Networking Essentials 3.0 Module 15-17 | Checkpoint Exam: Protocols for Specific Tasks Answers 2025 Full 100%
Networking Essentials 3.0 Module 15-17 | Checkpoint Exam: Protocols for Specific Tasks Answers Full 100% 2025
This Networking Essentials 3.0 Module 15-17 section for Checkpoint Exam: Protocols for Specific Tasks Answers which is provided with the correct answers to 100% of the questions. This module 15-17 exam answer is used for the Cisco SkillsForAll platform which is the latest version just released in 2025. Review all the questions and answers here, then you will meet randomly 20 questions from all here.
-
A client device has initiated a secure HTTP request to a web browser. Which well-known port address number is associated with the destination address?
- 443
- 110
- 80
- 404
Explanation: Port numbers are used in TCP and UDP communications to differentiate between the various services running on a device. The well-known port number used by HTTPs is port 443.
-
Which action is performed by a client when establishing communication with a server via the use of UDP at the transport layer?
- The client sets the window size for the session.
- The client sends an ISN to the server to start the 3-way handshake.
- The client sends a synchronization segment to begin the session.
- The client randomly selects a source port number.
Explanation: Because a session does not have to be established for UDP, the client selects a random source port to begin a connection. The random port number selected is inserted into the source port field of the UDP header.
-
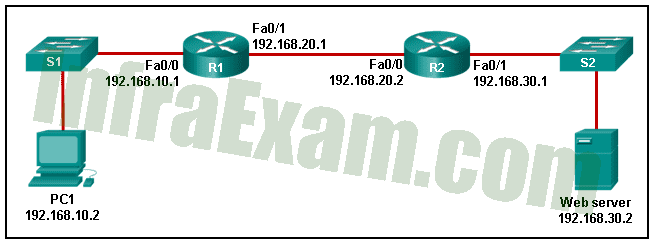
Refer to the exhibit. A TCP segment was sent by PC1 to the web server via port 80. Because of an unexpected network failure, the data was forwarded by R1 but was not received by R2. Which statement is correct about this scenario?
Networking Essentials 3.0 Module 15-17 Checkpoint Exam Protocols for Specific Tasks Answers 01 - The web server will not acknowledge this segment. The PC1 timer will expire and PC1 will resend the segment.
- R1 forwarded the data to R2 but R2 did not receive it. R2 will send a request to R1 to resend the segment.
- The timer on R1 will expire and R1 will resend the segment to R2.
- R1 will request that PC1 resend the segment.
Explanation: The TCP protocol works between end devices, not between each device on the network. Routers, switches, etc. do not participate in the packet recovery process. For each TCP segment (or group of segments) sent by a host, there is an acknowledgment. If the sender does not receive an acknowledgment within a period of time, the sender resends the segment.
-
What information is used by TCP to reassemble and reorder received segments?
- port numbers
- acknowledgment numbers
- sequence numbers
- fragment numbers
Explanation: At the transport layer, TCP uses the sequence numbers in the header of each TCP segment to reassemble the segments into the correct order.
-
A destination PC receives an email message with the sequence numbers on packets out of order. Which layer of the TCP/IP model is responsible for reassembling the packets of the message in the correct order?
- application
- network access
- internet
- transport
Explanation: The transport layer of the TCP/IP model is responsible for ensuring that all packets in a message are received, reassembling the message in the correct order after all packets are received, and identifying which applications are sending and receiving network data.
-
A PC user issues the netstat command without any options. What is displayed as the result of this command?
- a list of all established active TCP connections
- a local routing table
- a historical list of successful pings that have been sent
- a network connection and usage report
Explanation: When used by itself (without any options), the netstat command will display all the active TCP connections that are available.
-
What type of applications are best suited for using UDP?
- applications that are sensitive to packet loss
- applications that require retransmission of lost segments
- applications that need reliable delivery
- applications that are sensitive to delay
Explanation: UDP is not a connection-oriented protocol and does not provide retransmission, sequencing, or flow control mechanisms. It provides basic transport layer functions with a much lower overhead than TCP. Lower overhead makes UDP suitable for applications which are sensitive to delay.
-
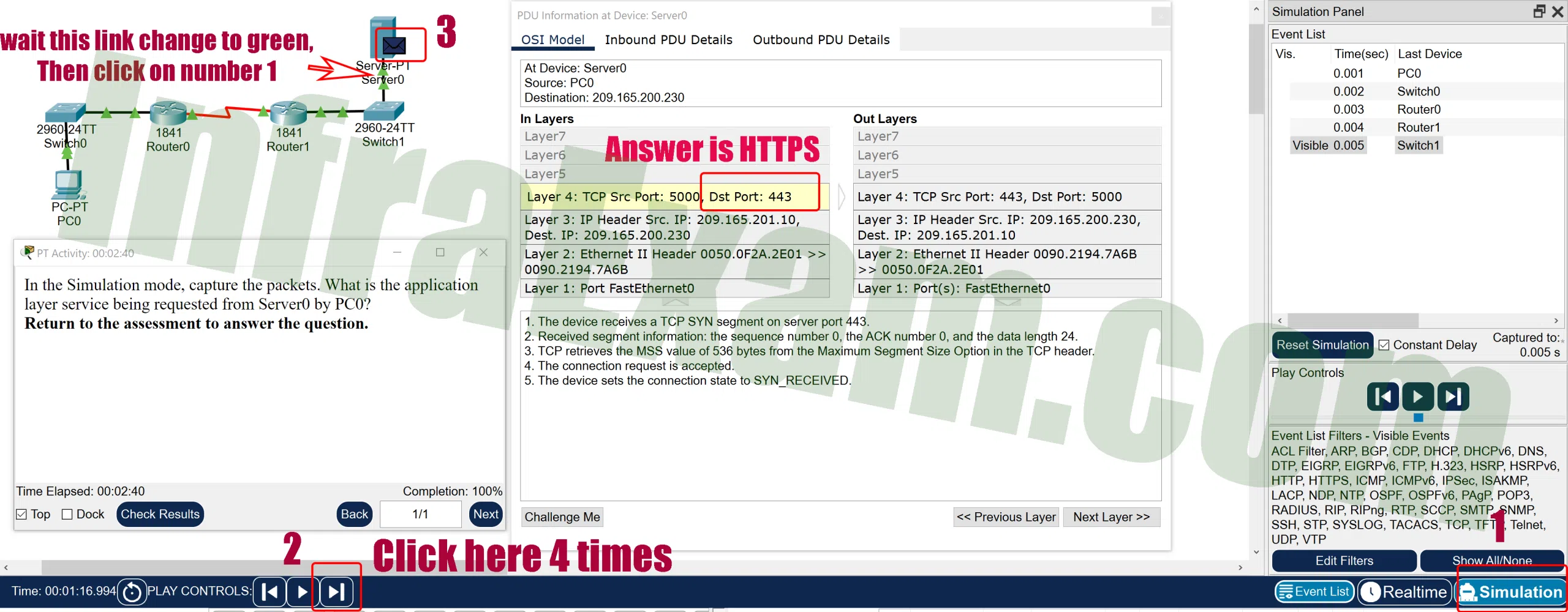
Open the PT activity. Perform the tasks in the activity instructions and then answer the question.
Networking Essentials 3.0 Module 15-17 Checkpoint Exam Protocols for Specific Tasks Answers PT 03 What is the application layer service being requested from Server0 by PC0?
- DNS
- HTTP
- HTTPS
- SMTP
- FTP
Explanation: From the PDU, the destination port is 443, which means the service requested is HTTPS.
-
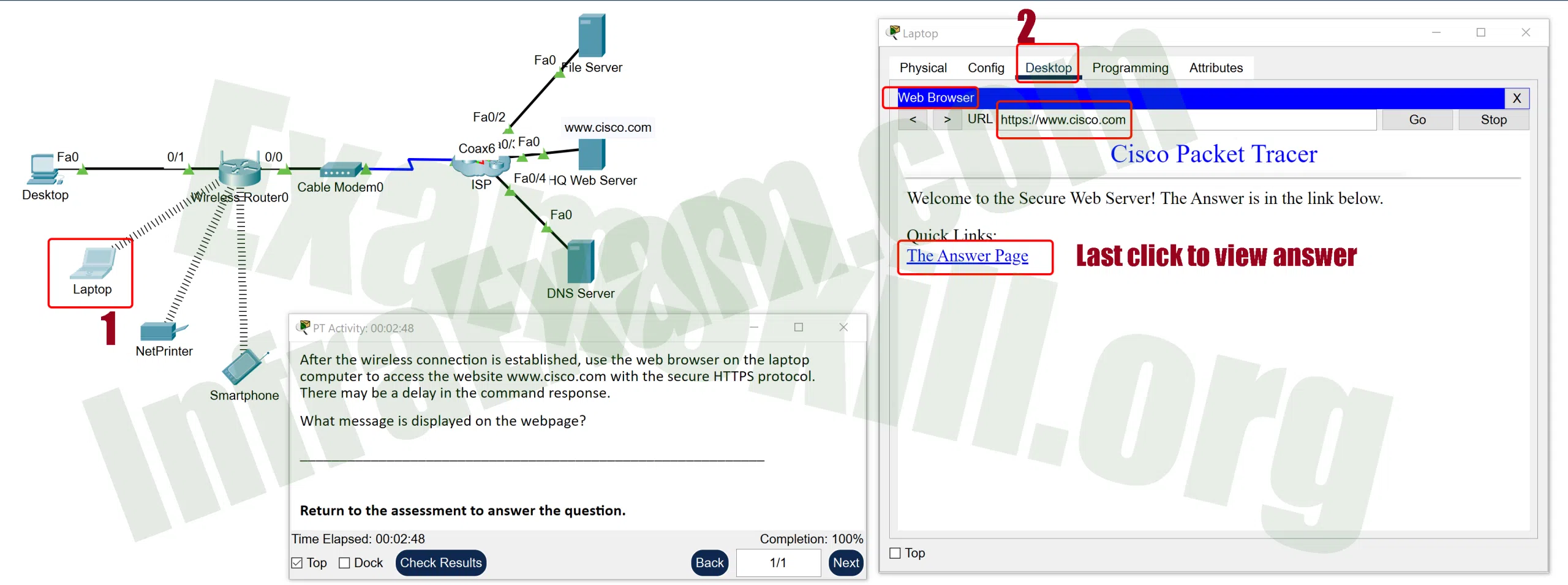
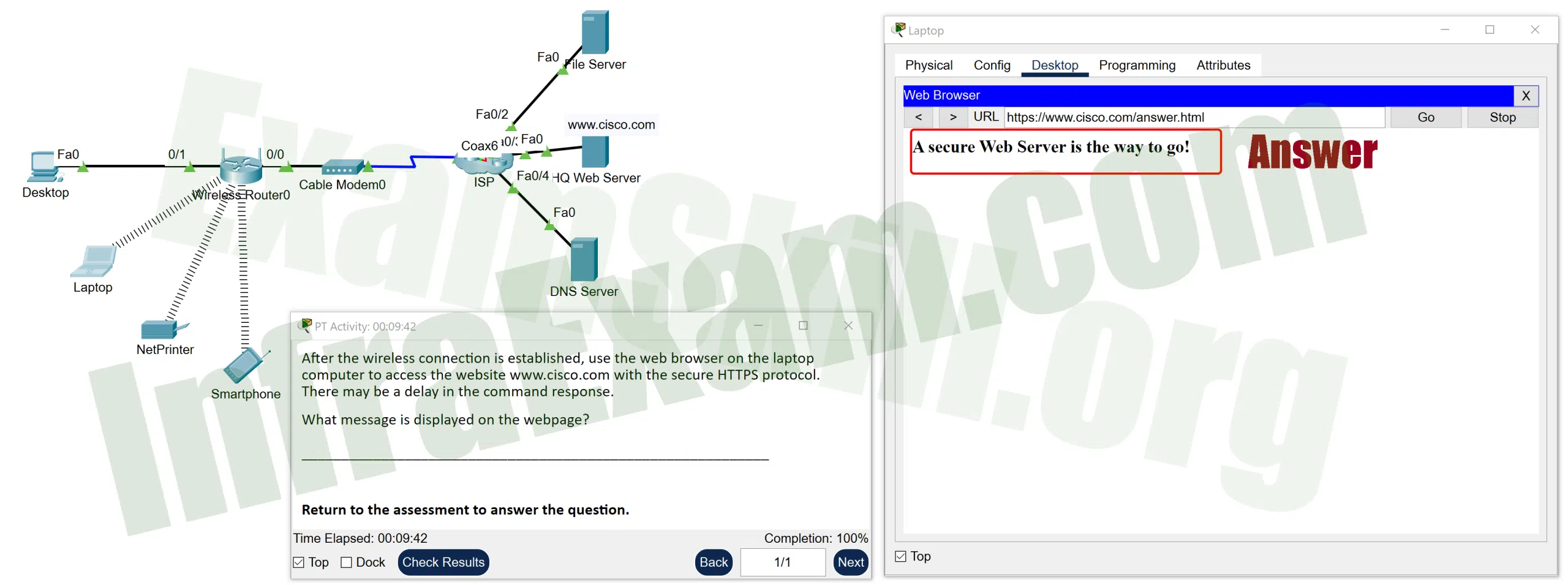
Open the PT Activity. Perform the tasks in the activity instructions and then answer the question.
Networking Essentials 3.0 Module 15-17 Checkpoint Exam Protocols for Specific Tasks Answers PT 02A Networking Essentials 3.0 Module 15-17 Checkpoint Exam Protocols for Specific Tasks Answers PT 02B What message is displayed on the webpage?
- A web server provides secure communication!
- A secure web server is running!
- A web server should run secure services!
- A secure web server is the way to go!
Explanation: Because the HQ web server runs a secure web service, the protocol HTTPS must be used to access the website. This means that the URL of https://www.cisco.com must be used to access the HQ web server and locate the message.
-
A new employee is attempting to configure a cell phone to connect to the email server of the company. Which port number should be selected when using the IMAP4 protocol to access email messages stored on the local server?
- 110
- 25
- 69
- 143
Explanation: The IMAP4 protocol uses the TCP protocol with port 143 for accessing emails stored on a local server.
-
While a network security product is being deployed, a customizable list of allowable protocols is shown. Which three protocols should be allowed to provide for the use of email on a network? (Choose three.)
- DNS
- IMAP4
- TFTP
- Telnet
- SMTP
- POP3
- HTTP
Explanation: The email protocols used on a network are SMTP, POP3, and IMAP4. SMTP is used to send messages to a local email server, whereas POP and IMAP are used to receive email.
-
Which number or set of numbers represents a socket?
- 21
- 01-23-45-67-89-AB
- 10.1.1.15
- 192.168.1.1:80
Explanation: A socket is defined by the combination of an IP address and a port number, and uniquely identifies a particular communication.
-
Which three pieces of information are identified by a URL? (Choose three.)
- the MAC address of the web server
- the protocol that is being used
- the location of the resource
- the IP address of the gateway
- the domain name that is being accessed
- the version of the browser
Explanation: URLs are used to access specific content on a web server through a web browser. The URL identifies the protocol that is being used such as HTTP or FTP, the domain of the server, and the location of the resource on the server.
-
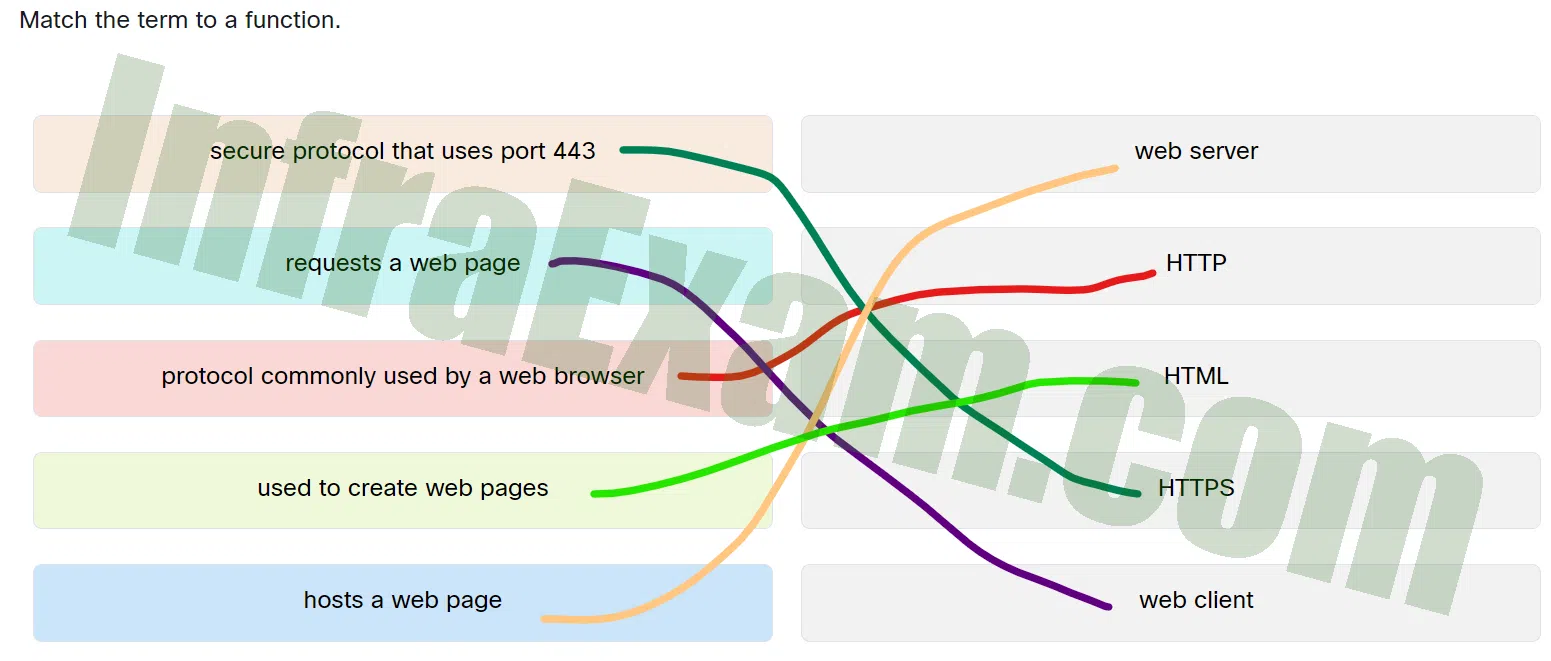
Match the term to a function.
Networking Essentials 3.0 Module 15-17 Checkpoint Exam Protocols for Specific Tasks Answers 001 - protocol commonly used by a web browser —> HTTP
- used to create web pages —> HTML
- requests a web page —> web client
- hosts a web page —> web server
- secure protocol that uses port 443 —> HTTPS
Explanation: Place the options in the following order:
Hosts a web page Web server Requests a web page Web client Used to create web pages HTML Secure protocol that uses port 443 HTTPS Protocol commonly used by a web browser HTTP
-
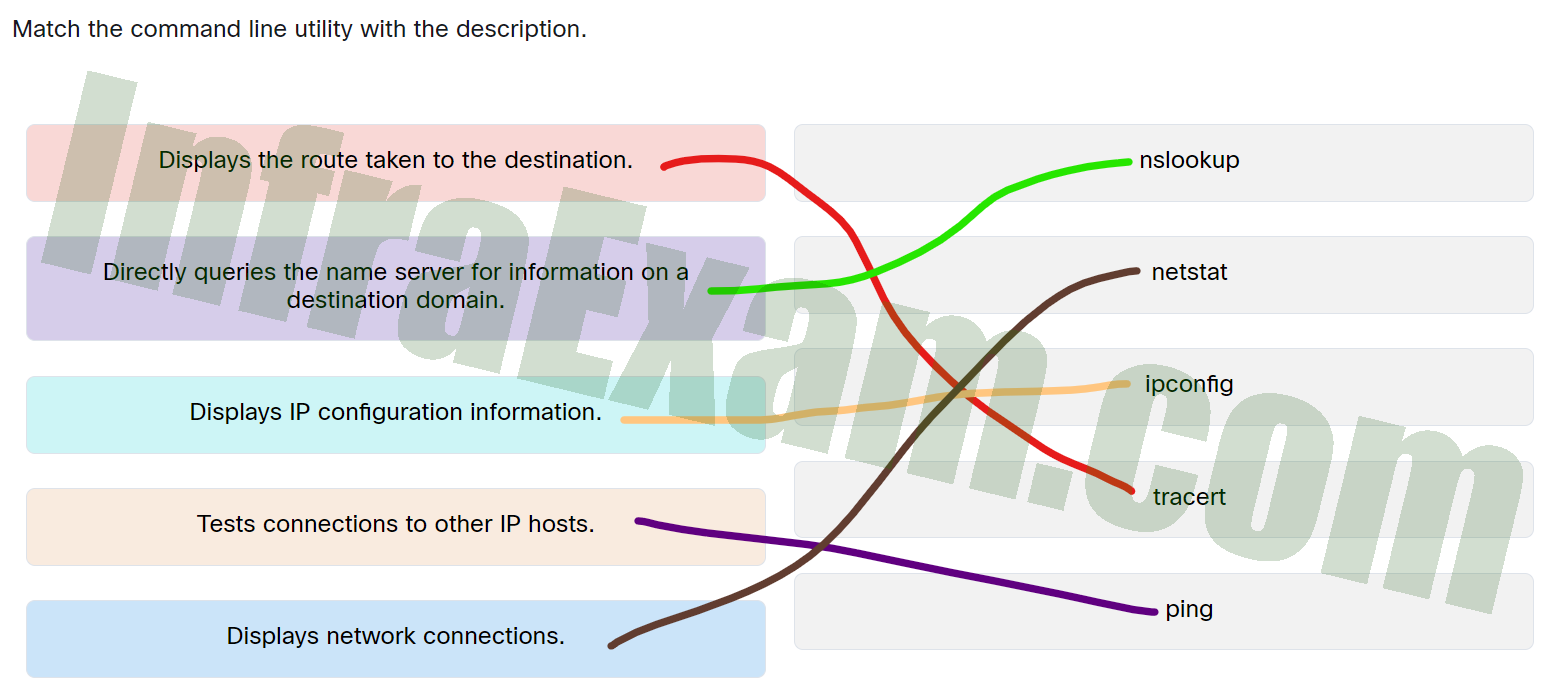
Match the command line utility with the description.
Networking Essentials 3.0 Module 15-17 Checkpoint Exam Protocols for Specific Tasks Answers 002 - Displays IP configuration information. —> ipconfig
- Tests connections to other IP hosts. —> ping
- Displays network connections. —> netstat
- Displays the route taken to the destination. —> tracert
- Directly queries the name server for information on a destination domain. —> nslookup
Explanation: Place the options in the following order:
Displays the route taken to the destination. Tracert Directly queries the name server for information on a destination domain. Nslookup Tests connections to other IP hosts. Ping Displays network connections. Netstat Displays IP configuration information. Ipconfig
-
What is a function of the tracert command that differs from the ping command when they are used on a workstation?
- The tracert command reaches the destination faster.
- The tracert command sends one ICMP message to each hop in the path.
- The tracert command is used to test the connectivity between two devices.
- The tracert command shows the information of routers in the path.
Explanation: The tracert command sends three pings to each hop (router) in the path toward the destination and displays the domain name and IP address of hops from their responses. Because tracert uses the ping command, the travel time is the same as a standalone ping command. The primary function of a standalone ping command is to test the connectivity between two hosts.
-
A technician is troubleshooting a network where it is suspected that a defective node in the network path is causing packets to be dropped. The technician only has the IP address of the end point device and does not have any details of the intermediate devices. What command can the technician use to identify the faulty node?
- tracert
- ipconfig /displaydns
- ping
- ipconfig /flushdns
Explanation: The ping command is used to verify connectivity to a device,the commands ipconfig /flushdns will cause the adapter to flush the DNS cache, while ipconfig /displaydns will result in the display of the DNS information in the cache.
-
Which statement describes the use of the ping command?
- The ping command tests end-to-end connectivity between two devices.
- The ping command can be used to determine the exact location of the problem when troubleshooting reachability issues.
- The ping command can be used to test reachability using the physical address of the device.
- The ping command shows current Layer 4 sessions.
Explanation: The ping command is used to test end-to-end connectivity between the source and destination IP address. It measures the time it takes a test message to make a round trip between the two end points. However, if the message does not reach the destination, or in the case of delays, there is no way to determine where the problem is located.
-
A computer has been assigned an IP address of 169.254.33.16. What command initiates the process of requesting a new IP address?
- nslookup
- net computer
- tracert
- ipconfig /release
Explanation: Forcing a PC to release its DHCP binding allows a new DHCP request operation to occur. The net, tracert, and nslookup commands do not have any effect on DHCP configurations.
-
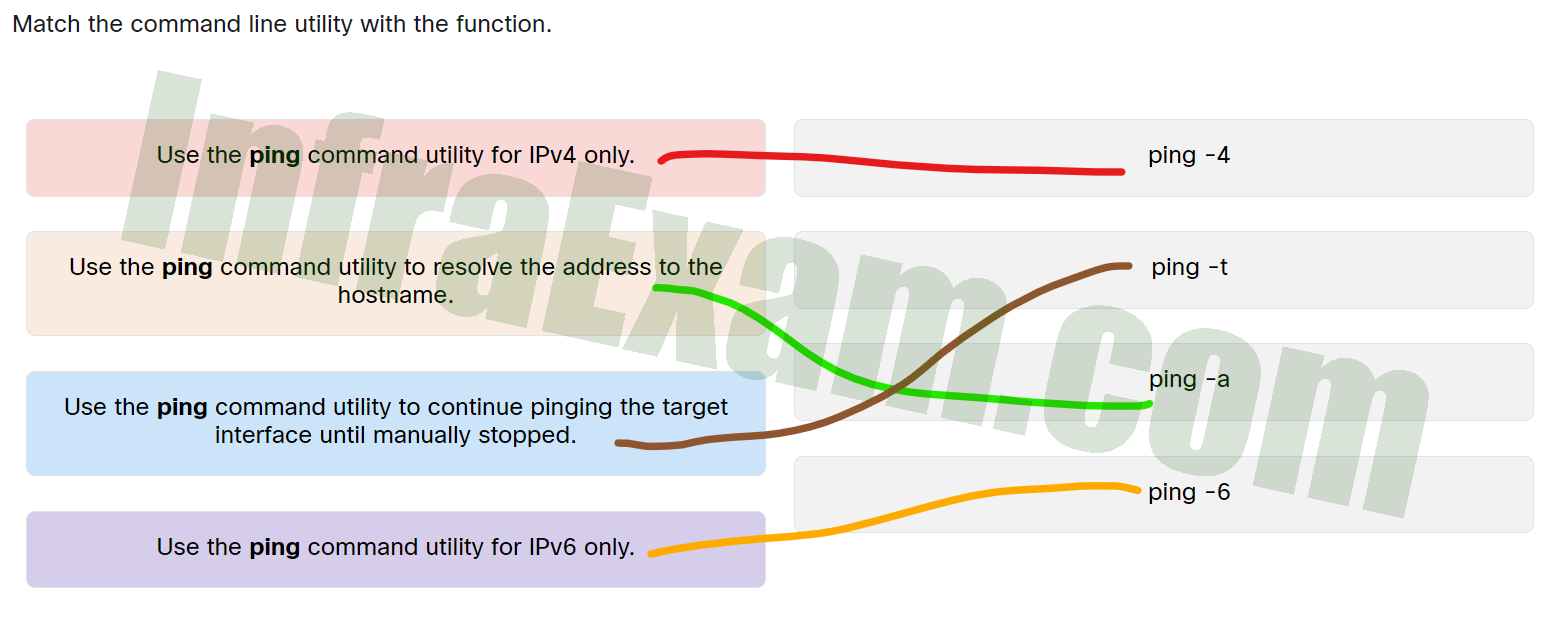
Match the command line utility with the function.
Networking Essentials 3.0 Module 15-17 Checkpoint Exam Protocols for Specific Tasks Answers 003 - Use the ping command utility for IPv4 only. —> ping -4
- Use the ping command utility for IPv6 only. —> ping -6
- Use the ping command utility to resolve the address to the hostname. —> ping -a
- Use the ping command utility to continue pinging the target interface until manually stopped. —> ping -t
Explanation: Place the options in the following order:
Use the ping command utility for IPv4 only. Ping -4 Use the ping command utility for IPv6 only. Ping -6 Use the ping command utility to resolve the address to the hostname. Ping -a Use the ping command utility to continue pinging the target interface until manually stopped. Ping -t
-
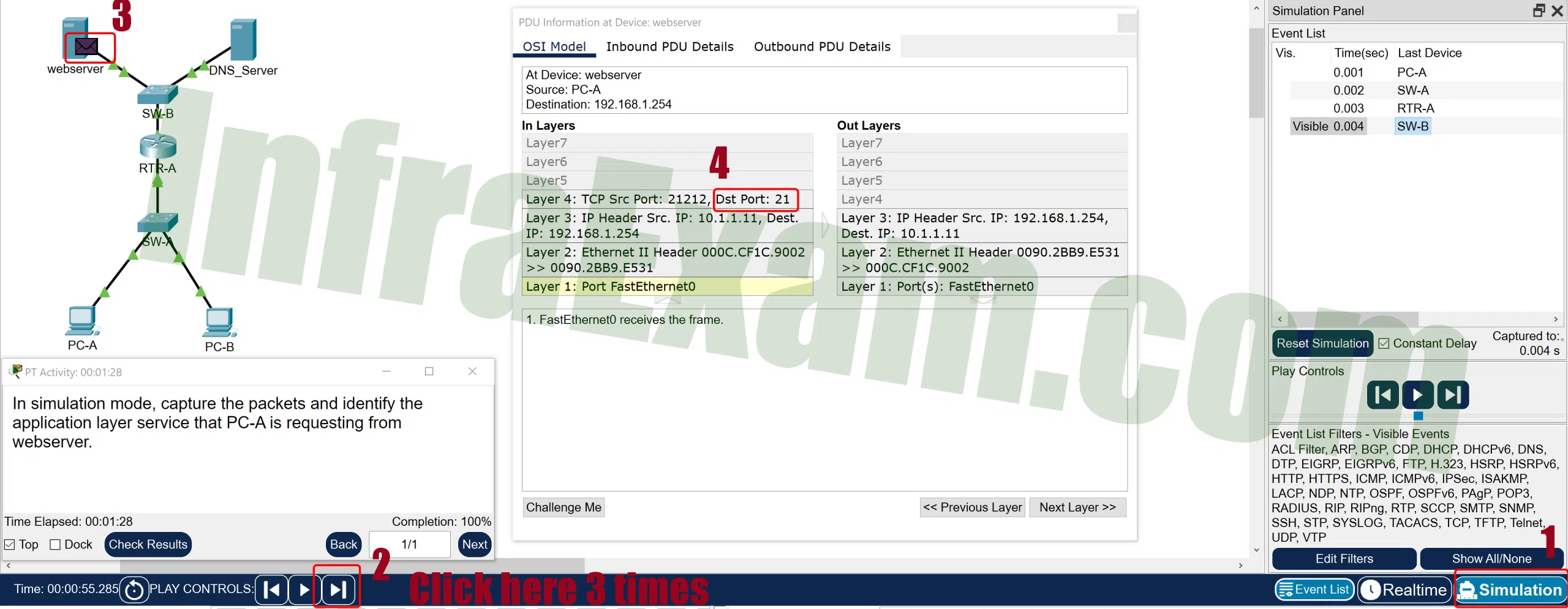
Open the PT Activity. Perform the tasks in the activity instructions and then answer the question or complete the task.
Networking Essentials 3.0 Module 15-17 Checkpoint Exam Protocols for Specific Tasks Answers PT 01 Capture traffic in simulation mode. What application layer service is PC-A requesting from the web server?
- SSH
- FTP
- HTTP
- TFTP
- telnet
Explanation & Hint: When a client is initiating a request to open an FTP session, it does so by sending a packet to the FTP server with the destination port 21.