MS-500 : Microsoft 365 Security Administration : Part 07
-
You have a Microsoft 365 subscription.
You need to create data loss prevention (DLP) queries in Microsoft SharePoint Online to find sensitive data stored in sites.
Which type of site collection should you create first?
- Records Center
- eDiscovery Center
- Enterprise Search Center
- Document Center
-
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and two branch offices in Seattle and New York.
The company has the offices shown in the following table.
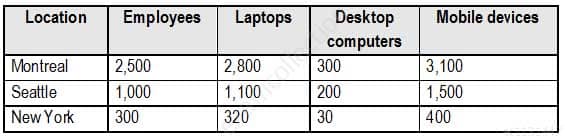
MS-500 Microsoft 365 Security Administration Part 07 Q02 144 Contoso has IT, human resources (HR), legal, marketing, and finance departments. Contoso uses Microsoft 365.
Existing Environment
Infrastructure
The network contains an Active Directory domain named contoso.com that is synced to a Microsoft Azure Active Directory (Azure AD) tenant. Password writeback is enabled.
The domain contains servers that run Windows Server 2016. The domain contains laptops and desktop computers that run Windows 10 Enterprise.
Each client computer has a single volume.
Each office connects to the Internet by using a NAT device. The offices have the IP addresses shown in the following table.
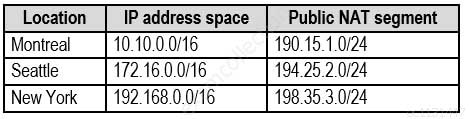
MS-500 Microsoft 365 Security Administration Part 07 Q02 145 Named locations are defined in Azure AD as shown in the following table.
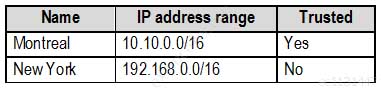
MS-500 Microsoft 365 Security Administration Part 07 Q02 146 From the Multi-Factor Authentication page, an address space of 198.35.3.0/24 is defined in the trusted IPs list.
Azure Multi-Factor Authentication (MFA) is enabled for the users in the finance department.
The tenant contains the users shown in the following table.
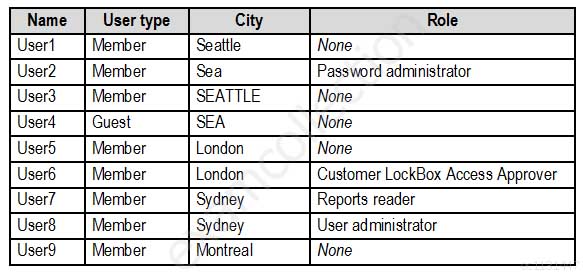
MS-500 Microsoft 365 Security Administration Part 07 Q02 147 The tenant contains the groups shown in the following table.
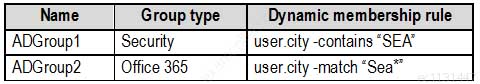
MS-500 Microsoft 365 Security Administration Part 07 Q02 148 Customer Lockbox is enabled in Microsoft 365.
Microsoft Endpoint Manager Configuration
The devices enrolled in Microsoft Endpoint Manager are configured as shown in the following table.
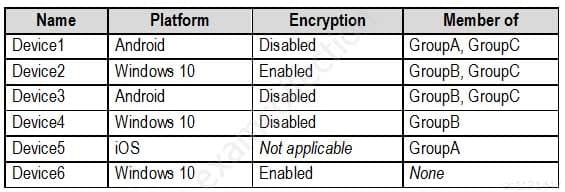
MS-500 Microsoft 365 Security Administration Part 07 Q02 149 The device compliance policies in Microsoft Endpoint Manager are configured as shown in the following table.
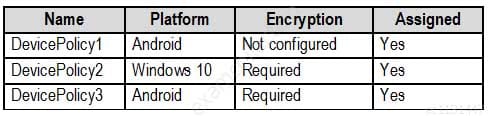
MS-500 Microsoft 365 Security Administration Part 07 Q02 150 The device compliance policies have the assignments shown in the following table.
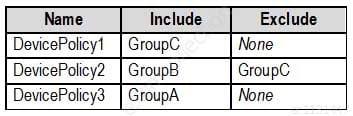
MS-500 Microsoft 365 Security Administration Part 07 Q02 151 The Mark devices with no compliance policy assigned as setting is set to Compliant.
Requirements
Technical Requirements
Contoso identifies the following technical requirements:
– Use the principle of least privilege
– Enable User1 to assign the Reports reader role to users
– Ensure that User6 approves Customer Lockbox requests as quickly as possible
– Ensure that User9 can enable and configure Azure AD Privileged Identity Management-
What should User6 use to meet the technical requirements?
- Supervision in the Security & Compliance admin center
- Service requests in the Microsoft 365 admin center
- Security & privacy in the Microsoft 365 admin center
- Data subject requests in the Security & Compliance admin center
-
-
You have a Microsoft 365 subscription.
The Global administrator role is assigned to your user account. You have a user named Admin1.
You create an eDiscovery case named Case1.
You need to ensure that Admin1 can view the results of Case1.
What should you do first?
- From the Azure Active Directory admin center, assign a role group to Admin1.
- From the Microsoft 365 admin center, assign a role to Admin1.
- From the Security & Compliance admin center, assign a role group to Admin1.
-
HOTSPOT
You have a Microsoft 365 subscription. From the Security & Compliance admin center, you create the retention policies shown in the following table.

MS-500 Microsoft 365 Security Administration Part 07 Q04 152 Policy1 if configured as showing in the following exhibit.
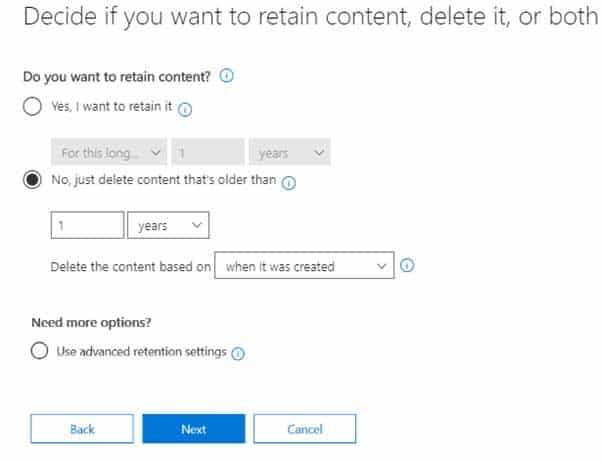
MS-500 Microsoft 365 Security Administration Part 07 Q04 153 Policy2 is configured as shown in the following exhibit.
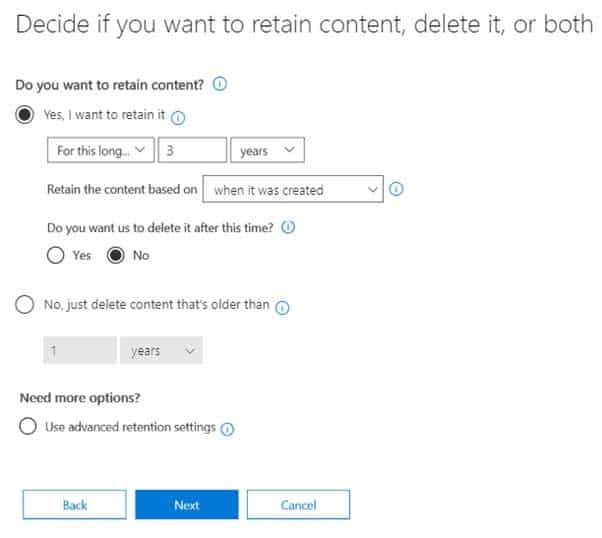
MS-500 Microsoft 365 Security Administration Part 07 Q04 154 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
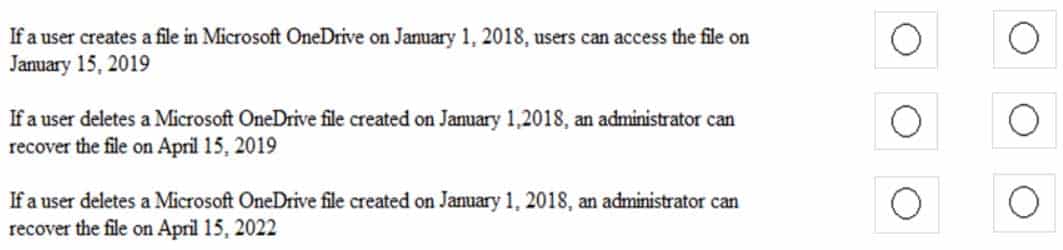
MS-500 Microsoft 365 Security Administration Part 07 Q04 155 Question 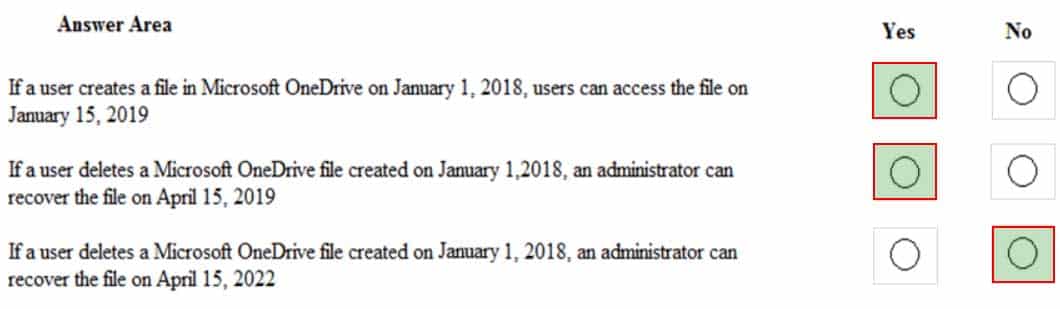
MS-500 Microsoft 365 Security Administration Part 07 Q04 155 Answer Explanation:Policy2 is in effect as it has the longer retention period.
-
You have a Microsoft 365 subscription.
You need to enable auditing for all Microsoft Exchange Online users.
What should you do?
- From the Exchange admin center, create a journal rule
- Run the Set-MailboxDatabase cmdlet
- Run the Set-Mailbox cmdlet
- From the Exchange admin center, create a mail flow message trace rule.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription that contains 1,000 user mailboxes.
An administrator named Admin1 must be able to search for the name of a competing company in the mailbox of a user named User5.
You need to ensure that Admin1 can search the mailbox of User5 successfully. The solution must prevent Admin1 from sending email messages as User5.
Solution: You modify the permissions of the mailbox of User5, and then create an eDiscovery case.
Does this meet the goal?
- Yes
- No
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription that contains 1,000 user mailboxes.
An administrator named Admin1 must be able to search for the name of a competing company in the mailbox of a user named User5.
You need to ensure that Admin1 can search the mailbox of User5 successfully. The solution must prevent Admin1 from sending email messages as User5.
Solution: You start a message trace, and then create a Data Subject Request (DSR) case.
Does this meet the goal?
- Yes
- No
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription that contains 1,000 user mailboxes.
An administrator named Admin1 must be able to search for the name of a competing company in the mailbox of a user named User5.
You need to ensure that Admin1 can search the mailbox of User5 successfully. The solution must prevent Admin1 from sending email messages as User5.
Solution: You assign the eDiscovery Manager role to Admin1, and then create an eDiscovery case.
Does this meet the goal?
- Yes
- No
-
SIMULATION
You need to ensure that all the email messages in the mailbox of a user named Allan Deyoung are retained for a period of 90 days, even if the messages are deleted.
To complete this task, sign in to the Microsoft 365 admin center.
- See explanation below.
Explanation:1. Navigate to the Exchange Admin Center
2. Navigate to Compliance management > Retention tags, and then click Add +
3. Select the Applied automatically to entire mailbox (default) option.
4. The New retention tag page title and options will vary depending on the type of tag you selected. Complete the following fields:
Name: Enter a name for the retention tag.
Retention action: Select Delete and Allow Recovery option.
Retention period: Select When the item reaches the following age (in days) option.
Comment: User this optional field to enter any administrative notes or comments. The field isn’t displayed to users.
5. Navigate to Compliance management > Retention policies, and then click Add +
6. In New Retention Policy, complete the following fields:
Name: Enter a name for the retention policy.
Retention tags: Click Add + to select the tags you want to add to this retention policy.After you create a retention policy, you must apply it.
1. Navigate to Recipients > Mailboxes.
2. In the list view, select the mailbox to which you want to apply the retention policy, and then click Edit.
3. In User Mailbox, click Mailbox features.
4. In the Retention policy list, select the policy you want to apply to the mailbox, and then click Save. -
SIMULATION
You need to create a retention policy that contains a data label. The policy must delete all Microsoft Office 365 content that is older than six months.
To complete this task, sign in to the Microsoft 365 admin center.
- See explanation below.
Explanation:Creating Office 356 labels is a two-step process. The first step is to create the actual label which includes the name, description, retention policy, and classifying the content as a record. Once this is completed, the second step requires the deployment of a label using a labelling policy which specifies the specific location to publish and applying the label automatically.
To create an Office 365 label, following these steps:
1. Open Security and Compliance Centre;
2. Click on Classifications;
3. Click on Labels;
4. The label will require configuration including: name your label (Name), add a description for the admins (Description for Admins), add a description for the users (Description for Users);
5. Click Next once the configuration is completed;
6. Click Label Settings on the left-hand side menu;
7. The Label Settings will need to be configured. On this screen, you can toggle the Retention switch to either “on” or “off”. If you choose “on”, then you can answer the question “When this label is applied to content” with one of two options. The first option is to Retain the Content. From the pick boxes, you can choose the length of retention and upon the end of the retention, the action that will take place. The three actions are to delete the data, trigger an approval flow for review, or nothing can be actioned. The second option is to not retain the data after a specified amount of time or based on the age of the data; and
8. The label has now been created.To create a label policy, follow these steps:
1. Open Security and Compliance Centre;
2. Click on Data Governance, Retention;
3. Choose Label Policies box at the top of the screen; and
4. There are now two options. The first is to Publish Labels. If your organization wants its end users to apply the label manually, then this is the option you would choose. Note that this is location based. The second option is to Auto-apply Labels. With Auto-apply, you would have the ability to automatically apply a label when it meets the specified criteria. -
SIMULATION
You need to create an eDiscovery case that places a hold on the mailbox of a user named Allan Deyoung. The hold must retain email messages that have a subject containing the word merger or the word Contoso.
To complete this task, sign in to the Microsoft 365 admin center.
- See explanation below.
Explanation:Explanation:
1. Navigate to eDiscovery in the Security & Compliance Center, and then click Create a case.
2. On the New Case page, give the case a name, type an optional description, and then click Save. The case name must be unique in your organization.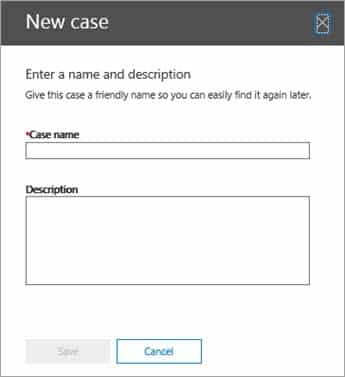
MS-500 Microsoft 365 Security Administration Part 07 Q11 156 The new case is displayed in the list of cases on the eDiscovery page. You can hover the cursor over a case name to display information about the case, including the status of the case (Active or Closed), the description of the case (that was created in the previous step), and when the case was changed last and who changed it.
To create a hold for an eDiscovery case:
1. In the Security & Compliance Center, click eDiscovery > eDiscovery to display the list of cases in your organization.
2. Click Open next to the case that you want to create the holds in.
3. On the Home page for the case, click the Hold tab.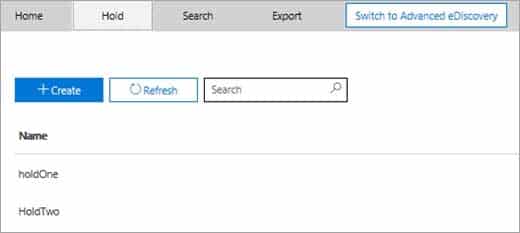
MS-500 Microsoft 365 Security Administration Part 07 Q11 157 4. On the Hold page, click Create.
5. On the Name your hold page, give the hold a name. The name of the hold must be unique in your organization.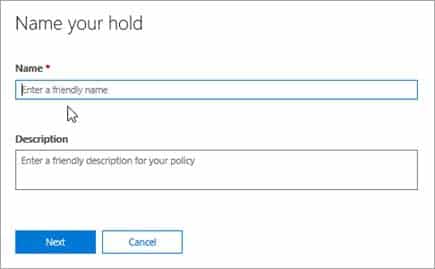
MS-500 Microsoft 365 Security Administration Part 07 Q11 158 6. (Optional) In the Description box, add a description of the hold.
7. Click Next.
8. Choose the content locations that you want to place on hold. You can place mailboxes, sites, and public folders on hold.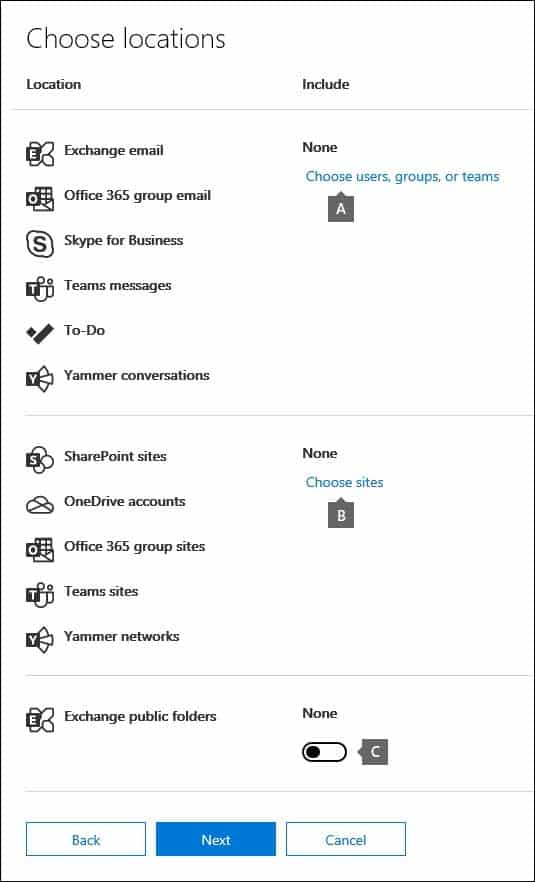
MS-500 Microsoft 365 Security Administration Part 07 Q11 159 – Exchange email – Click Choose users, groups, or teams and then click Choose users, groups, or teams again. to specify mailboxes to place on hold. Use the search box to find user mailboxes and distribution groups (to place a hold on the mailboxes of group members) to place on hold. You can also place a hold on the associated mailbox for a Microsoft Team, a Yammer Group, or an Office 365 Group. Select the user, group, team check box, click Choose, and then click Done.
Note
When you click Choose users, groups, or teams to specify mailboxes to place on hold, the mailbox picker that’s displayed is empty. This is by design to enhance performance. To add people to this list, type a name (a minimum of 3 characters) in the search box.9. After configuring a query-based hold, click Next.
10. Review your settings, and then click Create this hold. -
SIMULATION
You plan to create a script to automate user mailbox searches. The script will search the mailbox of a user named Allan Deyoung for messages that contain the word injunction.
You need to create the search that will be included in the script.
To complete this task, sign in to the Microsoft 365 admin center.
- See explanation below.
Explanation:Step 1: Create a CSV file that contains information about the searches you want to run
The comma separated value (CSV) file that you create in this step contains a row for each user that want to search. You can search the user’s Exchange Online mailbox (which includes the archive mailbox, if it’s enabled) and their OneDrive for Business site. Or you can search just the mailbox or the OneDrive for Business site. You can also search any site in your SharePoint Online organization. The script that you run in Step 3 will create a separate search for each row in the CSV file.
1. Copy and paste the following text into a .txt file using NotePad. Save this file to a folder on your local computer. You’ll save the other scripts to this folder as well.ExchangeLocation,SharePointLocation,ContentMatchQuery,StartDate,EndDate
[email protected],https://contoso-my.sharepoint.com/personal/sarad_contoso_onmicrosoft_com,(lawsuit OR legal),1/1/2000,12/31/2005
[email protected],https://contoso-my.sharepoint.com/personal/sarad_contoso_onmicrosoft_com,(lawsuit OR legal),1/1/2006,12/31/2010
[email protected],https://contoso-my.sharepoint.com/personal/sarad_contoso_onmicrosoft_com,(lawsuit OR legal),1/1/2011,3/21/2016
,https://contoso.sharepoint.com/sites/contoso,,,3/21/2016
,https://contoso-my.sharepoint.com/personal/davidl_contoso_onmicrosoft_com,,1/1/2015,
,https://contoso-my.sharepoint.com/personal/janets_contoso_onmicrosoft_com,,1/1/2015,The first row, or header row, of the file lists the parameters that will be used by New-Compliance Search cmdlet to create a new Content Searches. Each parameter name is separated by a comma. Make sure there aren’t any spaces in the header row. Each row under the header row represents the parameter values for each search. Be sure to replace the placeholder data in the CSV file with your actual data.
2. Open the .txt file in Excel, and then use the information in the following table to edit the file with information for each search.
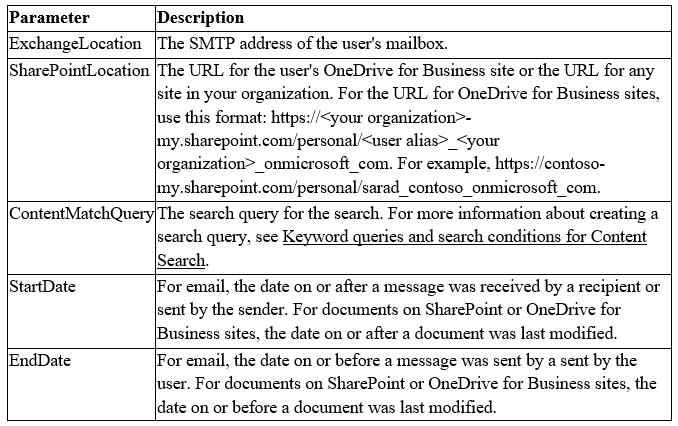
MS-500 Microsoft 365 Security Administration Part 07 Q12 160 3. Save the Excel file as a CSV file to a folder on your local computer. The script that you create in Step 3 will use the information in this CSV file to create the searches.
-
You have a Microsoft 365 subscription.
You create a supervision policy named Policy1, and you designate a user named User1 as the reviewer.
What should User1 use to view supervised communications?
- a team in Microsoft Teams
- the Security & Compliance admin center
- Outlook on the web
- the Exchange admin center
-
SIMULATION
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn’t matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
Username and password
MS-500 Microsoft 365 Security Administration Part 07 Q14 161 Use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Microsoft 365 Username:
[email protected]Microsoft 365 Password: &=Q8v@2qGzYz
If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab.
The following information is for technical support purposes only:
Lab instance: 11032396
You need to ensure that when users tag documents as classified, a classified watermark is applied to the documents.
To complete this task, sign in to the Microsoft Office 365 admin center.
- See explanation below.
Explanation:1. In the admin center, select the Compliance admin center.
2. Select Classification > Sensitivity labels.
3. Select Create a label, and when the warning appears, select Yes.
4. Enter a Label name, Tooltip, and Description. Select Next.
5. Turn on Encryption. Choose when you want to assign permissions, whether you want your users’ access to the content to expire, and whether you want to allow offline access.
6. Select Assign permissions > Add these email addresses or domains.
7. Enter an email address or domain name (such as Contoso.org). Select Add, and repeat for each email address or domain you want to add.
8. Select Choose permissions from preset or custom.
9. Use the drop-down list to select preset permissions, such as Reviewer or Viewer, or select Custom permissions. If you chose Custom, select the permissions from the list. Select Save >Save > Next.
10. Turn on Content marking, and choose the markings you want to use.
11. For each marking that you choose, select Customize text. Enter the text you want to appear on the document, and set the font and layout options. Select Save, and then repeat for any additional markings. Select Next.
12. Optionally, turn on Endpoint data loss prevention. Select Next.
13. Optionally, turn on Auto labeling. Add a condition. For example, under Detect content that contains, select Add a condition. Enter the condition; for example, add a condition that if passport, Social Security, or other sensitive information is detected, the label will be added. Select Next.
14. Review your settings, and select Create. Your label has been created. Repeat this process for any additional labels you want.
15. By default, labels appear in Office apps in this order: Confidential, Internal, and Public. To change the order, for each label, select More actions (the ellipsis), and then move the label up or down. Typically, permissions are listed from the lowest to highest level of permissions.
16. To add a sub-label to a label, select More actions, then Add sub level.
17. When finished, choose Publish labels> Choose labels to publish > Add. Select the labels you want to publish, and then select Add > Done > Next.
18. By default, the new label policy is applied to everyone. If you want to limit who the policy is applied to, select Choose users or groups > Add. Select who you want the policy to apply to, and then select Add > Done > Next.
19. If you want a default label for documents and email, select the label you want from the drop-down list. Review the remaining settings, adjust as needed, and then select Next.
20. Enter a Name and Description for your policy. Select Next.
21. Review your settings, then select Publish. -
SIMULATION
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn’t matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
Username and password
MS-500 Microsoft 365 Security Administration Part 07 Q15 162 Use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Microsoft 365 Username:
[email protected]Microsoft 365 Password: &=Q8v@2qGzYz
If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab.
The following information is for technical support purposes only:
Lab instance: 11032396
You need to ensure that email messages in Exchange Online and documents in SharePoint Online are retained for eight years.
To complete this task, sign in to the Microsoft Office 365 admin center.
- See explanation below.
Explanation:NB: For our purposes, the retention period will be 8 years.
For retaining email messages in Exchange Online:
Step 1: Create a retention tag
1. Navigate to the Exchange Admin Center
2. Navigate to Compliance management > Retention tags, and then click Add +
3. Select one of the following options:
– Applied automatically to entire mailbox (default): Select this option to create a default policy tag (DPT). You can use DPTs to create a default deletion policy and a default archive policy, which applies to all items in the mailbox.
– Applied automatically to a specific folder: Select this option to create a retention policy tag (RPT) for a default folder such as Inbox or Deleted Items.
– Applied by users to items and folders (Personal): Select this option to create personal tags. These tags allow Outlook and Outlook on the web (formerly known as Outlook Web App) users to apply archive or deletion settings to a message or folders that are different from the settings applied to the parent folder or the entire mailbox.
4. The New retention tag page title and options will vary depending on the type of tag you selected. Complete the following fields:
– Name: Enter a name for the retention tag. The tag name is for display purposes and doesn’t have any impact on the folder or item a tag is applied to. Consider that the personal tags you provision for users are available in Outlook and Outlook on the web.
– Apply this tag to the following default folder: This option is available only if you selected Applied automatically to a specific folder.
– Retention action: Select one of the following actions to be taken after the item reaches its retention period:
– Delete and Allow Recovery: Select this action to delete items but allow users to recover them using the Recover Deleted Items option in Outlook or Outlook on the web. Items are retained until the deleted item retention period configured for the mailbox database or the mailbox user is reached.
– Permanently Delete: Select this option to permanently delete the item from the mailbox database.
– Move to Archive: This action is available only if you’re creating a DPT or a personal tag. Select this action to move items to the user’s In-Place Archive.
– Retention period: Select one of the following options:
– Never: Select this option to specify that items should never be deleted or moved to the archive.
– When the item reaches the following age (in days): Select this option and specify the number of days to retain items before they’re moved or deleted. The retention age for all supported items except Calendar and Tasks is calculated from the date an item is received or created. Retention age for Calendar and Tasks items is calculated from the end date.
– Comment: User this optional field to enter any administrative notes or comments. The field isn’t displayed to users.Step 2: Create a retention policy
1. Navigate to Compliance management > Retention policies, and then click Add +
2. In New Retention Policy, complete the following fields:
– Name: Enter a name for the retention policy.
– Retention tags: Click Add + to select the tags you want to add to this retention policy.A retention policy can contain the following tags:
– One DPT with the Move to Archive action.
– One DPT with the Delete and Allow Recovery or Permanently Delete actions.
– One DPT for voice mail messages with the Delete and Allow Recovery or Permanently Delete actions.
– One RPT per default folder such as Inbox to delete items.
– Any number of personal tags.Step 3: Apply a retention policy to mailbox users
After you create a retention policy, you must apply it to mailbox users. You can apply different retention policies to different set of users.
1. Navigate to Recipients > Mailboxes.
2. In the list view, use the Shift or Ctrl keys to select multiple mailboxes.
3. In the details pane, click More options.
4. Under Retention Policy, click Update.
5. In Bulk Assign Retention Policy, select the retention policy you want to apply to the mailboxes, and then click Save.For retaining documents in SharePoint Online
Access Security & Compliance Admin Center
1. Navigate to the Office 365 Admin Centers
MS-500 Microsoft 365 Security Administration Part 07 Q15 163 2. From the list of available Admin Centers, click on Security & Compliance
MS-500 Microsoft 365 Security Administration Part 07 Q15 164 How to create and publish a Retention Policy on a SharePoint site
Now that we are in the Security & Compliance Admin Center, we are ready to create and publish a Retention Policy on a SharePoint site.
Under Data Governance, click Retention
MS-500 Microsoft 365 Security Administration Part 07 Q15 165 1. Hit Create button to create new Retention Policy
MS-500 Microsoft 365 Security Administration Part 07 Q15 166 2. Give your policy a name and description. Hit Next
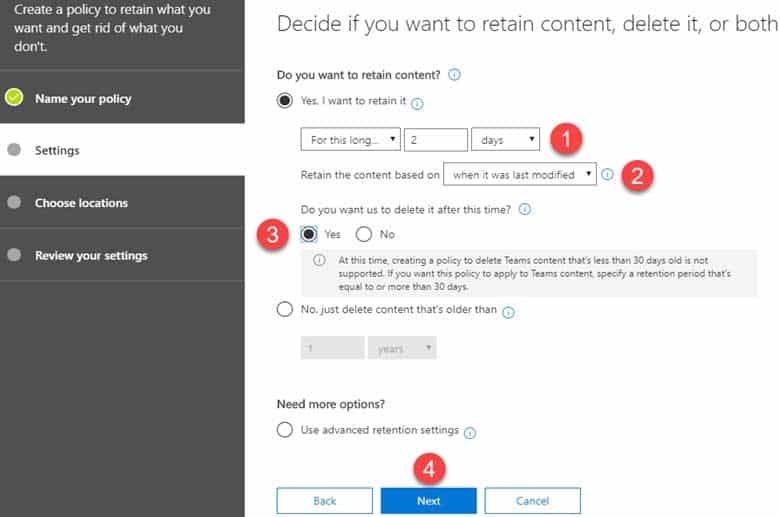
MS-500 Microsoft 365 Security Administration Part 07 Q15 167 3. On the next screen is where you set up the logic. You can configure how many days, months, or years to retain the content for, specify whether you want the math (retention period) to be calculated from the Created Date or Last Modified Date. Lastly, you can also specify whether you want to keep or delete content after the Retention period expires. Hit Next
MS-500 Microsoft 365 Security Administration Part 07 Q15 168 4. On the next screen, you get to choose where to apply the policy. You can apply it to email (Exchange), SharePoint sites, OneDrive accounts as well as Office 365 Groups.
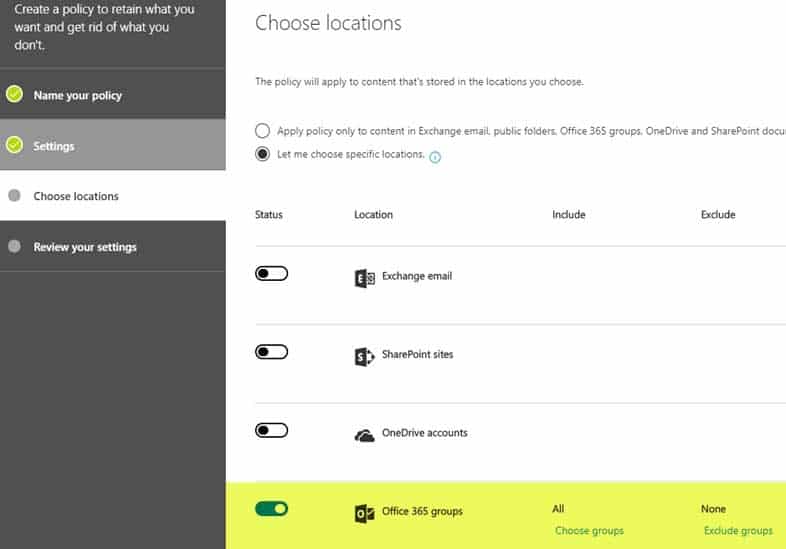
MS-500 Microsoft 365 Security Administration Part 07 Q15 169 5. In my case, I applied a policy to a single Office 365 Group Site
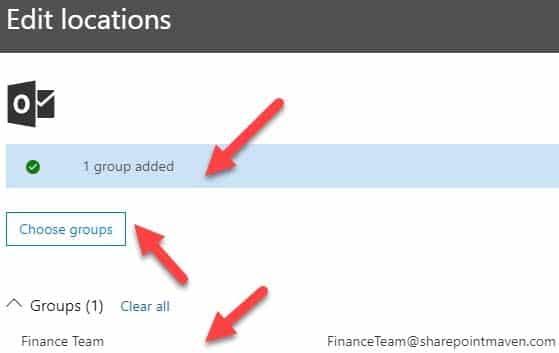
MS-500 Microsoft 365 Security Administration Part 07 Q15 170 6. On a final screen, you need to review and confirm the settings and click Create this policy button. It is imperative to note the message you get to see at the bottom. It warns you that content might be deleted as soon as the policy takes effect according to the logic you set up in previous steps.
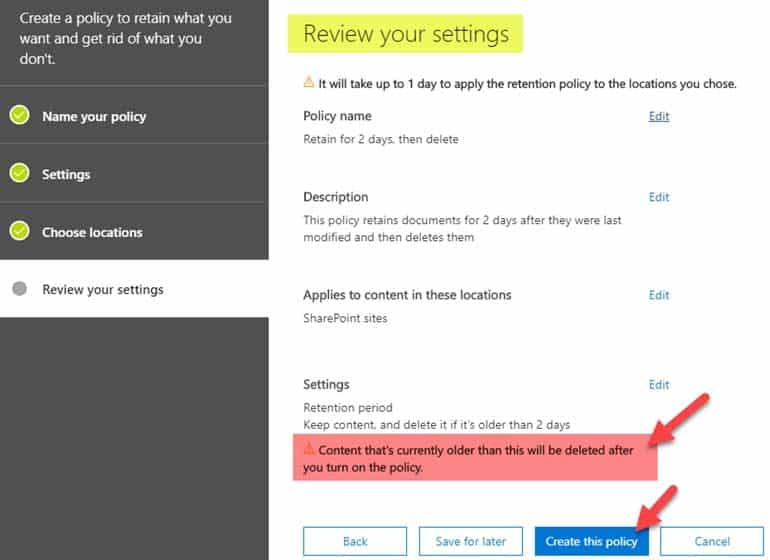
MS-500 Microsoft 365 Security Administration Part 07 Q15 171 -
SIMULATION
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn’t matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
Username and password
MS-500 Microsoft 365 Security Administration Part 07 Q16 172 Use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Microsoft 365 Username:
[email protected]Microsoft 365 Password: &=Q8v@2qGzYz
If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab.
The following information is for technical support purposes only:
Lab instance: 11032396
You need to ensure that [email protected] receives an alert when a user establishes a sync relationship to a document library from a computer that is a member of an Active Directory (AD) domain.
To complete this task, sign in to the Microsoft Office 365 admin center.
- See explanation below.
Explanation:1. Navigate to Manage Alerts in the Security & Compliance Center.
2. On the Activity alerts page, click + New.The flyout page to create an activity alert is displayed.
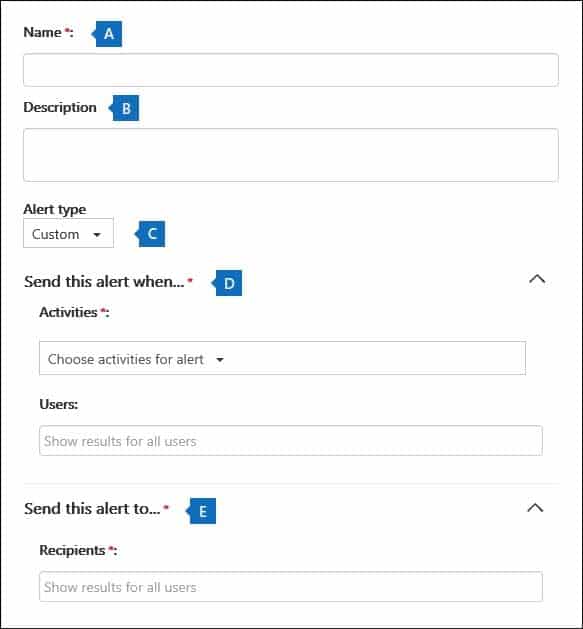
MS-500 Microsoft 365 Security Administration Part 07 Q16 173 3. Complete the following fields to create an activity alert:
a. Name – Type a name for the alert. Alert names must be unique within your organization.
b. Description (Optional) – Describe the alert, such as the activities and users being tracked, and the users that email notifications are sent to. Descriptions provide a quick and easy way to describe the purpose of the alert to other admins.
c. Alert type – Make sure the Custom option is selected.
d. Send this alert when – Click Send this alert when and then configure these two fields:
– Activities – Click the drop-down list to display the activities that you can create an alert for. This is the same activities list that’s displayed when you search the Office 365 audit log. You can select one or more specific activities or you can click the activity group name to select all activities in the group. For a description of these activities, see the “Audited activities” section in Search the audit log. When a user performs any of the activities that you’ve added to the alert, an email notification is sent.
– Users – Click this box and then select one or more users. If the users in this box perform the activities that you added to the Activities box, an alert will be sent. Leave the Users box blank to send an alert when any user in your organization performs the activities specified by the alert.
e. Send this alert to – Click Send this alert, and then click in the Recipients box and type a name to add a user’s who will receive an email notification when a user (specified in the Users box) performs an activity (specified in the Activities box). Note that you are added to the list of recipients by default. You can remove your name from this list.
4. Click Save to create the alert.The new alert is displayed in the list on the Activity alerts page.
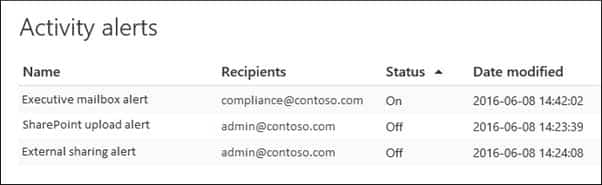
MS-500 Microsoft 365 Security Administration Part 07 Q16 174 The status of the alert is set to On. Note that the recipients who will receive an email notification when an alert is sent are also listed.
-
SIMULATION
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn’t matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
Username and password
MS-500 Microsoft 365 Security Administration Part 07 Q17 175 Use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Microsoft 365 Username:
[email protected]Microsoft 365 Password: &=Q8v@2qGzYz
If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab.
The following information is for technical support purposes only:
Lab instance: 11032396
You need to create a case that prevents the members of a group named Operations from deleting email messages that contain the word IPO.
To complete this task, sign in to the Microsoft Office 365 admin center.
- See explanation below.
Explanation:1. Navigate to the Security & Compliance Center.
2. In the Security & Compliance Center, click eDiscovery > eDiscovery, and then click Create a case.
3. On the New Case page, give the case a name, type an optional description, and then click Save. The case name must be unique in your organization.
MS-500 Microsoft 365 Security Administration Part 07 Q17 176 The new case is displayed in the list of cases on the eDiscovery page.
After you create a case, the next step is to add members to the case. The eDiscovery Manager who created the case is automatically added as a member. Members have to be assigned the appropriate eDiscovery permissions so they can access the case after you add them.
4. In the Security & Compliance Center, click eDiscovery > eDiscovery to display the list of cases in your organization.
5. Click the name of the case that you want to add members to.The Manage this case flyout page is displayed.
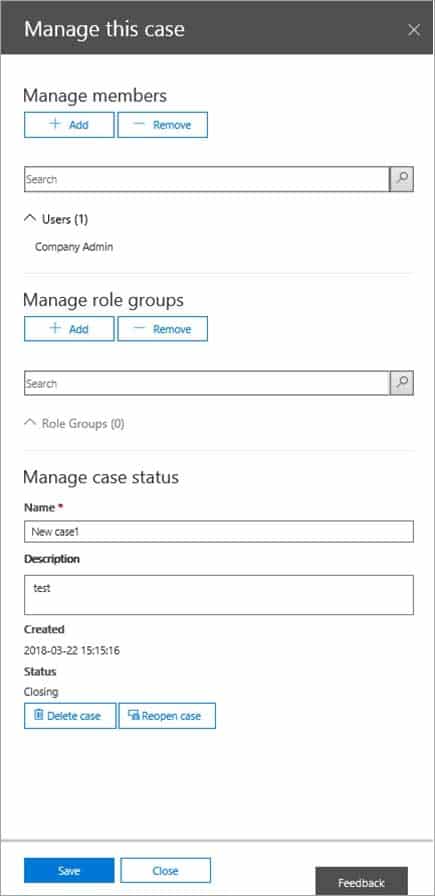
MS-500 Microsoft 365 Security Administration Part 07 Q17 177 6. Under Manage members, click Add to add members to the case.
You can also choose to add a role group to the case. Under Manage role groups, click Add.
7. In the list of people or role groups that can be added as members of the case, click the check box next to the names of the people or role groups that you want to add.
8. After you select the people or role groups to add as members of the group, click Add.
In Manage this case, click Save to save the new list of case members.
9. Click Save to save the new list of case members.You can use an eDiscovery case to create holds to preserve content that might be relevant to the case. You can place a hold on the mailboxes and OneDrive for Business sites of people who are custodians in the case. You can also place a hold on the group mailbox, SharePoint site, and OneDrive for Business site for an Office 365 Group. Similarly, you can place a hold on the mailboxes and sites that are associated with Microsoft Teams or Yammer Groups. When you place content locations on hold, content is held until you remove the hold from the content location or until you delete the hold.
To create a hold for an eDiscovery case:
1. In the Security & Compliance Center, click eDiscovery > eDiscovery to display the list of cases in your organization.
2. Click Open next to the case that you want to create the holds in.
3. On the Home page for the case, click the Hold tab.
MS-500 Microsoft 365 Security Administration Part 07 Q17 178 4. On the Hold page, click Create.
5. On the Name your hold page, give the hold a name. The name of the hold must be unique in your organization.
MS-500 Microsoft 365 Security Administration Part 07 Q17 179 6. (Optional) In the Description box, add a description of the hold.
7. Click Next.
8. Choose the content locations that you want to place on hold. You can place mailboxes, sites, and public folders on hold.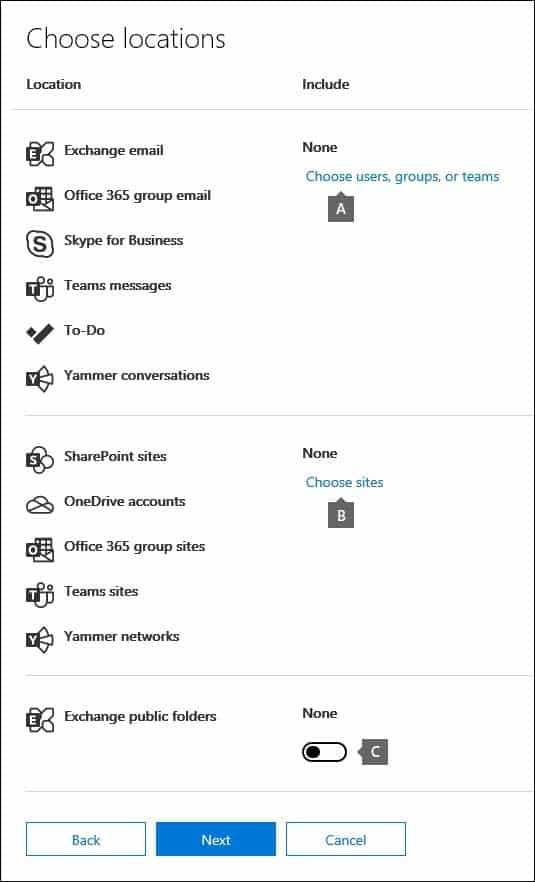
MS-500 Microsoft 365 Security Administration Part 07 Q17 180 a. Exchange email – Click Choose users, groups, or teams and then click Choose users, groups, or teams again. to specify mailboxes to place on hold. Use the search box to find user mailboxes and distribution groups (to place a hold on the mailboxes of group members) to place on hold. You can also place a hold on the associated mailbox for a Microsoft Team, a Yammer Group, or an Office 365 Group. Select the user, group, team check box, click Choose, and then click Done.
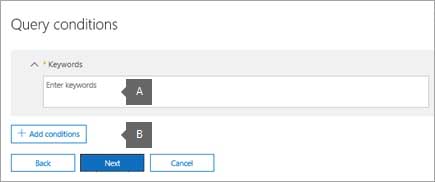
MS-500 Microsoft 365 Security Administration Part 07 Q17 181 a. In the box under Keywords, type a search query in the box so that only the content that meets the search criteria is placed on hold. You can specify keywords, message properties, or document properties, such as file names. You can also use more complex queries that use a Boolean operator, such as AND, OR, or NOT. If you leave the keyword box empty, then all content located in the specified content locations will be placed on hold.
b. Click Add conditions to add one or more conditions to narrow the search query for the hold. Each condition adds a clause to the KQL search query that is created and run when you create the hold. For example, you can specify a date range so that email or site documents that were created within the date ranged are placed on hold. A condition is logically connected to the keyword query (specified in the keyword box) by the AND operator. That means that items have to satisfy both the keyword query and the condition to be placed on hold.9. After configuring a query-based hold, click Next.
10. Review your settings, and then click Create this hold. -
DRAG DROP
You have a Microsoft 365 subscription.
You have a site collection named SiteCollection1 that contains a site named Site2. Site2 contains a document library named Customers.
Customers contains a document named Litware.docx. You need to remove Litware.docx permanently.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
MS-500 Microsoft 365 Security Administration Part 07 Q18 182 Question 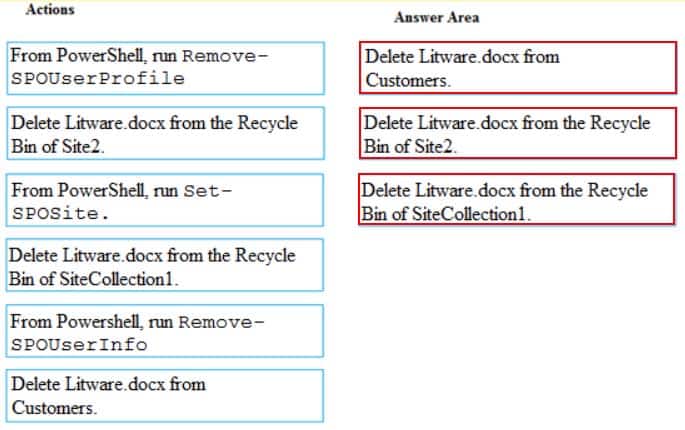
MS-500 Microsoft 365 Security Administration Part 07 Q18 182 Answer -
HOTSPOT
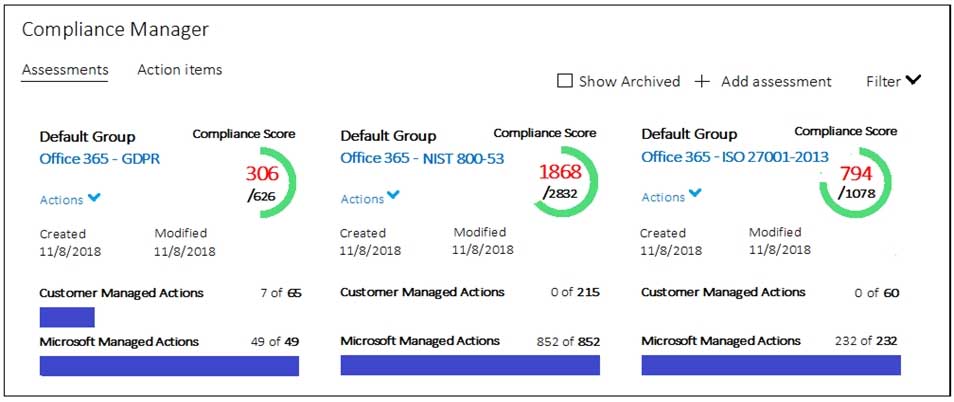
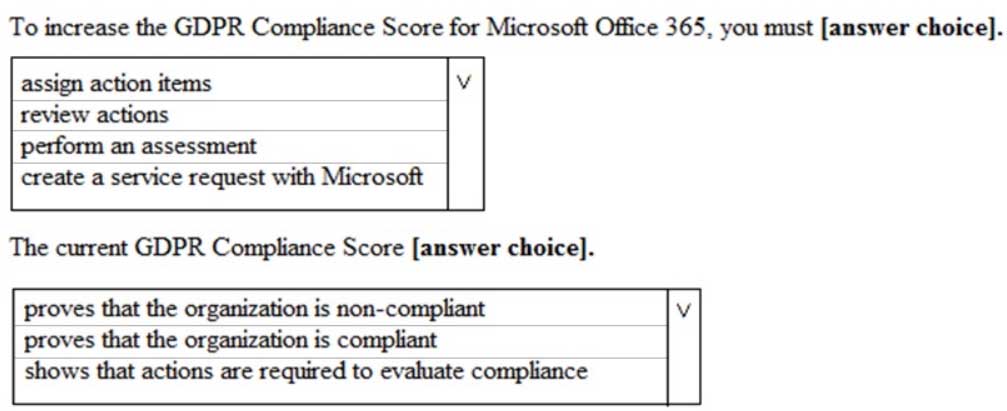
You view Compliance Manager as shown in the following exhibit.
MS-500 Microsoft 365 Security Administration Part 07 Q19 183 Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
MS-500 Microsoft 365 Security Administration Part 07 Q19 184 Question 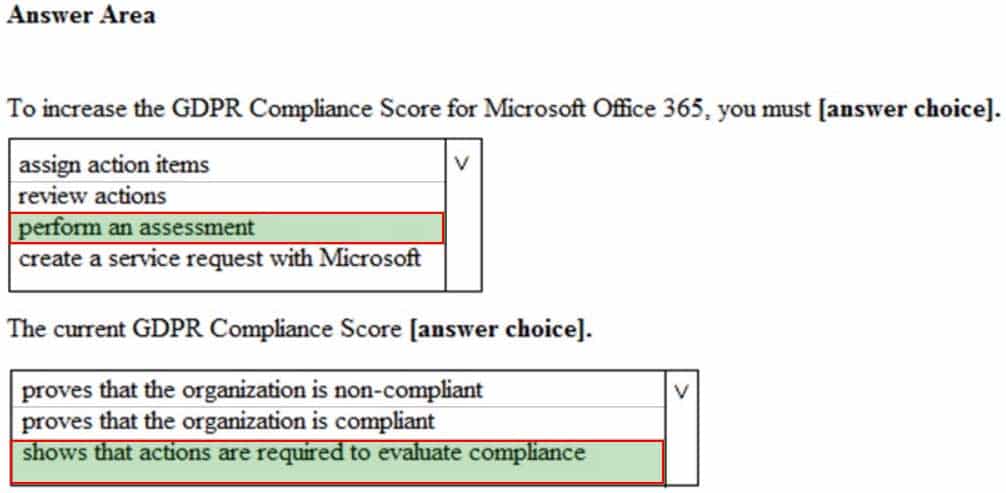
MS-500 Microsoft 365 Security Administration Part 07 Q19 184 Answer Explanation:Box 1: perform an assessment
You can start working with assessments and taking improvement actions to implement controls and improve your compliance score.Box 2: shows that actions are required to evaluate compliance
Your compliance score measures your progress in completing recommended actions that help reduce risks around data protection and regulatory standards. It does not express an absolute measure of organizational compliance with regard to a particular standard or regulation. -
You have a Microsoft 365 subscription.
All computers run Windows 10 Enterprise and are managed by using Microsoft Endpoint Manager.
You plan to view only security-related Windows telemetry data.
You need to ensure that only Windows security data is sent to Microsoft.
What should you create from the Endpoint Management admin center?
- a device configuration profile that has device restrictions configured
- a device configuration profile that has the Endpoint Protection settings configured
- a device compliance policy that has the System Security settings configured
- a device compliance policy that has the Device Health settings configured