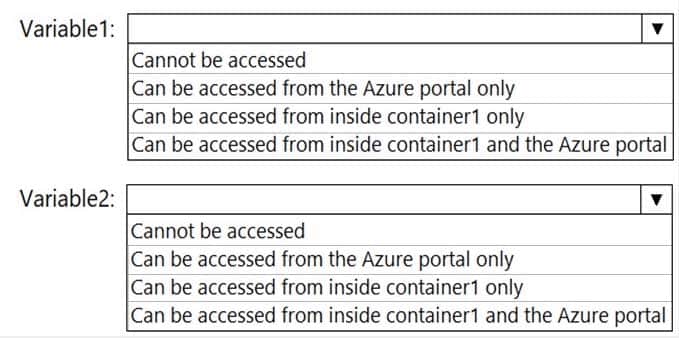
AZ-500 Microsoft Azure Security Technologies Part 06 Q02 185 Question 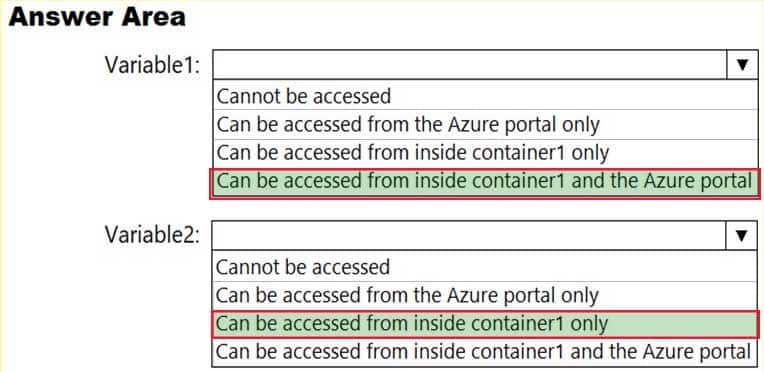
AZ-500 Microsoft Azure Security Technologies Part 06 Q02 185 Answer -
You have an Azure subscription that contains a virtual network. The virtual network contains the subnets shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 06 Q03 185a The subscription contains the virtual machines shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 06 Q03 185b You enable just in time (JIT) VM access for all the virtual machines.
You need to identify which virtual machines are protected by JIT.
Which virtual machines should you identify?
- VM4 only
- VM1 and VM3 only
- VM1, VM3 and VM4 only
- VM1, VM2, VM3, and VM4
Explanation:
An NSG needs to be enabled, either at the VM level or the subnet level. -
HOTSPOT
You have an Azure subscription that contains the virtual machines shown in the following table.
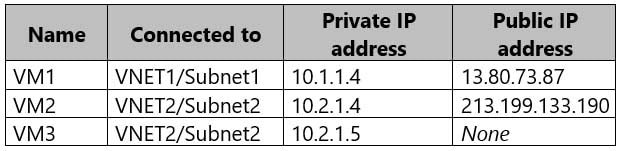
AZ-500 Microsoft Azure Security Technologies Part 06 Q04 186 Subnet1 and Subnet2 have a Microsoft.Storage service endpoint configured.
You have an Azure Storage account named storageacc1 that is configured as shown in the following exhibit.
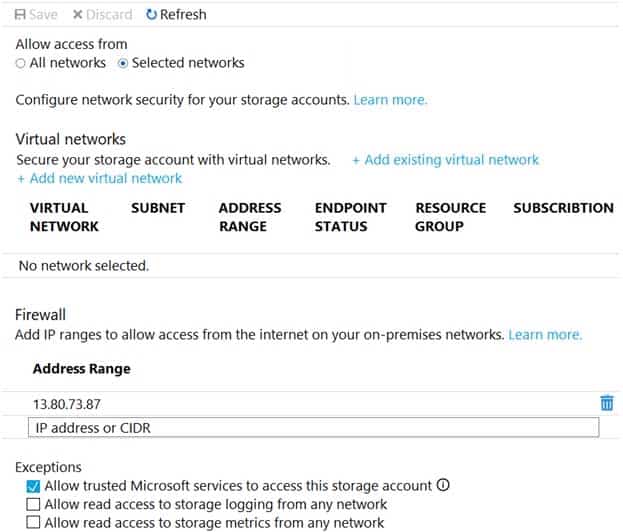
AZ-500 Microsoft Azure Security Technologies Part 06 Q04 187 For each of the following statements, select Yes if the statement is true. Otherwise, select No.

AZ-500 Microsoft Azure Security Technologies Part 06 Q04 188 Question 
AZ-500 Microsoft Azure Security Technologies Part 06 Q04 188 Answer Explanation:Box 1: Yes
The public IP of VM1 is allowed through the firewall.Box 2: No
The allowed virtual network list is empty so VM2 cannot access storageacc1 directly. The public IP address of VM2 is not in the allowed IP list so VM2 cannot access storageacc1 over the Internet.Box 3: No
The allowed virtual network list is empty so VM3 cannot access storageacc1 directly. VM3 does not have a public IP address so it cannot access storageacc1 over the Internet. -
HOTSPOT
You have Azure virtual machines that have Update Management enabled. The virtual machines are configured as shown in the following table.

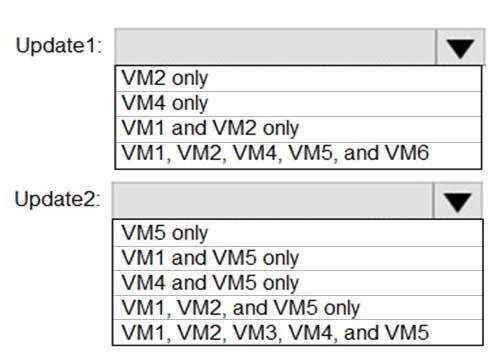
AZ-500 Microsoft Azure Security Technologies Part 06 Q05 189 You schedule two update deployments named Update1 and Update2. Update1 updates VM3. Update2 updates VM6.
Which additional virtual machines can be updated by using Update1 and Update2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
AZ-500 Microsoft Azure Security Technologies Part 06 Q05 190 Question 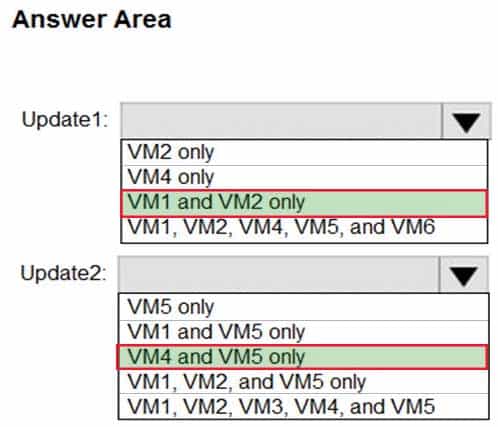
AZ-500 Microsoft Azure Security Technologies Part 06 Q05 190 Answer Explanation:An update deployment can apply to Windows VMs or Linux VMs but not both. The VMs can be in different regions, different subscriptions and different resource groups.
Update1: VM1 and VM2 only
VM3: Windows Server 2016.Update2: VM4 and VM5 only
VM6: CentOS 7.5.For Linux, the machine must have access to an update repository. The update repository can be private or public.
-
HOTSPOT
You have an Azure subscription named Sub1.
You create a virtual network that contains one subnet. On the subnet, you provision the virtual machines shown in the following table.
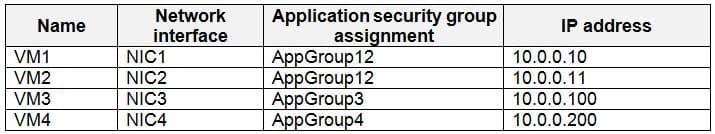
AZ-500 Microsoft Azure Security Technologies Part 06 Q06 191 Currently, you have not provisioned any network security groups (NSGs).
You need to implement network security to meet the following requirements:
– Allow traffic to VM4 from VM3 only.
– Allow traffic from the Internet to VM1 and VM2 only.
– Minimize the number of NSGs and network security rules.How many NSGs and network security rules should you create? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-500 Microsoft Azure Security Technologies Part 06 Q06 192 Question 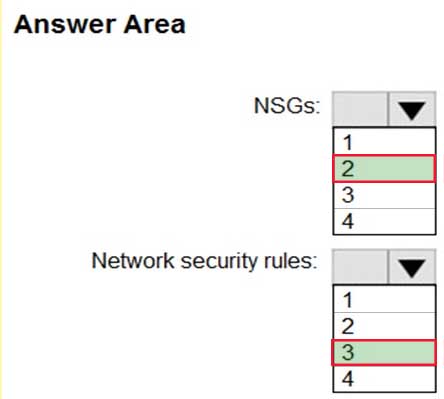
AZ-500 Microsoft Azure Security Technologies Part 06 Q06 192 Answer Explanation:NSGs: 2
Network security rules: 3
Not 2: You cannot specify multiple service tags or application groups) in a security rule.
-
HOTSPOT
You have an Azure key vault.
You need to delegate administrative access to the key vault to meet the following requirements:
Provide a user named User1 with the ability to set advanced access policies for the key vault.
Provide a user named User2 with the ability to add and delete certificates in the key vault.
Use the principle of least privilege.What should you use to assign access to each user? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
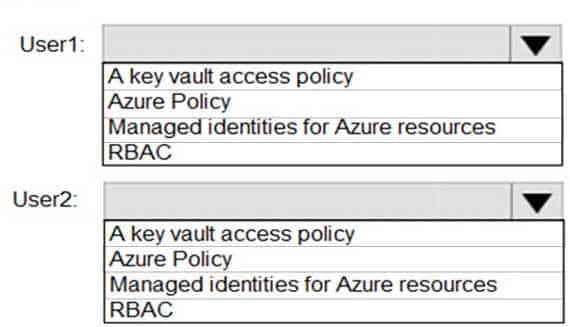
AZ-500 Microsoft Azure Security Technologies Part 06 Q07 193 Question 
AZ-500 Microsoft Azure Security Technologies Part 06 Q07 193 Answer Explanation:User1: RBAC
RBAC is used as the Key Vault access control mechanism for the management plane. It would allow a user with the proper identity to:
set Key Vault access policies
create, read, update, and delete key vaults
set Key Vault tagsNote: Role-based access control (RBAC) is a system that provides fine-grained access management of Azure resources. Using RBAC, you can segregate duties within your team and grant only the amount of access to users that they need to perform their jobs.
User2: A key vault access policy
A key vault access policy is the access control mechanism to get access to the key vault data plane. Key Vault access policies grant permissions separately to keys, secrets, and certificates. -
You have Azure Resource Manager templates that you use to deploy Azure virtual machines.
You need to disable unused Windows features automatically as instances of the virtual machines are provisioned.
What should you use?
- device compliance policies in Microsoft Intune
- Azure Automation State Configuration
- application security groups
- Azure Advisor
Explanation:
You can use Azure Automation State Configuration to manage Azure VMs (both Classic and Resource Manager), on-premises VMs, Linux machines, AWS VMs, and on-premises physical machines. Note: Azure Automation State Configuration provides a DSC pull server similar to the Windows Feature DSC Service so that target nodes automatically receive configurations, conform to the desired state, and report back on their compliance. The built-in pull server in Azure Automation eliminates the need to set up and maintain your own pull server. Azure Automation can target virtual or physical Windows or Linux machines, in the cloud or on-premises. -
You have an Azure Container Registry named Registry1.
From Azure Security Center, you enable Azure Container Registry vulnerability scanning of the images in Registry1.
You perform the following actions:
– Push a Windows image named Image1 to Registry1.
– Push a Linux image named Image2 to Registry1.
– Push a Windows image named Image3 to Registry1.
– Modify Image1 and push the new image as Image4 to Registry1.
– Modify Image2 and push the new image as Image5 to Registry1.Which two images will be scanned for vulnerabilities? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- Image4
- Image2
- Image1
- Image3
- Image5
Explanation:
Only Linux images are scanned. Windows images are not scanned. -
HOTSPOT
You have two Azure virtual machines in the East US 2 region as shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 06 Q10 194 You deploy and configure an Azure Key vault.
You need to ensure that you can enable Azure Disk Encryption on VM1 and VM2.
What should you modify on each virtual machine? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
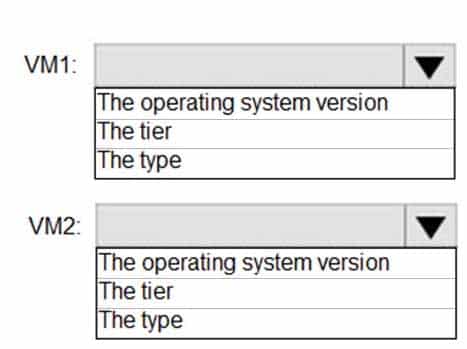
AZ-500 Microsoft Azure Security Technologies Part 06 Q10 195 Question 
AZ-500 Microsoft Azure Security Technologies Part 06 Q10 195 Answer Explanation:VM1: The Tier
The Tier needs to be upgraded to standard.
Disk Encryption for Windows and Linux IaaS VMs is in General Availability in all Azure public regions and Azure Government regions for Standard VMs and VMs with Azure Premium Storage.VM2: The type
Need to change the VMtype to any of A, D, DS, G, GS, F, and so on, series IaaS VMs.Not the operating system version: Ubuntu 16.04 is supported.
-
You have the Azure virtual machines shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 06 Q11 196 You create an Azure Log Analytics workspace named Analytics1 in RG1 in the East US region.
Which virtual machines can be enrolled in Analytics1?
- VM1 only
- VM1, VM2, and VM3 only
- VM1, VM2, VM3, and VM4
- VM1 and VM4 only
Explanation:Note: Create a workspace
– In the Azure portal, click All services. In the list of resources, type Log Analytics. As you begin typing, the list filters based on your input. Select Log Analytics.
– Click Create, and then select choices for the following items:Provide a name for the new Log Analytics workspace, such as DefaultLAWorkspace. OMS workspaces are now referred to as Log Analytics workspaces.
Select a Subscription to link to by selecting from the drop-down list if the default selected is not appropriate.
For Resource Group, select an existing resource group that contains one or more Azure virtual machines.
Select the Location your VMs are deployed to. For additional information, see which regions Log Analytics is available in.
Incorrect Answers:
B, C: A Log Analytics workspace provides a geographic location for data storage. VM2 and VM3 are at a different location.D: VM4 is a different resource group.
-
You are testing an Azure Kubernetes Service (AKS) cluster. The cluster is configured as shown in the exhibit. (Click the Exhibit tab.)
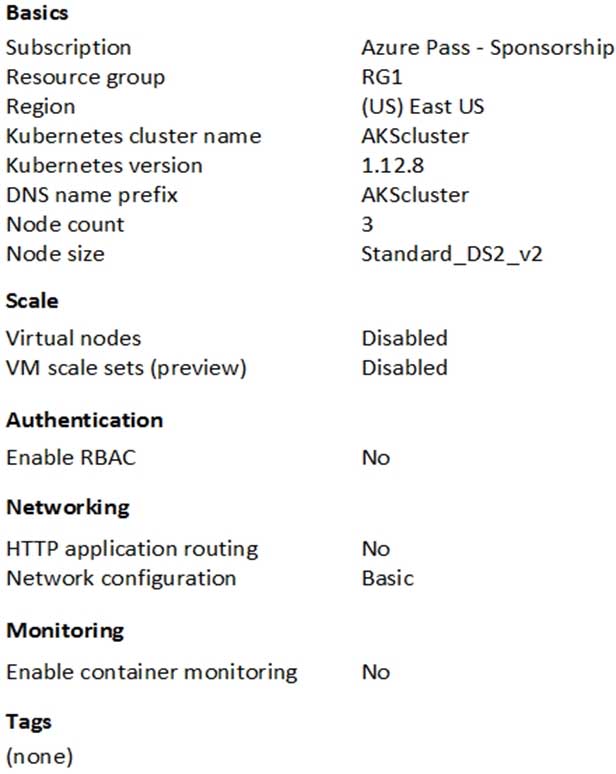
You plan to deploy the cluster to production. You disable HTTP application routing.
You need to implement application routing that will provide reverse proxy and TLS termination for AKS services by using a single IP address.
What should you do?
- Create an AKS Ingress controller.
- Install the container network interface (CNI) plug-in.
- Create an Azure Standard Load Balancer.
- Create an Azure Basic Load Balancer.
Explanation:
An ingress controller is a piece of software that provides reverse proxy, configurable traffic routing, and TLS termination for Kubernetes services. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription. The subscription contains 50 virtual machines that run Windows Server 2012 R2 or Windows Server 2016.
You need to deploy Microsoft Antimalware to the virtual machines.
Solution: You add an extension to each virtual machine.
Does this meet the goal?
- Yes
- No
Explanation:
You can use Visual Studio to enable and configure the Microsoft Antimalware service. This entails selecting Microsoft Antimalware extension from the dropdown list under Installed Extensions and click Add to configure with default antimalware configuration. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription. The subscription contains 50 virtual machines that run Windows Server 2012 R2 or Windows Server 2016.
You need to deploy Microsoft Antimalware to the virtual machines.
Solution: You connect to each virtual machine and add a Windows feature.
Does this meet the goal?
- Yes
- No
Explanation:
Microsoft Antimalware is deployed as an extension and not a feature. -
You have an Azure Active Directory (Azure AD) tenant named Contoso.com and an Azure Kubernetes Service (AKS) cluster AKS1.
You discover that AKS1 cannot be accessed by using accounts from Contoso.com.
You need to ensure AKS1 can be accessed by using accounts from Contoso.com. The solution must minimize administrative effort.
What should you do first?
- From Azure recreate AKS1.
- From AKS1, upgrade the version of Kubernetes.
- From Azure AD, implement Azure AD Premium.
- From Azure AD, configure the User settings.
-
You have an Azure subscription that contains an Azure Container Registry named Registry1. Azure Defender is enabled in the subscription.
You upload several container images to Register1.
You discover that vulnerability security scans were not performed.
You need to ensure that the container images are scanned for vulnerabilities when they are uploaded to Registry1.
What should you do?
- From the Azure portal modify the Pricing tier settings.
- From Azure CLI, lock the container images.
- Upload the container images by using AzCopy.
- Push the container images to Registry1 by using Docker
-
From Azure Security Center, you create a custom alert rule.
You need to configure which users will receive an email message when the alert is triggered.
What should you do?
- From Azure Monitor, create an action group.
- From Security Center, modify the Security policy settings of the Azure subscription.
- From Azure Active Directory (Azure AD), modify the members of the Security Reader role group.
- From Security Center, modify the alert rule.
-
You are configuring and securing a network environment.
You deploy an Azure virtual machine named VM1 that is configured to analyze network traffic.
You need to ensure that all network traffic is routed through VM1.
What should you configure?
- a system route
- a network security group (NSG)
- a user-defined route
Explanation:Although the use of system routes facilitates traffic automatically for your deployment, there are cases in which you want to control the routing of packets through a virtual appliance. You can do so by creating user defined routes that specify the next hop for packets flowing to a specific subnet to go to your virtual appliance instead, and enabling IP forwarding for the VM running as the virtual appliance.
Note: User Defined Routes
For most environments you will only need the system routes already defined by Azure. However, you may need to create a route table and add one or more routes in specific cases, such as:
– Force tunneling to the Internet via your on-premises network.
– Use of virtual appliances in your Azure environment.
– In the scenarios above, you will have to create a route table and add user defined routes to it. -
HOTSPOT
You have a network security group (NSG) bound to an Azure subnet.
You run Get-AzNetworkSecurityRuleConfig and receive the output shown in the following exhibit.
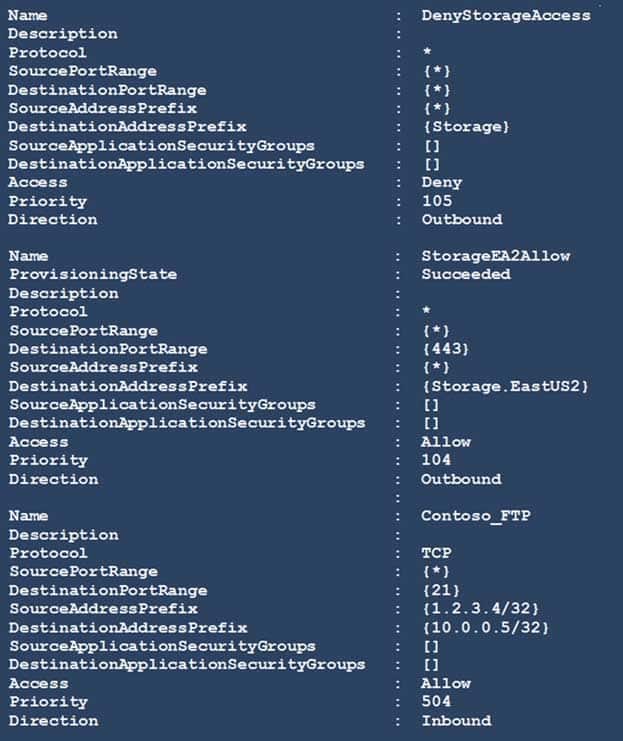
AZ-500 Microsoft Azure Security Technologies Part 06 Q19 198 Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

AZ-500 Microsoft Azure Security Technologies Part 06 Q19 199 Question 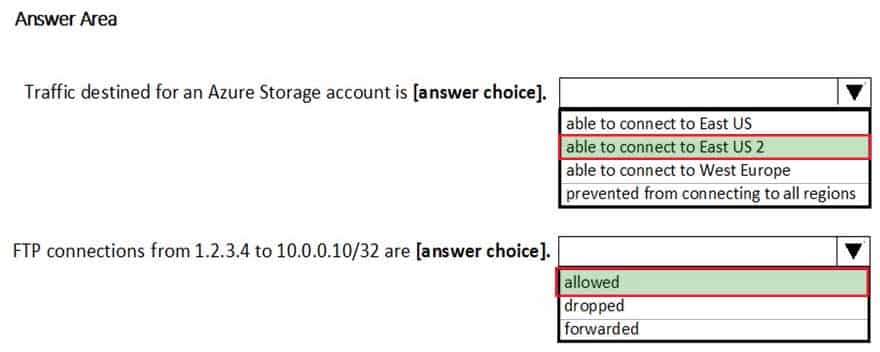
AZ-500 Microsoft Azure Security Technologies Part 06 Q19 199 Answer Explanation:Box 1: able to connect to East US 2
The StorageEA2Allow has DestinationAddressPrefix {Storage/EastUS2}Box 2: allowed
TCP Port 21 controls the FTP session. Contoso_FTP has SourceAddressPrefix {1.2.3.4/32} and DestinationAddressPrefix {10.0.0.5/32}Note:
The Get-AzureRmNetworkSecurityRuleConfig cmdlet gets a network security rule configuration for an Azure network security group.
Security rules in network security groups enable you to filter the type of network traffic that can flow in and out of virtual network subnets and network interfaces. -
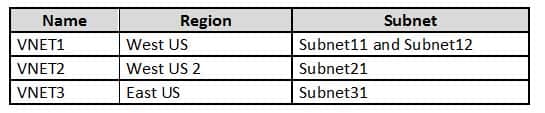
You have an Azure subscription that contains the virtual networks shown in the following table.
AZ-500 Microsoft Azure Security Technologies Part 06 Q20 200 The subscription contains the virtual machines shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 06 Q20 201 On NIC1, you configure an application security group named ASG1.
On which other network interfaces can you configure ASG1?
- NIC2 only
- NIC2, NIC3, NIC4, and NIC5
- NIC2 and NIC3 only
- NIC2, NIC3, and NIC4 only
Explanation:
Only network interfaces in NVET1, which consists of Subnet11 and Subnet12, can be configured in ASG1, as all network interfaces assigned to an application security group have to exist in the same virtual network that the first network interface assigned to the application security group is in.