AZ-500 : Microsoft Azure Security Technologies : Part 11
-
You have an Azure subscription named Subscription1 that contains a resource group named RG1 and the users shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 11 Q01 299 You perform the following tasks:
– Assign User1 the Network Contributor role for Subscription1.
– Assign User2 the Contributor role for RG1.To Subscription1 and RG1, you assign the following policy definition: External accounts with write permissions should be removed from your subscription.
What is the Compliance State of the policy assignments?
- The Compliance State of both policy assignments is Non-compliant.
- The Compliance State of the policy assignment to Subscription1 is Compliant, and the Compliance State of the policy assignment to RG1 is Non-compliant.
- The Compliance State of the policy assignment to Subscription1 is Non-compliant, and the Compliance State of the policy assignment to RG1 is Compliant.
- The Compliance State of both policy assignments is Compliant.
-
HOTSPOT
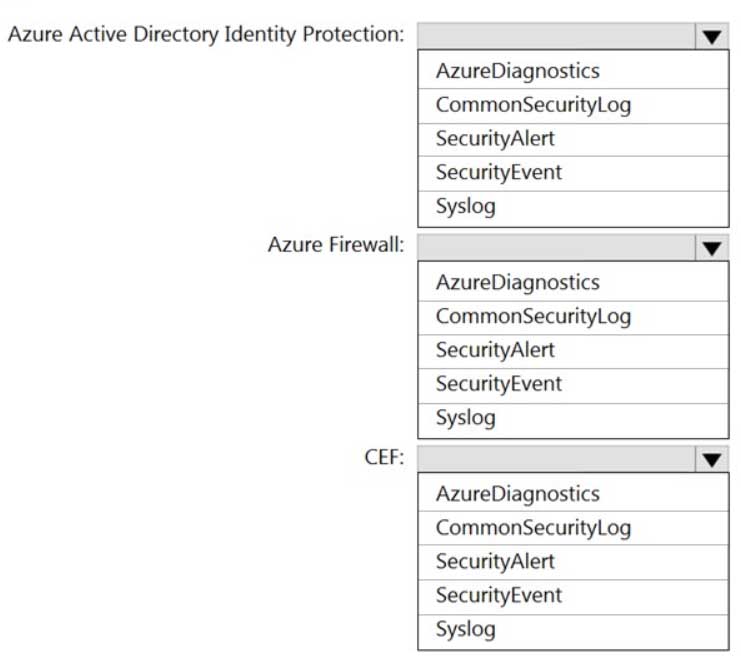
You have an Azure Sentinel workspace that has the following data connectors:
– Azure Active Directory Identity Protection
– Common Event Format (CEF)
– Azure FirewallYou need to ensure that data is being ingested from each connector.
From the Logs query window, which table should you query for each connector? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
AZ-500 Microsoft Azure Security Technologies Part 11 Q02 300 Question 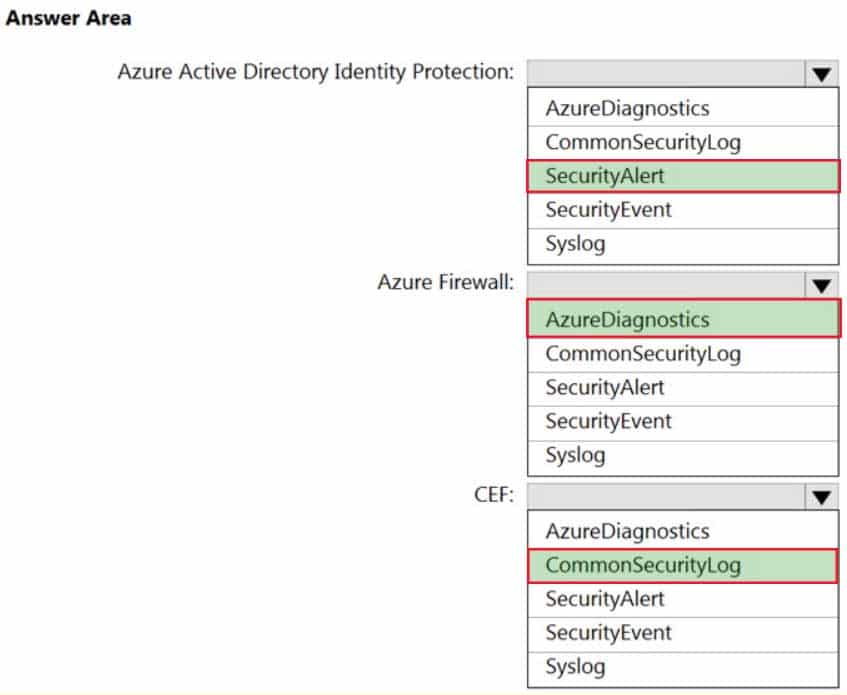
AZ-500 Microsoft Azure Security Technologies Part 11 Q02 300 Answer -
Case Study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.Overview
Litware, Inc. is a digital media company that has 500 employees in the Chicago area and 20 employees in the San Francisco area.
Existing Environment
Litware has an Azure subscription named Sub1 that has a subscription ID of 43894a43-17c2-4a39-8cfc-3540c2653ef4.
Sub1 is associated to an Azure Active Directory (Azure AD) tenant named litwareinc.com. The tenant contains the user objects and the device objects of all the Litware employees and their devices. Each user is assigned an Azure AD Premium P2 license. Azure AD Privileged Identity Management (PIM) is activated.
The tenant contains the groups shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 11 Q03 301 The Azure subscription contains the objects shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 11 Q03 302 Azure Security Center is set to the Standard tier.
Requirements
Planned Changes
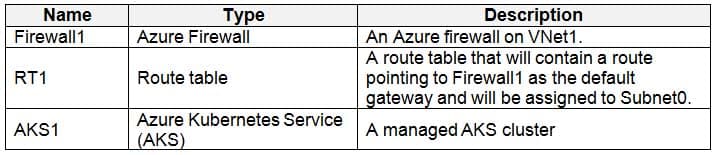
Litware plans to deploy the Azure resources shown in the following table.
AZ-500 Microsoft Azure Security Technologies Part 11 Q03 303 Identity and Access Requirements
Litware identifies the following identity and access requirements:
– All San Francisco users and their devices must be members of Group1.
– The members of Group2 must be assigned the Contributor role to RG2 by using a permanent eligible assignment.
– Users must be prevented from registering applications in Azure AD and from consenting to applications that access company information on the users’ behalf.Platform Protection Requirements
Litware identifies the following platform protection requirements:
– Microsoft Antimalware must be installed on the virtual machines in RG1.
– The members of Group2 must be assigned the Azure Kubernetes Service Cluster Admin Role.
– Azure AD users must be able to authenticate to AKS1 by using their Azure AD credentials.
– Following the implementation of the planned changes, the IT team must be able to connect to VM0 by using JIT VM access.
– A new custom RBAC role named Role1 must be used to delegate the administration of the managed disks in RG1. Role1 must be available only for RG1.Security Operations Requirements
Litware must be able to customize the operating system security configurations in Azure Security Center.
Data and Application Requirements
Litware identifies the following data and applications requirements:
– The users in Group2 must be able to authenticate to SQLDB1 by using their Azure AD credentials.
– WebApp1 must enforce mutual authentication.General Requirements
Litware identifies the following general requirements:
– Whenever possible, administrative effort must be minimized.
– Whenever possible, use of automation must be maximized.-
You need to configure WebApp1 to meet the data and application requirements.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Upload a public certificate.
- Turn on the HTTPS Only protocol setting.
- Set the Minimum TLS Version protocol setting to 1.2.
- Change the pricing tier of the App Service plan.
- Turn on the Incoming client certificates protocol setting.
Explanation:A: To configure Certificates for use in Azure Websites Applications you need to upload a public Certificate.
C: Over time, multiple versions of TLS have been released to mitigate different vulnerabilities. TLS 1.2 is the most current version available for apps running on Azure App Service.
Incorrect Answers:
B: We need support the http url as well.Note:
AZ-500 Microsoft Azure Security Technologies Part 11 Q03 304 -
HOTSPOT
You need to create Role1 to meet the platform protection requirements.
How should you complete the role definition of Role1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-500 Microsoft Azure Security Technologies Part 11 Q03 305 Question 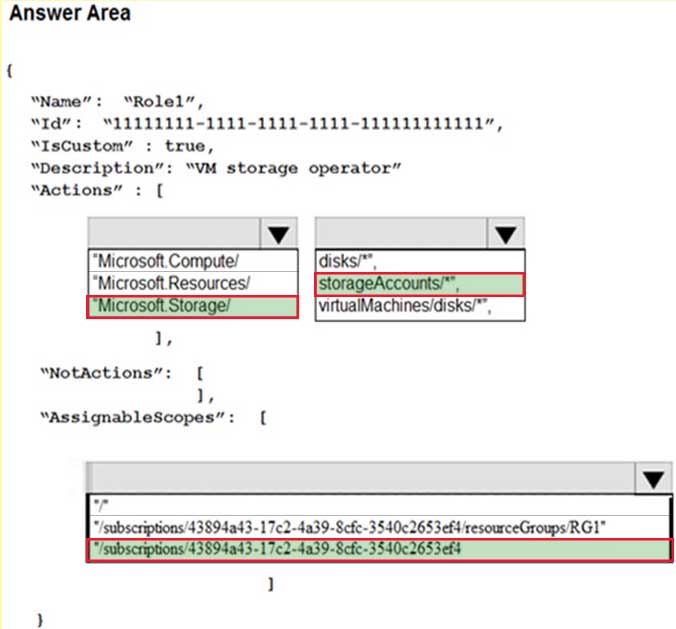
AZ-500 Microsoft Azure Security Technologies Part 11 Q03 305 Answer Explanation:Scenario: A new custom RBAC role named Role1 must be used to delegate the administration of the managed disks in RG1. Role1 must be available only for RG1.
Azure RBAC template managed disks “Microsoft.Storage/”
-
DRAG DROP
You need to configure SQLDB1 to meet the data and application requirements.
Which three actions should you recommend be performed in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

AZ-500 Microsoft Azure Security Technologies Part 11 Q03 306 Question 
AZ-500 Microsoft Azure Security Technologies Part 11 Q03 306 Answer
-
-
SIMULATION
You need to configure a weekly backup of an Azure SQL database named Homepage. The backup must be retained for eight weeks.
To complete this task, sign in to the Azure portal.
- See the explanation below.
Explanation:You need to configure the backup policy for the Azure SQL database.
1. In the Azure portal, type Azure SQL Database in the search box, select Azure SQL Database from the search results then select Homepage. Alternatively, browse to Azure SQL Database in the left navigation pane.
2. Select the server hosting the Homepage database and click on Manage backups.
3. Click on Configure policies.
4. Ensure that the Weekly Backups option is ticked.
5. Configure the How long would you like weekly backups to be retained option to 8 weeks.
6. Click Apply to save the changes. -
SIMULATION
You need to ensure that when administrators deploy resources by using an Azure Resource Manager template, the deployment can access secrets in an Azure key vault named KV11597200.
To complete this task, sign in to the Azure portal.
- See the explanation below.
Explanation:You need to configure an option in the Advanced Access Policy of the key vault.
1. In the Azure portal, type Azure Key Vault in the search box, select Azure Key Vault from the search results then select the key vault named KV11597200. Alternatively, browse to Azure Key Vault in the left navigation pane.
2. In the properties of the key vault, click on Advanced Access Policies.
3. Tick the checkbox labelled Enable access to Azure Resource Manager for template deployment.
4. Click Save to save the changes. -
HOTSPOT
You have an Azure subscription that contains the storage accounts shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 11 Q06 307 You enable Azure Defender for Storage.
Which storage services of storage5 are monitored by Azure Defender for Storage, and which storage accounts are protected by Azure Defender for Storage? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
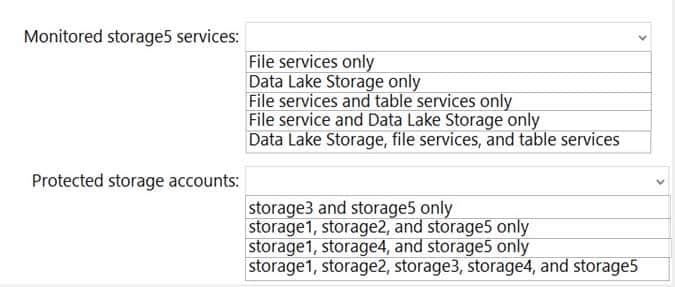
AZ-500 Microsoft Azure Security Technologies Part 11 Q06 308 Question 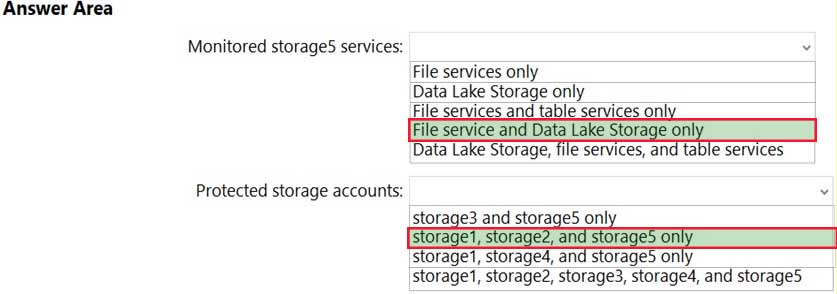
AZ-500 Microsoft Azure Security Technologies Part 11 Q06 308 Answer -
You have an Azure subscription that contains as Azure key vault and an Azure Storage account. The key vault contains customer-managed keys. The storage account is configured to use the customer-managed keys stored in the key vault.
You plan to store data in Azure by using the following services:
– Azure Files
– Azure Blob storage
– Azure Table storage
– Azure Queue storageWhich two services support data encryption by using the keys stored in the key vault? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- Table storage
- Azure Files
- Blob storage
- Queue storage
-
SIMULATION
You need to ensure that connections through an Azure Application Gateway named Homepage-AGW are inspected for malicious requests.
To complete this task, sign in to the Azure portal.
You do not need to wait for the task to complete.
- See the explanation below.
Explanation:You need to enable the Web Application Firewall on the Application Gateway.
1. In the Azure portal, type Application gateways in the search box, select Application gateways from the search results then select the gateway named Homepage-AGW. Alternatively, browse to Application Gateways in the left navigation pane.
2. In the properties of the application gateway, click on Web application firewall.
3. For the Tier setting, select WAF V2.
4. In the Firewall status section, click the slider to switch to Enabled.
5. In the Firewall mode section, click the slider to switch to Prevention.
6. Click Save to save the changes. -
SIMULATION
You need to create a web app named Intranet11597200 and enable users to authenticate to the web app by using Azure Active Directory (Azure AD).
To complete this task, sign in to the Azure portal.
- See the explanation below.
Explanation:1. In the Azure portal, type App services in the search box and select App services from the search results.
2. Click the Create app service button to create a new app service.
3. In the Resource Group section, click the Create new link to create a new resource group.
4. Give the resource group a name such as Intranet11597200RG and click OK.
5. In the Instance Details section, enter Intranet11597200 in the Name field.
6. In the Runtime stack field, select any runtime stack such as .NET Core 3.1.
7. Click the Review + create button.
8. Click the Create button to create the web app.
9. Click the Go to resource button to open the properties of the new web app.
10. In the Settings section, click on Authentication / Authorization.
11. Click the App Service Authentication slider to set it to On.
12. In the Action to take when request is not authentication box, select Log in with Azure Active Directory.
13. Click Save to save the changes. -
HOTSPOT
You have an Azure subscription that contains an Azure key vault named KeyVault1 and the virtual machines shown in the following table.
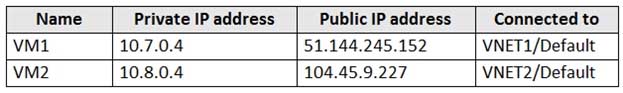
AZ-500 Microsoft Azure Security Technologies Part 11 Q10 309 You set the Key Vault access policy to Enable access to Azure Disk Encryption for volume encryption.
KeyVault1 is configured as shown in the following exhibit.

AZ-500 Microsoft Azure Security Technologies Part 11 Q10 309 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
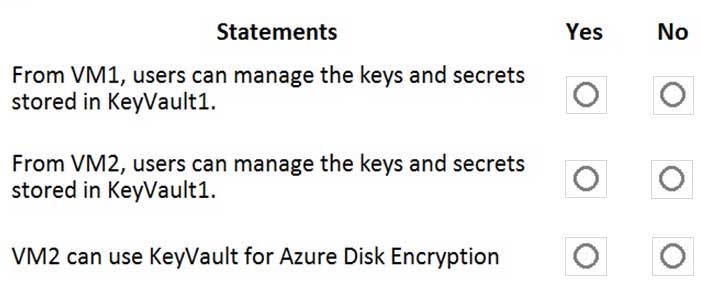
AZ-500 Microsoft Azure Security Technologies Part 11 Q10 311 Question 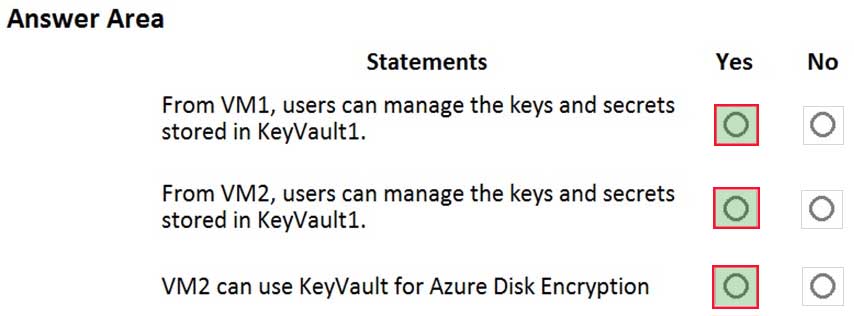
AZ-500 Microsoft Azure Security Technologies Part 11 Q10 311 Answer -
DRAG DROP
You have an Azure Storage account named storage1 and an Azure virtual machine named VM1. VM1 has a premium SSD managed disk.
You need to enable Azure Disk Encryption for VM1.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange then in the correct order.
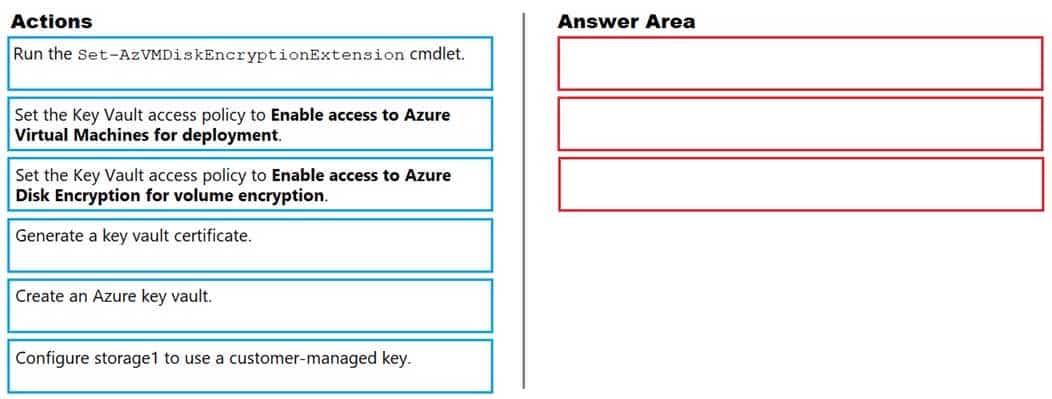
AZ-500 Microsoft Azure Security Technologies Part 11 Q11 312 Question 
AZ-500 Microsoft Azure Security Technologies Part 11 Q11 312 Answer -
SIMULATION
You need to enable Advanced Data Security for the SQLdb1 Azure SQL database. The solution must ensure that Azure Advanced Threat Protection (ATP) alerts are sent to [email protected].
To complete this task, sign in to the Azure portal and modify the Azure resources.
- See the explanation below.
Explanation:1. In the Azure portal, type SQL in the search box, select SQL databases from the search results then select SQLdb1. Alternatively, browse to SQL databases in the left navigation pane.
2. In the properties of SQLdb1, scroll down to the Security section and select Advanced data security.
3. Click on the Settings icon.
4. Tick the Enable Advanced Data Security at the database level checkbox.
5. Click Yes at the confirmation prompt.
6. In the Storage account select a storage account if one isn’t selected by default.
7. Under Advanced Threat Protection Settings, enter [email protected] in the Send alerts to box.
8. Click the Save button to save the changes. -
SIMULATION
You plan to use Azure Disk Encryption for several virtual machine disks.
You need to ensure that Azure Disk Encryption can retrieve secrets from the KeyVault11641655 Azure key vault.
To complete this task, sign in to the Azure portal and modify the Azure resources.
- See the explanation below.
Explanation:1. In the Azure portal, type Key Vaults in the search box, select Key Vaults from the search results then select KeyVault11641655. Alternatively, browse to Key Vaults in the left navigation pane.
2. In the Key Vault properties, scroll down to the Settings section and select Access Policies.
3. Select the Azure Disk Encryption for volume encryption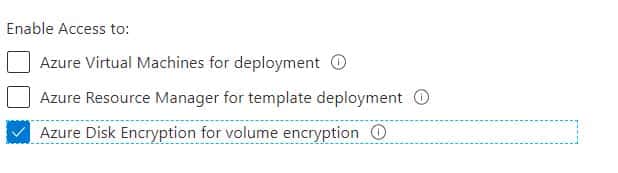
AZ-500 Microsoft Azure Security Technologies Part 11 Q13 313 4. Click Save to save the changes.
-
HOTSPOT
You have an Azure subscription that contains a web app named App1 and an Azure key vault named Vault1.
You need to configure App1 to store and access the secrets in Vault1.
How should you configure App1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-500 Microsoft Azure Security Technologies Part 11 Q14 314 Question 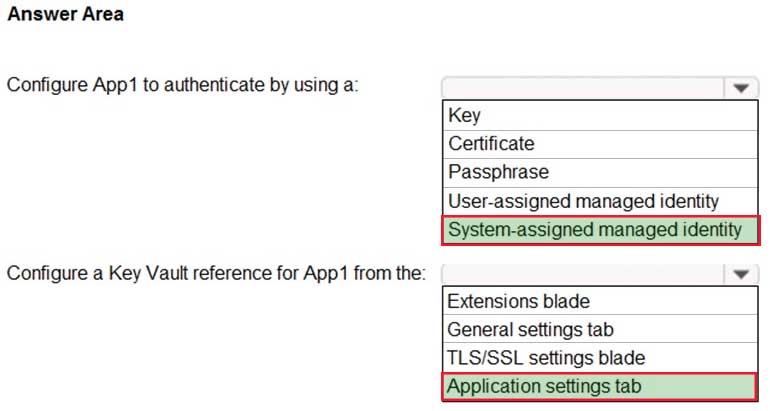
AZ-500 Microsoft Azure Security Technologies Part 11 Q14 314 Answer -
HOTSPOT
You have an Azure key vault named KeyVault1 that contains the items shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 11 Q15 315 In KeyVault1, the following events occur in sequence:
– Item1 is deleted.
– Item2 and Policy1 are deleted.For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
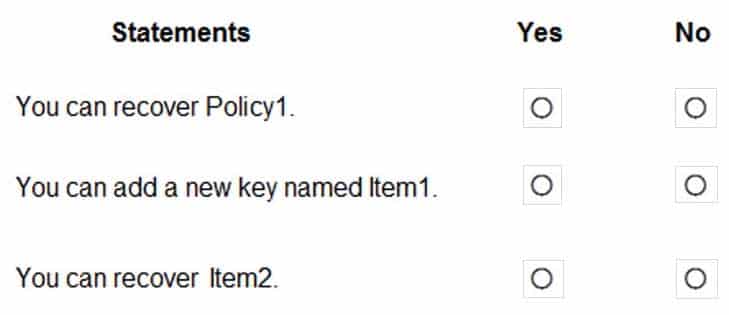
AZ-500 Microsoft Azure Security Technologies Part 11 Q15 316 Question 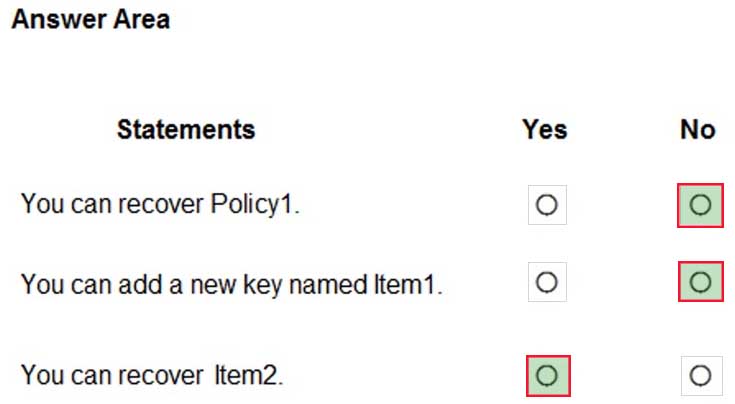
AZ-500 Microsoft Azure Security Technologies Part 11 Q15 316 Answer Explanation:Box1: No
Policies cannot be recovered.Box2: Soft delete is enabled by default on all key vaults. You cannot add a new key named Item1 because an object named Item1 exists in a soft-deleted state.
Box3: Soft delete is now enabled by default on all key vaults so you can recover Item2.
-
You have an Azure SQL Database server named SQL1.
For SQL1, you turn on Azure Defender for SQL to detect all threat detection types.
Which action will Azure Defender for SQL detect as a threat?
- A user updates more than 50 percent of the records in a table.
- A user attempts to sign in as SELECT * FROM table1.
- A user is added to the db_owner database role.
- A user deletes more than 100 records from the same table.
Explanation:
Advanced Threat Protection can detect potential SQL injections: This alert is triggered when an active exploit happens against an identified application vulnerability to SQL injection. This means the attacker is trying to inject malicious SQL statements using the vulnerable application code or stored procedures. -
HOTSPOT
You have the Azure Information Protection labels as shown in the following table.
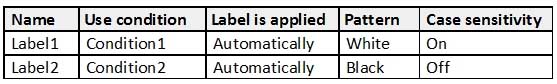
AZ-500 Microsoft Azure Security Technologies Part 11 Q17 317 You have the Azure Information Protection policies as shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 11 Q17 318 You need to identify how Azure Information Protection will label files.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
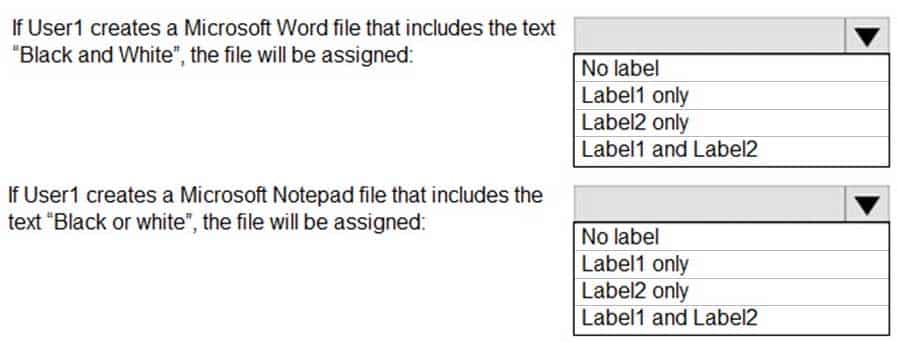
AZ-500 Microsoft Azure Security Technologies Part 11 Q17 319 Question 
AZ-500 Microsoft Azure Security Technologies Part 11 Q17 319 Answer -
Your company uses Azure DevOps.
You need to recommend a method to validate whether the code meets the company’s quality standards and code review standards.
What should you recommend implementing in Azure DevOps?
- branch folders
- branch permissions
- branch policies
- branch locking
Explanation:
Branch policies help teams protect their important branches of development. Policies enforce your team’s code quality and change management standards. -
SIMULATION
You need to ensure that User2-11641655 has all the key permissions for KeyVault11641655.
To complete this task, sign in to the Azure portal and modify the Azure resources.
- See the explanation below.
Explanation:You need to assign the user the Key Vault Secrets Officer role.
1. In the Azure portal, type Key Vaults in the search box, select Key Vaults from the search results then select KeyVault11641655. Alternatively, browse to Key Vaults in the left navigation pane.
2. In the key vault properties, select Access control (IAM).
3. In the Add a role assignment section, click the Add button.
4. In the Role box, select the Key Vault Secrets Officer role from the drop-down list.
5. In the Select box, start typing User2-11641655 and select User2-11641655 from the search results.
6. Click the Save button to save the changes. -
You have an Azure web app named WebApp1.
You upload a certificate to WebApp1.
You need to make the certificate accessible to the app code of WebApp1.
What should you do?
- Add a user-assigned managed identity to WebApp1.
- Add an app setting to the WebApp1 configuration.
- Enable system-assigned managed identity for WebApp1.
- Configure the TLS/SSL binding for WebApp1.