AZ-500 : Microsoft Azure Security Technologies : Part 12
-
HOTSPOT
You have the Azure key vaults shown in the following table.
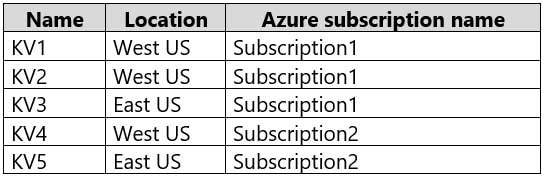
AZ-500 Microsoft Azure Security Technologies Part 12 Q01 320 KV1 stores a secret named Secret1 and a key for a managed storage account named Key1.
You back up Secret1 and Key1.
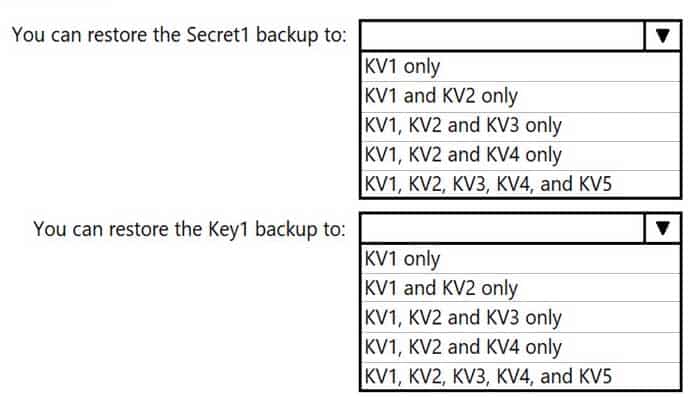
To which key vaults can you restore each backup? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
AZ-500 Microsoft Azure Security Technologies Part 12 Q01 321 Question 
AZ-500 Microsoft Azure Security Technologies Part 12 Q01 321 Answer Explanation:The backups can only be restored to key vaults in the same subscription and same geography. You can restore to a different region in the same geography.
-
HOTSPOT
You have an Azure subscription that contains an Azure key vault named Vault1.
On January 1, 2019, Vault1 stores the following secrets. All dates are in mm/dd/yy format.
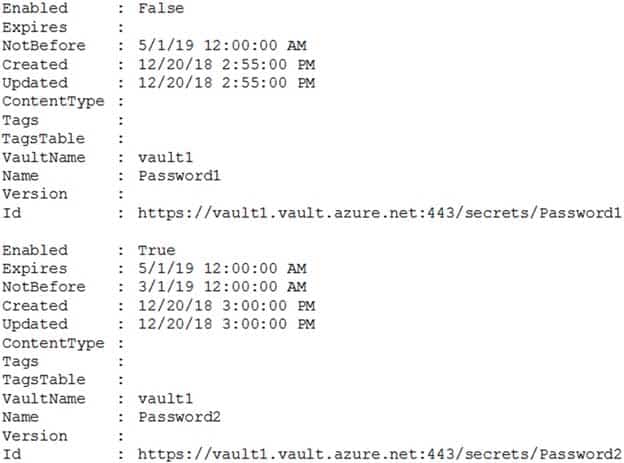
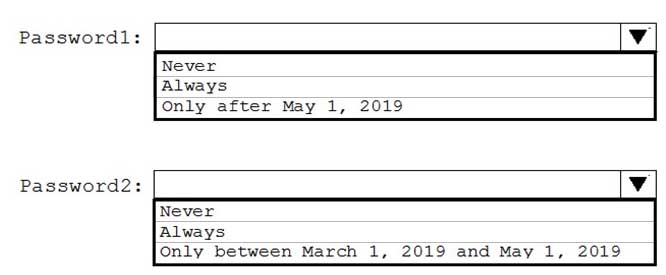
AZ-500 Microsoft Azure Security Technologies Part 12 Q02 322 When can each secret be used by an application? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
AZ-500 Microsoft Azure Security Technologies Part 12 Q02 323 Question 
AZ-500 Microsoft Azure Security Technologies Part 12 Q02 323 Answer -
You have an Azure web app named webapp1.
You need to configure continuous deployment for webapp1 by using an Azure Repo.
What should you create first?
- an Azure Application Insights service
- an Azure DevOps organization
- an Azure Storage account
- an Azure DevTest Labs lab
Explanation:
To use Azure Repos, make sure your Azure DevOps organization is linked to your Azure subscription. -
Your company has an Azure subscription named Sub1 that is associated to an Azure Active Directory (Azure AD) tenant named contoso.com.
The company develops an application named App1. App1 is registered in Azure AD.
You need to ensure that App1 can access secrets in Azure Key Vault on behalf of the application users.
What should you configure?
- an application permission without admin consent
- a delegated permission without admin consent
- a delegated permission that requires admin consent
- an application permission that requires admin consent
Explanation:Delegated permissions – Your client application needs to access the web API as the signed-in user, but with access limited by the selected permission. This type of permission can be granted by a user unless the permission requires administrator consent.
Incorrect Answers:
A, D: Application permissions – Your client application needs to access the web API directly as itself (no user context). This type of permission requires administrator consent and is also not available for public (desktop and mobile) client applications. -
DRAG DROP
Your company has an Azure Active Directory (Azure AD) tenant named contoso.com.
The company is developing an application named App1. App1 will run as a service on server that runs Windows Server 2016. App1 will authenticate to contoso.com and access Microsoft Graph to read directory data.
You need to delegate the minimum required permissions to App1.
Which three actions should you perform in sequence from the Azure portal? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
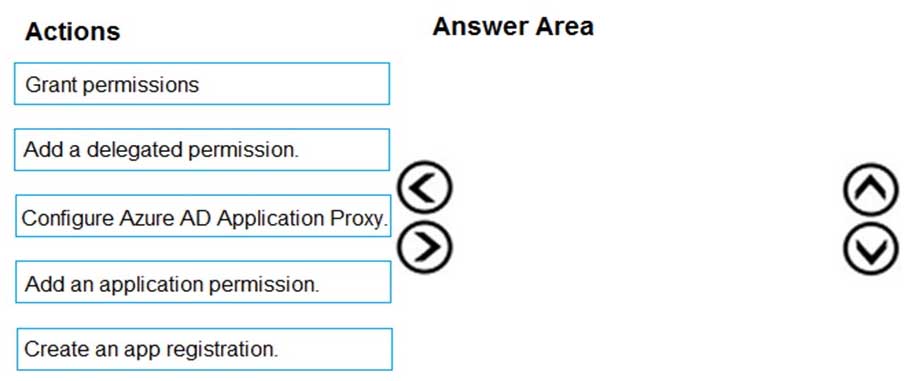
AZ-500 Microsoft Azure Security Technologies Part 12 Q05 325 Question 
AZ-500 Microsoft Azure Security Technologies Part 12 Q05 325 Answer Explanation:Step 1: Create an app registration
First the application must be created/registered.Step 2: Add an application permission
Application permissions are used by apps that run without a signed-in user present.Step 3: Grant permissions
Incorrect Answers:
Delegated permission
Delegated permissions are used by apps that have a signed-in user present.Application Proxy:
Azure Active Directory’s Application Proxy provides secure remote access to on-premises web applications. -
Your company has an Azure subscription named Sub1 that is associated to an Azure Active Directory (Azure AD) tenant named contoso.com.
The company develops a mobile application named App1. App1 uses the OAuth 2 implicit grant type to acquire Azure AD access tokens.
You need to register App1 in Azure AD.
What information should you obtain from the developer to register the application?
- a redirect URI
- a reply URL
- a key
- an application ID
Explanation:
For Native Applications you need to provide a Redirect URI, which Azure AD will use to return token responses. -
From the Azure portal, you are configuring an Azure policy.
You plan to assign policies that use the DeployIfNotExist, AuditIfNotExist, Append, and Deny effects.
Which effect requires a managed identity for the assignment?
- AuditIfNotExist
- Append
- DeployIfNotExist
- Deny
Explanation:
When Azure Policy runs the template in the deployIfNotExists policy definition, it does so using a managed identity. -
HOTSPOT
You have an Azure subscription named Sub1 that is associated to an Azure Active Directory (Azure AD) tenant named contoso.com.
You plan to implement an application that will consist of the resources shown in the following table.

AZ-500 Microsoft Azure Security Technologies Part 12 Q08 326 Users will authenticate by using their Azure AD user account and access the Cosmos DB account by using resource tokens.
You need to identify which tasks will be implemented in CosmosDB1 and WebApp1.
Which task should you identify for each resource? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
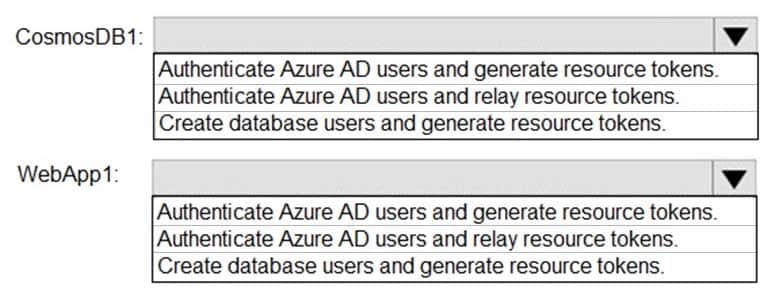
AZ-500 Microsoft Azure Security Technologies Part 12 Q08 327 Question 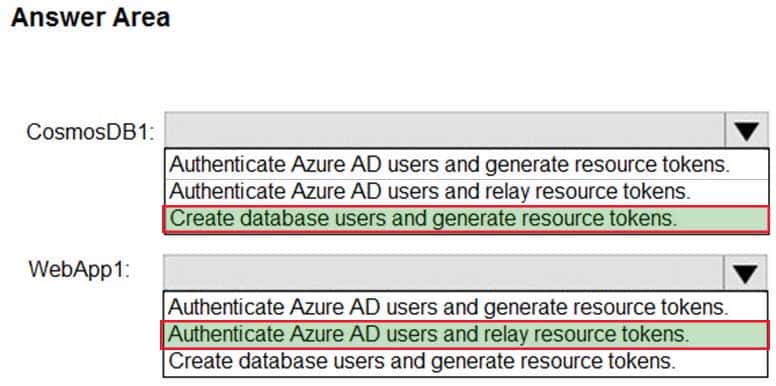
AZ-500 Microsoft Azure Security Technologies Part 12 Q08 327 Answer Explanation:CosmosDB1: Create database users and generate resource tokens.
Azure Cosmos DB resource tokens provide a safe mechanism for allowing clients to read, write, and delete specific resources in an Azure Cosmos DB account according to the granted permissions.WebApp1: Authenticate Azure AD users and relay resource tokens
A typical approach to requesting, generating, and delivering resource tokens to a mobile application is to use a resource token broker. The following diagram shows a high-level overview of how the sample application uses a resource token broker to manage access to the document database data:
AZ-500 Microsoft Azure Security Technologies Part 12 Q08 328 -
HOTSPOT
You need to create an Azure key vault. The solution must ensure that any object deleted from the key vault be retained for 90 days.
How should you complete the command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-500 Microsoft Azure Security Technologies Part 12 Q09 329 Question 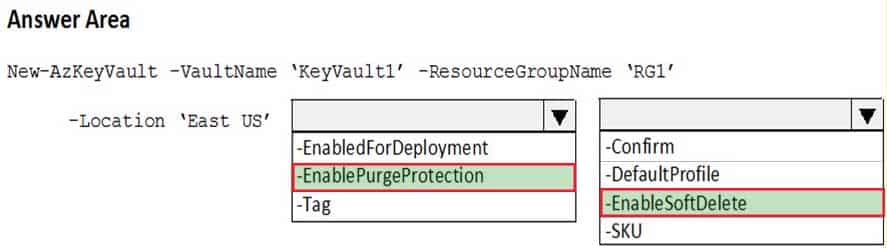
AZ-500 Microsoft Azure Security Technologies Part 12 Q09 329 Answer Explanation:Box 1: -EnablePurgeProtection
If specified, protection against immediate deletion is enabled for this vault; requires soft delete to be enabled as well.Box 2: -EnableSoftDelete
Specifies that the soft-delete functionality is enabled for this key vault. When soft-delete is enabled, for a grace period, you can recover this key vault and its contents after it is deleted. -
You have an Azure subscription that contains an Azure key vault named Vault1.
In Vault1, you create a secret named Secret1.
An application developer registers an application in Azure Active Directory (Azure AD).
You need to ensure that the application can use Secret1.
What should you do?
- In Azure AD, create a role.
- In Azure Key Vault, create a key.
- In Azure Key Vault, create an access policy.
- In Azure AD, enable Azure AD Application Proxy.
Explanation:Azure Key Vault provides a way to securely store credentials and other keys and secrets, but your code needs to authenticate to Key Vault to retrieve them.
Managed identities for Azure resources overview makes solving this problem simpler, by giving Azure services an automatically managed identity in Azure Active Directory (Azure AD). You can use this identity to authenticate to any service that supports Azure AD authentication, including Key Vault, without having any credentials in your code.Example: How a system-assigned managed identity works with an Azure VM
After the VM has an identity, use the service principal information to grant the VM access to Azure resources. To call Azure Resource Manager, use role-based access control (RBAC) in Azure AD to assign the appropriate role to the VM service principal. To call Key Vault, grant your code access to the specific secret or key in Key Vault. -
You have an Azure SQL database.
You implement Always Encrypted.
You need to ensure that application developers can retrieve and decrypt data in the database.
Which two pieces of information should you provide to the developers? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- a stored access policy
- a shared access signature (SAS)
- the column encryption key
- user credentials
- the column master key
Explanation:
Always Encrypted uses two types of keys: column encryption keys and column master keys. A column encryption key is used to encrypt data in an encrypted column. A column master key is a key-protecting key that encrypts one or more column encryption keys. -
You have a hybrid configuration of Azure Active Directory (Azure AD).
All users have computers that run Windows 10 and are hybrid Azure AD joined.
You have an Azure SQL database that is configured to support Azure AD authentication.
Database developers must connect to the SQL database by using Microsoft SQL Server Management Studio (SSMS) and authenticate by using their on-premises Active Directory account.
You need to tell the developers which authentication method to use to connect to the SQL database from SSMS. The solution must minimize authentication prompts.
Which authentication method should you instruct the developers to use?
- SQL Login
- Active Directory – Universal with MFA support
- Active Directory – Integrated
- Active Directory – Password
Explanation:Azure AD can be the initial Azure AD managed domain. Azure AD can also be an on-premises Active Directory Domain Services that is federated with the Azure AD.
Using an Azure AD identity to connect using SSMS or SSDT
The following procedures show you how to connect to a SQL database with an Azure AD identity using SQL Server Management Studio or SQL Server Database Tools.Active Directory integrated authentication
Use this method if you are logged in to Windows using your Azure Active Directory credentials from a federated domain.1. Start Management Studio or Data Tools and in the Connect to Server (or Connect to Database Engine) dialog box, in the Authentication box, select Active Directory – Integrated. No password is needed or can be entered because your existing credentials will be presented for the connection.
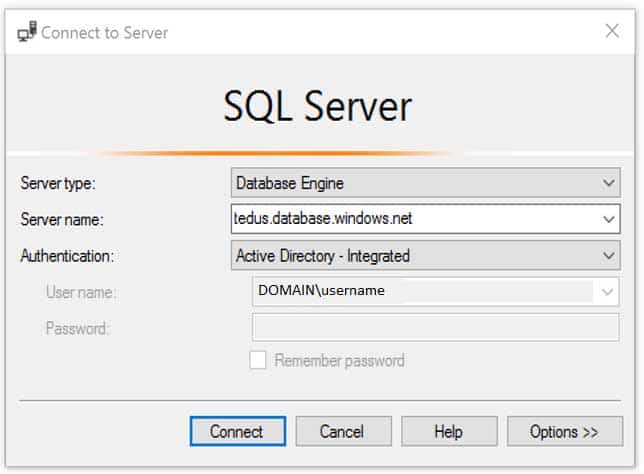
AZ-500 Microsoft Azure Security Technologies Part 12 Q12 330 2. Select the Options button, and on the Connection Properties page, in the Connect to database box, type the name of the user database you want to connect to. (The AD domain name or tenant ID” option is only supported for Universal with MFA connection options, otherwise it is greyed out.)
-
DRAG DROP
You have an Azure subscription named Sub1 that contains an Azure Storage account named contosostorage1 and an Azure key vault named Contosokeyvault1.
You plan to create an Azure Automation runbook that will rotate the keys of contosostorage1 and store them in Contosokeyvault1.
You need to implement prerequisites to ensure that you can implement the runbook.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

AZ-500 Microsoft Azure Security Technologies Part 12 Q13 331 Question 
AZ-500 Microsoft Azure Security Technologies Part 12 Q13 331 Answer Explanation:Step 1: Create an Azure Automation account
Runbooks live within the Azure Automation account and can execute PowerShell scripts.Step 2: Import PowerShell modules to the Azure Automation account
Under ‘Assets’ from the Azure Automation account Resources section select ‘to add in Modules to the runbook. To execute key vault cmdlets in the runbook, we need to add AzureRM.profile and AzureRM.key vault.Step 3: Create a connection resource in the Azure Automation account
You can use the sample code below, taken from the AzureAutomationTutorialScript example runbook, to authenticate using the Run As account to manage Resource Manager resources with your runbooks. The AzureRunAsConnection is a connection asset automatically created when we created ‘run as accounts’ above. This can be found under Assets -> Connections. After the authentication code, run the same code above to get all the keys from the vault.$connectionName = “AzureRunAsConnection”
try
{
# Get the connection “AzureRunAsConnection ”
$servicePrincipalConnection=Get-AutomationConnection -Name $connectionName“Logging in to Azure…”
Add-AzureRmAccount `
-ServicePrincipal `
-TenantId $servicePrincipalConnection.TenantId `
-ApplicationId $servicePrincipalConnection.ApplicationId `
-CertificateThumbprint $servicePrincipalConnection.CertificateThumbprint
} -
HOTSPOT
You have an Azure Storage account that contains a blob container named container1 and a client application named App1.
You need to enable App1 access to container1 by using Azure Active Directory (Azure AD) authentication.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
AZ-500 Microsoft Azure Security Technologies Part 12 Q14 332 Question 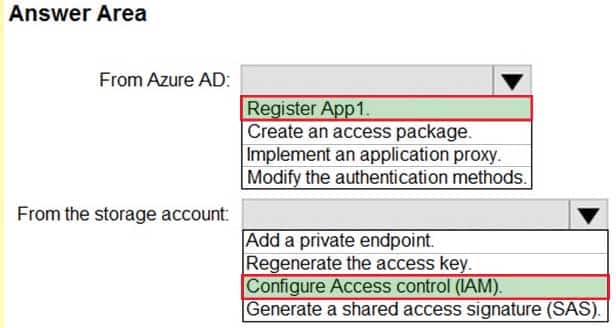
AZ-500 Microsoft Azure Security Technologies Part 12 Q14 332 Answer -
HOTSPOT
You have an Azure subscription that contains an Azure key vault named ContosoKey1.
You create users and assign them roles as shown in the following table.
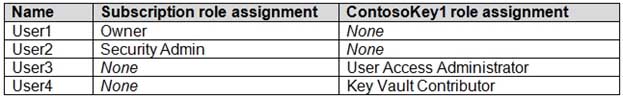
AZ-500 Microsoft Azure Security Technologies Part 12 Q15 333 You need to identify which users can perform the following actions:
– Delegate permissions for ContosoKey1.
– Configure network access to ContosoKey1.Which users should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-500 Microsoft Azure Security Technologies Part 12 Q15 334 Question 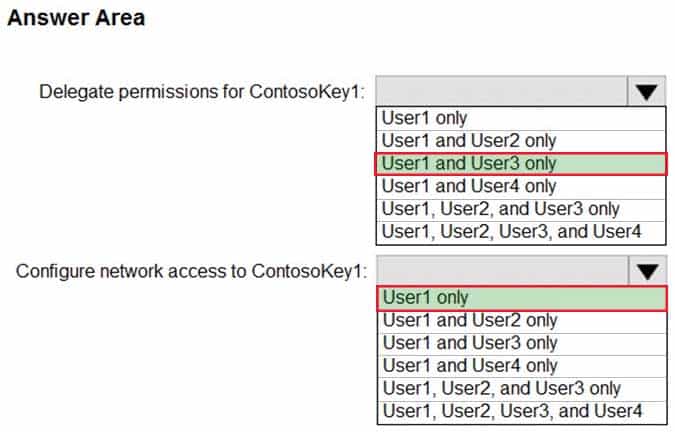
AZ-500 Microsoft Azure Security Technologies Part 12 Q15 334 Answer -
You have an Azure subscription that contains four Azure SQL managed instances.
You need to evaluate the vulnerability of the managed instances to SQL injection attacks.
What should you do first?
- Create an Azure Sentinel workspace.
- Enable Advanced Data Security.
- Add the SQL Health Check solution to Azure Monitor.
- Create an Azure Advanced Threat Protection (ATP) instance.
-
DRAG DROP
You have an Azure subscription named Sub1. Sub1 contains an Azure virtual machine named VM1 that runs Windows Server 2016.
You need to encrypt VM1 disks by using Azure Disk Encryption.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
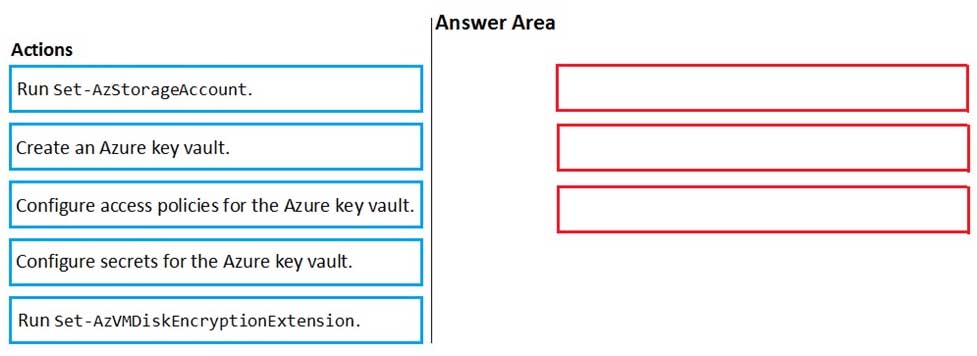
AZ-500 Microsoft Azure Security Technologies Part 12 Q17 335 Question 
AZ-500 Microsoft Azure Security Technologies Part 12 Q17 335 Answer -
You have an Azure subscription that contains a virtual machine named VM1.
You create an Azure key vault that has the following configurations:
– Name: Vault5
– Region: West US
– Resource group: RG1You need to use Vault5 to enable Azure Disk Encryption on VM1. The solution must support backing up VM1 by using Azure Backup.
Which key vault settings should you configure?
- Access policies
- Secrets
- Keys
- Locks
-
You have an Azure subscription named Sub1 that contains the resources shown in the following table.
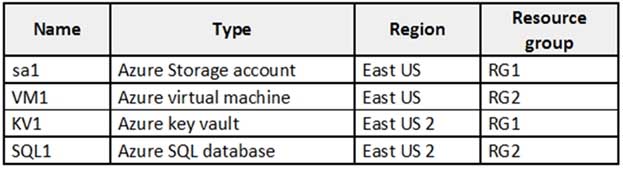
AZ-500 Microsoft Azure Security Technologies Part 12 Q19 336 You need to ensure that you can provide VM1 with secure access to a database on SQL1 by using a contained database user.
What should you do?
- Enable a managed identity on VM1.
- Create a secret in KV1.
- Configure a service endpoint on SQL1.
- Create a key in KV1.
-
You have an Azure subscription named Sub1 that contains the Azure key vaults shown in the following table:
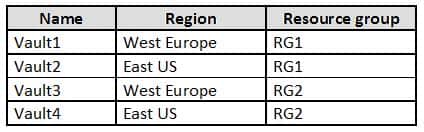
AZ-500 Microsoft Azure Security Technologies Part 12 Q20 337 In Sub1, you create a virtual machine that has the following configurations:
– Name: VM1
– Size: DS2v2
– Resource group: RG1
– Region: West Europe
– Operating system: Windows Server 2016You plan to enable Azure Disk Encryption on VM1.
In which key vaults can you store the encryption key for VM1?
- Vault1 or Vault3 only
- Vault1, Vault2, Vault3, or Vault4
- Vault1 only
- Vault1 or Vault2 only
Explanation:
In order to make sure the encryption secrets don’t cross regional boundaries, Azure Disk Encryption needs the Key Vault and the VMs to be co-located in the same region. Create and use a Key Vault that is in the same region as the VM to be encrypted.
