MD-101 : Managing Modern Desktops : Part 08
- This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.General Overview
Litware, Inc. is an international manufacturing company that has 3,000 employees. The company has sales, marketing, research, human resources (HR), development, and IT departments.
Litware has two main offices in New York and Los Angeles. Litware has five branch offices in Asia.
Existing Environment
Current Business Model
The Los Angeles office has 500 developers. The developers work flexible hours ranging from 11 AM to 10 PM.
Litware has a Microsoft Endpoint Configuration Manager deployment.
During discovery, the company discovers a process where users are emailing bank account information of its customers to internal and external recipients.
Current Environment
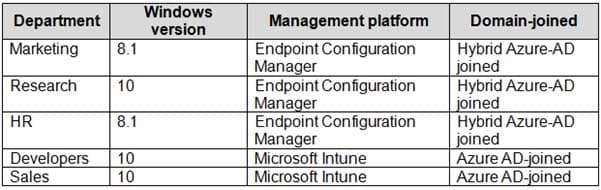
The network contains an Active Directory domain that is synced to Microsoft Azure Active Directory (Azure AD). The functional level of the forest and the domain is Windows Server 2012 R2. All domain controllers run Windows Server 2012 R2.
Litware has the computers shown in the following table.
MD-101 Managing Modern Desktops Part 08 Q01 082 The development department uses projects in Azure DevOps to build applications.
Most of the employees in the sales department are contractors. Each contractor is assigned a computer that runs Windows 10. At the end of each contract, the computer is assigned to a different contractor. Currently, the computers are re-provisioned manually by the IT department.
Problem Statements
Litware identifies the following issues on the network:
Employees in the Los Angeles office report slow Internet performance when updates are downloading. The employees also report that the updates frequently consume considerable resources when they are installed. The Update settings are configured as shown in the Updates exhibit. (Click the Updates button.)
Management suspects that the source code for the proprietary applications in Azure DevOps in being shared externally.
Re-provisioning the sales department computers is too time consuming.Requirements
Business Goals
Litware plans to transition to co-management for all the company-owned Windows 10 computers. Whenever possible, Litware wants to minimize hardware and software costs.
Device Management Requirements
Litware identifies the following device management requirements:
– Prevent the sales department employees from forwarding email that contains bank account information.
– Ensure that Microsoft Edge Favorites are accessible from all computers to which the developers sign in.
– Prevent employees in the research department from copying patented information from trusted applications to untrusted applications.Technical Requirements
Litware identifies the following technical requirements for the planned deployment:
– Re-provision the sales department computers by using Windows AutoPilot.
Ensure that the projects in Azure DevOps can be accessed from the corporate network only.
– Ensure that users can sign in to the Azure AD-joined computers by using a PIN. The PIN must expire every 30 days.
– Ensure that the company name and logo appears during the Out of Box Experience (OOBE) when using Windows AutoPilot.Exhibits
Updates
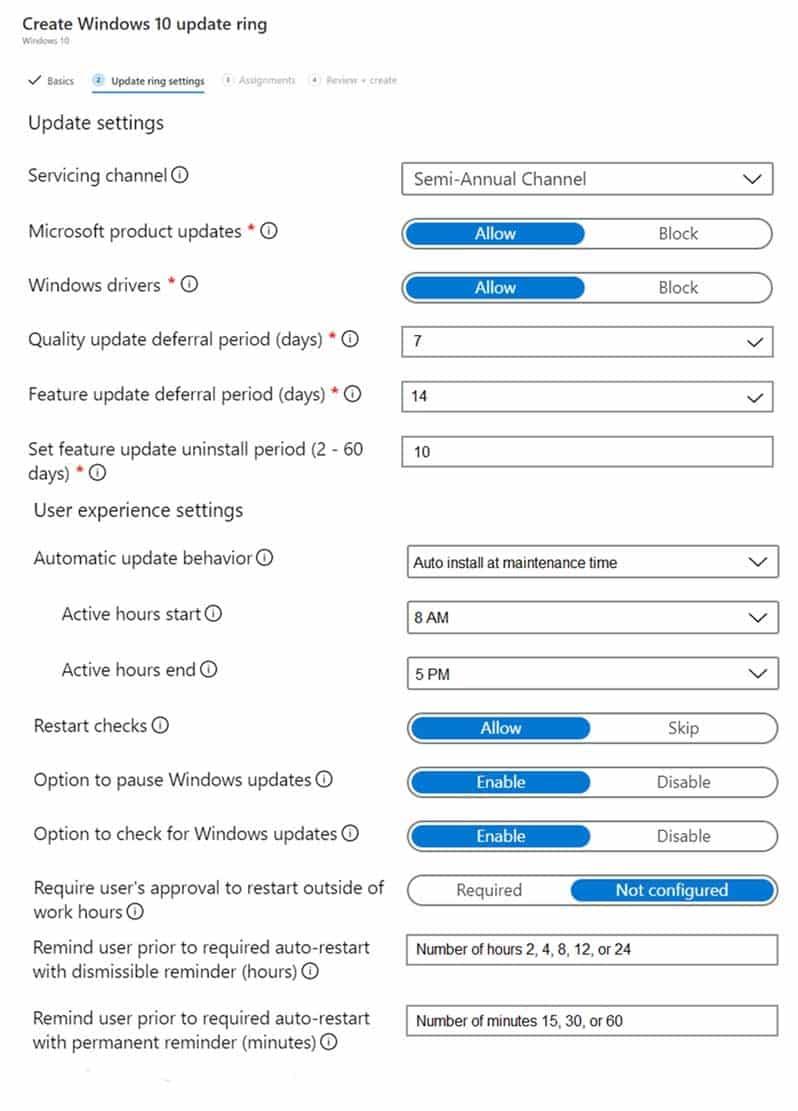
MD-101 Managing Modern Desktops Part 08 Q01 083 -
What should you use to meet the technical requirements for Azure DevOps?
- An app protection policy
- Windows Information Protection (WIP)
- Conditional access
- A device configuration profile
-
What should you upgrade before you can configure the environment to support co-management?
- the domain functional level
- Microsoft Endpoint Configuration Manager
- the domain controllers
- Windows Server Update Services (WSUS)
-
You need to meet the device management requirements for the developers.
What should you implement?
- Enterprise State Roaming
- folder redirection
- home folders
- known folder redirection in Microsoft OneDrive
Explanation:Litware identifies the following device management requirements:
– Ensure that Microsoft Edge Favorites are accessible from all computers to which the developers sign in.Enterprise State Roaming allows for the synchronization of Microsoft Edge browser setting, including favorites and reading list, across devices.
-
- This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.Overview
Contoso, Ltd, is a consulting company that has a main office in Montreal and two branch offices in Seattle and New York.Contoso has the users and computers shown in the following table.
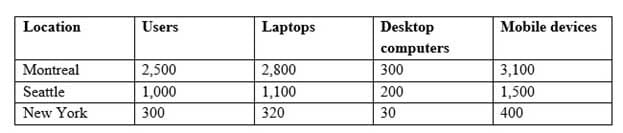
MD-101 Managing Modern Desktops Part 08 Q02 084 The company has IT, human resources (HR), legal (LEG), marketing (MKG) and finance (FIN) departments.
Contoso uses Microsoft Store for Business and recently purchased a Microsoft 365 subscription.
The company is opening a new branch office in Phoenix. Most of the users in the Phoenix office will work from home.
Existing Environment
The network contains an Active Directory domain named contoso.com that is synced to Microsoft Azure Active Directory (Azure AD).All member servers run Windows Server 2016. All laptops and desktop computers run Windows 10 Enterprise.
The computers are managed by using Microsoft Endpoint Configuration Manager. The mobile devices are managed by using Microsoft Intune.
The naming convention for the computers is the department acronym, followed by a hyphen, and then four numbers, for example, FIN-6785. All the computers are joined to the on-premises Active Directory domain.
Each department has an organizational unit (OU) that contains a child OU named Computers. Each computer account is in the Computers OU of its respective department.
Intune Configuration
The domain has the users shown in the following table.

MD-101 Managing Modern Desktops Part 08 Q02 085 User2 is a device enrollment manager (DEM) in Intune.
The devices enrolled in Intune are shown in the following table.

MD-101 Managing Modern Desktops Part 08 Q02 086 The device compliance policies in Intune are configured as shown in the following table.
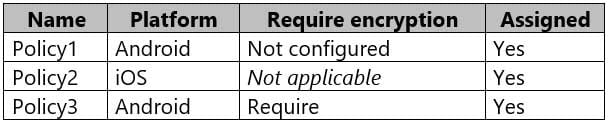
MD-101 Managing Modern Desktops Part 08 Q02 087 The device compliance policies have the assignments shown in the following table.

MD-101 Managing Modern Desktops Part 08 Q02 088 The device limit restrictions in Intune are configured as shown in the following table.

MD-101 Managing Modern Desktops Part 08 Q02 089 Requirements
Planned Changes
Contoso plans to implement the following changes:– Provide new computers to the Phoenix office users. The new computers have Windows 10 Pro preinstalled and were purchased already.
– Start using a free Microsoft Store for Business app named App1.
– Implement co-management for the computers.Technical Requirements
Contoso must meet the following technical requirements:– Ensure that the users in a group named Group4 can only access Microsoft Exchange Online from devices that are enrolled in Intune.
– Deploy Windows 10 Enterprise to the computers of the Phoenix office users by using Windows Autopilot.
– Monitor the computers in the LEG department by using Windows Analytics.
– Create a provisioning package for new computers in the HR department.
– Block iOS devices from sending diagnostic and usage telemetry data.
– Use the principle of least privilege whenever possible.
– Enable the users in the MKG department to use App1.
– Pilot co-management for the IT department.-
You need to meet the technical requirements for the iOS devices.
Which object should you create in Intune?
- A compliance policy
- An app protection policy
- A deployment profile
- A device configuration profile
Explanation:Scenario: Technical requirements include: Block iOS devices from sending diagnostic and usage telemetry data.
Intune includes device restriction policies that help administrators control Android, iOS, macOS, and Windows devices. These restrictions let you control a wide range of settings and features to protect your organization’s resources. For example, administrators can:
Allow or block the device camera
Control access to Google Play, app stores, viewing documents, and gaming
Block built-in apps, or create a list of apps that allowed or prohibited
Allow or prevent backing up files to cloud and storage accounts
Set a minimum password length, and block simple passwords -
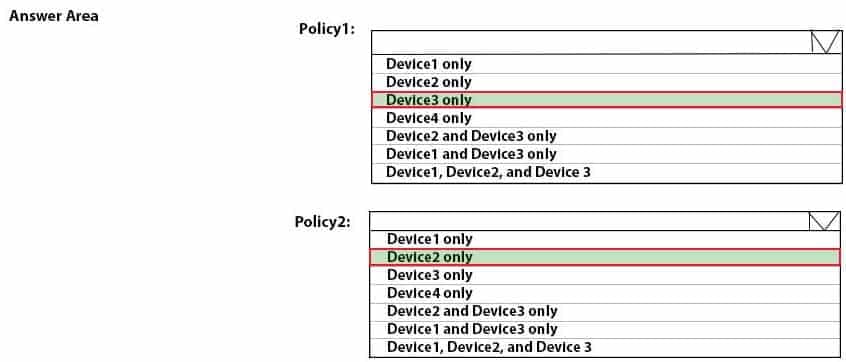
HOTSPOT
To which devices do Policy1 and Policy2 apply? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
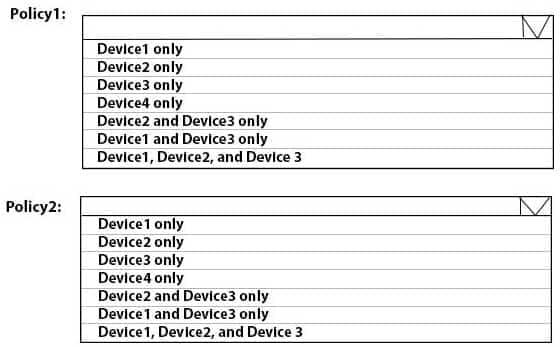
MD-101 Managing Modern Desktops Part 08 Q02 090 Question -
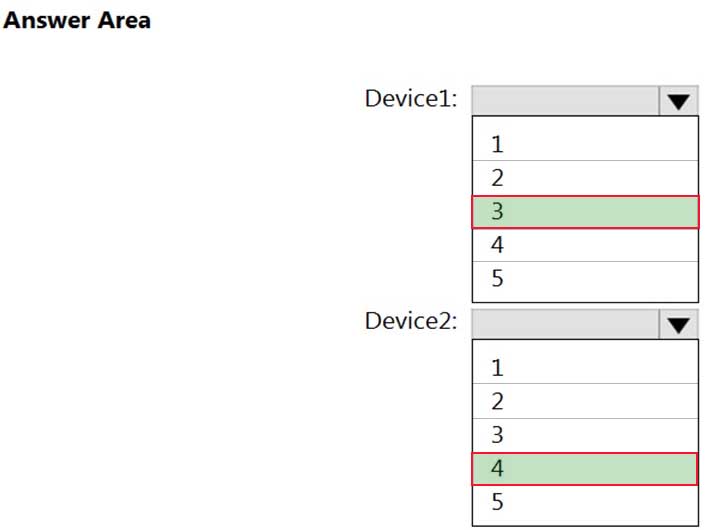
HOTSPOT
What is the maximum number of devices that User1 and User2 can enroll in Intune? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
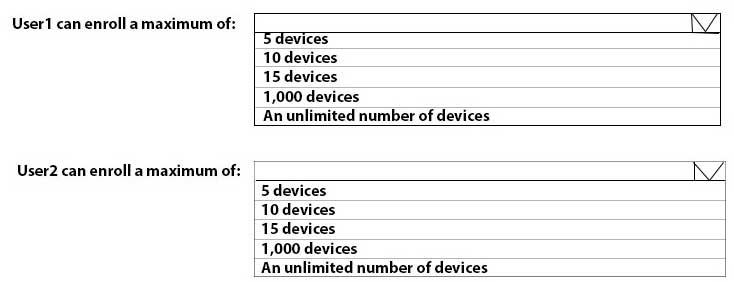
MD-101 Managing Modern Desktops Part 08 Q02 091 Question -
You need to meet the technical requirements for the IT department.
What should you do first?
- From the Azure Active Directory blade in the Azure portal, enable Seamless single sign-on.
- From the Configuration Manager console, add an Intune subscription.
- From the Azure Active Directory blade in the Azure portal, configure the Mobility (MDM and MAM) settings.
- From the Microsoft Intune blade in the Azure portal, configure the Windows enrollment settings.
-
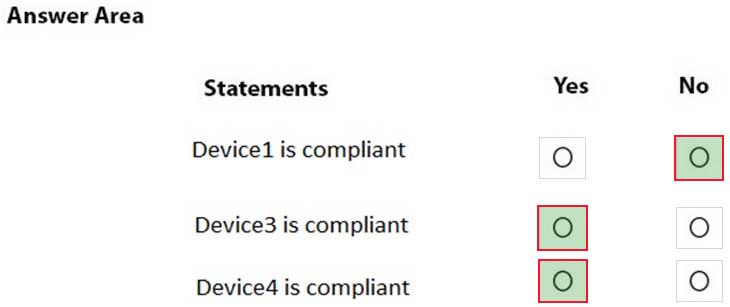
HOTSPOT
You are evaluating which devices are compliant.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MD-101 Managing Modern Desktops Part 08 Q02 092 Question -
HOTSPOT
You create a new conditional access policy that has an assignment for Office 365 Exchange Online.
You need to configure the policy to meet the technical requirements for Group4.
Which two settings should you configure in the policy? To answer, select the appropriate settings in the answer area.
NOTE: Each correct selection is worth one point.

MD-101 Managing Modern Desktops Part 08 Q02 093 Question 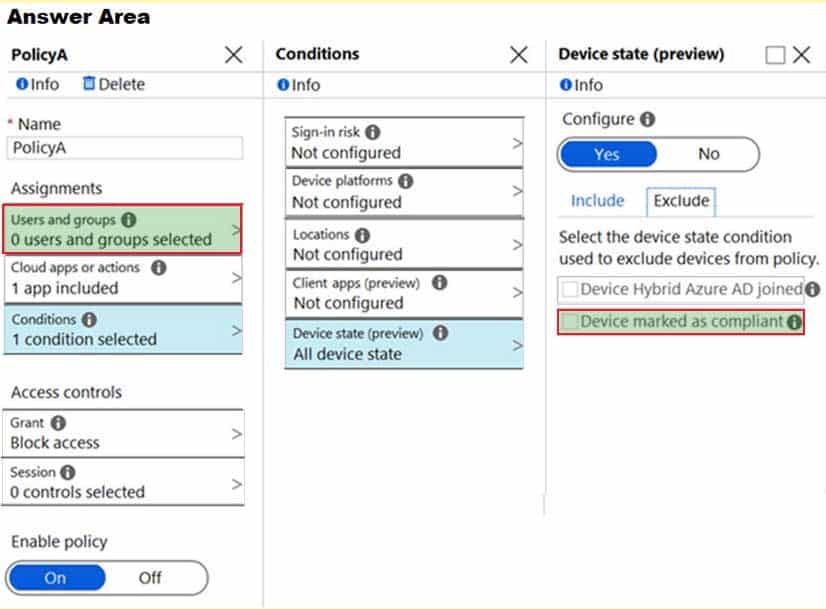
MD-101 Managing Modern Desktops Part 08 Q02 093 Answer Explanation:The policy needs to be applied to Group4 so we need to configure Users and Groups.
The Access controls are set to Block access

MD-101 Managing Modern Desktops Part 08 Q02 094 We therefore need to exclude compliant devices.
From the scenario:
– Ensure that the users in a group named Group4 can only access Microsoft Exchange Online from devices that are enrolled in Intune.Note: When a device enrolls in Intune, the device information is updated in Azure AD to include the device compliance status. This compliance status is used by conditional access policies to block or allow access to e-mail and other organization resources.
-
-
Case study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.
Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and branch offices in Seattle and New York.
Contoso has a Microsoft 365 E5 subscription.
Environment
Network Environment
The network contains an on-premises Active Directory domain named contoso.com. The domain contains the servers shown in the following table.

MD-101 Managing Modern Desktops Part 08 Q03 095 Contoso has a hybrid Azure Active Directory (Azure AD) tenant named contoso.com.
Contoso has a Microsoft Store for Business instance.
Users and Groups
The contoso.com tenant contains the users shown in the following table.
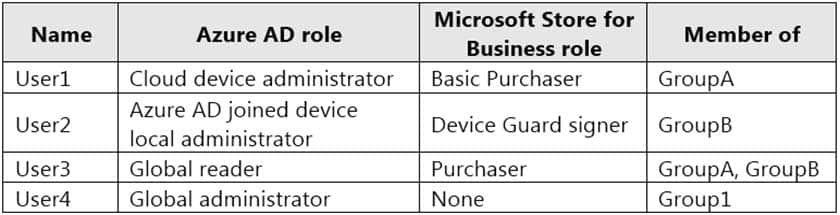
MD-101 Managing Modern Desktops Part 08 Q03 096 All users are assigned a Microsoft Office 365 license and an Enterprise Mobility + Security E3 license.
Enterprise State Roaming is enabled for Group1 and GroupA.
Group1 and Group2 have a Membership type of Assigned.
Devices
Contoso has the Windows 10 devices shown in the following table.
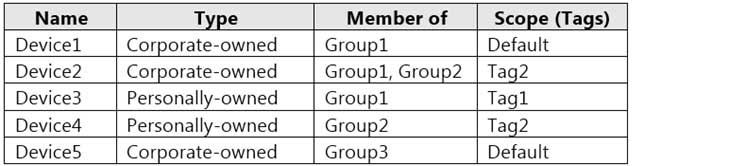
MD-101 Managing Modern Desktops Part 08 Q03 097 The Windows 10 devices are joined to Azure AD and enrolled in Microsoft Intune.
The Windows 10 devices are configured as shown in the following table.

MD-101 Managing Modern Desktops Part 08 Q03 098 All the Azure AD joined devices have an executable file named C:\AppA.exe and a folder named D:\Folder1.
Microsoft Endpoint Manager Configuration
Microsoft Endpoint Manager has the compliance policies shown in the following table.
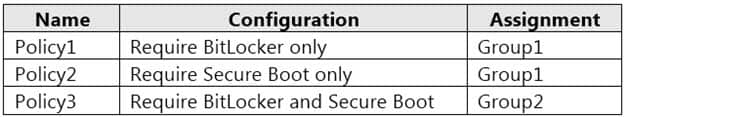
MD-101 Managing Modern Desktops Part 08 Q03 099 The Compliance policy settings are shown in the following exhibit.

MD-101 Managing Modern Desktops Part 08 Q03 100 The Automatic Enrollment settings have the following configurations:
MDM user scope: Group A
MAM user scope: Group BYou have an Endpoint protection configuration profile that has the following Controlled folder access settings:
Name: Protection1
Folder protection: Enable
List of apps that have access to protected folders: C:\*\AppA.exe
List of additional folders that need to be protected: D:\Folder1
Assignments:
– Included groups: Group2, Group BWindows Autopilot Configuration
Contoso has a Windows Autopilot deployment profile configured as shown in the following exhibit.

MD-101 Managing Modern Desktops Part 08 Q03 101 Currently, there are no devices deployed by using Window Autopilot.
The Intune connector for Active Directory is installed on Server1.
Requirements
Planned Changes
Contoso plans to implement the following changes:
Purchase a new Windows 10 device named Device6 and enroll the device in Intune.
New computers will be deployed by using Windows Autopilot and will be hybrid Azure AD joined.
Deploy a network boundary configuration profile that will have the following settings:
– Name: Boundary1
– Network boundary: 192.168.1.0/24
– Scope tags: Tag1
– Assignments:
– – Included groups: Group1, Group2Deploy two VPN configuration profiles named Connection1 and Connection2 that will have the following settings:
– Name: Connection1
– Connection name: VPN1
– Connection type: L2TP
– Assignments:
– – Included groups: Group1, Group2, GroupA
– – Excluded groups: —– Name: Connection2
– Connection name: VPN2
– Connection type: IKEv2
– Assignments:
– – Included groups: GroupA
– – Excluded groups: GroupBPurchase an app named App1 that is available in Microsoft Store for Business and to assign the app to all the users.
Technical Requirements
Contoso must meet the following technical requirements:
Users in GroupA must be able to deploy new computers.
Administrative effort must be minimized.-
HOTSPOT
User1 and User2 plan to use Sync your settings.
On which devices can the users use Sync your settings? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
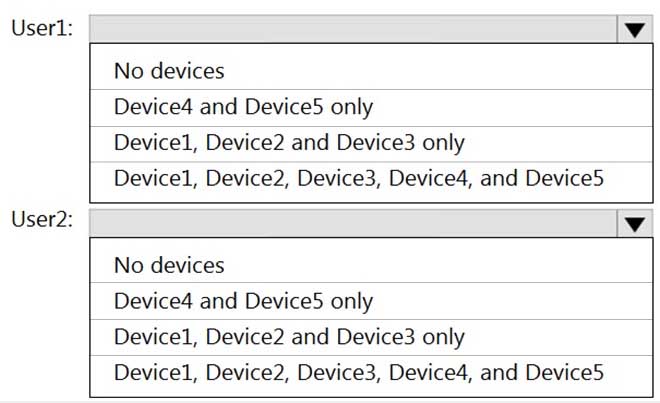
MD-101 Managing Modern Desktops Part 08 Q03 102 Question -
Which user can enroll Device6 in Intune?
- User4 and User2 only
- User4 and User1 only
- User4, User1, and User2 only
- User1, User2, User3, and User4
-
HOTSPOT
You implement the planned changes for Connection1 and Connection2.
How many VPN connections will there be for User1 when the user signs in to Device1 and Device2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
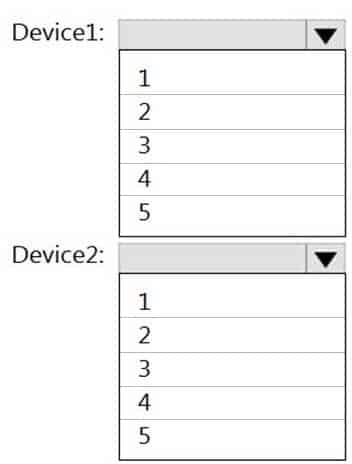
MD-101 Managing Modern Desktops Part 08 Q03 103 Question
-
-
HOTSPOT
You have a workgroup computer named Computer1 that runs Windows 10 and has the users shown in the following table.
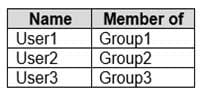
MD-101 Managing Modern Desktops Part 08 Q04 104 Group1 is a member of Group3.
You are creating a file named Kiosk.xml that specifies a lockdown profile for a multi-app kiosk.
Kiosk.xml contains the following section.

MD-101 Managing Modern Desktops Part 08 Q04 105 You apply Kiosk.xml to Computer1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
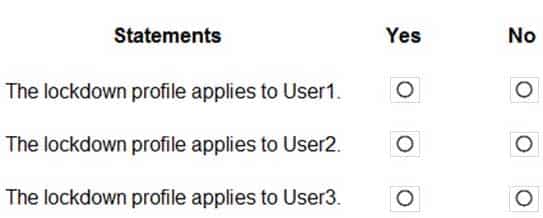
MD-101 Managing Modern Desktops Part 08 Q04 106 Question -
HOTSPOT
Your network contains an Active Directory domain named contoso.com that syncs to Azure Active Directory (Azure AD). The domain contains the users shown in the following table.
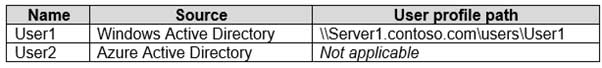
MD-101 Managing Modern Desktops Part 08 Q05 107 Enterprise State Roaming is enabled for User2.
You have the computers shown in the following table.
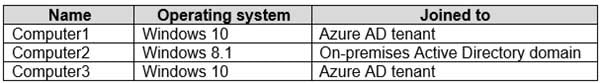
MD-101 Managing Modern Desktops Part 08 Q05 108 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
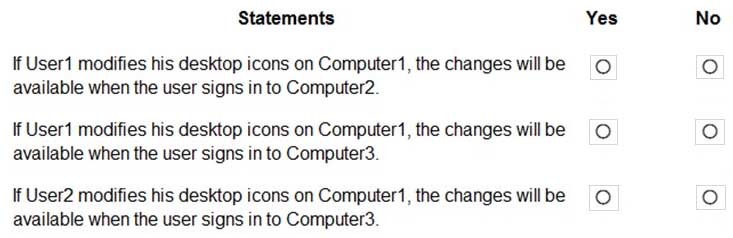
MD-101 Managing Modern Desktops Part 08 Q05 109 Question -
HOTSPOT
Your company has computers that run Windows 8.1, Windows 10, or macOS.
The company uses Microsoft Intune to manage the computers.
You need to create a device configuration profile to configure Windows Hello for Business on the computers that support it.
Which platform type and profile type should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
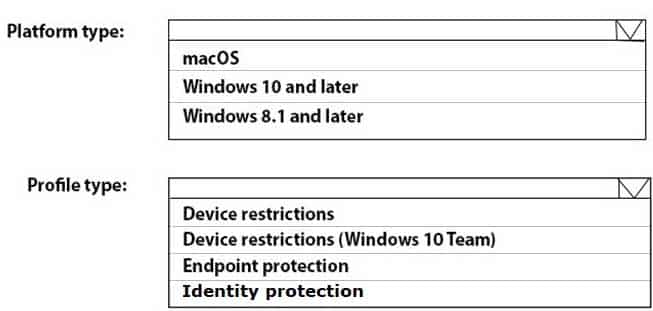
MD-101 Managing Modern Desktops Part 08 Q06 110 Question 
MD-101 Managing Modern Desktops Part 08 Q06 110 Answer Explanation:Windows Hello for Business is a method for signing in to Windows devices by replacing passwords, smart cards, and virtual smart cards. Intune includes built-in settings so Administrators can configure and use Windows Hello for Business. For example, you can use these settings to:
– Enable Windows Hello for Business for devices and users
– Set device PIN requirements, including a minimum or maximum PIN length
– Allow gestures, such as a fingerprint, that users can (or can’t use) to sign in to devices -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Directory group named Group1 that contains Windows 10 Enterprise devices and Windows 10 Pro devices.
From Microsoft Intune, you create a device configuration profile named Profile1.
You need to ensure that Profile1 applies to only the Windows 10 Enterprise devices in Group1.
Solution: You create an Azure Active Directory group that contains only the Windows 10 Enterprise devices. You assign Profile1 to the new group.
Does this meet the goal?
- Yes
- No
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Directory group named Group1 that contains Windows 10 Enterprise devices and Windows 10 Pro devices.
From Microsoft Intune, you create a device configuration profile named Profile1.
You need to ensure that Profile1 applies to only the Windows 10 Enterprise devices in Group1.
Solution: You create a scope tag, and then you add the scope tag to the Windows 10 Enterprise devices. You edit the settings of Profile1.
Does this meet the goal?
- Yes
- No
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Directory group named Group1 that contains Windows 10 Enterprise devices and Windows 10 Pro devices.
From Microsoft Intune, you create a device configuration profile named Profile1.
You need to ensure that Profile1 applies to only the Windows 10 Enterprise devices in Group1.
Solution: You configure an applicability rule for Profile1. You assign Profile1 to Group1.
Does this meet the goal?
- Yes
- No
-
HOTSPOT
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains a user named User1. User1 has the devices shown in the following table.

MD-101 Managing Modern Desktops Part 08 Q10 111 On September 5, 2019, you create and enforce a terms of use (ToU) in contoso.com. The ToU has the following settings:
– Name: Terms1
– Display name: Terms1 name
– Require users to expand the terms of use: Off
– Require users to consent on every device: On
– Expire consents: On
– Expire starting on: October 10, 2019
– Frequency: MonthlyFor each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MD-101 Managing Modern Desktops Part 08 Q10 112 Question -
HOTSPOT
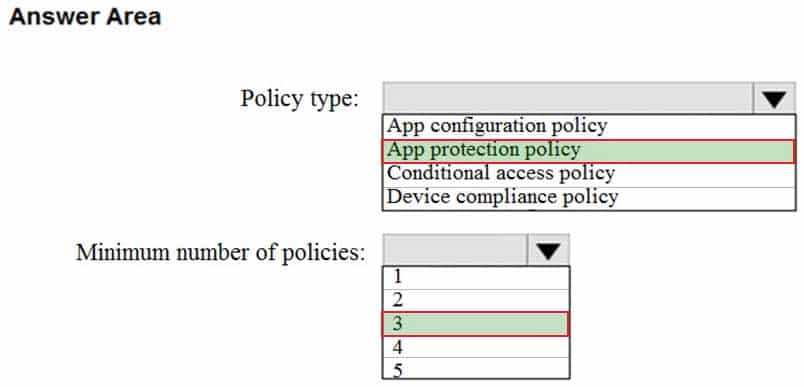
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the devices shown in the following table.
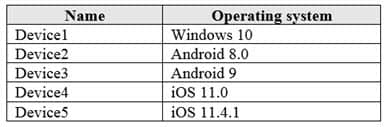
MD-101 Managing Modern Desktops Part 08 Q11 113 All devices contain an app named App1 and are enrolled in Microsoft Intune.
You need to prevent users from copying data from App1 and pasting the data into other apps.
Which type of policy and how many policies should you create in Intune? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
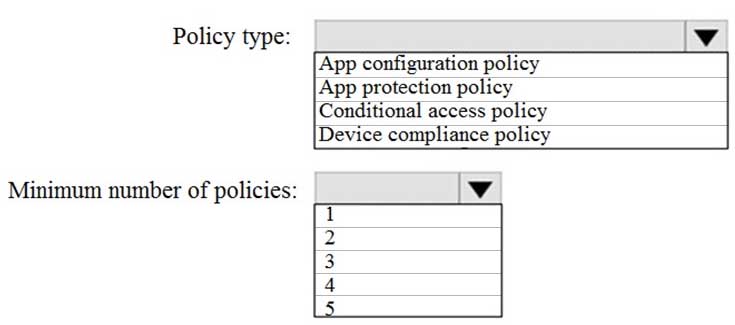
MD-101 Managing Modern Desktops Part 08 Q11 114 Question -
Your company has an internal portal that uses a URL of http://contoso.com.
The network contains computers that run Windows 10. The default browser on all the computers is Microsoft Edge.
You need to ensure that all users only use Internet Explorer to connect to the internal portal. The solution must ensure that Microsoft Edge can be used to connect to all other websites.
What should you do from each computer?
- From Internet Explorer, configure the Compatibility View settings
- From the local policy, configure Enterprise Mode
- From Microsoft Edge, configure the Advanced Site Settings
- From the Settings app, configure the default web browser settings
-
Your company uses Microsoft Intune.
More than 500 Android and iOS devices are enrolled in the Intune tenant.
You plan to deploy new Intune policies. Different policies will apply depending on the version of Android or iOS installed on the device.
You need to ensure that the policies can target the devices based on their version of Android or iOS.
What should you configure first?
- Corporate device identifiers in Intune
- Device settings in Microsoft Azure Active Directory (Azure AD)
- Device categories in Intune
- Groups that have dynamic membership rules in Microsoft Azure Active Directory (Azure AD)
Explanation:
We can create dynamic groups by using the device OS Version or device OS Type properties, and then apply Intune configuration policies to those groups. -
You have computers that run Windows 10 Pro. The computers are joined to Microsoft Azure Active Directory (Azure AD) and enrolled in Microsoft Intune.
You need to upgrade the computers to Windows 10 Enterprise.
What should you configure in Intune?
- A device enrollment policy
- A device cleanup rule
- A device compliance policy
- A device configuration profile
-
You are creating a device configuration profile in Microsoft Intune.
You need to implement an ADMX-backed policy.
Which profile type should you use?
- Identity protection
- Custom
- Device restrictions
- Device restrictions (Windows 10 Team)
-
HOTSPOT
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.

MD-101 Managing Modern Desktops Part 08 Q16 115 Contoso.com contains the devices shown in the following table.

MD-101 Managing Modern Desktops Part 08 Q16 116 In Intune, you create the app protection policies shown in the following table.

MD-101 Managing Modern Desktops Part 08 Q16 117 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MD-101 Managing Modern Desktops Part 08 Q16 118 Question -
Your network contains an Active Directory named contoso.com. The domain contains two computers named Computer1 and Computer2 that run Windows 10.
Folder Redirection is configured for a domain user named User1. The AppData\Roaming folder and the Desktop folder are redirected to a network share.
User1 signs in to Computer1 and performs the following tasks:
– Configures screen saver to start after five minutes of inactivity
– Modifies the default save location for Microsoft Word
– Creates a file named File1.docx on the desktop
– Modifies the desktop backgroundWhat will be retained when User1 signs in to Computer2?
- File1.docx and the desktop background only
- File1.docx, the screen saver settings, the desktop background, and the default save location for Word
- File1.docx only
- File1.docx, the desktop background, and the default save location for Word only
-
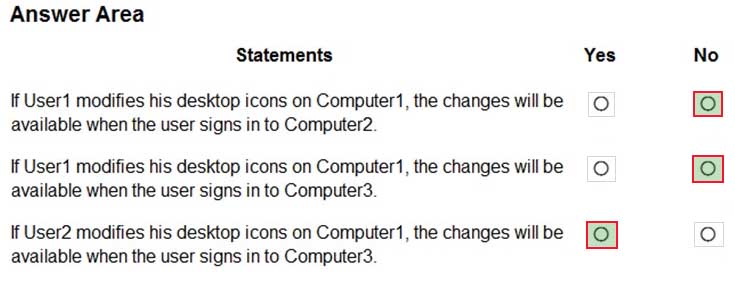
HOTSPOT
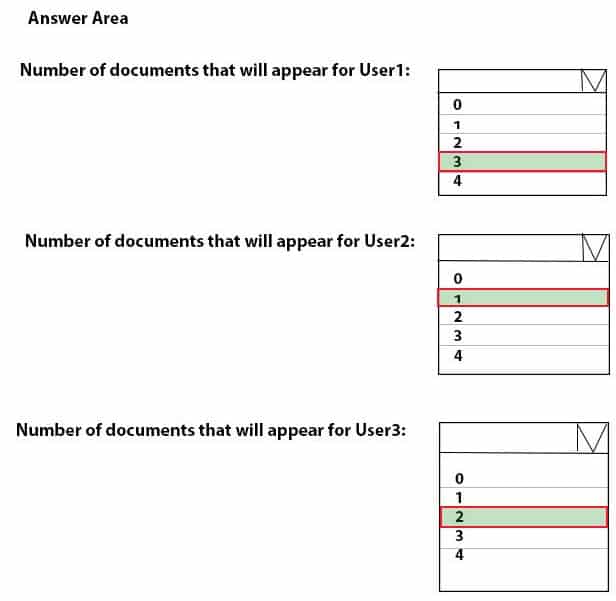
You have a computer named Computer1 that runs Windows 10.
Computer1 has the users shown in the following table.
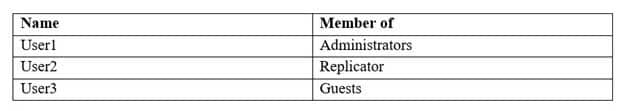
MD-101 Managing Modern Desktops Part 08 Q18 119 User1 signs in to Computer1, creates the following files, and then signs out:
– File1.docx in C:\Users\User1\Desktop
– File2.docx in C:\Users\Public\Public Desktop
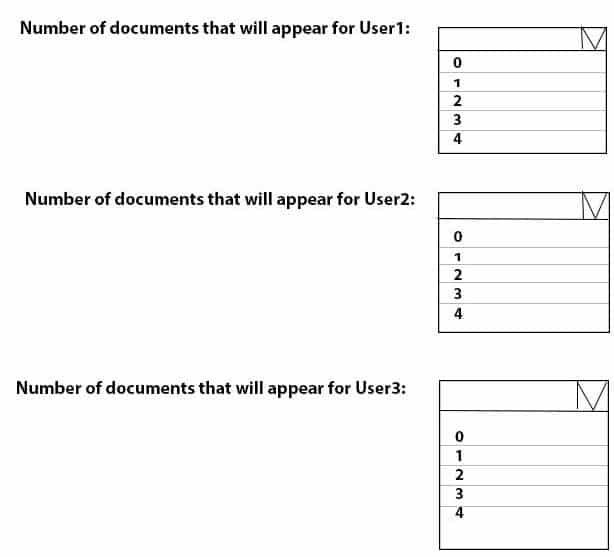
– File3.docx in C:\Users\Default\ DesktopUser3 then signs in to Computer1 and creates a file named File4.docx in C:\Users\User3\Desktop.
User2 has never signed in to Computer1.How many DOCX files will appear on the desktop of each user the next time each user signs in? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
MD-101 Managing Modern Desktops Part 08 Q18 120 Question -
Your network contains an Active Directory domain named contoso.com. The domain contains 200 computers that run Windows 10.
Folder Redirection for the Desktop folder is configured as shown in the following exhibit.

MD-101 Managing Modern Desktops Part 08 Q19 121 The target is set to Server1.
You plan to use known folder redirection in Microsoft OneDrive for Business.
You need to ensure that the desktop content of users remains on their desktop when you implement known folder redirection.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Clear the Grant the user exclusive rights to Desktop check box.
- Change the Policy Removal setting.
- Disable Folder Redirection.
- Clear the Move the contents of Desktop to the new location check box.
-
HOTSPOT
You have a Microsoft 365 subscription.
All computers are enrolled in Microsoft Intune.
You have business requirements for securing your Windows 10 environment as shown in the following table.

MD-101 Managing Modern Desktops Part 08 Q20 122 What should you implement to meet each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
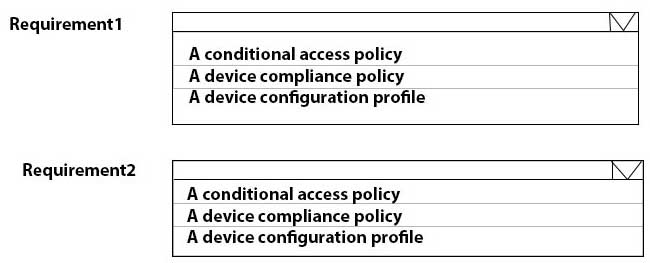
MD-101 Managing Modern Desktops Part 08 Q20 123 Question