AZ-500 : Microsoft Azure Security Technologies : Part 08
-
Your company has an Azure Active Directory (Azure AD) tenant named contoso.com.
You plan to create several security alerts by using Azure Monitor.
You need to prepare the Azure subscription for the alerts.
What should you create first?
- an Azure Storage account
- an Azure Log Analytics workspace
- an Azure event hub
- an Azure Automation account
-
You company has an Azure subscription named Sub1. Sub1 contains an Azure web app named WebApp1 that uses Azure Application Insights. WebApp1 requires users to authenticate by using OAuth 2.0 client secrets.
Developers at the company plan to create a multi-step web test app that preforms synthetic transactions emulating user traffic to Web App1.
You need to ensure that web tests can run unattended.
What should you do first?
- In Microsoft Visual Studio, modify the .webtest file.
- Upload the .webtest file to Application Insights.
- Register the web test app in Azure AD.
- Add a plug-in to the web test app.
-
You have an Azure subscription named Subscription1.
You deploy a Linux virtual machine named VM1 to Subscription1.
You need to monitor the metrics and the logs of VM1.
What should you use?
- the AzurePerformanceDiagnostics extension
- Azure HDInsight
- Linux Diagnostic Extension (LAD) 3.0
- Azure Analysis Services
-
You onboard Azure Sentinel. You connect Azure Sentinel to Azure Security Center.
You need to automate the mitigation of incidents in Azure Sentinel. The solution must minimize administrative effort.
What should you create?
- an alert rule
- a playbook
- a function app
- a runbook
-
You have an Azure Active Directory (Azure AD) tenant named contoso.com.
You need to configure diagnostic settings for contoso.com. The solution must meet the following requirements:
– Retain logs for two years.
– Query logs by using the Kusto query language.
– Minimize administrative effort.Where should you store the logs?
- an Azure event hub
- an Azure Log Analytics workspace
- an Azure Storage account
-
You are troubleshooting a security issue for an Azure Storage account.
You enable the diagnostic logs for the storage account.
What should you use to retrieve the diagnostics logs?
- the Security & Compliance admin center
- Azure Security Center
- Azure Cosmos DB explorer
- AzCopy
Explanation:
If you want to download the metrics for long-term storage or to analyze them locally, you must use a tool or write some code to read the tables. You must download the minute metrics for analysis. The tables do not appear if you list all the tables in your storage account, but you can access them directly by name. Many storage-browsing tools are aware of these tables and enable you to view them directly (see Azure Storage Client Tools for a list of available tools).
Microsoft provides several graphical user interface (GUI) tools for working with the data in your Azure Storage account. All of the tools outlined in the following table are free.
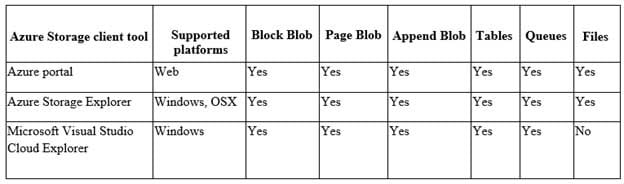
AZ-500 Microsoft Azure Security Technologies Part 08 Q06 253 Note:
There are several versions of this question in the exam. The questions in the exam have two different correct answers:
1. Azure Storage Explorer
2. AZCopyOther incorrect answer options you may see on the exam include the following:
1. SQL query editor in Azure
2. File Explorer in Windows
3. Azure Monitor -
You have an Azure subscription that contains the virtual machines shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 08 Q07 254 From Azure Security Center, you turn on Auto Provisioning.
You deploy the virtual machines shown in the following table.
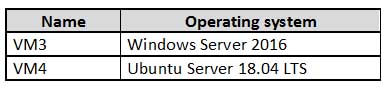
AZ-500 Microsoft Azure Security Technologies Part 08 Q07 255 On which virtual machines is the Microsoft Monitoring Agent installed?
- VM3 only
- VM1 and VM3 only
- VM3 and VM4 only
- VM1, VM2, VM3, and VM4
Explanation:
When automatic provisioning is enabled, Security Center provisions the Microsoft Monitoring Agent on all supported Azure VMs and any new ones that are created.
Supported Operating systems include: Ubuntu 14.04 LTS (x86/x64), 16.04 LTS (x86/x64), and 18.04 LTS (x64) and Windows Server 2008 R2, 2012, 2012 R2, 2016, version 1709 and 1803. -
SIMULATION
You need to email an alert to a user named [email protected] if the average CPU usage of a virtual machine named VM1 is greater than 70 percent for a period of 15 minutes.
To complete this task, sign in to the Azure portal.
- See the explanation below.
Explanation:Create an alert rule on a metric with the Azure portal
1. In the portal, locate the resource, here VM1, you are interested in monitoring and select it.2. Select Alerts (Classic) under the MONITORING section. The text and icon may vary slightly for different resources.
3. Select the Add metric alert (classic) button and fill in the fields as per below, and click OK.
Metric: CPU Percentage
Condition: Greater than
Period: Over last 15 minutes
Notify via: email
Additional administrator email(s): [email protected]
AZ-500 Microsoft Azure Security Technologies Part 08 Q08 256 -
SIMULATION
You need to collect all the audit failure data from the security log of a virtual machine named VM1 to an Azure Storage account.
To complete this task, sign in to the Azure portal.
This task might take several minutes to complete You can perform other tasks while the task completes.
- See the explanation below.
Explanation:Step 1: Create a workspace
Azure Monitor can collect data directly from your Azure virtual machines into a Log Analytics workspace for detailed analysis and correlation.
1. In the Azure portal, select All services. In the list of resources, type Log Analytics. As you begin typing, the list filters based on your input. Select Log Analytics workspaces.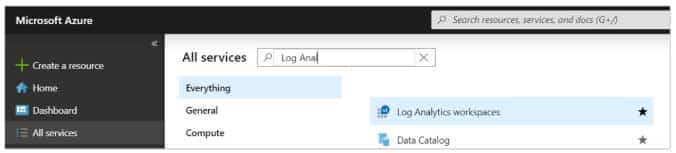
AZ-500 Microsoft Azure Security Technologies Part 08 Q09 257 2. Select Create, and then select choices for the following items:
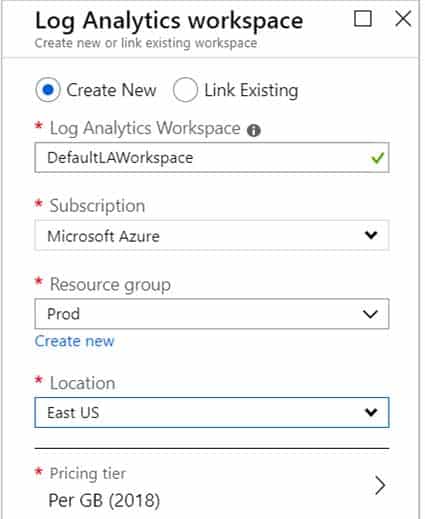
AZ-500 Microsoft Azure Security Technologies Part 08 Q09 258 3. After providing the required information on the Log Analytics workspace pane, select OK.
While the information is verified and the workspace is created, you can track its progress under Notifications from the menu.
Step 2: Enable the Log Analytics VM Extension
Installing the Log Analytics VM extension for Windows and Linux allows Azure Monitor to collect data from your Azure VMs.1. In the Azure portal, select All services found in the upper left-hand corner. In the list of resources, type Log Analytics. As you begin typing, the list filters based on your input. Select Log Analytics workspaces.
2. In your list of Log Analytics workspaces, select DefaultWorkspace (the name you created in step 1).
3. On the left-hand menu, under Workspace Data Sources, select Virtual machines.
4. In the list of Virtual machines, select a virtual machine you want to install the agent on. Notice that the Log Analytics connection status for the VM indicates that it is Not connected.
5. In the details for your virtual machine, select Connect. The agent is automatically installed and configured for your Log Analytics workspace. This process takes a few minutes, during which time the Status shows Connecting.After you install and connect the agent, the Log Analytics connection status will be updated with This workspace.
-
You have 10 virtual machines on a single subnet that has a single network security group (NSG).
You need to log the network traffic to an Azure Storage account.
What should you do?
- Install the Network Performance Monitor solution.
- Create an Azure Log Analytics workspace.
- Enable diagnostic logging for the NSG.
- Enable NSG flow logs.
Explanation:
A network security group (NSG) enables you to filter inbound traffic to, and outbound traffic from, a virtual machine (VM). You can log network traffic that flows through an NSG with Network Watcher’s NSG flow log capability. Steps include:
– Create a VM with a network security group
– Enable Network Watcher and register the Microsoft.Insights provider
– Enable a traffic flow log for an NSG, using Network Watcher’s NSG flow log capability
– Download logged data
– View logged data -
You have an Azure subscription that contains the virtual machines shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 08 Q10 259 From Azure Security Center, you turn on Auto Provisioning.
You deploy the virtual machines shown in the following table.
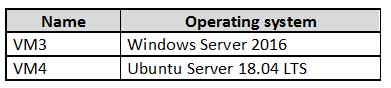
AZ-500 Microsoft Azure Security Technologies Part 08 Q10 260 On which virtual machines is the Log Analytics Agent installed?
- VM3 only
- VM1 and VM3 only
- VM3 and VM4 only
- VM1, VM2, VM3, and VM4
Explanation:When automatic provisioning is On, Security Center provisions the Log Analytics Agent on all supported Azure VMs and any new ones that are created.
Supported Operating systems include: Ubuntu 14.04 LTS (x86/x64), 16.04 LTS (x86/x64), and 18.04 LTS (x64) and Windows Server 2008 R2, 2012, 2012 R2, 2016, version 1709 and 1803
-
HOTSPOT
You plan to use Azure Log Analytics to collect logs from 200 servers that run Windows Server 2016.
You need to automate the deployment of the Microsoft Monitoring Agent to all the servers by using an Azure Resource Manager template.
How should you complete the template? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
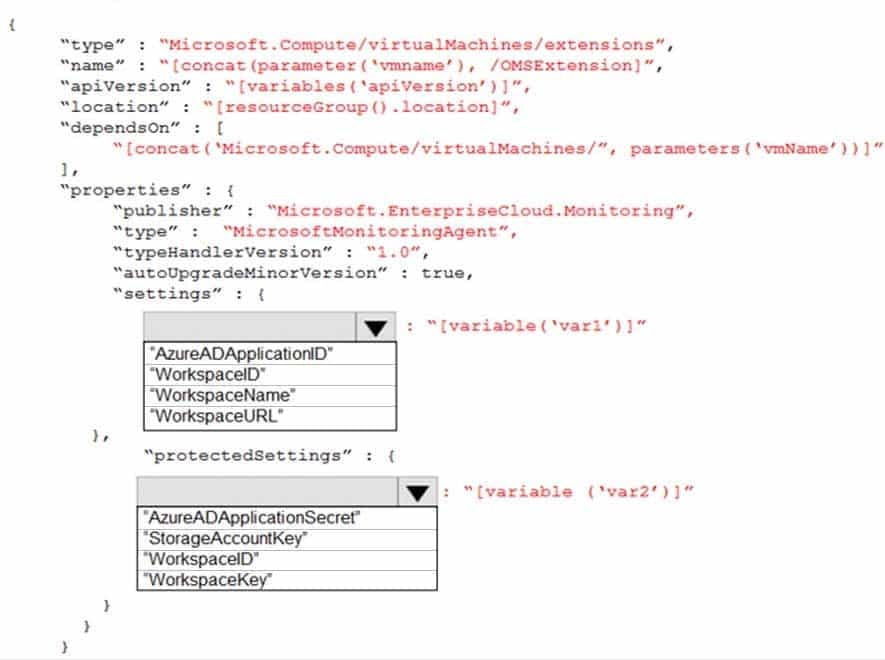
AZ-500 Microsoft Azure Security Technologies Part 08 Q12 261 Question 
AZ-500 Microsoft Azure Security Technologies Part 08 Q12 261 Answer -
HOTSPOT
You have an Azure subscription that contains the alerts shown in the following exhibit.
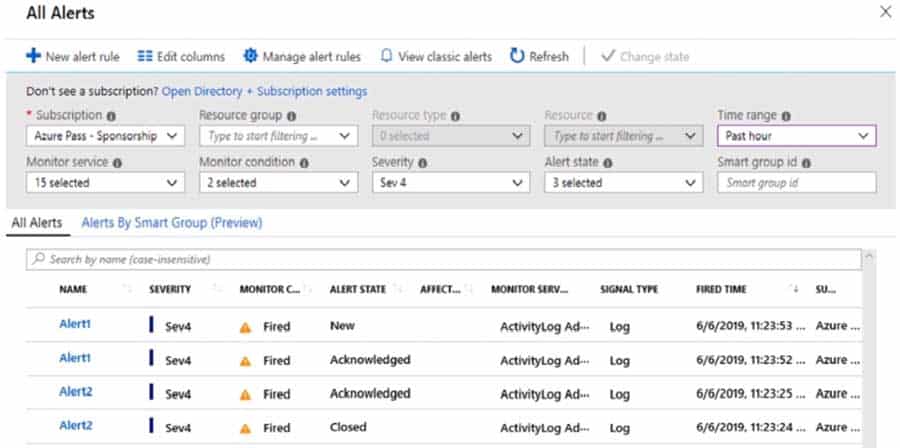
AZ-500 Microsoft Azure Security Technologies Part 08 Q13 262 Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

AZ-500 Microsoft Azure Security Technologies Part 08 Q13 263 Question 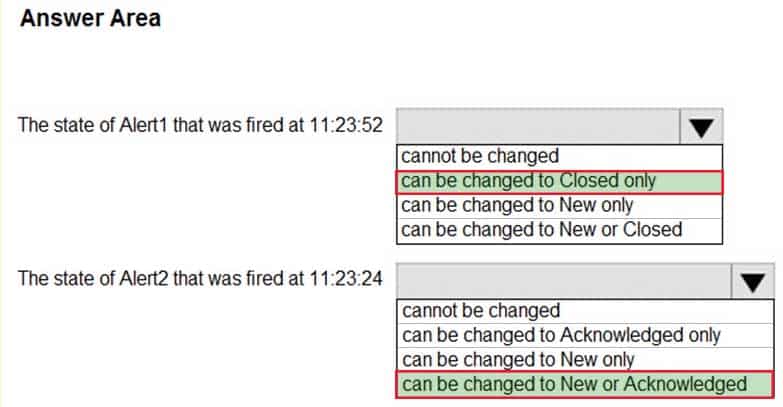
AZ-500 Microsoft Azure Security Technologies Part 08 Q13 263 Answer -
You have an Azure subscription named Sub1 that is associated to an Azure Active Directory (Azure AD) tenant named contoso.com.
You are assigned the Global administrator role for the tenant. You are responsible for managing Azure Security Center settings.
You need to create a custom sensitivity label.
What should you do?
- Create a custom sensitive information type.
- Elevate access for global administrators in Azure AD.
- Upgrade the pricing tier of the Security Center to Standard.
- Enable integration with Microsoft Cloud App Security.
Explanation:
First, you need to create a new sensitive information type because you can’t directly modify the default rules. -
HOTSPOT
You have the hierarchy of Azure resources shown in the following exhibit.
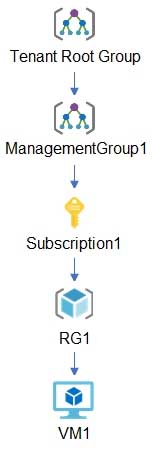
AZ-500 Microsoft Azure Security Technologies Part 08 Q15 264 You create the Azure Blueprints definitions shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 08 Q15 265 To which objects can you assign Blueprint1 and Blueprint2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
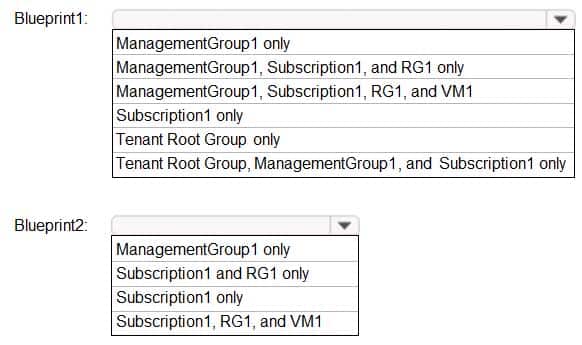
AZ-500 Microsoft Azure Security Technologies Part 08 Q15 266 Question 
AZ-500 Microsoft Azure Security Technologies Part 08 Q15 266 Answer Explanation:Blueprints can only be assigned to subscriptions.
-
You have an Azure subscription that contains the Azure Log Analytics workspaces shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 08 Q16 267 You create the virtual machines shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 08 Q16 268 You plan to use Azure Sentinel to monitor Windows Defender Firewall on the virtual machines.
Which virtual machines you can connect to Azure Sentinel?
- VM1 only
- VM1 and VM3 only
- VM1, VM2, VM3, and VM4
- VM1 and VM2 only
-
HOTSPOT
You have an Azure subscription that contains a user named Admin1 and a resource group named RG1.
In Azure Monitor, you create the alert rules shown in the following table.
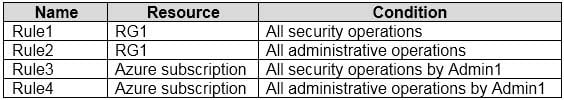
AZ-500 Microsoft Azure Security Technologies Part 08 Q17 269 Admin1 performs the following actions on RG1:
– Adds a virtual network named VNET1
– Adds a Delete lock named Lock1Which rules will trigger an alert as a result of the actions of Admin1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
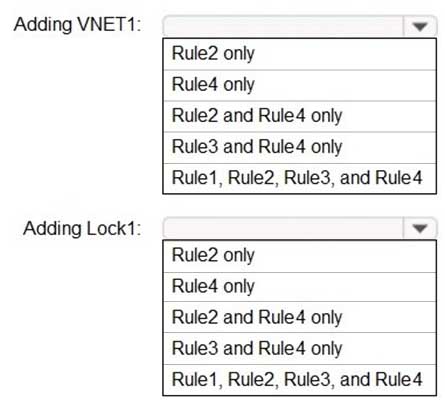
AZ-500 Microsoft Azure Security Technologies Part 08 Q17 270 Question 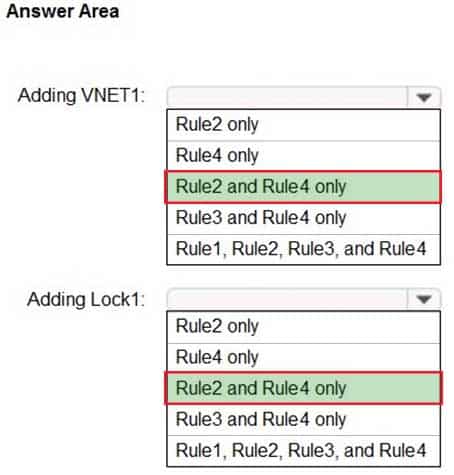
AZ-500 Microsoft Azure Security Technologies Part 08 Q17 270 Answer -
You have an Azure subscription that contains 100 virtual machines and has Azure Defender enabled.
You plan to perform a vulnerability scan of each virtual machine.
You need to deploy the vulnerability scanner extension to the virtual machines by using an Azure Resource Manager template.
Which two values should you specify in the code to automate the deployment of the extension to the virtual machines? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- the user-assigned managed identity
- the workspace ID
- the Azure Active Directory (Azure AD) ID
- the Key Vault managed storage account key
- the system-assigned managed identity
- the primary shared key
-
You have an Azure subscription that contains a user named Admin1 and a virtual machine named VM1. VM1 runs Windows Server 2019 and was deployed by using an Azure Resource Manager template. VM1 is the member of a backend pool of a public Azure Basic Load Balancer.
Admin1 reports that VM1 is listed as Unsupported on the Just in time VM access blade of Azure Security Center.
You need to ensure that Admin1 can enable just in time (JIT) VM access for VM1.
What should you do?
- Create and configure a network security group (NSG).
- Create and configure an additional public IP address for VM1.
- Replace the Basic Load Balancer with an Azure Standard Load Balancer.
- Assign an Azure Active Directory Premium Plan 1 license to Admin1.
-
HOTSPOT
You have an Azure Sentinel workspace that contains an Azure Active Directory (Azure AD) connector, an Azure Log Analytics query named Query1, and a playbook named Playbook1.
Query1 returns a subset of security events generated by Azure AD.
You plan to create an Azure Sentinel analytic rule based on Query1 that will trigger Playbook1.
You need to ensure that you can add Playbook1 to the new rule.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
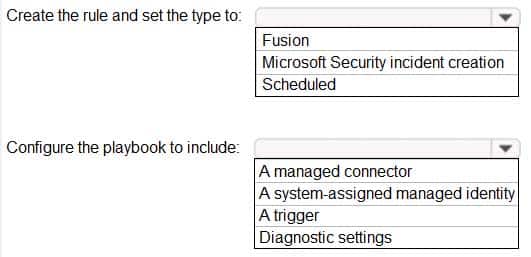
AZ-500 Microsoft Azure Security Technologies Part 08 Q20 271 Question 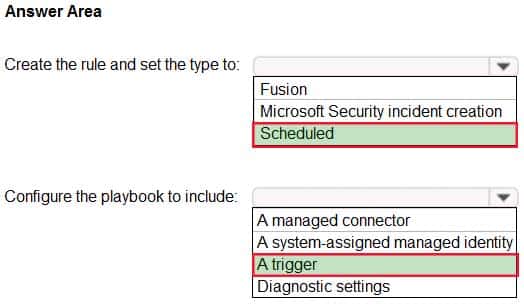
AZ-500 Microsoft Azure Security Technologies Part 08 Q20 271 Answer