Networking Essentials 3.0 Module 18-20 | Checkpoint Exam: Characteristics of Network Design Answers 2025 Full 100%
Networking Essentials 3.0 Module 18-20 | Checkpoint Exam: Characteristics of Network Design Answers Full 100% 2025
This Networking Essentials 3.0 Module 18-20 section for Checkpoint Exam: Characteristics of Network Design Answers is provided with the correct answers to 100% of the questions. This module 18-20 exam answer is used for the Cisco SkillsForAll platform which is the latest version just released in 2025. Review all the questions and answers here, then you will meet randomly 21 questions from all here.
-
An administrator is adding voice and video service capabilities to an existing network. What design requirement is being satisfied by this situation?
- scalability
- manageability
- availability
- security
Explanation: Scalability refers to the ability of a network to expand to support new users, services, and applications. In this example, scalability allows the administrator to expand the ability of the network to support voice and video.
-
A networking technician is working on the wireless network at a medical clinic. The technician accidentally sets up the wireless network so that patients can see the medical records data of other patients. Which of the four network characteristics has been violated in this situation?
- security
- scalability
- fault tolerance
- reliability
- Quality of Service (QoS)
Explanation: Network security includes protecting the confidentiality of data that is on the network. In this case, because confidential data has been made available to unauthorized users, the security characteristic of the network has failed.
-
A college is building a new dormitory on its campus. Workers are digging in the ground to install a new water pipe for the dormitory. A worker accidentally damages a fiber optic cable that connects two of the existing dormitories to the campus data center. Although the cable has been cut, students in the dormitories only experience a very short interruption of network services. What characteristic of the network is shown here?
- scalability
- fault tolerance
- security
- quality of service (QoS)
- integrity
Explanation: Fault tolerance is the characteristic of a network which allows it to quickly respond to failures of network devices, media, or services. Quality of service refers to the measures taken to ensure that network traffic requiring higher throughput receives the required network resources. Scalability refers to the ability of the network to grow to accommodate new requirements. Security refers to protecting networks and data from theft, alteration, or destruction. Integrity refers to the completeness of something and is generally not used as a characteristic of networks in the same way as the other terms.
-
Which feature relies on prioritization of network traffic and is used to ensure successful delivery of real-time services?
- security
- reliability
- redundancy
- quality of service
Explanation: Quality of Service (QoS) is implemented in networks to prioritize traffic. Traffic for real-time services such as voice and video requires a higher priority than data traffic to ensure reliable delivery of voice and video content to users.
-
Which layer of the hierarchical design model provides a means of connecting devices to the network and controlling which devices are allowed to communicate on the network?
- core
- network
- distribution
- application
- access
Explanation: The access layer in the hierarchical network design provides a connection point for end user devices to the network and allows multiple hosts to connect to other hosts through a network device.
-
Which is a characteristic of a Type 2 hypervisor?
- best suited for enterprise environments
- has direct access to server hardware resources
- does not require management console software
- installs directly on hardware
Explanation: Type 2 hypervisors are hosted on an underlaying operating system and are best suited for consumer applications and those experimenting with virtualization. Unlike Type 1 hypervisors, Type 2 hypervisors do not require a management console and do not have direct access to hardware.
-
What type of address is physically assigned to the NIC of a workstation?
- MAC address
- host address
- network address
- IP address
Explanation: A MAC address is physically assigned to the host NIC and is known as the physical address. The physical address remains the same regardless of where the host is placed on the network. The IP address is known as a logical address because it is assigned logically based on where the host is located. IP addresses contain two parts, network address and host address.
-
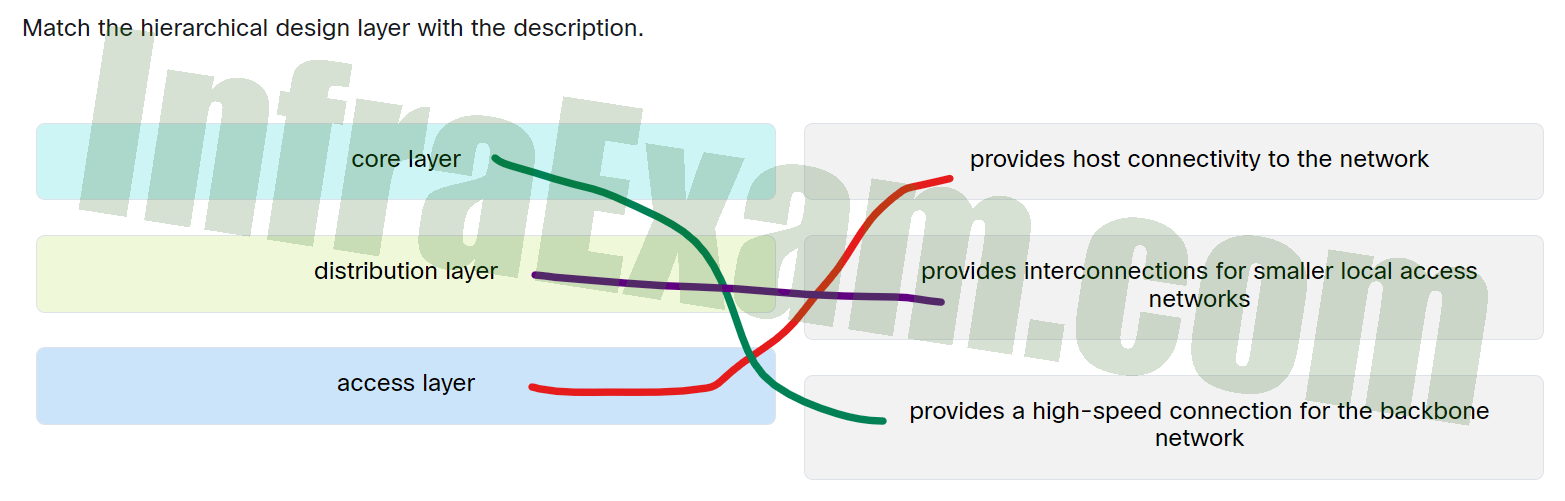
Match the hierarchical design layer with the description.
Networking Essentials 3.0 Module 18-20 Checkpoint Exam Characteristics of Network Design Answers 001 - distribution layer – provides interconnections for smaller local access networks
- access layer – provides host connectivity to the network
- core layer – provides a high-speed connection for the backbone network
Explanation: Place the options in the following order:
Access layer Provides host connectivity to the network Core layer Provides a high-speed connection for the backbone network Distribution layer Provides interconnections for smaller local access networks
-
Which statement accurately describes a Type 2 hypervisor?
- It runs as a software layer on top of a host operating system.
- It sits directly on bare metal and provides the ability to virtualize the hardware for multiple virtual machines.
- It is commonly an open source operating system.
- It is the most common type of hypervisor in enterprise data centers.
Explanation: Type 2 hypervisors run as a software layer atop a host operating system. These hypervisors are often found on PCs and not high-end servers.
-
Which characteristic defines a private cloud?
- composed of two or more clouds
- intended for a specific organization
- created for a specific community
- available to the general public
Explanation: A private cloud is one that is available to a specific organization and not to the general public.
-
What is the function of a hypervisor?
- to create an isolated environment where containerized applications run
- to perform FCAPS functions for VNFs
- to create VMs and provide hardware abstraction to support them
- to centralize management of vSwitch configuration
Explanation: A hypervisor is a software process that abstracts the hardware layer from the operating systems allowing multiple virtual machines to run simultaneously.
-
A company leases a cloud-based payroll system. Which cloud computing technology is this company using?
- platform as a service (PaaS)
- wireless as a service (WaaS)
- infrastructure as a service (IaaS)
- software as a service (SaaS)
Explanation: Software as a service (SaaS) refers to on demand software that is leased from the provider. Platform as a service (PaaS) is when the provider provides the platform for a developer. Infrastructure as a service (IaaS) is when key network devices such as routers and firewalls are leased from a provider. Wireless as a service (WaaS) is when a provider provides wireless connectivity at a fixed monthly cost.
-
Which Cloud computing service would be best for an organization that needs to collaboratively create applications and deliver them over the web?
- ITaaS
- SaaS
- IaaS
- PaaS
Explanation: Platform as a service (PaaS) provides a collaborative environment where multiple developers can create software and host an application through a Cloud provider.
-
Which Cloud computing service would be best for a new organization that cannot afford physical servers and networking equipment and must purchase network services on-demand?
- IaaS
- SaaS
- ITaaS
- PaaS
Explanation: Infrastructure as a service (IaaS) provides an environment where users have an on-demand infrastructure that they can install any platform as needed.
-
What is the dotted decimal representation of the IPv4 address which is represented as the binary string 00001010.01100100.00010101.00000001?
- 100.10.11.1
- 10.100.21.1
- 10.10.20.1
- 100.21.10.1
Explanation: Converting the binary string of 00001010.01100100.00010101.00000001 to dotted decimal gives 10.100.21.1
-
What are two differences between binary and decimal numbers? (Choose two.)
- Binary numbers are based on powers of 2.
- Numbers typed on a keyboard are entered as binary and converted to decimal by the computer.
- Binary numbers consist of three states: on, off, null. Decimal numbers do not have states.
- Decimal numbers include 0 through 9.
- Decimal numbers are based on powers of 1.
Explanation: Computing devices use the binary system for data processing and storage. Binary numbers are based on powers of 2 and decimal numbers are based on powers of 10.
-
What is the decimal equivalent of the hexadecimal value of 3F?
- 45
- 18
- 34
- 46
- 63
Explanation: In order to convert a hexadecimal number to decimal, consider that the digit to the far right represents the 1s column where values 0 through F can appear. A hexadecimal value of A equals the decimal number 10. B equals 11, and so on through F equaling 15. The value of F in the number F equals 15. Next consider the value of 3 in the hexadecimal number of 3F. That place holder is the 16s column. Multiple the number 3 times 16 for a total of 48. Add 48 to 15 for the grand total of 63. Hexadecimal 3F equals a decimal value of 63.
-
How many bits make up the single IPv6 hextet :10CD:?
- 16
- 32
- 8
- 4
Explanation: A hextet consists of 4 hexadecimal characters. Each hexadecimal character is represented by four bits, giving a total of 16 bits.
-
How many unique values are possible using a single binary digit?
- 4
- 1
- 8
- 2
Explanation: Binary is a numbering system that consists of the digits 0 and 1 called bits. A binary number is a series of only 1s and 0s.
-
What is the hexadecimal equivalent for the binary number 10111010?
- D9
- A1
- BA
- 85
Explanation: Each 4 binary digits equates to 1 hexadecimal digit.
1011 = 11 (decimal) = B (hexadecimal)
1010 = 10 (decimal) = A (hexadecimal)
-
A student is learning number systems. What is the hexadecimal equivalent for the decimal number 165?
- 7D
- A5
- C8
- 9F
Explanation: Decimal 165 in binary is 10100101. 128+32+4+1 = 165.
Each 4 binary digits equates to 1 hexadecimal digit.
1010 = 10 (decimal) = A (hexadecimal)
0101 = 5 (decimal) = 5 (hexadecimal)
-
Which term describes the state of a network when the demand on the network resources exceeds the available capacity?
- synchronization
- convergence
- optimization
- congestion
Explanation & Hint: When the demand on the network resources exceeds the available capacity, the network becomes congested. A converged network is designed to deliver multiple communication types, such as data, video and voice services, using the same network infrastructure.
-
A company is considering implementing virtualization solutions in a data center. What are three advantages of virtualization the company can expect to benefit from?(Choose three.)
- reduced physical space requirements
- shorter work week
- improved disaster recovery
- faster server provisioning
- less employee training
- reduced security requirements
Explanation & Hint: Virtualization is the ability to run many instances of an OS simultaneously on the same hardware platform. This reduces the amount of equipment that is required, thus resulting in less power consumption and improved disaster recovery.
-
Which IPv4 address format was created for ease of use by people and is expressed as 201.192.1.14?
- hexadecimal
- dotted decimal
- binary
- ASCII
Explanation & Hint: For ease of use by people, binary patterns are represented as dotted decimal. Computer systems were created to understand binary addressing.
-
What is required for a network administrator to perform out-of-band management tasks on a Cisco device?
- a valid IP address configured on VLAN 1
- SSH enabled and functional on the device
- an active network connection available to the device
- a computer directly connected to the console port of the device
Answers Explanation & Hints: With out-of-band management, the only requirement is to have a computer directly connected to the console port of the device. This is the primary method to configure a new device because no network connection or prior configurations on the device is required.
-
Which two files are loaded into RAM of a Cisco switch when it is booted? (Choose two.)
- routing table
- IOS image file
- file that contains customer settings
- startup configuration file
- running configuration file
Answers Explanation & Hints: When a Cisco device boots, it loads the IOS and startup configuration files into RAM.
-
Which two ports can be used for the initial configuration of a Cisco router? (Choose two.)
- AUX
- console
- flash slot
- LAN interface
- WAN interface
Answers Explanation & Hints: The AUX and console ports on a Cisco 1941 router can be used to perform initial setup. The initial setup does not require that the router be connected to a network. A network administrator uses a computer to connect to the console ports directly. A network administrator can also access the router remotely through a dialup phone line and a modem connected to the AUX port. LAN and WAN interfaces are used to connect to networks. The flash slots expand storage capability through the use of a compact flash card.
-
When a router is powered on, where will the router first search for a valid IOS image to load by default?
- RAM
- ROM
- flash memory
- NVRAM
Answers Explanation & Hints: By default, if no boot system commands are in the configuration, a router will load the first valid Cisco IOS image in flash memory and run it. RAM is active memory that is not used to store image files. NVRAM stores configuration files. ROM stores a minimal version of the Cisco IOS image that can be used to provide limited functions if a valid IOS image is not available in flash memory.
-
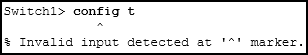
Refer to the exhibit. An administrator is trying to configure the switch but receives the error message that is displayed in the exhibit. What is the problem?
Modules 17 – 20 Introduction to Cisco Networking Pre-Test Exam Answers 01 - The entire command, configure terminal , must be used.
- The administrator is already in global configuration mode.
- The administrator must first enter privileged EXEC mode before issuing the command.
- The administrator must connect via the console port to access global configuration mode.
Answers Explanation & Hints: In order to enter global configuration mode, the command configure terminal , or a shortened version such as config t , must be entered from privileged EXEC mode. In this scenario the administrator is in user EXEC mode, as indicated by the > symbol after the hostname. The administrator would need to use the enable command to move into privileged EXEC mode before entering the configure terminal command.
-
Which keys act as a hot key combination that is used to interrupt an IOS process?
- Ctrl-Shift-X
- Ctrl-Shift-6
- Ctrl-Z
- Ctrl-C
Answers Explanation & Hints: The Cisco IOS provides both hot keys and shortcuts for configuring routers and switches. The Ctrl-Shift-6 hot key combination is used to interrupt an IOS process, such as a ping or traceroute. Ctrl-Z is used to exit the configuration mode. Ctrl-C aborts the current command. Ctrl-Shift-X has no IOS function.
-
What function does pressing the Tab key have when entering a command in IOS?
- It aborts the current command and returns to configuration mode.
- It exits configuration mode and returns to user EXEC mode.
- It moves the cursor to the beginning of the next line.
- It completes the remainder of a partially typed word in a command.
Answers Explanation & Hints: Pressing the Tab key after a command has been partially typed will cause the IOS to complete the rest of the command.
-
While troubleshooting a network problem, a network administrator issues the show version command on a router. What information can be found by using this command?
- the amount of NVRAM, DRAM, and flash memory installed on the router
- the bandwidth, encapsulation, and I/O statistics on the interfaces
- differences between the backup configuration and the current running configuration
- the version of the routing protocol that is running on the router
Answers Explanation & Hints: The show version command displays much information about the device, including the amount of memory (flash, NVRAM, and DRAM) that is installed on the device.
-
Which interface is the default SVI on a Cisco switch?
- FastEthernet 0/1
- GigabitEthernet 0/1
- VLAN 1
- VLAN 99
Answers Explanation & Hints: An SVI is a virtual interface and VLAN 1 is enabled by default on Cisco switches. VLAN 99 must be configured to be used. FastEthernet 0/1 and GigabitEthernet 0/1 are physical interfaces.
-
What is the effect of using the Router# copy running-config startup-config command on a router?
- The contents of ROM will change.
- The contents of RAM will change.
- The contents of NVRAM will change.
- The contents of flash will change.
Answers Explanation & Hints: The command copy running-config startup-config copies the running-configuration file from RAM into NVRAM and saves it as the startup-configuration file. Since NVRAM is none-volatile memory it will be able to retain the configuration details when the router is powered off.
-
A network administrator enters the service password-encryption command into the configuration mode of a router. What does this command accomplish?
- This command encrypts passwords as they are transmitted across serial WAN links.
- This command prevents someone from viewing the running configuration passwords.
- This command enables a strong encryption algorithm for the enable secret password command.
- This command automatically encrypts passwords in configuration files that are currently stored in NVRAM.
- This command provides an exclusive encrypted password for external service personnel who are required to do router maintenance.
Answers Explanation & Hints: The startup-config and running-config files display most passwords in plaintext. Use the service password-encryption global config command to encrypt all plaintext passwords in these files.
-
What happens when the transport input ssh command is entered on the switch vty lines?
- The SSH client on the switch is enabled.
- Communication between the switch and remote users is encrypted.
- The switch requires a username/password combination for remote access.
- The switch requires remote connections via a proprietary client software.
Answers Explanation & Hints: The transport input ssh command when entered on the switch vty (virtual terminal lines) will encrypt all inbound controlled telnet connections.
-
A small office uses a wireless router to connect to a cable modem for Internet access. The network administrator receives a call that one office computer cannot access external websites. The first troubleshooting step that the network administrator performs is to ping the wireless router from the office computer. Which troubleshooting technique does this represent?
- top-down
- bottom-up
- substitution
- divide-and-conquer
Answers Explanation & Hints: A ping to the wireless router can verify Layer 3 connectivity. As a troubleshooting method, this is the divide-and-conquer approach.
-
What are two common causes of a physical layer network connectivity problem? (Choose two.)
- a monitor unplugged
- an Ethernet cable plugged into a wrong port
- an incorrect default gateway
- an unassigned IP address
- a faulty Ethernet cable
Answers Explanation & Hints: An Ethernet cable plugged into a wrong port and a faulty Ethernet cable are two possible causes for physical network connectivity issues. An incorrect default gateway configuration and a lack of an IP address will cause logical connectivity issues.
-
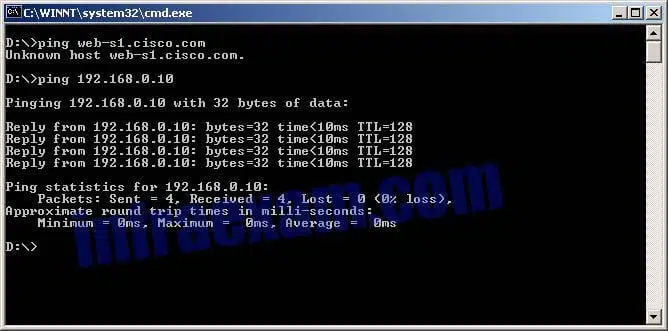
Refer to the exhibit. A web designer calls to report that the web server web-s1.cisco.com is not reachable through a web browser. The technician uses command line utilities to verify the problem and to begin the troubleshooting process. Which two things can be determined about the problem? (Choose two.)
Modules 17 – 20 Introduction to Cisco Networking Pre-Test Exam Answers 01 - The web server at 192.168.0.10 is reachable from the source host.
- There is a problem with the web server software on web-s1.cisco.com.
- A router is down between the source host and the server web-s1.cisco.com.
- DNS cannot resolve the IP address for the server web-s1.cisco.com.
- The default gateway between the source host and the server at 192.168.0.10 is down.
Answers Explanation & Hints: The successful result of the ping to the IP address indicates that the network is operational and the web server is online. However, the fact that the ping to the domain name of the server fails indicates there is a DNS issue, namely that the host cannot resolve the domain name to its associated IP address.
-
Which command would a technician use to display network connections on a host computer?
- nslookup
- netstat
- tracert
- ipconfig
Answers Explanation & Hints: The netstat command is a network utility that can be used to display active TCP connections that are open and running on a networked host.
-
What type of cable is used to connect a workstation serial port to a Cisco router console port?
- crossover
- rollover
- straight-through
- coaxial
Answers Explanation & Hints: UTP cable wire pairs can be terminated in different configurations for use in different applications. To use a UTP cable for consoling into a Cisco router from a PC serial port, it must be terminated as a rollover or console cable.
-
What are two requirements when using out-of-band configuration of a Cisco IOS network device? (Choose two.)
- HTTP access to the device
- a terminal emulation client
- Telnet or SSH access to the device
- a direct connection to the console or AUX port
- a connection to an operational network interface on the device
Answers Explanation & Hints: A connection to an operational network interface on the device, and Telnet, SSH, or HTTP access are required for in-band management of Cisco IOS networking devices.
-
When is an IP address required to be configured on a Cisco LAN switch?
- when the switch is connected to another switch
- when the switch must forward LAN traffic
- when the switch needs to be managed through an in-band connection
- when the switch is configured from a computer connected to the console port
Answers Explanation & Hints: A LAN switch uses Layer 2 addresses to determine how to forward packets. An IP address is only necessary if the switch needs to be remotely managed through an in-band connection on the network.
-
Following default settings, what two tasks are performed first in the router boot sequence? (Choose two.)
- Perform the POST routine.
- Locate and load the startup-config file from NVRAM.
- Load the bootstrap program from ROM.
- Load the running-config file from RAM.
- Locate and load the operating system.
Answers Explanation & Hints: There are three major steps to the router boot sequence:
- Perform Power-On-Self-Test (POST) and load the bootstrap program.
- Load the IOS from Flash or TFTP server.
- Load the startup configuration file from NVRAM.
-
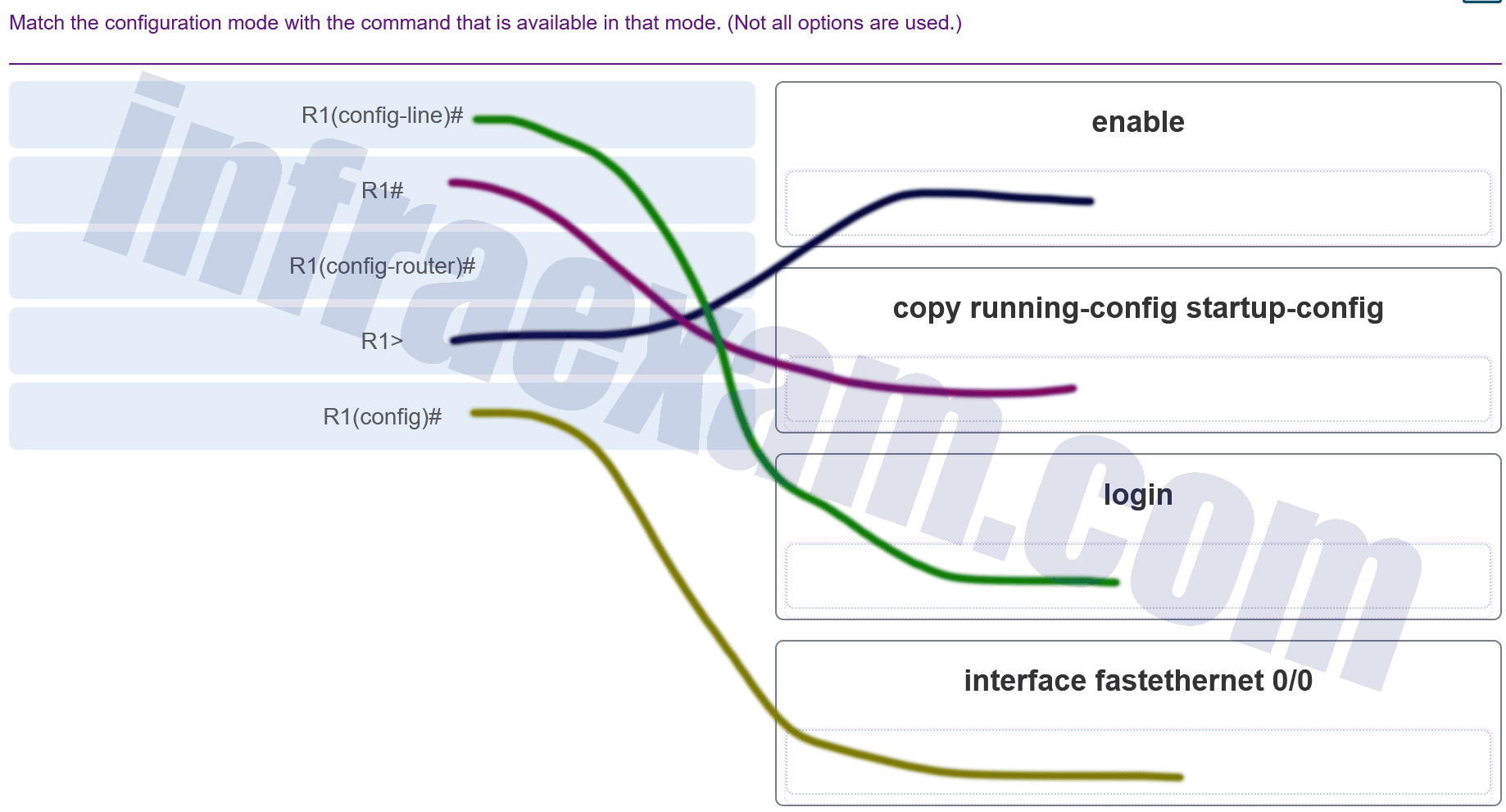
Match the configuration mode with the command that is available in that mode. (Not all options are used.)
Modules 17 – 20 Introduction to Cisco Networking Group Exam Answers 001 Answers Explanation & Hints: The enable command is entered at the R1> prompt. The login command is entered at the R1(config-line)# prompt. The copy running-config startup-config command is entered at the R1# prompt. The interface fastethernet 0/0 command is entered at the R1(config)# prompt.
-
A network administrator is working on a Cisco router. The CLI prompt is Router1(config-if)#. Which operation is the administrator likely to configure next?
- the vty lines
- a LAN interface
- the console port
- the password that is required to access the privileged EXEC mode
Answers Explanation & Hints: Cisco IOS uses different prompts to identify the specific configuration modes. The prompt Router1(config-if)# is a subconfiguration mode of Router(config)#. This mode indicates that the configuration commands that follow are applied to a LAN or WAN interface.
-
To save time, IOS commands may be partially entered and then completed by typing which key or key combination?
- Tab
- Ctrl-P
- Ctrl-N
- Up Arrow
- Right Arrow
- Down Arrow
-
A network administrator issues the Switch# show running-config command on a Cisco switch. Which term is used to describe the part ” running-config” in the command?
- hot key
- keyword
- argument
- command
Answers Explanation & Hints: The running-config is a keyword of the show command.
-
Refer to the exhibit. Which element of IOS syntax is the expression MainOffice ?
- a command
- a keyword
- an argument
- a subcommand
Answers Explanation & Hints: An argument of a CLI command is generally not a predefined word, but rather is a value defined by the user. Keywords, however, describe specific parameters of a command that are predefined words that are known to the command interpreter.
-
A network administrator is troubleshooting inter-connection issues between routers. Which show command can be used to check the bandwidth and MTU settings of an interface?
- show arp
- show ip route
- show protocols
- show interfaces
Answers Explanation & Hints: The show interfaces command displays the hardware settings of each interface, such as MTU, MAC address, and bandwidth.
-
What is the purpose of assigning an IP address to the VLAN1 interface on a Cisco Layer 2 switch?
- to create a new IP local network on the switch
- to permit IP packets to be forwarded by the switch
- to enable remote access to the switch to manage it
- to enable the switch to route packets between networks
Answers Explanation & Hints: The VLAN 1 on a Cisco Layer 2 switch is a virtual interface. By default, VLAN 1 is assigned as the management interface for remote access (Telnet or SSH) to the device for management tasks. In order to allow remote access through the network, a valid IP address configuration is needed on VLAN 1.
-
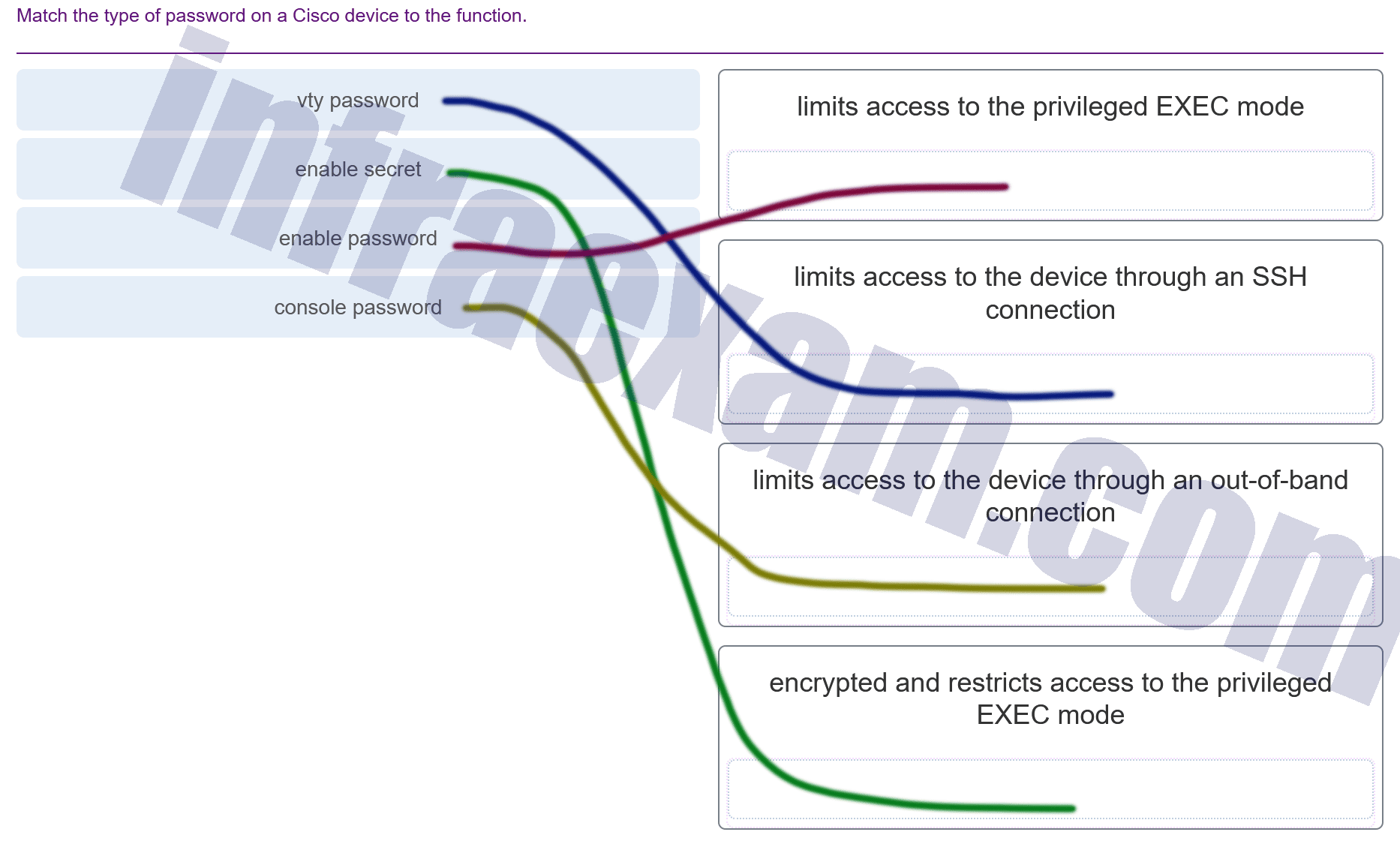
Match the type of password on a Cisco device to the function.
Modules 17 – 20 Introduction to Cisco Networking Group Exam Answers 002 -
Which statement regarding the service password-encryption command is true?
- It is configured in privileged EXEC mode.
- It encrypts only line mode passwords.
- As soon as the service password-encryption command is entered, all currently set passwords formerly displayed in plain text are encrypted.
- To see the passwords encrypted by the service password-encryption command in plain text, issue the no service password-encryption command.
Answers Explanation & Hints: The command service password-encryption is used to encrypt all the clear text passwords in the running-configuration file.
-
Passwords can be used to restrict access to all or parts of the Cisco IOS. Select the modes and interfaces that can be protected with passwords. (Choose three.)
- VTY interface
- console interface
- Ethernet interface
- boot IOS mode
- privileged EXEC mode
- router configuration mode
Answers Explanation & Hints: Access to the VTY and console interfaces can be restricted using passwords. Out-of-band management of the router can be restricted in both user EXEC and privileged EXEC modes.
-
An administrator defined a local user account with a secret password on router R1 for use with SSH. Which three additional steps are required to configure R1 to accept only encrypted SSH connections? (Choose three.)
- Configure the IP domain name on the router.
- Enable inbound vty Telnet sessions.
- Generate the SSH keys.
- Configure DNS on the router.
- Enable inbound vty SSH sessions.
- Generate two-way pre-shared keys.
Answers Explanation & Hints: There are four steps to configure SSH support on a Cisco router:
Step 1: Set the domain name.
Step 2: Generate one-way secret keys.
Step 3: Create a local username and password.
Step 4: Enable SSH inbound on a vty line.
-
What advantage does SSH offer over Telnet?
- encryption
- more connection lines
- connection-oriented services
- username and password authentication
Answers Explanation & Hints: Both Telnet and SSH are used to remotely connect to a network device for management tasks. However, Telnet uses plaintext communications, whereas SSH provides security for remote connections by providing encryption of all transmitted data between devices.
-
A user can print to a printer that is on the same network, but the traffic of the user cannot reach the Internet. What is a possible cause of the problem?
- The PC default gateway address is missing or incorrect.
- The PC has an incorrect IP address.
- The network cable connected to the user PC is faulty.
- The NIC on the PC is faulty.
Answers Explanation & Hints: The default gateway IP address is used to reach other networks, including the Internet.
-
For the second time in a week, workstations on a LAN are not able to log into a specific server. The technician fixed the problem the first time, but cannot remember the steps taken to solve it. What aspect of the troubleshooting process has the technician neglected?
- identifying the problem
- asking questions of end users
- documenting the troubleshooting process
- using structured techniques to solve a problem
Answers Explanation & Hints: Proper documentation is a very important step in troubleshooting. The proper documentation can help troubleshoot the same or similar problems in the future.
-
Which utility can be used to view a list of open TCP connections on Linux or Windows systems?
- Tracert
- Ping
- Netstat
- Ipconfig
Answers Explanation & Hints: Netstat is a utility that is available for both Linux and Windows systems. It is a utility that can be used to indicate that something or someone is connected to the local host. It lists the protocol in use, the local address and port numbers, the foreign address and port numbers, and the state of the connection.
-
Which three pieces of information are revealed by the ipconfig command (without the /all switch)? (Choose three.)
- IP address
- DHCP server
- subnet mask
- default gateway
- DNS server
- MAC address
Answers Explanation & Hints: The ipconfig command is used to display the current TCP/IP network configuration values of the device. This includes the IP address; the subnet mask and the default gateway addresses. Using the ipconfig /all switch displays additional information like the physical address of the device and the DHCP server address among other things.
-
Which command can be used to verify connectivity between two host devices?
- ipconfig
- ping
- netstat
- nslookup
Answers Explanation & Hints: The ping command can be used to test end-to-end connectivity between two host devices. It measures the round-trip time for a message to get from source to destination.
-
How does an activity LED on wireless routers indicate that traffic is moving through a port?
- by flashing
- by staying turned off
- by staying a solid green color
- by staying a solid amber color
Answers Explanation & Hints: One of the first steps when using the bottom-up strategy of troubleshooting is to examine the LED lights of the device, which indicate the current state or activity of the device. LEDs may change color or flash to convey information. Although the exact configuration and meaning of LEDs varies between manufacturers and devices, a flashing light indicates flow of traffic.
-
A user experiences access and performance issues with the Internet connection from a home computer. The Internet connection is provided through a DSL line. The user calls the support line of the phone company for help. The support technician asks the user to connect the computer directly to the DSL modem. Which two pieces of information will help the technician to troubleshoot the problem? (Choose two.)
- when the problem started
- the model and vendor of the computer
- the IP address of the computer
- the MAC address of the Ethernet NIC on the computer
- the number of times that the ping command was issued
Answers Explanation & Hints: The timeline and the IP address will help the technician to troubleshoot and test to verify the problem. The timeline can be used to check the operation status of the DSL equipment in the phone company. The IP address can be used to verify if the DHCP is functional from the phone company. The MAC address of the Ethernet NIC is irrelevant because the connection is not an Ethernet connection. The technician should not assume that a client is technically savvy. If the ping command is necessary, the technician should instruct the client on how to issue the ping command.