MD-101 : Managing Modern Desktops : Part 13
-
You have a computer named Computer1 that runs Windows 10.
Computer1 is used by a user named User1.
You need to ensure that when User1 opens websites from untrusted locations by using Microsoft Edge, Microsoft Edge runs in an isolated container.
What should you do first?
- From Windows Features, turn on Microsoft Defender Application Guard.
- From Windows Features, turn on Hyper-V Platform.
- From Windows Security, configure the Virus & threat protection settings.
- From Windows Security, configure the Device security settings.
-
You have computers that run Windows 10 and are managed by using Microsoft Intune.
Users store their files in a folder named D:\Folder1.
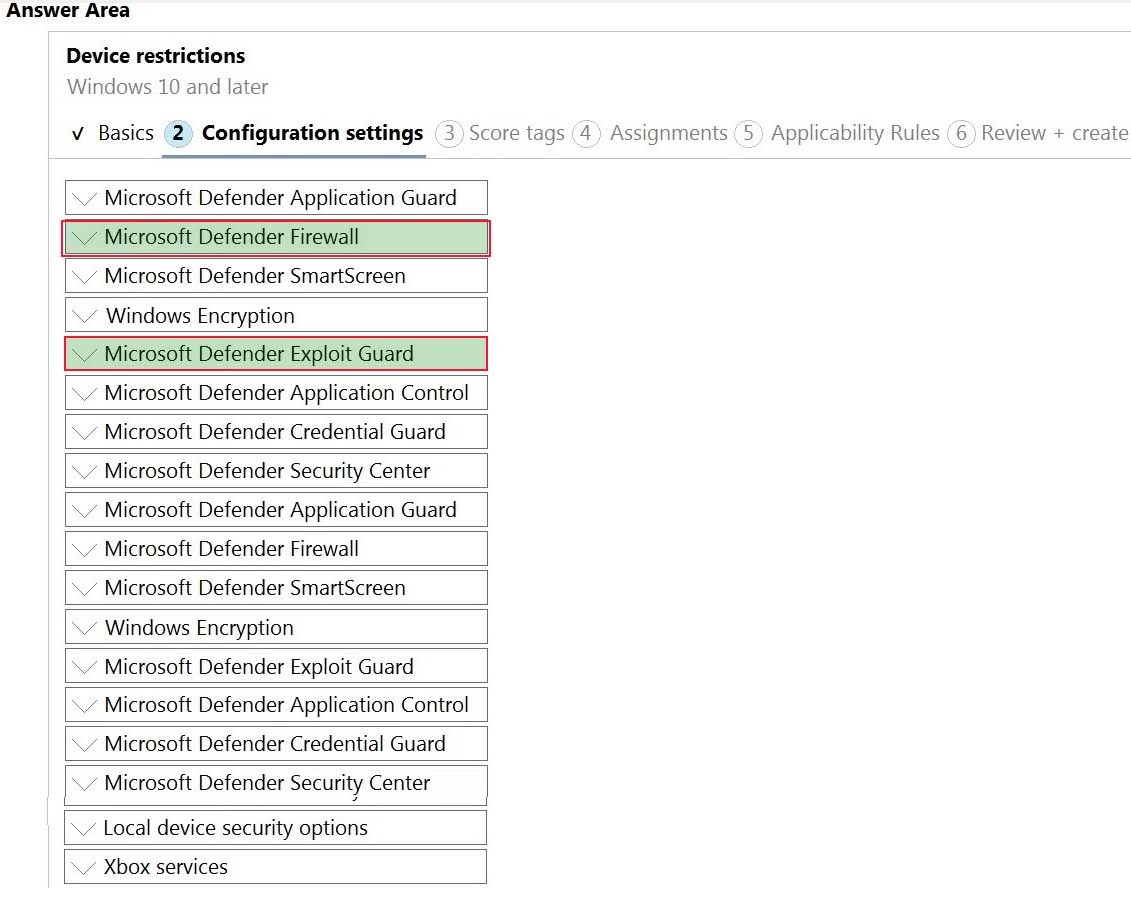
You need to ensure that only a trusted list of applications is granted write access to D:\Folder1.
What should you configure in the device configuration profile?
- Microsoft Defender SmartScreen
- Microsoft Defender Exploit Guard
- Microsoft Defender Application Guard
- Microsoft Defender Application Control
-
HOTSPOT
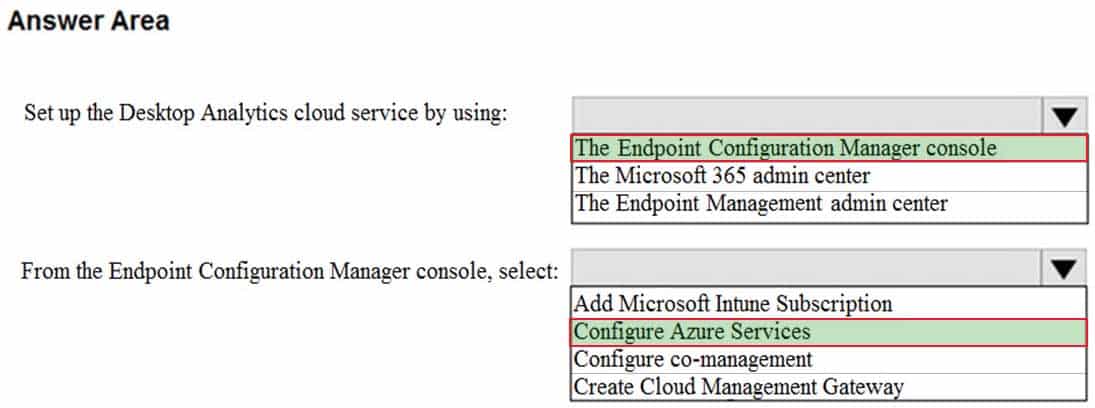
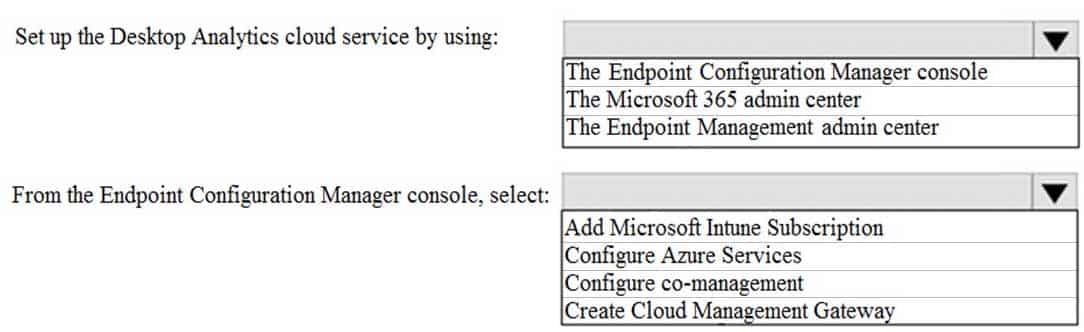
Your company uses Microsoft Endpoint Configuration Manager and purchases a Microsoft 365 subscription.
You need to set up Desktop Analytics.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
MD-101 Managing Modern Desktops Part 13 Q03 193 Question -
You need to enable Microsoft Defender Credential Guard on computers that run Windows 10.
What should you install on the computers?
- Hyper-V
- Microsoft Defender Application Guard
- a guarded host
- containers
-
DRAG DROP
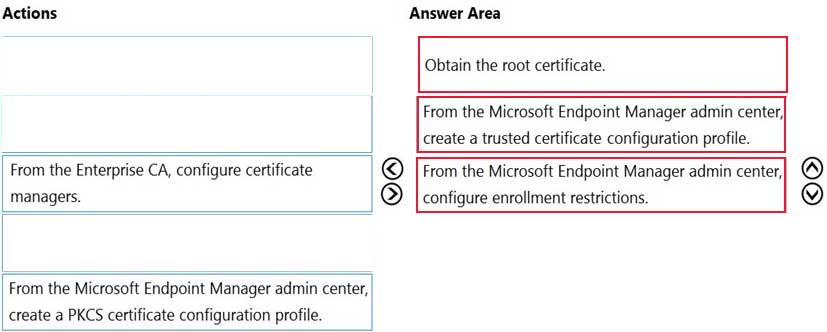
You have a Microsoft Intune subscription that is configured to use a PFX certificate connector to an on-premises Enterprise certification authority (CA).
You need to use Intune to configure autoenrollment for Android devices by using public key pair (PKCS) certificates.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
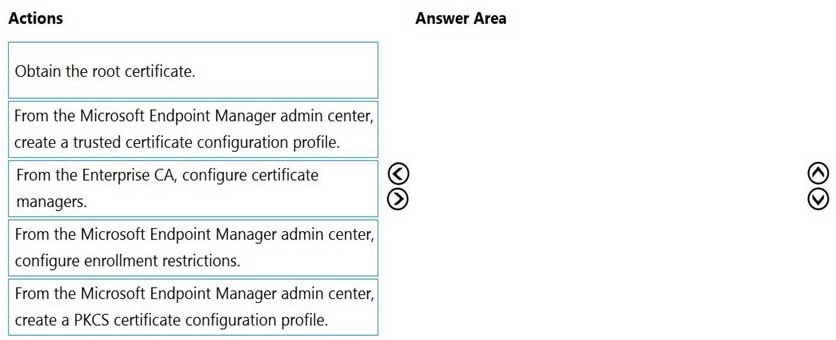
MD-101 Managing Modern Desktops Part 13 Q05 194 Question -
HOTSPOT
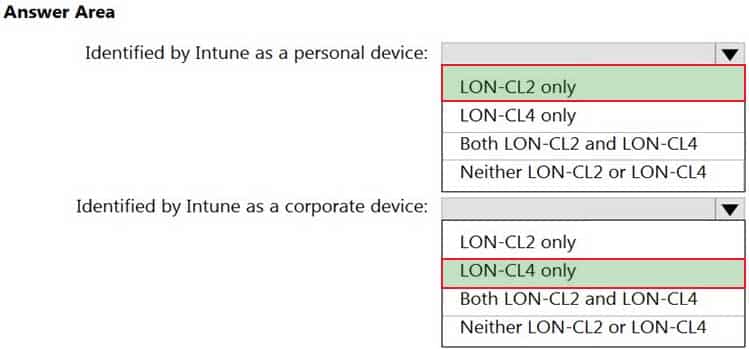
You have a Microsoft 365 tenant that uses Microsoft Intune to manage personal and corporate devices. The tenant contains three Windows 10 devices as shown in the following exhibit.

MD-101 Managing Modern Desktops Part 13 Q06 195 How will Intune classify each device after the devices are enrolled in Intune automatically? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
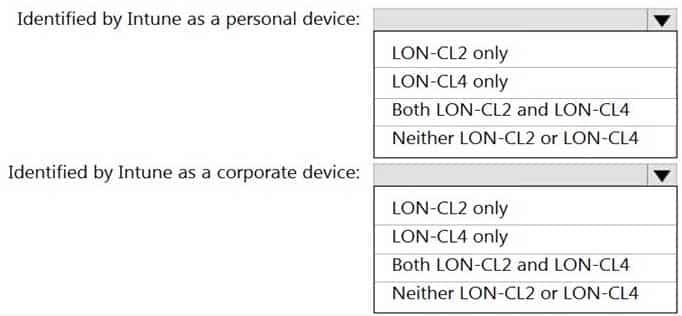
MD-101 Managing Modern Desktops Part 13 Q06 196 Question -
You have computers that run Windows 10 and are joined to Azure Active Directory (Azure AD).
All users sign in to the computers by using their Azure AD account.
Enterprise State Roaming is enabled.
From the Settings app, a user named User1 adds a Microsoft account.
Which account will be used for the Synchronizing Windows setting?
- the work account only
- the Microsoft account only
- both the Microsoft account and the work account
-
Your network contains an Active Directory domain. The domain contains 100 computers that run Windows 10.
You need to prevent users and apps from accessing dangerous websites.
What should you configure?
- Microsoft Defender Application Control
- Microsoft Defender Exploit Guard
- Microsoft Defender Application Guard
- Microsoft Defender Firewall
-
You have a Microsoft Intune subscription associated to an Azure Active Directory (Azure AD) tenant named contoso.com.
Users use one of the following three suffixes when they sign in to the tenant: us.contoso.com, eu.contoso.com, or contoso.com.
You need to ensure that the users are NOT required to specify the mobile device management (MDM) enrollment URL as part of the enrollment process. The solution must minimize the number of changes.
Which DNS records do you need?
- three TXT records
- one CNAME record only
- one TXT record only
- three CNAME records
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has several Windows 10 devices that are enrolled in Microsoft Intune.
You deploy a new computer named Computer1 that runs Windows 10 and is in a workgroup.
You need to enroll Computer1 in Intune.
Solution: From Computer1, you sign in to https://endpoint.microsoft.com and use the Windows enrollment blade.
Does this meet the goal?
- Yes
- No
Explanation:
Use MDM enrolment.
MDM only enrollment lets users enroll an existing Workgroup, Active Directory, or Azure Active directory joined PC into Intune. Users enroll from Settings on the existing Windows PC. -
HOTSPOT
Your network contains an Active Directory domain. Active Directory is synced with Microsoft Azure Active Directory (Azure AD).
There are 500 Active Directory domain-joined computers that run Windows 10 and are enrolled in Microsoft Intune.
You plan to implement Microsoft Defender Exploit Guard.
You need to create a custom Microsoft Defender Exploit Guard policy, and then distribute the policy to all the computers.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
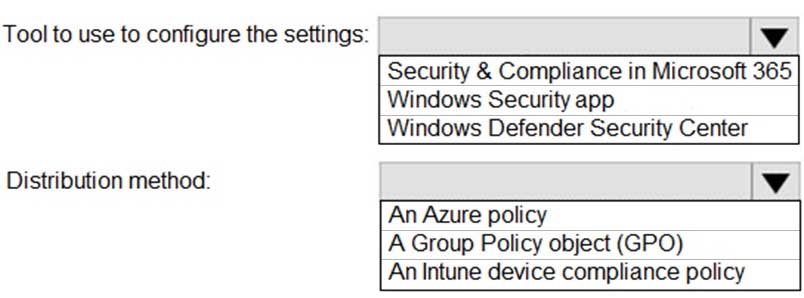
MD-101 Managing Modern Desktops Part 13 Q11 197 Question -
You have 100 devices that run Windows 10 and are joined to Microsoft Azure Active Directory (Azure AD).
You need to prevent users from joining their home computer to Azure AD.
What should you do?
- From the Device enrollment blade in the Intune admin center, modify the Enrollment restriction settings.
- From the Devices blade in the Azure Active Directory admin center, modify the Device settings.
- From the Device enrollment blade in the Intune admin center, modify the Device enrollment manages settings.
- From the Mobility (MDM and MAM) blade in the Azure Active Directory admin center, modify the Microsoft Intune enrollment settings.
-
Your company has a Microsoft 365 subscription.
A new user named Admin1 is responsible for deploying Windows 10 to computers and joining the computers to Microsoft Azure Active Directory (Azure AD).
Admin1 successfully joins computers to Azure AD.
Several days later, Admin1 receives the following error message: “This user is not authorized to enroll. You can try to do this again or contact your system administrator with the error code (0x801c0003).”
You need to ensure that Admin1 can join computers to Azure AD and follow the principle of least privilege.
What should you do?
- Assign the Global administrator role to Admin1.
- Modify the Device settings in Azure AD.
- Assign the Cloud device administrator role to Admin1.
- Modify the User settings in Azure AD.
-
Your network contains an Active Directory domain named contoso.com. The domain contains computers that run Windows 10 and are joined to the domain.
The domain is synced to Microsoft Azure Active Directory (Azure AD).
You create an Azure Log Analytics workspace and deploy the Update Compliance solution.
You need to enroll the computers in the Update Compliance solution.
Which Group Policy setting should you configure?
- Specify intranet Microsoft update service location
- Allow Telemetry
- Configure the Commercial ID
- Connected User Experiences and Telemetry
Explanation:
Microsoft uses a unique commercial ID to map information from user computers to your Azure workspace. Copy your commercial ID key from any of the Windows Analytics solutions you have added to your Windows Portal, and then deploy it to user computers. -
You have an Azure Active Directory (Azure AD) tenant and 100 Windows 10 devices that are Azure AD joined and managed by using Microsoft Intune.
You need to configure Microsoft Defender Firewall and Microsoft Defender Antivirus on the devices. The solution must minimize administrative effort.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- To configure Microsoft Defender Antivirus, create a device configuration profile and configure the Endpoint protection settings.
- To configure Microsoft Defender Firewall, create a device configuration profile and configure the Device restrictions settings.
- To configure Microsoft Defender Firewall, create a Group Policy Object (GPO) and configure Windows Defender Firewall with Advanced Security.
- To configure Microsoft Defender Antivirus, create a Group Policy Object (GPO) and configure Windows Defender Antivirus settings.
- To configure Microsoft Defender Antivirus, create a device configuration profile and configure the Device restrictions settings.
- To configure Microsoft Defender Firewall, create a device configuration profile and configure the Endpoint protection settings.
Explanation:
F: With Intune, you can use device configuration profiles to manage common endpoint protection security features on devices, including:
– Firewall
– BitLocker
– Allowing and blocking apps
– Microsoft Defender and encryption -
Your network contains an Active Directory domain that is synced to Microsoft Azure Active Directory (Azure AD). The domain contains computers that run Windows 10. The computers are enrolled in Microsoft Intune and Windows Analytics.
Your company protects documents by using Windows Information Protection (WIP).
You need to identify non-approved apps that attempt to open corporate documents.
What should you use?
- the Device Health solution in Windows Analytics
- Microsoft Cloud App Security
- Intune Data Warehouse
- the App protection status report in Intune
-
HOTSPOT
Your company uses Microsoft Defender for Endpoint. Microsoft Defender for Endpoint includes the device groups shown in the following table.
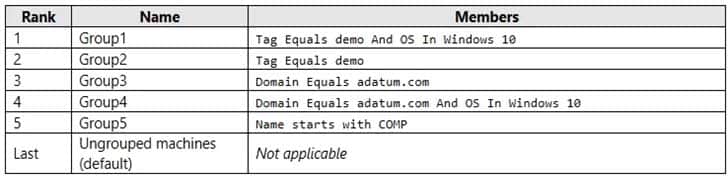
MD-101 Managing Modern Desktops Part 13 Q17 198 You onboard a computer to Microsoft Defender for Endpoint as shown in the following exhibit.
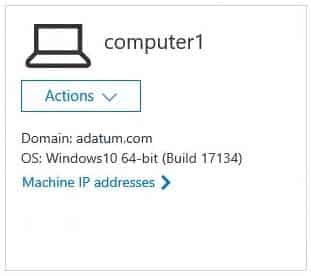
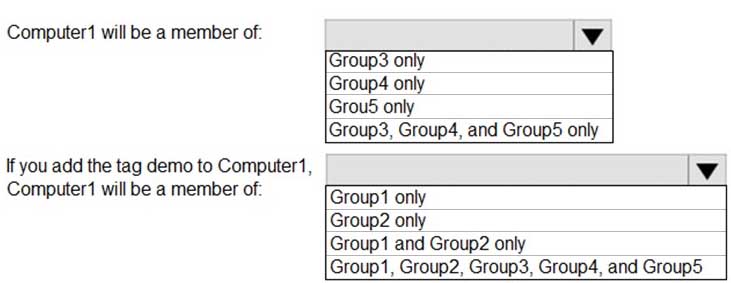
MD-101 Managing Modern Desktops Part 13 Q17 199 What is the effect of the Microsoft Defender for Endpoint configuration? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
MD-101 Managing Modern Desktops Part 13 Q17 200 Question -
Your company has computers that run Windows 10. The company uses Microsoft Intune to manage the computers.
You have an app protection policy for Microsoft Edge. You assign the policy to a group.
On a computer named Computer1, you open Microsoft Edge.
You need to verify whether Microsoft Edge on Computer1 is protected by the app protection policy.
Which column should you add in Task Manager?
- Operating system context
- UAC virtualization
- Enterprise Context
- Data Execution Prevention
-
HOTSPOT
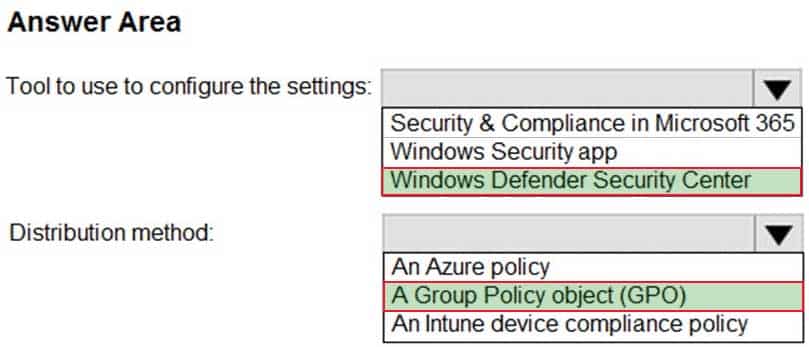
You have 200 computers that run Windows 10. The computers are joined to Microsoft Azure Active Directory (Azure AD) and enrolled in Microsoft Intune.
You need to configure an Intune device configuration profile to meet the following requirements:
Prevent Microsoft Office applications from launching child processes.
Block users from transferring files over FTP.Which two settings should you configure in Endpoint protection? To answer, select the appropriate settings in the answer area.
NOTE: Each correct selection is worth one point.
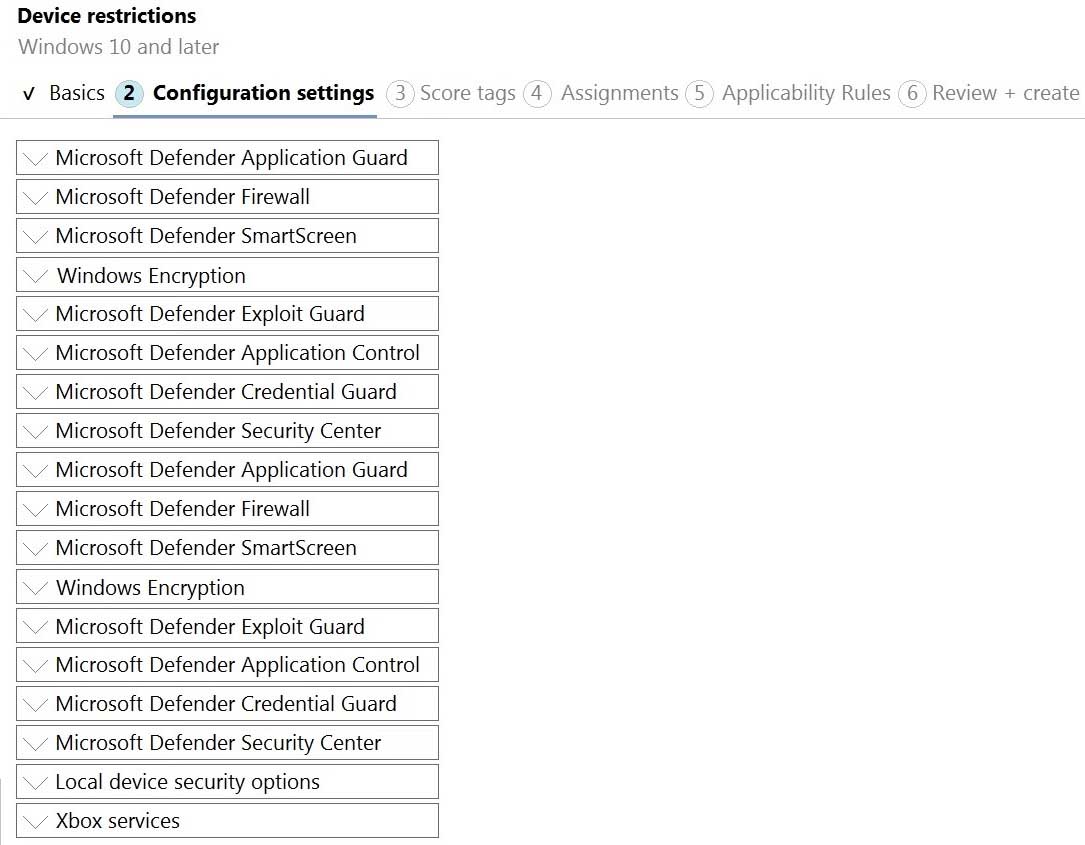
MD-101 Managing Modern Desktops Part 13 Q19 201 Question -
HOTSPOT
You have a Microsoft 365 subscription.
You need to configure access to Microsoft Office 365 for unmanaged devices. The solution must meet the following requirements:
– Allow only the Microsoft Intune Managed Browser to access Office 365 web interfaces.
– Ensure that when users use the Intune Managed Browser to access Office 365 web interfaces, they can only copy data to applications that are managed by the company.Which two settings should you configure from the Microsoft Intune blade? To answer, select the appropriate settings in the answer area.
Note: Each correct selection is worth one point.
MD-101 Managing Modern Desktops Part 13 Q20 202 Question