AZ-500 : Microsoft Azure Security Technologies : Part 10
-
You have an Azure resource group that contains 100 virtual machines.
You have an initiative named Initiative1 that contains multiple policy definitions. Initiative1 is assigned to the resource group.
You need to identify which resources do NOT match the policy definitions.
What should you do?
- From Azure Security Center, view the Regulatory compliance assessment.
- From the Policy blade of the Azure Active Directory admin center, select Compliance.
- From Azure Security Center, view the Secure Score.
- From the Policy blade of the Azure Active Directory admin center, select Assignments.
-
You have an Azure subscription named Subscription1.
You need to view which security settings are assigned to Subscription1 by default.
Which Azure policy or initiative definition should you review?
- the Audit diagnostic setting policy definition
- the Enable Monitoring in Azure Security Center initiative definition
- the Enable Azure Monitor for VMs initiative definition
- the Azure Monitor solution ‘Security and Audit’ must be deployed policy definition
-
DRAG DROP
You have an Azure Sentinel workspace that has an Azure Active Directory (Azure AD) data connector.
You are threat hunting suspicious traffic from a specific IP address.
You need to annotate an intermediate event stored in the workspace and be able to reference the IP address when navigating through the investigation graph.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
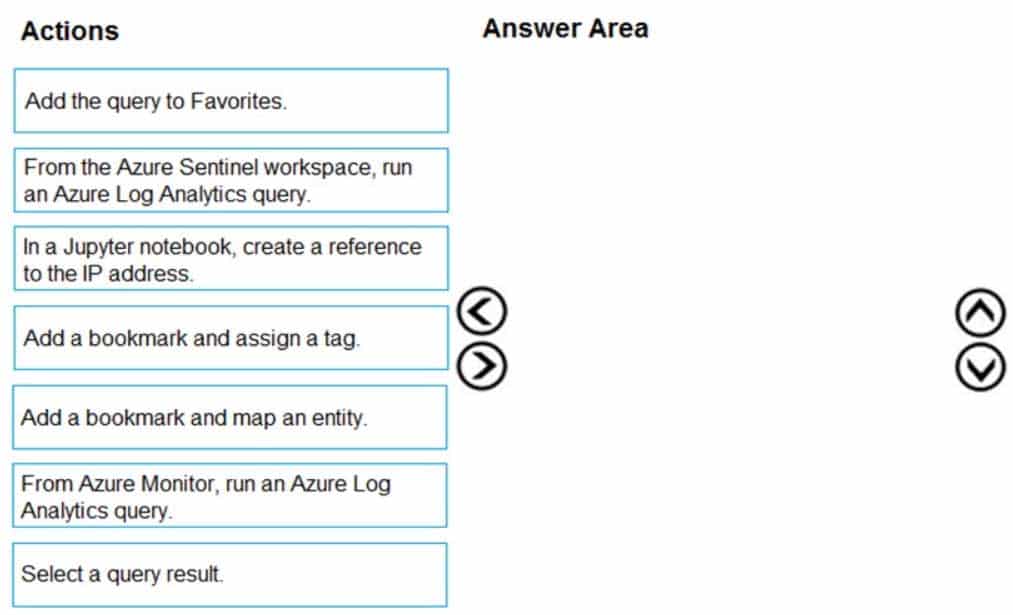
AZ-500 Microsoft Azure Security Technologies Part 10 Q03 284 Question 
AZ-500 Microsoft Azure Security Technologies Part 10 Q03 284 Answer -
HOTSPOT
You have 20 Azure subscriptions and a security group named Group1. The subscriptions are children of the root management group.
Each subscription contains a resource group named RG1.
You need to ensure that for each subscription RG1 meets the following requirements:
– The members of Group1 are assigned the Owner role.
– The modification of permissions to RG1 is prevented.What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
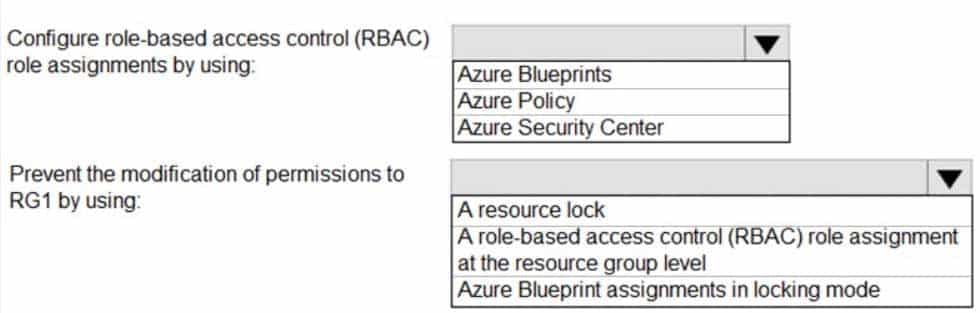
AZ-500 Microsoft Azure Security Technologies Part 10 Q04 285 Question 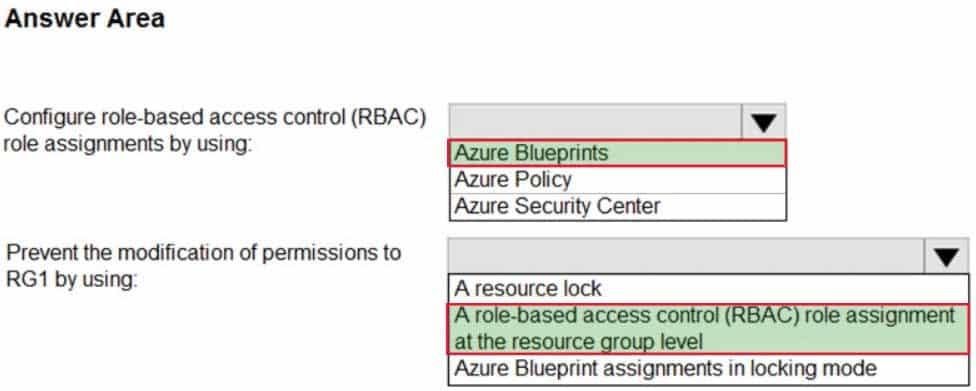
AZ-500 Microsoft Azure Security Technologies Part 10 Q04 285 Answer -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You use Azure Security Center for the centralized policy management of three Azure subscriptions.
You use several policy definitions to manage the security of the subscriptions.
You need to deploy the policy definitions as a group to all three subscriptions.
Solution: You create a policy initiative and an assignment that is scoped to the Tenant Root Group management group.
Does this meet the goal?
- Yes
- No
-
You have an Azure environment.
You need to identify any Azure configurations and workloads that are non-compliant with ISO 27001 standards.
What should you use?
- Azure Sentinel
- Azure Active Directory (Azure AD) Identity Protection
- Azure Security Center
- Microsoft Defender for Identity
-
DRAG DROP
You have an Azure subscription that contains 100 virtual machines. Azure Diagnostics is enabled on all the virtual machines.
You are planning the monitoring of Azure services in the subscription.
You need to retrieve the following details:
– Identify the user who deleted a virtual machine three weeks ago.
– Query the security events of a virtual machine that runs Windows Server 2016.What should you use in Azure Monitor? To answer, drag the appropriate configuration settings to the correct details. Each configuration setting may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

AZ-500 Microsoft Azure Security Technologies Part 10 Q07 286 Question 
AZ-500 Microsoft Azure Security Technologies Part 10 Q07 286 Answer -
HOTSPOT
You have an Azure subscription that contains the resources shown in the following table.
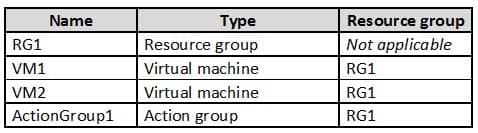
AZ-500 Microsoft Azure Security Technologies Part 10 Q08 287 VM1 and VM2 are stopped.
You create an alert rule that has the following settings:
– Resource: RG1
– Condition: All Administrative operations
– Actions: Action groups configured for this alert rule: ActionGroup1
– Alert rule name: Alert1You create an action rule that has the following settings:
– Scope: VM1
– Filter criteria: Resource Type = “Virtual Machines”
– Define on this scope: Suppression
– Suppression config: From now (always)
– Name: ActionRule1For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Note: Each correct selection is worth one point.

AZ-500 Microsoft Azure Security Technologies Part 10 Q08 288 Question 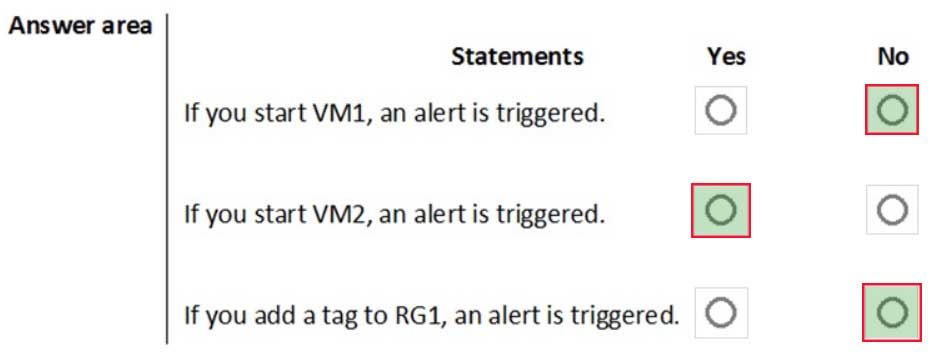
AZ-500 Microsoft Azure Security Technologies Part 10 Q08 288 Answer -
DRAG DROP
You have an Azure subscription named Sub1 that contains an Azure Log Analytics workspace named LAW1.
You have 500 Azure virtual machines that run Windows Server 2016 and are enrolled in LAW1.
You plan to add the System Update Assessment solution to LAW1.
You need to ensure that System Update Assessment-related logs are uploaded to LAW1 from 100 of the virtual machines only.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
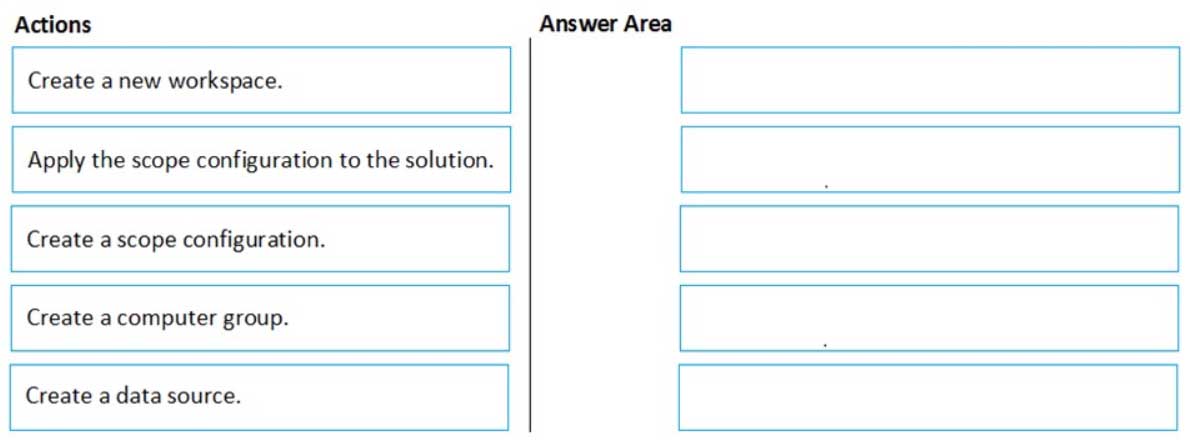
AZ-500 Microsoft Azure Security Technologies Part 10 Q09 289 Question 
AZ-500 Microsoft Azure Security Technologies Part 10 Q09 289 Answer -
You have an Azure subscription named Sub1 that contains the virtual machines shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 10 Q10 290 You need to ensure that the virtual machines in RG1 have the Remote Desktop port closed until an authorized user requests access.
What should you configure?
- Azure Active Directory (Azure AD) Privileged Identity Management (PIM)
- an application security group
- Azure Active Directory (Azure AD) conditional access
- just in time (JIT) VM access
Explanation:Just-in-time (JIT) virtual machine (VM) access can be used to lock down inbound traffic to your Azure VMs, reducing exposure to attacks while providing easy access to connect to VMs when needed.
Note: When just-in-time is enabled, Security Center locks down inbound traffic to your Azure VMs by creating an NSG rule. You select the ports on the VM to which inbound traffic will be locked down. These ports are controlled by the just-in-time solution.
When a user requests access to a VM, Security Center checks that the user has Role-Based Access Control (RBAC) permissions that permit them to successfully request access to a VM. If the request is approved, Security Center automatically configures the Network Security Groups (NSGs) and Azure Firewall to allow inbound traffic to the selected ports and requested source IP addresses or ranges, for the amount of time that was specified. After the time has expired, Security Center restores the NSGs to their previous states. Those connections that are already established are not being interrupted, however.
-
SIMULATION
You need to ensure that web11597200 is protected from malware by using Microsoft Antimalware for Virtual Machines and is scanned every Friday at 01:00.
To complete this task, sign in to the Azure portal.
- See the explanation below.
Explanation:You need to install and configure the Microsoft Antimalware extension on the virtual machine named web11597200.
1. In the Azure portal, type Virtual Machines in the search box, select Virtual Machines from the search results then select web11597200. Alternatively, browse to Virtual Machines in the left navigation pane.
2. In the properties of web11597200, click on Extensions.
3. Click the Add button to add an Extension.
4. Scroll down the list of extensions and select Microsoft Antimalware.
5. Click the Create button. This will open the settings pane for the Microsoft Antimalware Extension.
6. In the Scan day field, select Friday.
7. In the Scan time field, enter 60. The scan time is measured in minutes after midnight so 60 would be 01:00, 120 would be 02:00 etc.
8. Click the OK button to save the configuration and install the extension. -
SIMULATION
You need to ensure that the events in the NetworkSecurityGroupRuleCounter log of the VNET01-Subnet0-NSG network security group (NSG) are stored in the logs11597200 Azure Storage account for 30 days.
To complete this task, sign in to the Azure portal.
- See the explanation below.
Explanation:You need to configure the diagnostic logging for the NetworkSecurityGroupRuleCounter log.
1. In the Azure portal, type Network Security Groups in the search box, select Network Security Groups from the search results then select VNET01-Subnet0-NSG. Alternatively, browse to Network Security Groups in the left navigation pane.
2. In the properties of the Network Security Group, click on Diagnostic Settings.
3. Click on the Add diagnostic setting link.
4. Provide a name in the Diagnostic settings name field. It doesn’t matter what name you provide for the exam.
5. In the Log section, select NetworkSecurityGroupRuleCounter.
6. In the Destination details section, select Archive to a storage account.
7. In the Storage account field, select the logs11597200 storage account.
8. In the Retention (days) field, enter 30.
9. Click the Save button to save the changes. -
HOTSPOT
On Monday, you configure an email notification in Azure Security Center to email notifications to [email protected] about alerts that have a severity level of Low, Medium, or High.
On Tuesday, Security Center generates the security alerts shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 10 Q13 291 How many email notifications will [email protected] receive on Tuesday? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-500 Microsoft Azure Security Technologies Part 10 Q13 292 Question 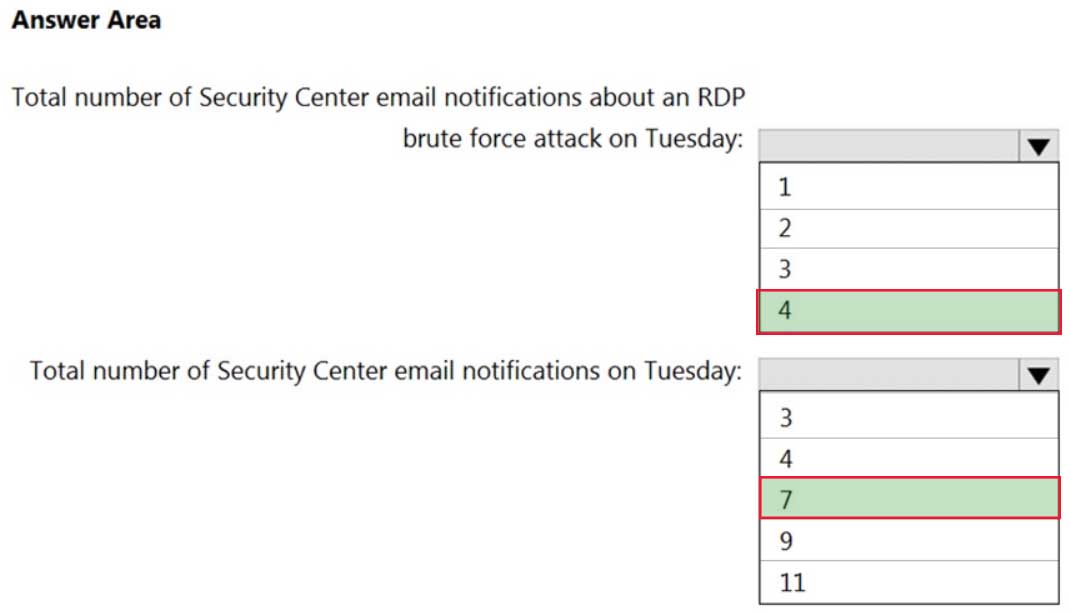
AZ-500 Microsoft Azure Security Technologies Part 10 Q13 292 Answer -
You are troubleshooting a security issue for an Azure Storage account.
You enable the diagnostic logs for the storage account.
What should you use to retrieve the diagnostics logs?
- Azure Security Center
- Azure Monitor
- the Security admin center
- Azure Storage Explorer
-
You have an Azure subscription that contains the resources shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 10 Q15 293 You plan to enable Azure Defender for the subscription.
Which resources can be protected by using Azure Defender?
- VM1, VNET1, storage1, and Vault1
- VM1, VNET1, and storage1 only
- VM1, storage1, and Vault1 only
- VM1 and VNET1 only
- VM1 and storage1 only
-
DRAG DROP
You have an Azure subscription that contains the following resources:
A network virtual appliance (NVA) that runs non-Microsoft firewall software and routes all outbound traffic from the virtual machines to the internet
An Azure function that contains a script to manage the firewall rules of the NVA
Azure Security Center standard tier enabled for all virtual machines
An Azure Sentinel workspace
30 virtual machinesYou need to ensure that when a high-priority alert is generated in Security Center for a virtual machine, an incident is created in Azure Sentinel and then a script is initiated to configure a firewall rule for the NVA.
How should you configure Azure Sentinel to meet the requirements? To answer, drag the appropriate components to the correct requirements. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
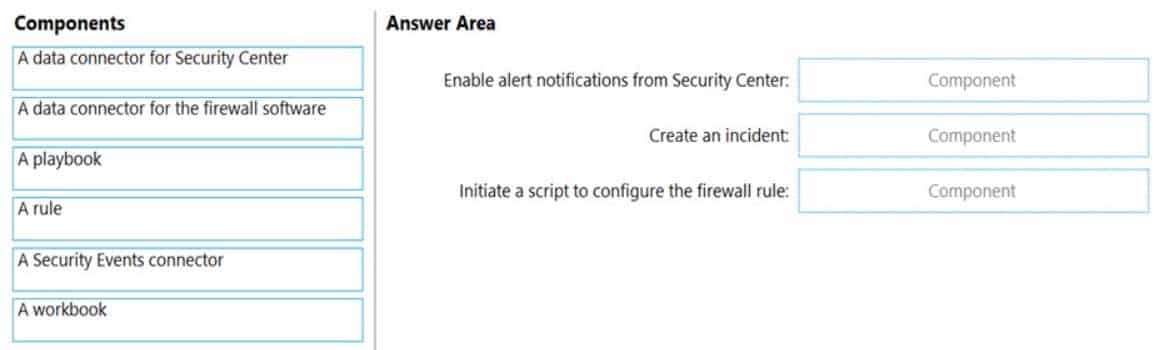
AZ-500 Microsoft Azure Security Technologies Part 10 Q16 294 Question 
AZ-500 Microsoft Azure Security Technologies Part 10 Q16 294 Answer -
You have an Azure subscription that contains a resource group named RG1 and a security group named ServerAdmins. RG1 contains 10 virtual machines, a virtual network named VNET1, and a network security group (NSG) named NSG1. ServerAdmins can access the virtual machines by using RDP.
You need to ensure that NSG1 only allows RDP connections to the virtual machines for a maximum of 60 minutes when a member of ServerAdmins requests access.
What should you configure?
- an Azure policy assigned to RG1
- a just in time (JIT) VM access policy in Azure Security Center
- an Azure Active Directory (Azure AD) Privileged Identity Management (PIM) role assignment
- an Azure Bastion host on VNET1
-
HOTSPOT
You have an Azure subscription named Subscription1 that contains the resources shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 10 Q18 295 You have an Azure subscription named Subscription2 that contains the following resources:
– An Azure Sentinel workspace
– An Azure Event Grid instanceYou need to ingest the CEF messages from the NVAs to Azure Sentinel.
What should you configure for each subscription? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
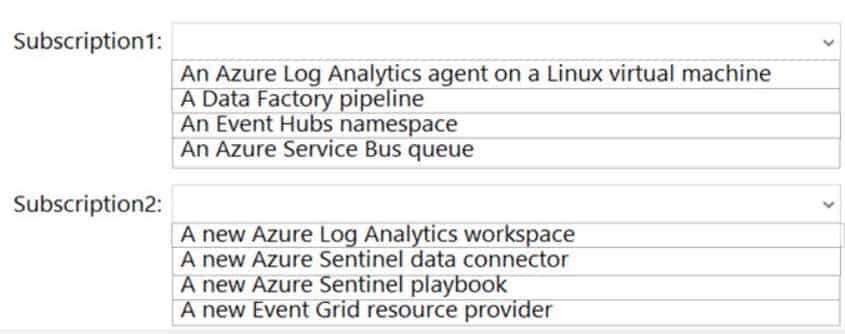
AZ-500 Microsoft Azure Security Technologies Part 10 Q18 296 Question 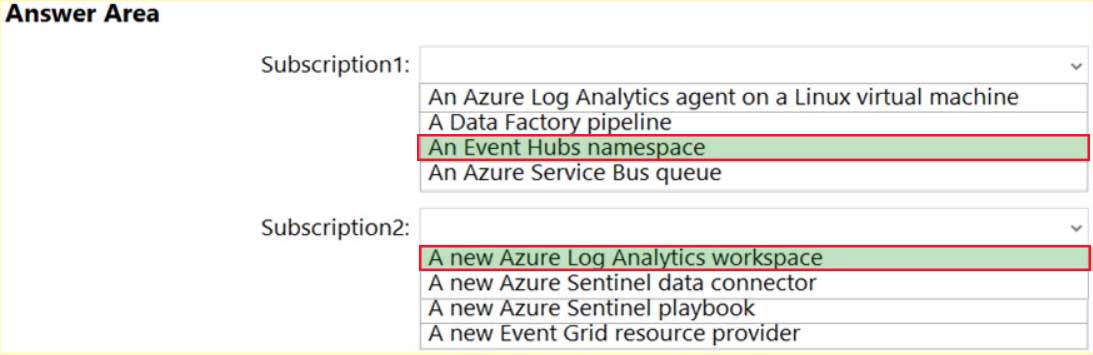
AZ-500 Microsoft Azure Security Technologies Part 10 Q18 296 Answer -
HOTSPOT
You have an Azure subscription named Subscription1 that contains a resource group named RG1 and a user named User1. User1 is assigned the Owner role for RG1.
You create an Azure Blueprints definition named Blueprint1 that includes a resource group named RG2 as shown in the following exhibit.
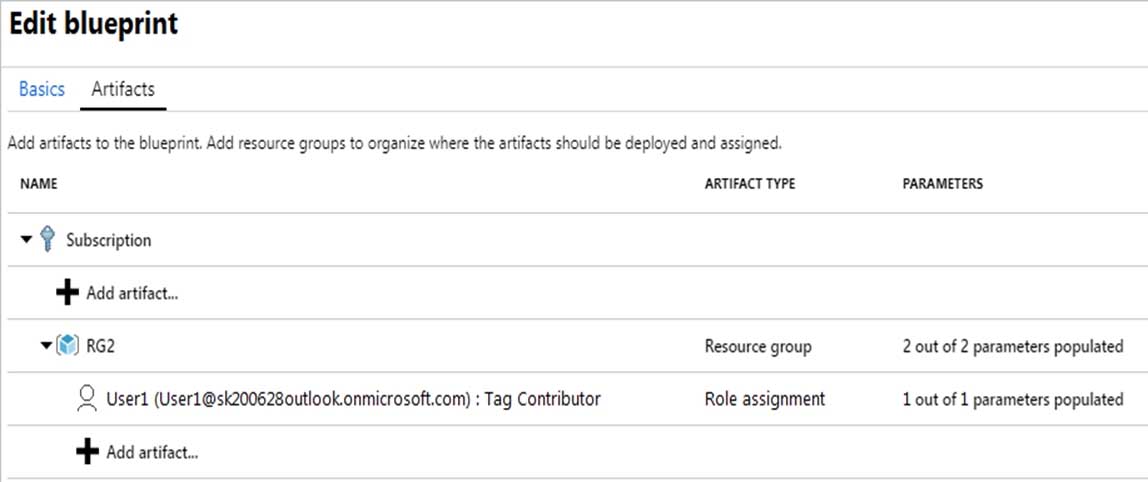
AZ-500 Microsoft Azure Security Technologies Part 10 Q19 297 You assign Blueprint1 to Subscription1 by using the following settings:
Lock assignment: Read Only
Managed Identity: System assignedFor each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

AZ-500 Microsoft Azure Security Technologies Part 10 Q19 298 Question 
AZ-500 Microsoft Azure Security Technologies Part 10 Q19 298 Answer -
You have an Azure Sentinel deployment.
You need to create a scheduled query rule named Rule1.
What should you use to define the query rule logic for Rule1?
- a Transact-SQL statement
- a JSON definition
- GraphQL
- a Kusto query