MS-100 : Microsoft 365 Identity and Services : Part 11
-
HOTSPOT
Your network contains an on-premises Active Directory domain named contoso.com. The domain contains five domain controllers.
Your company purchases Microsoft 365 and creates a Microsoft Azure Directory (Azure AD) tenant named contoso.onmicrosoft,com.
You plan to establish federation authentication between on-premises Active Directory and the Azure AD tenant by using Active Directory Federation Services (AD FS).
You need to establish the federation.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MS-100 Microsoft 365 Identity and Services Part 11 Q01 136 Question 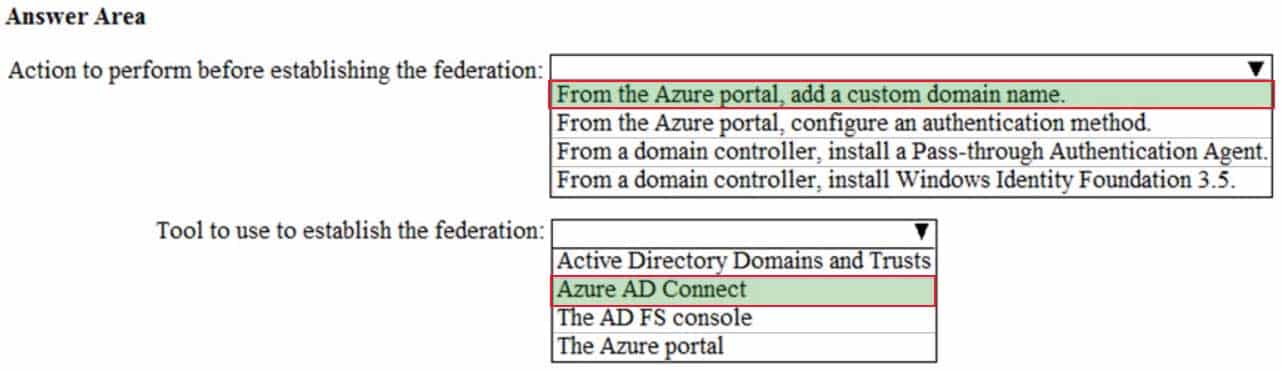
MS-100 Microsoft 365 Identity and Services Part 11 Q01 136 Answer Explanation:The on-premises Active Directory domain is named contoso.com. Before you can configure federation authentication between on-premises Active Directory and the Azure AD tenant, you need to add the domain contoso.com to Microsoft 365. You do this by adding a custom domain name.
The next step is to establish the federation. You can configure AD FS by using Azure AD Connect. -
Case study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and two branch offices in Seattle and New York.
The offices have the users and devices shown in the following table.

MS-100 Microsoft 365 Identity and Services Part 11 Q02 137 Contoso recently purchased a Microsoft 365 E5 subscription.
Existing Environment
The network contains an Active directory forest named contoso.com and a Microsoft Azure Active Directory (Azure AD) tenant named contoso.onmicrosoft.com.You recently configured the forest to sync to the Azure AD tenant.
You add and then verify adatum.com as an additional domain name.
All servers run Windows Server 2016.
All desktop computers and laptops run Windows 10 Enterprise and are joined to contoso.com.
All the mobile devices in the Montreal and Seattle offices run Android. All the mobile devices in the New York office run iOS.
Contoso has the users shown in the following table.

MS-100 Microsoft 365 Identity and Services Part 11 Q02 138 Contoso has the groups shown in the following table.
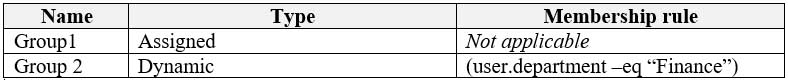
MS-100 Microsoft 365 Identity and Services Part 11 Q02 139 Microsoft Office 365 licenses are assigned only to Group2.
The network also contains external users from a vendor company who have Microsoft accounts that use a suffix of @outlook.com.
Requirements
Planned Changes
Contoso plans to provide email addresses for all the users in the following domains:– East.adatum.com
– Contoso.adatum.com
– Humongousinsurance.comTechnical Requirements
Contoso identifies the following technical requirements:– All new users must be assigned Office 365 licenses automatically.
– The principle of least privilege must be used whenever possible.Security Requirements
Contoso identifies the following security requirements:– Vendors must be able to authenticate by using their Microsoft account when accessing Contoso resources.
– User2 must be able to view reports and schedule the email delivery of security and compliance reports.
– The members of Group1 must be required to answer a security question before changing their password.
– User3 must be able to manage Office 365 connectors.
– User4 must be able to reset User3 password.-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You need to assign User2 the required roles to meet the security requirements.
Solution: From the Office 365 admin center, you assign User2 the Security Reader role. From the Exchange admin center, you assign User2 the Compliance Management role.
Does this meet the goal?
- Yes
- No
Explanation:– User2 must be able to view reports and schedule the email delivery of security and compliance reports.
The Security Reader role can view reports.
The Compliance Management role can schedule the email delivery of security and compliance reports. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You need to assign User2 the required roles to meet the security requirements.
Solution: From the Office 365 admin center, you assign User2 the Security Administrator role. From the Exchange admin center, you add User2 to the View-Only Organization Management role.
Does this meet the goal?
- Yes
- No
Explanation:– User2 must be able to view reports and schedule the email delivery of security and compliance reports.
The Security Administrator role can view reports but not schedule the email delivery of security and compliance reports.
The View-Only Organization Management role cannot schedule the email delivery of security and compliance reports. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You need to assign User2 the required roles to meet the security requirements.
Solution: From the Office 365 admin center, you assign User2 the Security Reader role. From the Exchange admin center, you assign User2 the Help Desk role.
Does this meet the goal?
- Yes
- No
Explanation:– User2 must be able to view reports and schedule the email delivery of security and compliance reports.
The Security Reader role can view reports but not schedule the email delivery of security and compliance reports.
The Help Desk role cannot schedule the email delivery of security and compliance reports. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You need to assign User2 the required roles to meet the security requirements.
Solution: From the Office 365 admin center, you assign User2 the Records Management role. From the Exchange admin center, you assign User2 the Help Desk role.
Does this meet the goal?
- Yes
- No
Explanation:– User2 must be able to view reports and schedule the email delivery of security and compliance reports.
The Records Management role cannot view reports or schedule the email delivery of security and compliance reports.
The Help Desk role cannot schedule the email delivery of security and compliance reports. -
HOTSPOT
You need to meet the technical requirements for the user licenses.
Which two properties should you configure for each user? To answer, select the appropriate properties in the answer area.
NOTE: Each correct selection is worth one point.
MS-100 Microsoft 365 Identity and Services Part 11 Q02 140 Question 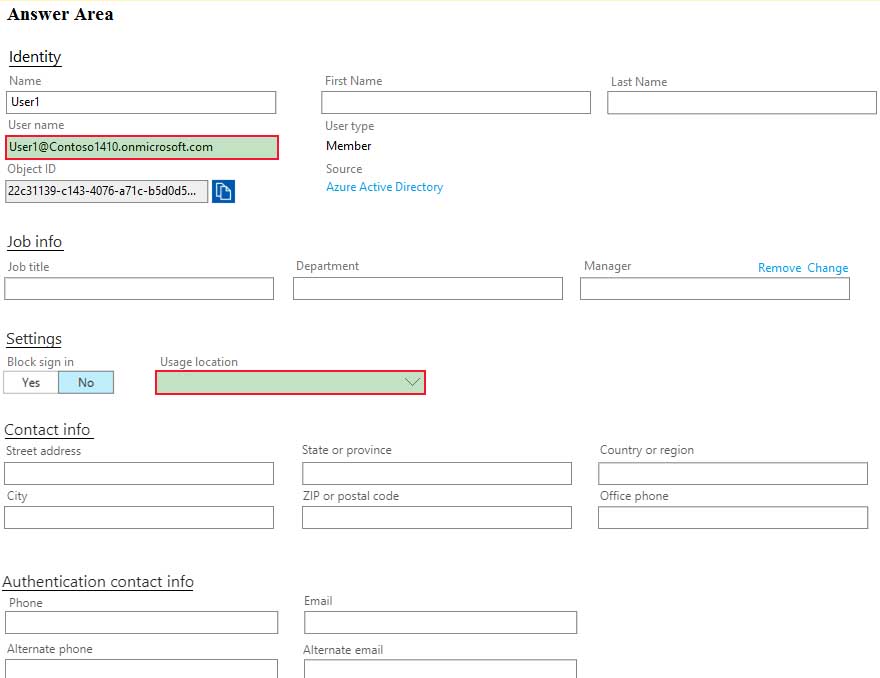
MS-100 Microsoft 365 Identity and Services Part 11 Q02 140 Answer Explanation:– All new users must be assigned Office 365 licenses automatically.
To enable Microsoft 365 license assignment, the users must have a username. This is also the UPN. The users must also have a Usage Location.
-
To which Azure AD role should you add User4 to meet the security requirement?
- Password administrator
- Global administrator
- Security administrator
- Privileged role administrator
Explanation:– User4 must be able to reset User3 password.
User3 is assigned the Customer Lockbox Access Approver role. Only global admins can reset the passwords of people assigned to this role as it’s considered a privileged role.
-
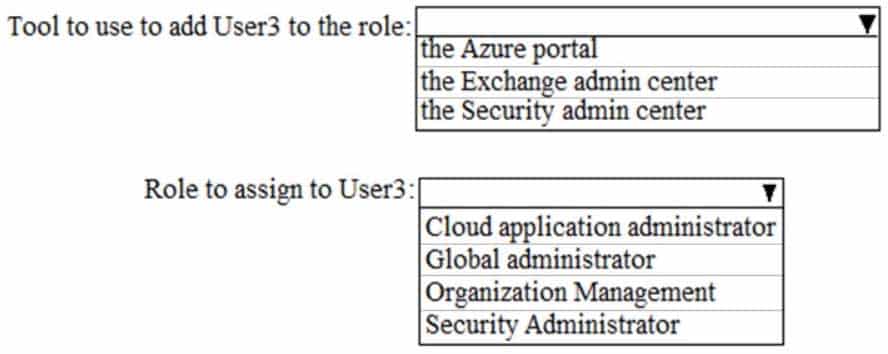
HOTSPOT
You need to meet the security requirements for User3. The solution must meet the technical requirements.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
MS-100 Microsoft 365 Identity and Services Part 11 Q02 141 Question 
MS-100 Microsoft 365 Identity and Services Part 11 Q02 141 Answer Explanation:– User3 must be able to manage Office 365 connectors.
– The principle of least privilege must be used whenever possible.Office 365 connectors are configured in the Exchange Admin Center.
You need to assign User3 the Organization Management role to enable User3 to manage Office 365 connectors.
A Global Admin could manage Office 365 connectors but the Organization Management role has less privilege. -
You need to assign User2 the required roles to meet the security requirements and the technical requirements.
To which two roles should you assign User2? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- the Exchange View-only Organization Management role
- the Microsoft 365 Records Management role
- the Exchange Online Help Desk role
- the Microsoft 365 Security Reader role
- the Exchange Online Compliance Management role
Explanation:– User2 must be able to view reports and schedule the email delivery of security and compliance reports.
The Security Reader role can view reports but not schedule the email delivery of security and compliance reports.
The Exchange Online Compliance Management role can schedule the email delivery of security and compliance reports.
-
-
Case study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.Overview
Fabrikam, Inc. is an electronics company that produces consumer products. Fabrikam has 10,000 employees worldwide.
Fabrikam has a main office in London and branch offices in major cities in Europe, Asia, and the United States.
Existing Environment
Active Directory Environment
The network contains an Active Directory forest named fabrikam.com. The forest contains all the identities used for user and computer authentication.Each department is represented by a top-level organizational unit (OU) that contains several child OUs for user accounts and computer accounts.
All users authenticate to on-premises applications by signing in to their device by using a UPN format of [email protected].
Fabrikam does NOT plan to implement identity federation.
Network Infrastructure
Each office has a high-speed connection to the Internet.
Each office contains two domain controllers. All domain controllers are configured as a DNS server.
The public zone for fabrikam.com is managed by an external DNS server.
All users connect to an on-premises Microsoft Exchange Server 2016 organization. The users access their email by using Outlook Anywhere, Outlook on the web, or the Microsoft Outlook app for iOS. All the Exchange servers have the latest cumulative updates installed.
All shared company documents are stored on a Microsoft SharePoint Server farm.
Requirements
Planned Changes
Fabrikam plans to implement a Microsoft 365 Enterprise subscription and move all email and shared documents to the subscription.Fabrikam plans to implement two pilot projects:
– Project1: During Project1, the mailboxes of 100 users in the sales department will be moved to Microsoft 365.
– Project2: After the successful completion of Project1, Microsoft Teams & Skype for Business will be enabled in Microsoft 365 for the sales department users.Fabrikam plans to create a group named UserLicenses that will manage the allocation of all Microsoft 365 bulk licenses.
Technical Requirements
Fabrikam identifies the following technical requirements:– All users must be able to exchange email messages successfully during Project1 by using their current email address.
– Users must be able to authenticate to cloud services if Active Directory becomes unavailable.
– A user named User1 must be able to view all DLP reports from the Microsoft 365 admin center.
– Microsoft 365 Apps for enterprise applications must be installed from a network share only.
– Disruptions to email access must be minimized.Application Requirements
Fabrikam identifies the following application requirements:– An on-premises web application named App1 must allow users to complete their expense reports online. App1 must be available to users from the My Apps portal.
– The installation of feature updates for Microsoft 365 Apps for enterprise must be minimized.Security Requirements
Fabrikam identifies the following security requirements:– After the planned migration to Microsoft 365, all users must continue to authenticate to their mailbox and to SharePoint sites by using their UPN.
– The memberships of UserLicenses must be validated monthly. Unused user accounts must be removed from the group automatically.
– After the planned migration to Microsoft 365, all users must be signed in to on-premises and cloud-based applications automatically.
– The principle of least privilege must be used.-
HOTSPOT
You need to create the UserLicenses group. The solution must meet the security requirements.
Which group type and control method should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MS-100 Microsoft 365 Identity and Services Part 11 Q03 142 Question 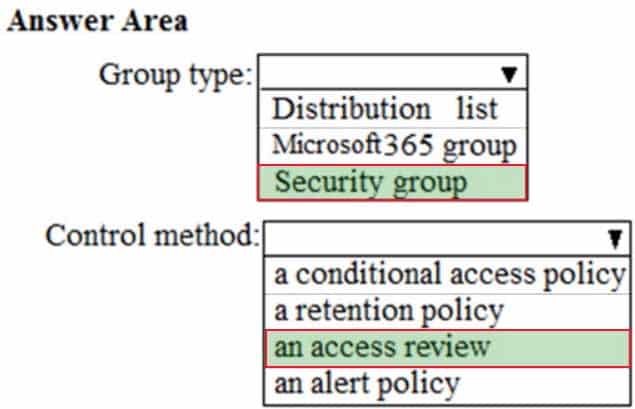
MS-100 Microsoft 365 Identity and Services Part 11 Q03 142 Answer Explanation:Fabrikam plans to create a group named UserLicenses that will manage the allocation of all Microsoft 365 bulk licenses.
The memberships of UserLicenses must be validated monthly. Unused user accounts must be removed from the group automatically.The group needs to be a Security group.
Azure Active Directory (Azure AD) access reviews enable organizations to efficiently manage group memberships, access to enterprise applications, and role assignments. User’s access can be reviewed on a regular basis to make sure only the right people have continued access. -
Which role should you assign to User1?
- Security Administrator
- Records Management
- Security Reader
- Hygiene Management
Explanation:– A user named User1 must be able to view all DLP reports from the Microsoft 365 admin center.
Users with the Security Reader role have global read-only access on security-related features, including all information in Microsoft 365 security center, Azure Active Directory, Identity Protection, Privileged Identity Management, as well as the ability to read Azure Active Directory sign-in reports and audit logs, and in Office 365 Security & Compliance Center.
-
-
Case study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.Overview
General Overview
Litware, Inc. is a consulting company that has a main office in Montreal and a branch office in Seattle.
Litware collaborates with a third-party company named ADatum Corporation.
Environment
On-Premises Environment
The network of Litware contains an Active Directory domain named litware.com. The domain contains three organizational units (OUs) named LitwareAdmins, Montreal Users, and Seattle Users and the users shown in the following table.

MS-100 Microsoft 365 Identity and Services Part 11 Q04 143 The domain contains 2,000 Windows 10 Pro devices and 100 servers that run Windows Server 2019.
Cloud environment
Litware has a pilot Microsoft 365 subscription that includes Microsoft Office 365 Enterprise E3 licenses and Azure Active Directory Premium Plan 2 licenses.
The subscription contains a verified DNS domain named litware.com.
Azure AD Connect is installed and has the following configurations:
Password hash synchronization is enabled.
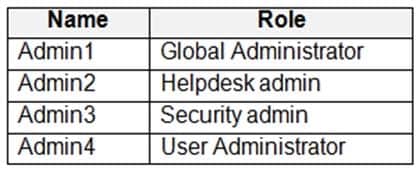
Synchronization is enabled for the LitwareAdmins OU only.Users are assigned the roles shown in the following table.
MS-100 Microsoft 365 Identity and Services Part 11 Q04 144 Self-service password reset (SSPR) is enabled.
The Azure Active Directory (Azure AD) tenant has Security defaults enabled.
Requirements
Planned Changes
Litware identifies the following issues:
– Admin1 cannot create conditional access policies.
– Admin4 receives an error when attempting to use SSPR.
– Users access new Office 365 service and feature updates before the updates are reviewed by Admin2.Technical Requirements
Litware plans to implement the following changes:
– Implement Microsoft Intune.
– Implement Microsoft Teams.
– Implement Microsoft Defender for Office 365.
– Ensure that users can install Office 365 apps on their device.
– Convert all the Windows 10 Pro devices to Windows 10 Enterprise E5.
– Configure Azure AD Connect to sync the Montreal Users OU and the Seattle Users OU.-
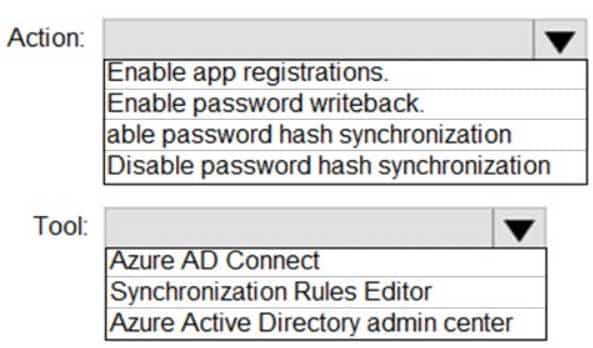
HOTSPOT
You need to ensure that Admin4 can use SSPR.
Which tool should you use, and which action should you perform? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
MS-100 Microsoft 365 Identity and Services Part 11 Q04 145 Question 
MS-100 Microsoft 365 Identity and Services Part 11 Q04 145 Answer
-
-
HOTSPOT
You have a Microsoft 365 subscription that contains a guest user named User1. User1 is assigned the User administrator role.
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com. Contoso.com is configured as shown in the following exhibit.
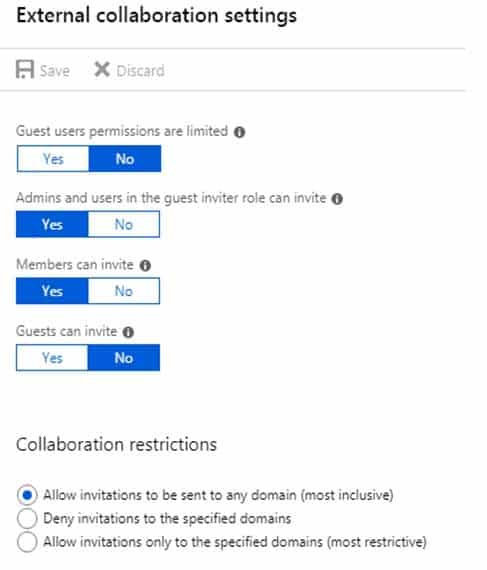
MS-100 Microsoft 365 Identity and Services Part 11 Q05 146 Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
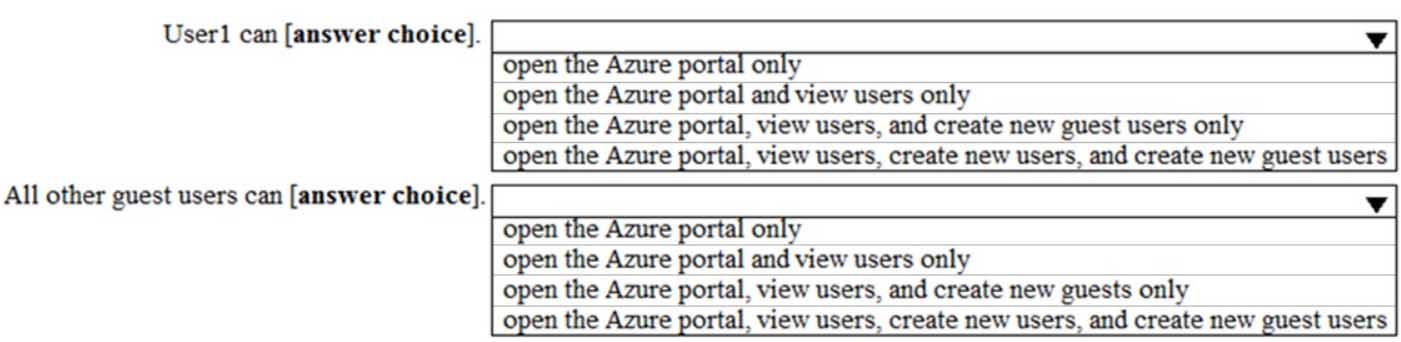
MS-100 Microsoft 365 Identity and Services Part 11 Q05 147 Question 
MS-100 Microsoft 365 Identity and Services Part 11 Q05 147 Answer Explanation:Default permissions for guests are restrictive by default. Guests can be added to administrator roles, which grant them full read and write permissions contained in the role. There is one additional restriction available, the ability for guests to invite other guests. Setting Guests can invite to No prevents guests from inviting other guests.
User1 is assigned the User Administrator role. Therefore, User1 can open the Azure portal, view users, create new users, and create new guest users.
In the exhibit, the ‘Guest user permissions are limited’ is set to no. This means that guest users have the same permissions as members. However, the ‘Guests can invite’ setting is set to No. Therefore, other guest users (all guest users except User1) can open the Azure portal and view users in the same way as member users can.
-
You have a Microsoft 365 subscription and a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
Contoso.com is configured as shown in the following exhibit.
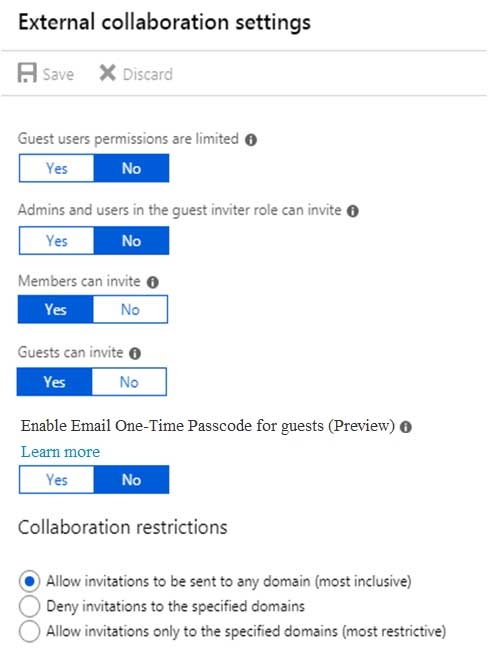
MS-100 Microsoft 365 Identity and Services Part 11 Q06 148 You need to ensure that guest users can be created in the tenant.
Which setting should you modify?
- Guests can invite.
- Guest users permissions are limited.
- Members can invite.
- Admins and users in the guest inviter role can invite.
- Deny invitations to the specified domains.
Explanation:
The setting “Admins and users in the guest inviter role can invite” is set to No. This means that no one can create guest accounts because they cannot ‘invite’ guests. This setting needs to be changed to Yes to ensure that guest users can be created in the tenant. -
Your company recently purchased a Microsoft 365 subscription.
You enable Microsoft Azure Multi-Factor Authentication (MFA) for all 500 users in the Azure Active Directory (Azure AD) tenant.
You need to generate a report that lists all the users who completed the Azure MFA registration process.
What is the best approach to achieve the goal? More than one answer choice may achieve the goal. Select the BEST answer.
- From Azure Cloud Shell, run the Get-AzureADUser cmdlet.
- From Azure Cloud Shell, run the Get-MsolUser cmdlet.
- From the Azure Active Directory admin center, use the Usage & insights blade.
- From the Azure Active Directory admin center, use the Risky sign-ins blade.
Explanation:You can use the Get-MsolUser cmdlet to generate a report that lists all the users who completed the Azure MFA registration process. The full command would look like this:
Get-MsolUser -All | Where-Object {$_.StrongAuthenticationMethods.Count -eq 0} | Select-Object -Property UserPrincipalName
-
You have a Microsoft 365 Enterprise subscription.
You have a conditional access policy to force multi-factor authentication when accessing Microsoft SharePoint from a mobile device.
You need to view which users authenticated by using multi-factor authentication.
What should you do?
- From the Microsoft 365 admin center, view the Security & Compliance reports.
- From the Azure Active Directory admin center, view the user sign-ins.
- From the Microsoft 365 admin center, view the Usage reports.
- From the Azure Active Directory admin center, view the audit logs.
Explanation:
With the sign-ins activity report in the Azure portal, you can get the information you need to determine how your environment is doing.
The sign-ins report can provide you with information about the usage of managed applications and user sign-in activities, which includes information about multi-factor authentication (MFA) usage. The MFA data gives you insights into how MFA is working in your organization. It enables you to answer questions like:
– Was the sign-in challenged with MFA?
– How did the user complete MFA?
– Why was the user unable to complete MFA?
– How many users are challenged for MFA?
– How many users are unable to complete the MFA challenge?
– What are the common MFA issues end users are running into? -
You have a Microsoft 365 Enterprise E5 subscription.
You need to enforce multi-factor authentication on all cloud-based applications for the users in the finance department.
What should you do?
- Create a sign-in risk policy.
- Create a new app registration.
- Assign an Enterprise Mobility + Security E5 license to the finance department users.
- Configure the sign-in status for the user accounts of the finance department users.
Explanation:You can configure a sign-in risk policy that applies to the Finance department users. The policy can be configured to ‘Allow access’ but with multi-factor authentication as a requirement.
Note:
There are several versions of this question in the exam. The question has two possible correct answers:
1. Create a sign-in risk policy.
2. Create a conditional access policy.Other incorrect answer options you may see on the exam include the following:
1. Create an activity policy.
2. Create a session policy.
3. Create an app permission policy.
4. Configure the sign-in status for the user accounts of the finance department users.
5. Assign an Enterprise Mobility + Security E5 license to the finance department users. -
Your network contains an on-premises Active Directory domain named contoso.local. The domain contains five domain controllers.
Your company purchases Microsoft 365 and creates a Microsoft Azure Active Directory (Azure AD) tenant named contoso.onmicrosoft.com.
You plan to install Azure AD connect on a member server and implement pass-through authentication.
You need to prepare the environment for the planned implementation of pass-through authentication.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Modify the email address attribute for each user account.
- From the Azure portal, add a custom domain name.
- From Active Directory Domains and Trusts, add a UPN suffix.
- Modify the User logon name for each user account.
- From the Azure portal, configure an authentication method.
- From a domain controller, install an Authentication Agent.
Explanation:The on-premise Active Directory domain is named contoso.local. Before you can configure Azure AD Connect, you need to purchase a routable domain, for example, contoso.com.
You then need to add the domain contoso.com to Microsoft as a custom domain name.The user accounts in the Active Directory domain need to be configured to use the domain name contoso.com as a UPN suffix. You need to add contoso.com to the Active Directory first by using Active Directory Domains and Trusts to add contoso.com add a UPN suffix. You can then configure each account to use the new UPN suffix.
An Authentication Agent is required on a domain controller to perform the authentication when pass-through authentication is used. When the custom domain and user accounts are configured, you can install and configure Azure AD Connect. An Authentication Agent is installed when you select the pass-through authentication option in the Azure AD Connect configuration or you can install the Authentication Agent manually.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company plans to deploy several Microsoft Office 365 services.
You need to design an authentication strategy for the planned deployment. The solution must meet the following requirements:
– Users must be able to authenticate during business hours only.
– Authentication requests must be processed successfully if a single server fails.
– When the password for an on-premises user account expires, the new password must be enforced the next time the user signs in.
– Users who connect to Office 365 services from domain-joined devices that are connected to the internal network must be signed in automatically.Solution: You design an authentication strategy that contains a pass-through authentication model. The solution contains two servers that have an Authentication Agent installed and password hash synchronization configured.
Does this meet the goal?
- Yes
- No
Explanation:This solution meets the following goals:
– Users must be able to authenticate during business hours only.
– Authentication requests must be processed successfully if a single server fails.
– When the password for an on-premises user account expires, the new password must be enforced the next time the user signs in.However, the following goal is not met:
– Users who connect to Office 365 services from domain-joined devices that are connected to the internal network must be signed in automatically.You would need to configure Single-sign on (SSO) to meet the last requirement.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company plans to deploy several Microsoft Office 365 services.
You need to design an authentication strategy for the planned deployment. The solution must meet the following requirements:
– Users must be able to authenticate during business hours only.
– Authentication requests must be processed successfully if a single server fails.
– When the password for an on-premises user account expires, the new password must be enforced the next time the user signs in.
– Users who connect to Office 365 services from domain-joined devices that are connected to the internal network must be signed in automatically.Solution: You design an authentication strategy that contains a pass-through authentication model. You install an Authentication Agent on three servers and configure seamless SSO.
Does this meet the goal?
- Yes
- No
Explanation:
This solution meets all the requirements:
– Users must be able to authenticate during business hours only. (This can be configured by using Logon Hours in Active Directory. Pass-through authentication passes authentication to the on-premise Active Directory)
– Authentication requests must be processed successfully if a single server fails. (We have Authentication Agents running on three servers)
– When the password for an on-premises user account expires, the new password must be enforced the next time the user signs in. (This can be configured in Active Directory. Pass-through authentication passes authentication to the on-premise Active Directory)
– Users who connect to Office 365 services from domain-joined devices that are connected to the internal network must be signed in automatically. (This goal is met by seamless SSO) -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company plans to deploy several Microsoft Office 365 services.
You need to design an authentication strategy for the planned deployment. The solution must meet the following requirements:
– Users must be able to authenticate during business hours only.
– Authentication requests must be processed successfully if a single server fails.
– When the password for an on-premises user account expires, the new password must be enforced the next time the user signs in.
– Users who connect to Office 365 services from domain-joined devices that are connected to the internal network must be signed in automatically.Solution: You design an authentication strategy that uses password hash synchronization and seamless SSO. The solution contains two servers that have an Authentication Agent installed.
Does this meet the goal?
- Yes
- No
Explanation:This solution meets the following requirements:
– Users who connect to Office 365 services from domain-joined devices that are connected to the internal network must be signed in automatically.
– Authentication requests must be processed successfully if a single server fails.The following requirements are not met:
– Users must be able to authenticate during business hours only.
– When the password for an on-premises user account expires, the new password must be enforced the next time the user signs in.To meet these two requirements, you would have to configure pass-through authentication.
-
HOTSPOT
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.
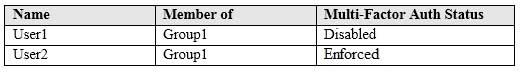
MS-100 Microsoft 365 Identity and Services Part 11 Q14 149 Multi-factor authentication (MFA) is configured to use 131.107.5.0/24 as trusted IPs.
The tenant contains the named locations shown in the following table.

MS-100 Microsoft 365 Identity and Services Part 11 Q14 150 You create a conditional access policy that has the following configurations:
Users and groups assignment: All users
Cloud apps assignment: App1
Conditions: Include all trusted locations
Grant access: Require multi-factor authenticationFor each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MS-100 Microsoft 365 Identity and Services Part 11 Q14 151 Question 
MS-100 Microsoft 365 Identity and Services Part 11 Q14 151 Answer Explanation:Box 1: Yes
131.107.50.10 is in a Trusted Location so the conditional access policy applies. The policy requires MFA. However, User1’s MFA status is disabled. The MFA requirement in the conditional access policy will override the user’s MFA status of disabled. Therefore, User1 must use MFA.Box 2: Yes.
131.107.20.15 is in a Trusted Location so the conditional access policy applies. The policy requires MFA so User2 must use MFA.Box 3: Yes.
131.107.5.5 is an MFA Trusted IP so that counts as a Trusted Location in the conditional access policy. The “All Trusted Locations” setting includes MFA Trusted IPs. Therefore, the conditional access policy applies so User2 must use MFA. -
You have a Microsoft 365 Enterprise E5 subscription.
You need to enforce multi-factor authentication on all cloud-based applications for the users in the finance department.
What should you do?
- Create an activity policy.
- Create a new app registration.
- Create a conditional access policy.
- Create a session policy.
Explanation:You can configure a conditional access policy that applies to the Finance department users. The policy can be configured to ‘Allow access’ but with multi-factor authentication as a requirement.
The reference below explains how to create a conditional access policy that requires MFA for all users. To apply the policy to finance users only, you would select Users and Group in the Include section instead of All Users and then specify the finance department group.
Note:
There are several versions of this question in the exam. The question has two possible correct answers:
1. Create a sign-in risk policy.
2. Create a conditional access policy.Other incorrect answer options you may see on the exam include the following:
1. Create an activity policy.
2. Create a session policy.
3. Create an app permission policy.
4. Configure the sign-in status for the user accounts of the finance department users.
5. Assign an Enterprise Mobility + Security E5 license to the finance department users. -
You have a Microsoft 365 subscription.
Your company deploys an Active Directory Federation Services (AD FS) solution.
You need to configure the environment to audit AD FS user authentication.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- From all the AD FS servers, run auditpol.exe.
- From all the domain controllers, run the Set-AdminAuditLogConfig cmdlet and specify the –LogLevel parameter.
- On a domain controller, install Azure AD Connect Health for AD DS.
- From the Azure AD Connect server, run the Register-AzureADConnectHealthSyncAgent cmdlet.
- On an AD FS server, install Azure AD Connect Health for AD FS.
Explanation:
To audit AD FS user authentication, you need to install Azure AD Connect Health for AD FS. The agent should be installed on an AD FS server. After the installation, you need to register the agent by running the Register-AzureADConnectHealthSyncAgent cmdlet. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory forest.
You deploy Microsoft 365.
You plan to implement directory synchronization.
You need to recommend a security solution for the synchronized identities. The solution must meet the following requirements:
– Users must be able to authenticate successfully to Microsoft 365 services if Active Directory becomes unavailable.
– User passwords must be 10 characters or more.Solution: Implement password hash synchronization and configure password protection in the Azure AD tenant.
Does this meet the goal?
- Yes
- No
Explanation:This solution meets the following requirement:
– Users must be able to authenticate successfully to Microsoft 365 services if Active Directory becomes unavailable. (this is because the authentication is performed by Azure Active Directory).This solution does not meet the following requirement:
– Users passwords must be 10 characters or more.To meet this requirement, you would need to configure the Default Domain Policy in the on-premise Active Directory.
Azure Password Protection can prevent users from using passwords from a ‘banned password’ list but it cannot be configured to require that passwords must be 10 characters or more.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory forest.
You deploy Microsoft 365.
You plan to implement directory synchronization.
You need to recommend a security solution for the synchronized identities. The solution must meet the following requirements:
– Users must be able to authenticate successfully to Microsoft 365 services if Active Directory becomes unavailable.
– User passwords must be 10 characters or more.Solution: Implement pass-through authentication and modify the password settings from the Default Domain Policy in Active Directory.
Does this meet the goal?
- Yes
- No
Explanation:This solution does not meet the following requirement:
– Users must be able to authenticate successfully to Microsoft 365 services if Active Directory becomes unavailable.
This is because with pass-through authentication, the authentication is performed by the on-premise Active Directory.This solution does meet the following requirement:
– User passwords must be 10 characters or more.
Configuring the Default Domain Policy in the on-premise Active Directory meets the requirement. -
You have a Microsoft 365 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com.
A temporary employee at your company uses an email address of [email protected].
You need to ensure that the temporary employee can sign in to contoso.com by using the [email protected] account.
What should you do?
- From the Azure Active Directory admin center, create a new user.
- From the Microsoft 365 admin center, create a new contact.
- From the Azure Active Directory admin center, create a new guest user.
- From the Microsoft 365 admin center, create a new user.
Explanation:
You can invite guest users to the directory, to a group, or to an application. After you invite a user through any of these methods, the invited user’s account is added to Azure Active Directory (Azure AD), with a user type of Guest. The guest user must then redeem their invitation to access resources. An invitation of a user does not expire.
The invitation will include a link to create a Microsoft account. The user can then authenticate using their Microsoft account. In this question, the external vendor already has a Microsoft account ([email protected]) so he can authenticate using that. -
Your company has an Azure Active Directory (Azure AD) tenant named contoso.com that contains 10,000 users.
The company has a Microsoft 365 subscription.
You enable Azure Multi-Factor Authentication (MFA) for all the users in contoso.com.
You run the following query.
search "SigninLogs" | where ResultDescription == "User did not pass the MFA challenge."
The query returns blank results.
You need to ensure that the query returns the expected results.
What should you do?
- From the Azure Active Directory admin center, configure the diagnostics settings to archive logs to an Azure Storage account.
- From the Security & Compliance admin center, turn on auditing.
- From the Security & Compliance admin center, enable Office 365 Analytics.
- From the Azure Active Directory admin center, configure the diagnostics settings to send logs to an Azure Log Analytics workspace.
Explanation:
You can now send audit logs to Azure Log Analytics. This gives you much easier reporting on audit events and the ability to perform queries such as the one in this question.