AZ-500 : Microsoft Azure Security Technologies : Part 07
-
You have 15 Azure virtual machines in a resource group named RG1.
All the virtual machines run identical applications.
You need to prevent unauthorized applications and malware from running on the virtual machines.
What should you do?
- Apply an Azure policy to RG1.
- From Azure Security Center, configure adaptive application controls.
- Configure Azure Active Directory (Azure AD) Identity Protection.
- Apply a resource lock to RG1.
Explanation:
Adaptive application control is an intelligent, automated end-to-end application whitelisting solution from Azure Security Center. It helps you control which applications can run on your Azure and non-Azure VMs (Windows and Linux), which, among other benefits, helps harden your VMs against malware. Security Center uses machine learning to analyze the applications running on your VMs and helps you apply the specific whitelisting rules using this intelligence. -
You have a web app hosted on an on-premises server that is accessed by using a URL of https://www.contoso.com.
You plan to migrate the web app to Azure. You will continue to use https://www.contoso.com.
You need to enable HTTPS for the Azure web app.
What should you do first?
- Export the public key from the on-premises server and save the key as a P7b file.
- Export the private key from the on-premises server and save the key as a PFX file that is encrypted by using TripleDES.
- Export the public key from the on-premises server and save the key as a CER file.
- Export the private key from the on-premises server and save the key as a PFX file that is encrypted by using AES256.
-
You plan to deploy Azure container instances.
You have a containerized application that validates credit cards. The application is comprised of two containers: an application container and a validation container.
The application container is monitored by the validation container. The validation container performs security checks by making requests to the application container and waiting for responses after every transaction.
You need to ensure that the application container and the validation container are scheduled to be deployed together. The containers must communicate to each other only on ports that are not externally exposed.
What should you include in the deployment?
- application security groups
- network security groups (NSGs)
- management groups
- container groups
Explanation:
Azure Container Instances supports the deployment of multiple containers onto a single host using a container group. A container group is useful when building an application sidecar for logging, monitoring, or any other configuration where a service needs a second attached process. -
DRAG DROP
You are configuring network connectivity for two Azure virtual networks named VNET1 and VNET2.
You need to implement VPN gateways for the virtual networks to meet the following requirements:
– VNET1 must have six site-to-site connections that use BGP.
– VNET2 must have 12 site-to-site connections that use BGP.
– Costs must be minimized.Which VPN gateway SKU should you use for each virtual network? To answer, drag the appropriate SKUs to the correct networks. Each SKU may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

AZ-500 Microsoft Azure Security Technologies Part 07 Q04 202 Question 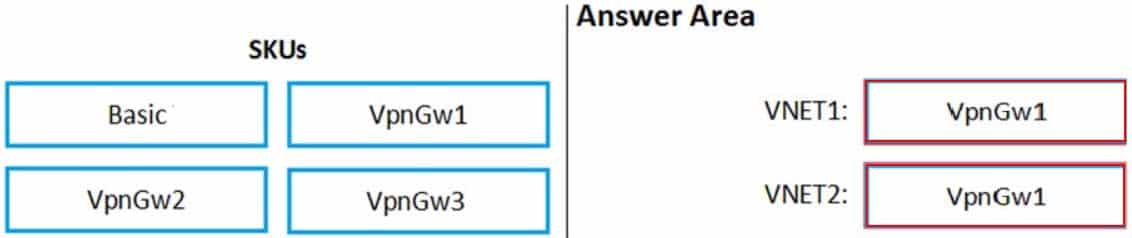
AZ-500 Microsoft Azure Security Technologies Part 07 Q04 202 Answer -
You are securing access to the resources in an Azure subscription.
A new company policy states that all the Azure virtual machines in the subscription must use managed disks.
You need to prevent users from creating virtual machines that use unmanaged disks.
What should you use?
- Azure Monitor
- Azure Policy
- Azure Security Center
- Azure Service Health
-
HOTSPOT
You have an Azure subscription that contains a storage account named storage1 and several virtual machines. The storage account and virtual machines are in the same Azure region. The network configurations of the virtual machines are shown in the following table.
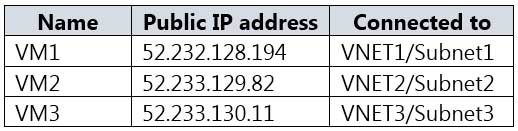
AZ-500 Microsoft Azure Security Technologies Part 07 Q06 203 The virtual network subnets have service endpoints defined as shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 07 Q06 204 You configure the following Firewall and virtual networks settings for storage1:
Allow access from: Selected networks
Virtual networks: VNET3\Subnet3
Firewall – Address range: 52.233.129.0/24For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
AZ-500 Microsoft Azure Security Technologies Part 07 Q07 205 Question 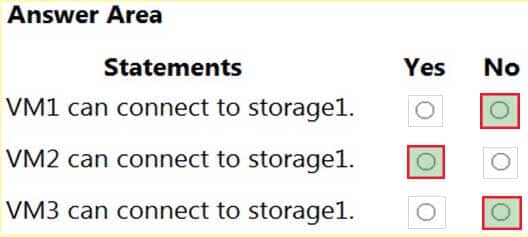
AZ-500 Microsoft Azure Security Technologies Part 07 Q07 205 Answer Explanation:Box 1: No
VNet1 has a service endpoint configure for Azure Storage. However, the Azure storage does not allow access from VNet1 or the public IP address of VM1.Box 2: Yes
VNet2 does not have a service endpoint configured. However, the Azure storage allows access from the public IP address of VM2.Box 3: No
Azure storage allows access from VNet3. However, VNet3 does not have a service endpoint for Azure storage. The Azure storage also does not allow access from the public IP of VM3. -
You plan to create an Azure Kubernetes Service (AKS) cluster in an Azure subscription.
The manifest of the registered server application is shown in the following exhibit.

AZ-500 Microsoft Azure Security Technologies Part 07 Q07 206 You need to ensure that the AKS cluster and Azure Active Directory (Azure AD) are integrated.
Which property should you modify in the manifest?
- accessTokenAcceptedVersion
- keyCredentials
- groupMembershipClaims
- acceptMappedClaims
-
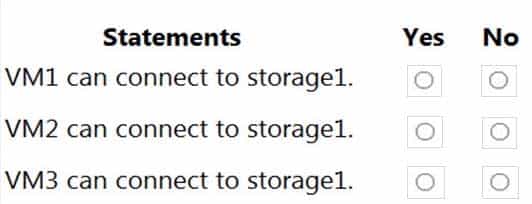
HOTSPOT
You have the Azure virtual networks shown in the following table.
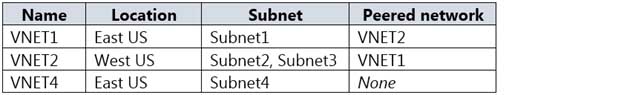
AZ-500 Microsoft Azure Security Technologies Part 07 Q08 207 You have the Azure virtual machines shown in the following table.
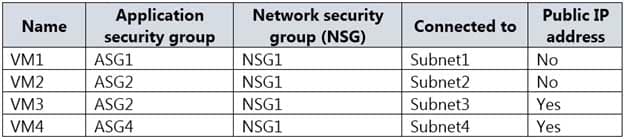
AZ-500 Microsoft Azure Security Technologies Part 07 Q08 208 The firewalls on all the virtual machines allow ping traffic.
NSG1 is configured as shown in the following exhibit.
Inbound security rules
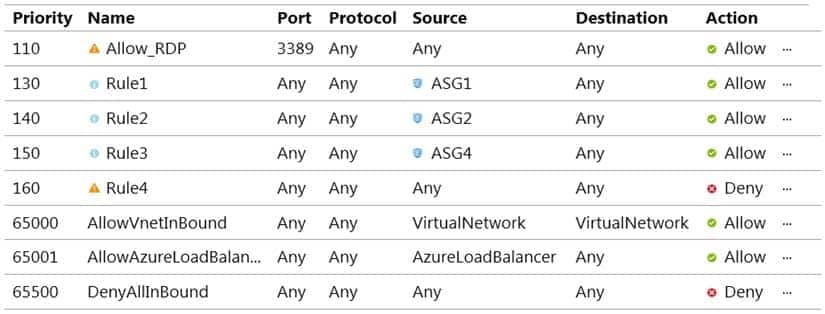
AZ-500 Microsoft Azure Security Technologies Part 07 Q08 209 Outbound security rules

AZ-500 Microsoft Azure Security Technologies Part 07 Q08 210 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
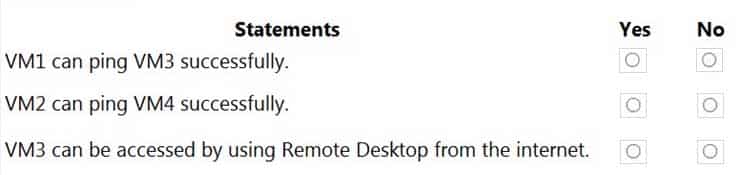
AZ-500 Microsoft Azure Security Technologies Part 07 Q08 211 Question 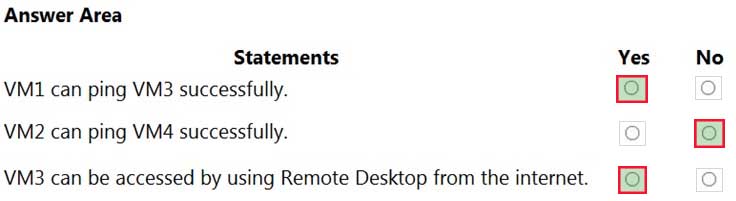
AZ-500 Microsoft Azure Security Technologies Part 07 Q08 211 Answer Explanation:Box 1: Yes
VM1 and VM3 are on peered VNets. The firewall rules with a source of ASG1 and ASG2 allow ‘any’ traffic on ‘any’ protocol so pings are allowed between VM1 and VM3.Box 2: No
VM2 and VM4 are on separate VNets and the VNets are not peered. Therefore, the pings would have to go over the Internet. VM4 does have a public IP and the firewall allows pings. However, for VM2 to be able to ping VM4, VM2 would also need a public IP address. In Azure, pings don’t go out through the default gateway as they would in a physical network. For an Azure VM to ping external IPs, the VM must have a public IP address assigned to it.Box 3: Yes
VM3 has a public IP address and the firewall allows traffic on port 3389. -
Case Study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.
General Overview
Fabrikam, Inc. is a consulting company that has a main office in Montreal and branch offices in Seattle and New York. Fabrikam has IT, human resources (HR), and finance departments.
Existing Environment
Network Environment
Fabrikam has a Microsoft 365 subscription and an Azure subscription named subscription1.
The network contains an on-premises Active Directory domain named Fabrikam.com. The domain contains two organizational units (OUs) named OU1 and OU2. Azure AD Connect cloud sync syncs only OU1.
The Azure resources hierarchy is shown in the following exhibit.
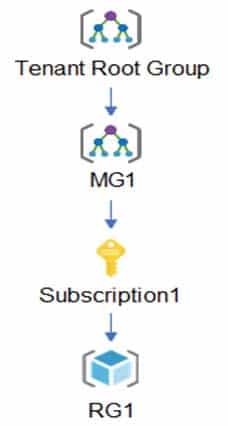
AZ-500 Microsoft Azure Security Technologies Part 07 Q09 212 The Azure Active Directory (Azure AD) tenant contains the users shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 07 Q09 213 Azure AD contains the resources shown in the following table.
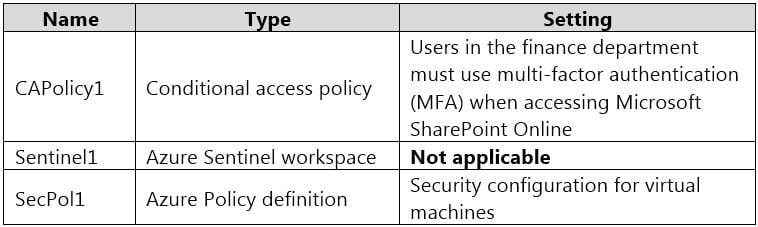
AZ-500 Microsoft Azure Security Technologies Part 07 Q09 214 Subscription1 Resources
Subscription1 contains the virtual networks shown in the following table.
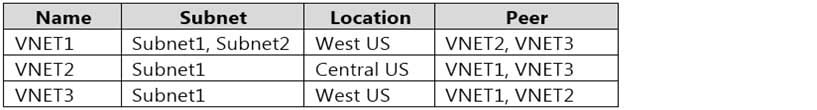
AZ-500 Microsoft Azure Security Technologies Part 07 Q09 215 Subscription1 contains the network security groups (NSGs) shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 07 Q09 216 Subscription1 contains the virtual machines shown in the following table.
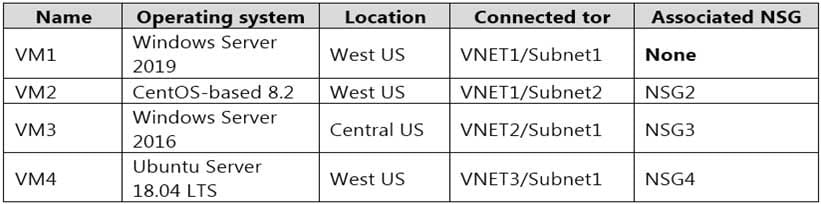
AZ-500 Microsoft Azure Security Technologies Part 07 Q09 217 Subscription1 contains the Azure key vaults shown in the following table.
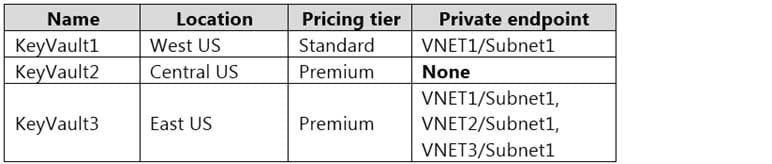
AZ-500 Microsoft Azure Security Technologies Part 07 Q09 218 Subscription1 contains a storage account named storage1 in the West US Azure region.
Planned Changes and Requirements
Planned Changes
Fabrikam plans to implement the following changes:
– Create two application security groups as shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 07 Q09 219 – Associate the network interface of VM1 to ASG1.
– Deploy SecPol1 by using Azure Security Center.
– Deploy a third-party app named App1. A version of App1 exists for all available operating systems.
– Create a resource group named RG2.
– Sync OU2 to Azure AD.
– Add User1 to Group1.Technical Requirements
Fabrikam identifies the following technical requirements:
– The finance department users must reauthenticate after three hours when they access SharePoint Online.
– Storage1 must be encrypted by using customer-managed keys and automatic key rotation.
– From Sentinel1, you must ensure that the following notebooks can be launched:
– Entity Explorer – Account
– Entity Explorer – Windows Host
– Guided Investigation Process Alerts
– VM1, VM2, and VM3 must be encrypted by using Azure Disk Encryption.
– Just in time (JIT) VM access for VM1, VM2, and VM3 must be enabled.
– App1 must use a secure connection string stored in KeyVault1.
– KeyVault1 traffic must NOT travel over the internet.Subscription1 Resources
Subscription1 contains the virtual networks shown in the following table.
-
HOTSPOT
You need to configure support for Azure Sentinel notebooks to meet the technical requirements.
What is the minimum number of Azure container registries and Azure Machine Learning workspaces required?

AZ-500 Microsoft Azure Security Technologies Part 07 Q09 220 Question 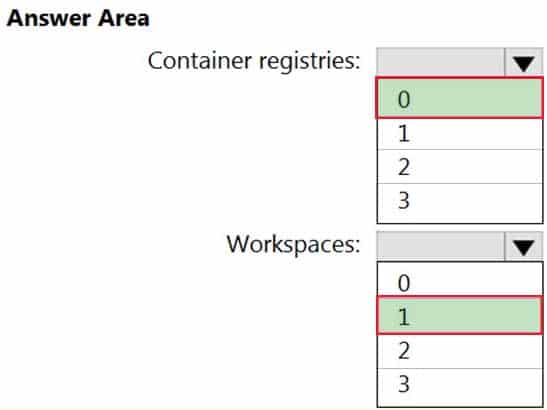
AZ-500 Microsoft Azure Security Technologies Part 07 Q09 220 Answer -
From Azure Security Center, you need to deploy SecPol1.
What should you do first?
- Enable Azure Defender.
- Create an Azure Management group.
- Create an initiative.
- Configure continuous export.
-
-
Case Study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and two branch offices in Seattle and New York.
The company hosts its entire server infrastructure in Azure.
Contoso has two Azure subscriptions named Sub1 and Sub2. Both subscriptions are associated to an Azure Active Directory (Azure AD) tenant named contoso.com.
Existing Environment
Azure AD
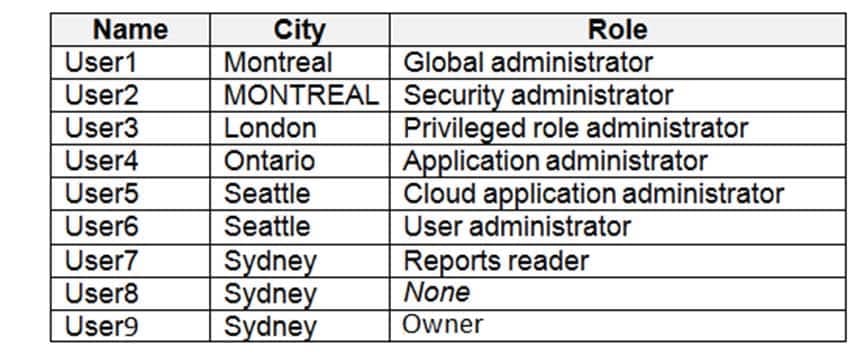
Contoso.com contains the users shown in the following table.
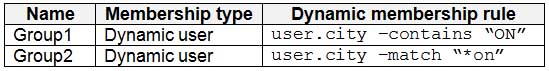
AZ-500 Microsoft Azure Security Technologies Part 07 Q10 221 Contoso.com contains the security groups shown in the following table.
AZ-500 Microsoft Azure Security Technologies Part 07 Q10 222 Sub1
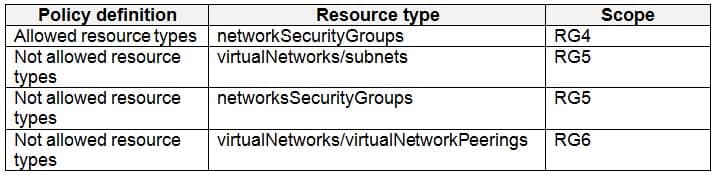
Sub1 contains six resource groups named RG1, RG2, RG3, RG4, RG5, and RG6.
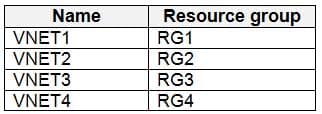
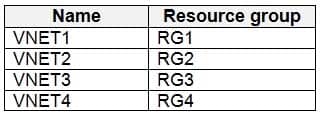
User9 creates the virtual networks shown in the following table.
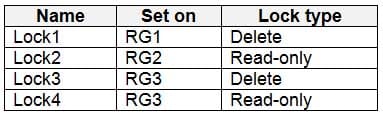
AZ-500 Microsoft Azure Security Technologies Part 07 Q10 223 Sub1 contains the locks shown in the following table.
AZ-500 Microsoft Azure Security Technologies Part 07 Q10 224 Sub1 contains the Azure policies shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 07 Q10 225 Sub2
Sub2 contains the virtual networks shown in the following table.
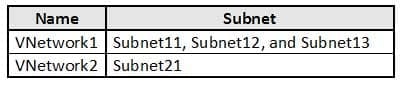
AZ-500 Microsoft Azure Security Technologies Part 07 Q10 226 Sub2 contains the virtual machines shown in the following table.
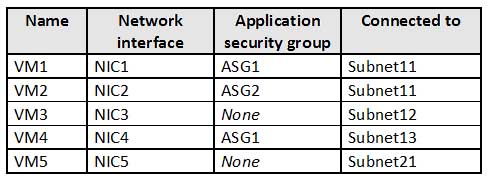
AZ-500 Microsoft Azure Security Technologies Part 07 Q10 227 All virtual machines have public IP addresses and the Web Server (IIS) role installed. The firewalls for each virtual machine allow ping requests and web requests.
Sub2 contains the network security groups (NSGs) shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 07 Q10 228 NSG1 has the inbound security rules shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 07 Q10 229 NSG2 has the inbound security rules shown in the following table.
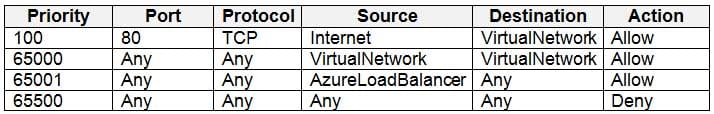
AZ-500 Microsoft Azure Security Technologies Part 07 Q10 230 NSG3 has the inbound security rules shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 07 Q10 231 NSG4 has the inbound security rules shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 07 Q10 232 NSG1, NSG2, NSG3, and NSG4 have the outbound security rules shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 07 Q10 233 Technical Requirements
Contoso identifies the following technical requirements:
– Deploy Azure Firewall to VNetwork1 in Sub2.
– Register an application named App2 in contoso.com.
– Whenever possible, use the principle of least privilege.
– Enable Azure AD Privileged Identity Management (PIM) for contoso.com.-
HOTSPOT
You assign User8 the Owner role for RG4, RG5, and RG6.
In which resource groups can User8 create virtual networks and NSGs by using the Azure portal? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
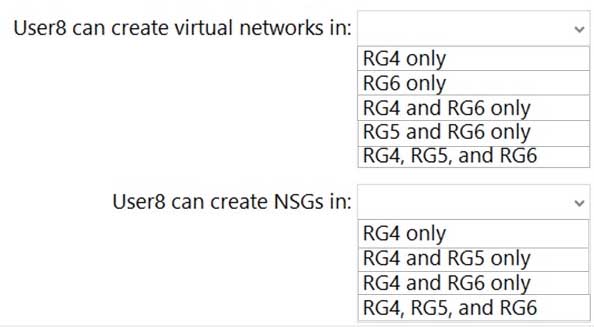
AZ-500 Microsoft Azure Security Technologies Part 07 Q10 234 Question 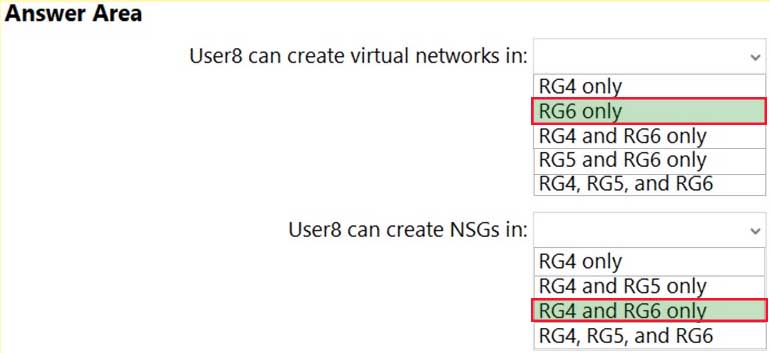
AZ-500 Microsoft Azure Security Technologies Part 07 Q10 234 Answer -
HOTSPOT
Which virtual networks in Sub1 can User9 modify and delete in their current state? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-500 Microsoft Azure Security Technologies Part 07 Q10 236 Question 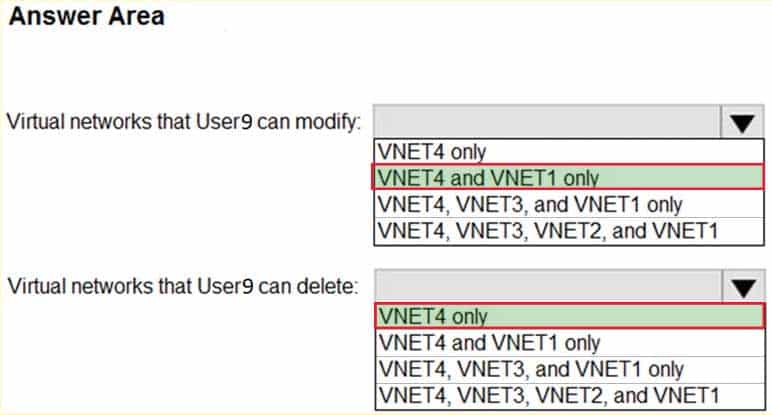
AZ-500 Microsoft Azure Security Technologies Part 07 Q10 236 Question Explanation:Box 1: VNET4 and VNET1 only
RG1 has only Delete lock, while there are no locks on RG4.
RG2 and RG3 both have Read-only locks.Box 2: VNET4 only
There are no locks on RG4, while the other resource groups have either Delete or Read-only locks.Note: As an administrator, you may need to lock a subscription, resource group, or resource to prevent other users in your organization from accidentally deleting or modifying critical resources. You can set the lock level to CanNotDelete or ReadOnly. In the portal, the locks are called Delete and Read-only respectively.
– CanNotDelete means authorized users can still read and modify a resource, but they can’t delete the resource.
– ReadOnly means authorized users can read a resource, but they can’t delete or update the resource. Applying this lock is similar to restricting all authorized users to the permissions granted by the Reader role.Scenario:
Sub1 contains six resource groups named RG1, RG2, RG3, RG4, RG5, and RG6.User9 creates the virtual networks shown in the following table.
AZ-500 Microsoft Azure Security Technologies Part 07 Q10 237 Sub1 contains the locks shown in the following table.
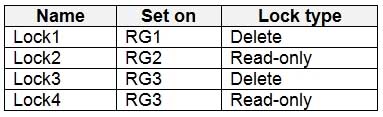
AZ-500 Microsoft Azure Security Technologies Part 07 Q10 238
-
-
Case Study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.Overview
Litware, Inc. is a digital media company that has 500 employees in the Chicago area and 20 employees in the San Francisco area.
Existing Environment
Litware has an Azure subscription named Sub1 that has a subscription ID of 43894a43-17c2-4a39-8cfc-3540c2653ef4.
Sub1 is associated to an Azure Active Directory (Azure AD) tenant named litwareinc.com. The tenant contains the user objects and the device objects of all the Litware employees and their devices. Each user is assigned an Azure AD Premium P2 license. Azure AD Privileged Identity Management (PIM) is activated.
The tenant contains the groups shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 07 Q11 239 The Azure subscription contains the objects shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 07 Q11 240 Azure Security Center is set to the Standard tier.
Requirements
Planned Changes
Litware plans to deploy the Azure resources shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 07 Q11 241 Identity and Access Requirements
Litware identifies the following identity and access requirements:
– All San Francisco users and their devices must be members of Group1.
– The members of Group2 must be assigned the Contributor role to RG2 by using a permanent eligible assignment.
– Users must be prevented from registering applications in Azure AD and from consenting to applications that access company information on the users’ behalf.Platform Protection Requirements
Litware identifies the following platform protection requirements:
– Microsoft Antimalware must be installed on the virtual machines in RG1.
– The members of Group2 must be assigned the Azure Kubernetes Service Cluster Admin Role.
– Azure AD users must be able to authenticate to AKS1 by using their Azure AD credentials.
– Following the implementation of the planned changes, the IT team must be able to connect to VM0 by using JIT VM access.
– A new custom RBAC role named Role1 must be used to delegate the administration of the managed disks in RG1. Role1 must be available only for RG1.Security Operations Requirements
Litware must be able to customize the operating system security configurations in Azure Security Center.
Data and Application Requirements
Litware identifies the following data and applications requirements:
– The users in Group2 must be able to authenticate to SQLDB1 by using their Azure AD credentials.
– WebApp1 must enforce mutual authentication.General Requirements
Litware identifies the following general requirements:
– Whenever possible, administrative effort must be minimized.
– Whenever possible, use of automation must be maximized.-
You need to ensure that you can meet the security operations requirements. What should you do first?
- Turn on Auto Provisioning in Security Center.
- Integrate Security Center and Microsoft Cloud App Security.
- Upgrade the pricing tier of Security Center to Standard.
- Modify the Security Center workspace configuration.
Explanation:The Standard tier extends the capabilities of the Free tier to workloads running in private and other public clouds, providing unified security management and threat protection across your hybrid cloud workloads. The Standard tier also adds advanced threat detection capabilities, which uses built-in behavioral analytics and machine learning to identify attacks and zero-days exploits, access and application controls to reduce exposure to network attacks and malware, and more.
Scenario: Security Operations Requirements
Litware must be able to customize the operating system security configurations in Azure Security Center.
-
-
SIMULATION
A user named Debbie has the Azure app installed on her mobile device.
You need to ensure that [email protected] is alerted when a resource lock is deleted.
To complete this task, sign in to the Azure portal.
- See the explanation below.
Explanation:You need to configure an alert rule in Azure Monitor.
1. Type Monitor into the search box and select Monitor from the search results.
2. Click on Alerts.
3. Click on +New Alert Rule.
4. In the Scope section, click on the Select resource link.
5. In the Filter by resource type box, type locks and select Management locks (locks) from the filtered results.
6. Select the subscription then click the Done button.
7. In the Condition section, click on the Select condition link.
8. Select the Delete management locks condition the click the Done button.
9. In the Action group section, click on the Select action group link.
10 Click the Create action group button to create a new action group.
11. Give the group a name such as Debbie Mobile App (it doesn’t matter what name you enter for the exam) then click the Next: Notifications > button.
12. In the Notification type box, select the Email/SMS message/Push/Voice option.
13. In the Email/SMS message/Push/Voice window, tick the Azure app Push Notifications checkbox and enter [email protected] in the Azure account email field.
14. Click the OK button to close the window.
15. Enter a name such as Debbie Mobile App in the notification name box.
16. Click the Review & Create button then click the Create button to create the action group.
17. Back in the Create alert rule window, in the Alert rule details section, enter a name such as Management lock deletion in the Alert rule name field.
18. Click the Create alert rule button to create the alert rule. -
You are troubleshooting a security issue for an Azure Storage account.
You enable the diagnostic logs for the storage account.
What should you use to retrieve the diagnostics logs?
- Azure Storage Explorer
- SQL query editor in Azure
- File Explorer in Windows
- Azure Security Center
Explanation:If you want to download the metrics for long-term storage or to analyze them locally, you must use a tool or write some code to read the tables. You must download the minute metrics for analysis. The tables do not appear if you list all the tables in your storage account, but you can access them directly by name. Many storage-browsing tools are aware of these tables and enable you to view them directly (see Azure Storage Client Tools for a list of available tools).
Microsoft provides several graphical user interface (GUI) tools for working with the data in your Azure Storage account. All of the tools outlined in the following table are free.

AZ-500 Microsoft Azure Security Technologies Part 07 Q13 242 Note:
There are several versions of this question in the exam. The questions in the exam have two different correct answers:
1. Azure Storage Explorer
2. AZCopyOther incorrect answer options you may see on the exam include the following:
1. Azure Monitor
2. The Security & Compliance admin center
3. Azure Cosmos DB explorer
4. Azure Monitor -
SIMULATION
You plan to connect several Windows servers to the WS11641655 Azure Log Analytics workspace.
You need to ensure that the events in the System event logs are collected automatically to the workspace after you connect the Windows servers.
To complete this task, sign in to the Azure portal and modify the Azure resources.
- See the explanation below.
Explanation:Azure Monitor can collect events from the Windows event logs or Linux Syslog and performance counters that you specify for longer term analysis and reporting, and take action when a particular condition is detected. Follow these steps to configure collection of events from the Windows system log and Linux Syslog, and several common performance counters to start with.
Data collection from Windows VM
1. In the Azure portal, locate the WS11641655 Azure Log Analytics workspace then select Advanced settings.
AZ-500 Microsoft Azure Security Technologies Part 07 Q14 243 2. Select Data, and then select Windows Event Logs.
3. You add an event log by typing in the name of the log. Type System and then select the plus sign +.
4. In the table, check the severities Error and Warning. (for this question, select all severities to ensure that ALL logs are collected).
5. Select Save at the top of the page to save the configuration. -
SIMULATION
You need to ensure that the AzureBackupReport log for the Vault1 Recovery Services vault is stored in the WS11641655 Azure Log Analytics workspace.
To complete this task, sign in to the Azure portal and modify the Azure resources.
- See the explanation below.
Explanation:1. In the Azure portal, type Recovery Services Vaults in the search box, select Recovery Services Vaults from the search results then select Vault1. Alternatively, browse to Recovery Services Vaults in the left navigation pane.
2. In the properties of Vault1, scroll down to the Monitoring section and select Diagnostic Settings.
3. Click the Add a diagnostic setting link.
4. Enter a name in the Diagnostic settings name box.
5. In the Log section, select AzureBackupReport.
AZ-500 Microsoft Azure Security Technologies Part 07 Q15 244 6. In the Destination details section, select Send to log analytics
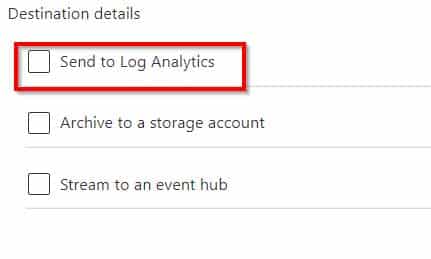
AZ-500 Microsoft Azure Security Technologies Part 07 Q15 245 7. Select the WS11641655 Azure Log Analytics workspace.
8. Click the Save button to save the changes. -
SIMULATION
You need to ensure that the audit logs from the SQLdb1 Azure SQL database are stored in the WS11641655 Azure Log Analytics workspace.
To complete this task, sign in to the Azure portal and modify the Azure resources.
- See explanation below.
Explanation:1. In the Azure portal, type SQL in the search box, select SQL databases from the search results then select SQLdb1. Alternatively, browse to SQL databases in the left navigation pane.
2. In the properties of SQLdb1, scroll down to the Security section and select Auditing.
3. Turn auditing on if it isn’t already, tick the Log Analytics checkbox then click on Configure.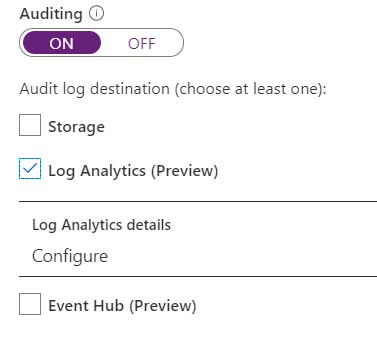
AZ-500 Microsoft Azure Security Technologies Part 07 Q16 246 4. Select the WS11641655 Azure Log Analytics workspace.
5. Click Save to save the changes. -
HOTSPOT
You are configuring just in time (JIT) VM access to a Windows Server 2019 Azure virtual machine.
You need to grant users PowerShell access to the virtual machine by using JIT VM access.
What should you configure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
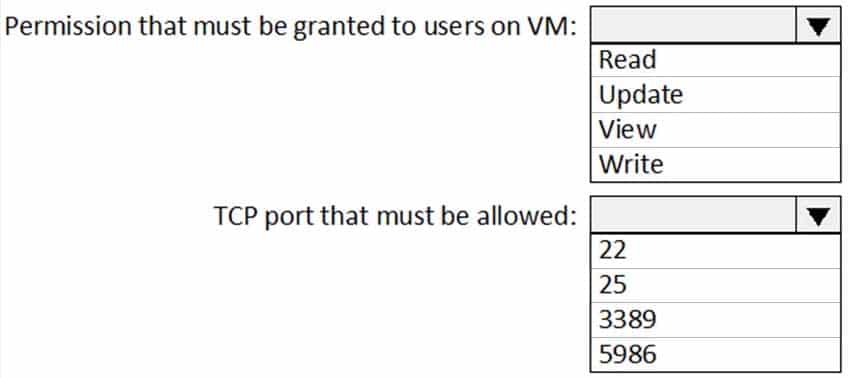
AZ-500 Microsoft Azure Security Technologies Part 07 Q17 247 Question 
AZ-500 Microsoft Azure Security Technologies Part 07 Q17 247 Answer -
HOTSPOT
You have an Azure subscription that contains the resources shown in the following table.
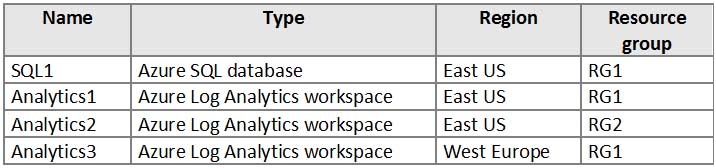
AZ-500 Microsoft Azure Security Technologies Part 07 Q18 248 You create the Azure Storage accounts shown in the following table.
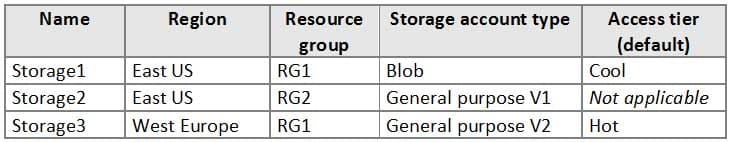
AZ-500 Microsoft Azure Security Technologies Part 07 Q18 249 You need to configure auditing for SQL1.
Which storage accounts and Log Analytics workspaces can you use as the audit log destination? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-500 Microsoft Azure Security Technologies Part 07 Q18 250 Question 
AZ-500 Microsoft Azure Security Technologies Part 07 Q18 250 Answer -
HOTSPOT
You have an Azure subscription named Sub1. Sub1 has an Azure Storage account named storage1 that contains the resources shown in the following table.
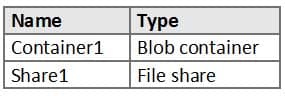
AZ-500 Microsoft Azure Security Technologies Part 07 Q19 251 You generate a shared access signature (SAS) to connect to the blob service and the file service.
Which tool can you use to access the contents in Container1 and Share1 by using the SAS? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-500 Microsoft Azure Security Technologies Part 07 Q19 252 Question 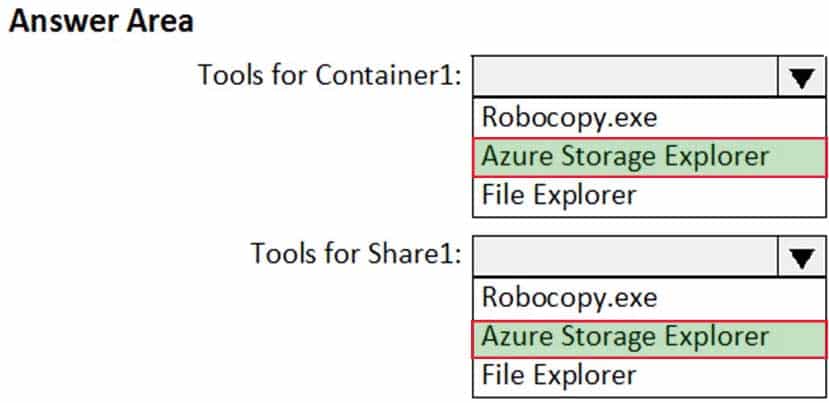
AZ-500 Microsoft Azure Security Technologies Part 07 Q19 252 Answer -
You have an Azure Storage account named storage1 that has a container named container1.
You need to prevent the blobs in container1 from being modified.
What should you do?
- From container1, change the access level.
- From container1, add an access policy.
- From container1, modify the Access Control (IAM) settings.
- From storage1, enable soft delete for blobs.