Networking Essentials 3.0 Module 1-4 | Checkpoint Exam: Build a Small Network Answers 2025 Full 100%
Networking Essentials 3.0 Module 1-4 | Checkpoint Exam: Build a Small Network Answers Full 100% 2025
This Networking Essentials 3.0 Module 1-4 section for Checkpoint Exam: Build a Small Network Answers which is provided with the correct answers to 100% of the questions. This module 1-4 exam answer is used for the Cisco SkillsForAll platform which is the latest version just released in 2025. Review all the questions and answers here, then you will meet randomly 20 questions from all here.
-
What is the order of bandwidth measurement from smallest to largest?
- Tbps, Mbps, Kbps, Gbps
- Kbps, Mbps, Gbps, Tbps
- Kbps, Tbps, Mbps, Gbps
- Gbps, Tbps, Mbps, Kbps
Explanation and Hint: Command bandwidth measurements are as follows from smallest to largest:
- Thousands of bits per second (Kbps) or Kilobits per second
- Millions of bits per second (Mbps) or Megabits per second
- Billions of bits per second (Gbps) or Gigabits per second
- Trillions of bits per second (Tbps) or Terabits per second
-
A user is looking for a wireless headphone for listening to songs stored on a smartphone. What wireless technology would the headphone use?
- Bluetooth
- Wi-Fi
- infrared
- 3G/4G
Explanation and Hint: Bluetooth is a wireless technology for data exchange over a short distance. It is suitable for connecting devices with simple tasks, such as headsets, keyboards, mice, and printers. Wi-Fi is suitable for variety of applications with high speed wireless connectivity required or preferred. Infrared requires a direct line of sight between the transmitter and the receiver. 3G/4G are cellular network technologies to manage voice calls and data transmission between clients and service providers.
-
Which is a characteristic of the Internet?
- It supports only wired network connections.
- It is not centrally governed.
- It is localized to specific geographic locations.
- It is operated by the US government.
Explanation and Hint: The Internet is a global system of interconnected computer networks that has no central governance. It is not limited to geographic boundaries and uses static public IP addresses for communication.
-
How many unique values are possible using a single binary digit?
- 16
- 2
- 4
- 8
- 9
- 1
Explanation and Hint: A bit is stored and transmitted as one of two possible discrete states. Each bit can only have one of two possible values, 0 or 1. The term bit is an abbreviation of “binary digit” and represents the smallest piece of data.
-
What data representation is used when a computer or network device is processing data?
- binary
- text
- readable
- inferred
Explanation and Hint: Computers use 1s and 0s or binary code to represent and interpret text, numbers, and special characters.
-
Which items are collectively referred to as network media?
- wires and radio waves
- routers and switches
- PCs and laptops
- firewalls and servers
Explanation and Hint: Network media is a term used to describe the actual physical layer transport along the path over which an electrical signal travels as it moves from one component to another.
-
What allows digital devices to interconnect and transmit data?
- a sensor
- a global positioning sensor
- a network
- a smart phone
Explanation and Hint: A network connects people and devices through wired or wireless means.
-
Which three devices are considered intermediate devices in a network? (Choose three.)
- network printer
- workstation
- router
- switch
- server
- wireless access point
Explanation and Hint: Intermediate devices in a network provide network connectivity to end devices and transfer user data packets during data communications.
-
What are two types of wired high-speed Internet connections? (Choose two.)
- dial-up
- cable
- satellite
- cellular
- DSL
Explanation and Hint: Cable and DSL Internet technologies both use physical cabling to provide an Internet connection to a residence or a small business. Although dial-up is a wired technology, it does not provide a high-speed Internet connection. Satellite and cellular connections provide a wireless Internet connection.
-
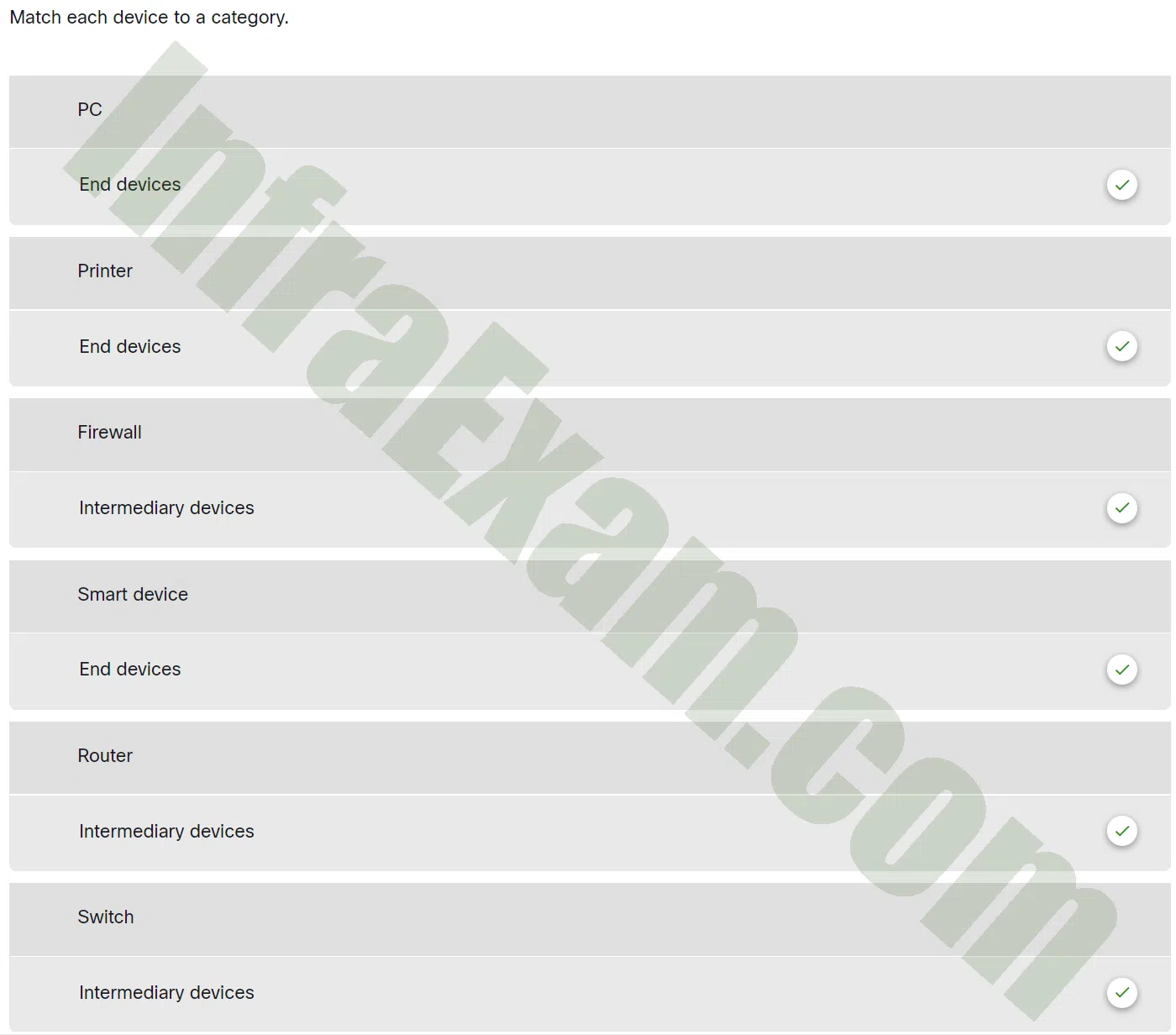
Match each device to a category.
Networking Essentials 3.0 Module 1-4 Checkpoint Exam Build a Small Network Answers 001 - PC —> End devices
- Printer —> End devices
- Firewall —> Intermediary devices
- Smart device —> End devices
- Router —> Intermediary devices
- Switch —> Intermediary devices
Explanation and Hint: Options matched to the correct selection.
end devices intermediary devices PC Firewall Printer Router Smart device Switch
-
Which two devices are considered end devices? (Choose two.)
- hub
- printer
- router
- switch
- laptop
Explanation and Hint: A device that forms the interface between users and the underlying communication network is known as an end device. End devices are either the source or destination of a message.
-
Which two methods are used to directly connect mobile devices such as tablets and smartphones to a data network? (Choose two.)
- wired Ethernet
- Bluetooth
- WiMax
- Wi-Fi
- cellular communications
Explanation and Hint: Mobile devices connect wirelessly to data networks using either Wi-Fi or a telecommunication provider cellular network. Bluetooth is used to connect to peripherals or other local devices over very short distances. Ethernet is a wired network access technology and is not used by mobile devices. Mobile devices do not typically implement WiMAX technology.
-
What are two methods typically used on a mobile device to provide internet connectivity? (Choose two.)
- cellular
- GPS
- NFC
- Wi-Fi
- Bluetooth
Explanation and Hint: Mobile devices commonly use Wi-Fi and cellular to connect to the internet. The cellular connection uses the cellular data network for a fee. The Wi-Fi connection uses an 802.11 wireless network in the area to connect to the internet.
-
In the context of mobile devices, what does the term tethering involve?
- connecting a mobile device to another mobile device or computer to share a network connection
- connecting a mobile device to a USB port on a computer in order to charge the mobile device
- connecting a mobile device to a hands-free headset
- connecting a mobile device to a 4G cellular network
Explanation and Hint: Tethering allows a laptop or PC to use the Internet connection of a mobile device such as a cell phone, usually through a cellular data connection. This allows devices to connect to the Internet in locations where there is no Wi-Fi or cabled connection, but where there is still a cellular data connection.
-
A consumer places a smartphone close to a pay terminal at a store and the shopping charge is successfully paid. Which type of wireless technology was used?
- Wi-Fi
- 3G
- NFC
- Bluetooth
Explanation and Hint: NFC is a wireless technology that allows data to be exchanged between devices that are in very close proximity to each other.
-
What information may be requested when pairing devices over Bluetooth?
- a PIN
- a username
- the SSID
- an IP address
Explanation and Hint: During the pairing process, a personal identification number (PIN) may be requested for authentication.
-
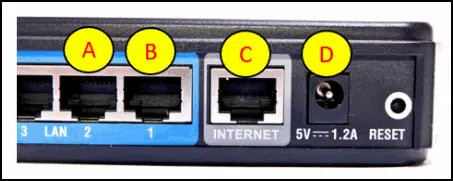
Refer to the exhibit. Which router port connects to the modem provided by the service provider?
Network Basics Module 1 – 4 Checkpoint Exam Answers 01 - A
- D
- B
- C
Explanation and Hint: The ports shown in the diagram are used as follows: The LAN ports, A and B, are used to connect wired devices on the home network. The Internet port, C, is connected to the modem. The port, labeled D, is the 5V DC power port that supplies power to the router.
-
Which technology is used to uniquely identify a WLAN network?
- SSID
- WPA
- WEP
- MAC address table
Explanation and Hint: When a wireless AP or router is being set up, an SSID is configured to uniquely identify the WLAN that is managed by the device.
-
What two radio frequency bands are used in home Wireless LANs? (Choose two.)
- 5 GHz
- 900 GHz
- 9 MHz
- 2.4 GHz
- 5 MHz
Explanation and Hint: The wireless technologies most frequently used in home networks are in the unlicensed 2.4 GHz and 5 GHz frequency ranges.
-
A user is setting up a home wireless network. Which type of device must the user have in order to establish the wireless network and provide access to the internet for multiple home devices?
- hub
- switch
- patch panel
- wireless router
Explanation and Hint: A wireless router connects multiple wireless devices to the network. It will then aggregate the internet access requests from home devices to the internet.
-
Which wireless RF band do IEEE 802.11b/g devices use?
- 900 MHz
- 60 GHz
- 2.4 GHz
- 5 GHz
Explanation and Hint: 900 MHz is an FCC wireless technology that was used before development of the 802.11 standards. 900 MHz devices have a larger coverage range than the higher frequencies have and do not require line of sight between devices. 802.11b/g/n/ad devices all operate at 2.4 GHz. 802.11a/n/ac/ad devices operate at 5 GHz, and 802.11ad devices operate at 60 GHz.
-
Which feature is characteristic of MAC filtering in wireless networks?
- It allows only authorized users to detect the network.
- It encrypts data that is transmitted on a wireless network.
- It restricts computer access to a wireless network.
- It is configured on the computer rather than on the router.
Explanation and Hint: MAC address filtering uses the MAC address to identify which devices are allowed to connect to the wireless network.
-
What is a characteristic of a SOHO network?
- It consists of multiple LANs with backbone infrastructure connections.
- It is a large network, such as those used by corporations and schools, with hundreds or thousands of interconnected hosts.
- It is a collection of interconnected private and public networks.
- It is a small network that connects a few computers to each other and to the internet.
Answers Explanation & Hints: The SOHO network allows computers in a home office or a remote office to connect to a corporate network, or access centralized, shared resources.
-
What is the delay in the amount of time for data to travel between two points on a network?
- bandwidth
- throughput
- latency
- goodput
Answers Explanation & Hints: Latency is a term used to indicate delay when getting a packet from one point to another. Network connections with small amounts of delay are called low-latency networks, whereas network connections with long delays are called high-latency networks. High latency creates bottlenecks in any network communications.
-
What type of network is defined by two computers that can both send and receive requests for resources?
- client/server
- peer-to-peer
- enterprise
- campus
Answers Explanation & Hints: The simplest form of peer-to-peer networking consists of two computers that are directly connected to each other through the use of a wired or wireless connection.
-
What is a role of an intermediary device on a network?
- functions as the primary source of information for end devices
- determines the path and directs data along the way to its final destination
- runs applications that support collaboration for business
- forms the interface between the human network and the underlying communication network
Answers Explanation & Hints: Processes running on the intermediary network devices perform functions like regenerating and re-transmitting data signals, maintaining information about what pathways exist through the network and internetwork, directing data along alternate pathways when there is a link failure, and permitting or denying the flow of data, based on security settings.
-
Which type of technology is used to provide digital data transmissions over cell phone networks?
- 4G
- Wi-Fi
- NFC
- Bluetooth
Answers Explanation & Hints: 3G, 4G, and 4G-LTE are technologies that are used to provide enhanced cell phone networks that are capable of fast data transmission.
-
Which wireless technology is used on smart phones to transmit data to another device within only very close proximity?
- NFC
- Wi-Fi
- 3G/4G
- Bluetooth
Answers Explanation & Hints: Near Field Communications (NFC) is a wireless technology that enables data to be exchanged by devices that are in very close proximity to each other.
-
Which IP configuration parameter provides the IP address of a network device that a computer would use to access the Internet?
- default gateway
- host IP address
- subnet mask
- DNS server
Answers Explanation & Hints: The types of IP configuration on a host device include these:
IP address – identifies the host on the network.
Subnet mask – identifies the network on which the host is connected.
Default gateway – identifies the networking device that the host uses to access the Internet or another remote network.
DNS server – identifies the server that is used to translate a domain name into an IP address.
-
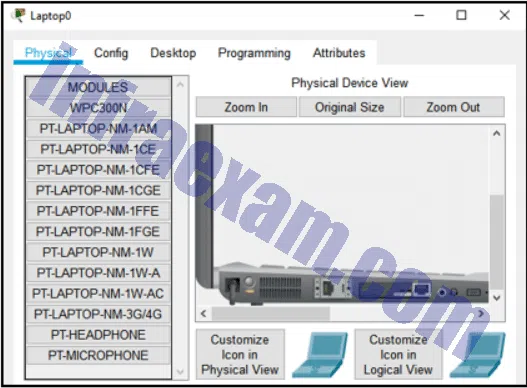
Refer to the exhibit. A student is working on a Packet Tracer lab that includes a home wireless router to be used for both wired and wireless devices. The router and laptop have been placed within the logical workspace. The student adds a laptop device and wants to replace the wired network card with a wireless network card. What is the first step the student should do to install the wireless card?
Modules 1 – 4 Internet Connection Getting Online Pre-Test Exam Answers 02 - Power off the laptop by clicking on the power button.
- Drag the wired network card into the list on the left side.
- Select the Config tab and then the wireless network card checkbox.
- Select the WPC300N option from the left and drag that card to the side of the laptop.
Answers Explanation & Hints: Any time you are removing or installing devices into a PC or laptop within Packet Tracer, turn the power off. For the Packet Tracer laptop, use the Physical tab and click on the power button to the immediate right of the power cord.
-
Which type of cable connection would be used in Packet Tracer to connect a FastEthernet port on a PC to a switch port?
- console
- crossover
- fiber
- straight-through
Answers Explanation & Hints: A FastEthernet straight-through cable is used to connect the FastEthernet0 port on a PC to a switch port.
-
Refer to the exhibit. Which menu item would be used to bring up a web browser?
Modules 1 – 4 Internet Connection Getting Online Pre-Test Exam Answers 02 - Physical
- Config
- Desktop
- Programming
- Attributes
Answers Explanation & Hints: The Desktop menu item is used to access common applications and tools used to configure a device such as the IP address, command prompt, web browser, as well as other apps.
-
Refer to the exhibit. A user is creating a wired and wireless network using Packet Tracer. The user has added a home wireless router, a PC, and a laptop. The user configures the home wireless router. Which icon represents the tool that can be used on the laptop to view the SSID and connect to the wireless router?
Modules 1 – 4 Internet Connection Getting Online Pre-Test Exam Answers 03 - Command Prompt
- IP Configuration
- Web Browser
- PC Wireless
Answers Explanation & Hints: The PC Wireless icon represents the tool that can be used to view and connect to a specific wireless SSID that has been configured on a wireless router.
-
Which type of network cable is commonly used in backbone networks and telephone companies?
- coaxial cable
- fiber-optic cable
- twisted-pair cable
- shielded twisted-pair cable
Answers Explanation & Hints: Fiber-optic cables can carry very large amounts of data and are used extensively by telephone companies and in backbone networks.
-
A group of newly hired entry-level network engineers are talking about the network cabling they are going to have to install as a team. What is a characteristic of Ethernet straight-through UTP cable?
- It can only use the T568A standard at both ends of the cable.
- It can be used to connect two network hosts.
- It is Cisco proprietary.
- It is susceptible to interferences from EMI and RFI.
Answers Explanation & Hints: Ethernet straight-through UTP cable is commonly used to interconnect a host to a switch and a switch to a router. It can use one standard (T568A or T568B) at both ends. EMI and RFI signals can distort and corrupt the data signals being carried by copper media.
-
A network administrator would like to determine the path a packet takes to reach the destination 192.168.1.1. What is the best command to determine the network path?
- tracert 192.168.1.1
- ping 127.0.0.1
- ping 192.168.1.1
- ipconfig 192.168.1.1
Answers Explanation & Hints: The traceroute (tracert) command is used to verify the path to a destination device. The ping c
-
What is a purpose of an IP address?
- It identifies the physical location of a data center.
- It identifies a location in memory from which a program runs.
- It identifies a return address for replying to email messages.
- It identifies the source and destination of data packets.
Answers Explanation & Hints: Packets that are routed across the Internet contain source and destination IP addresses. These addresses are used to determine how the packets should be routed from source to destination by intermediate devices.
-
What terms represent the maximum and actual speed that can be utilized by a device to transfer data?
- bandwidth; throughput
- throughput; bandwidth
- bandwidth; goodput
- throughput; goodput
Answers Explanation & Hints: Bandwidth measures the maximum rate at which a device can transfer data. However, in practice, the actual speed for data transfer could be reduced because of numerous factors like network congestion, overhead etc. This actual rate of transfer is known as throughput.
-
Which factor classifies a host as a server?
- the CPU speed
- the software installed
- the amount of memory
- the network connection
Answers Explanation & Hints: A server is a host with server software installed. Although CPU, memory, and the network connection will determine the performance of a server, it is the server software that provides desired server services.
-
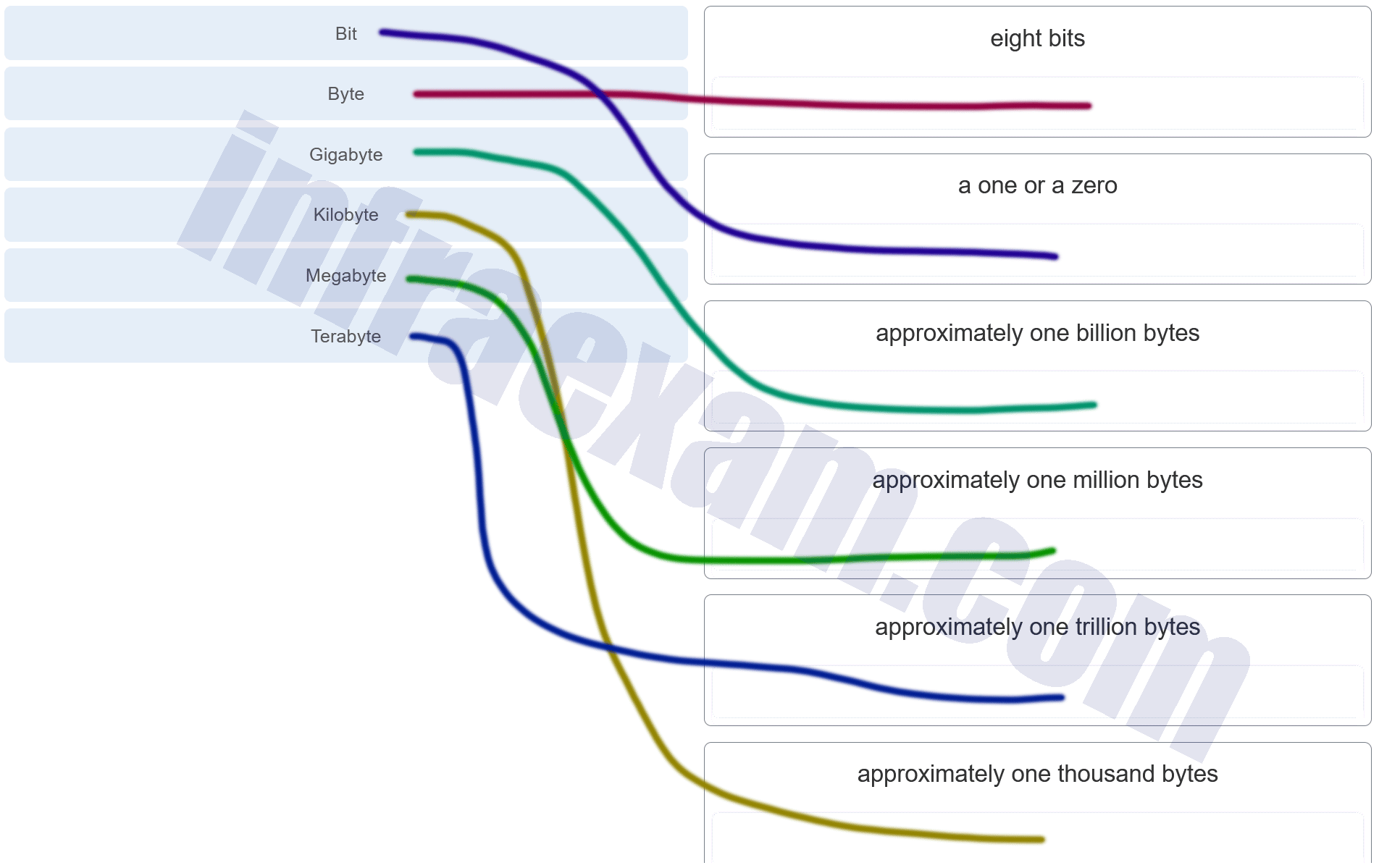
Match the term to the value represented.
Modules 1 – 4 Internet Connection Getting Online Group Exam Answers 001 -
Which term is used to describe a network device that relies on another device to obtain information?
- web server
- console
- server
- client
Answers Explanation & Hints: A client device has software installed which enables it to request the required service from a server device. For instance, a user who uses a web browser is effectively requesting pages from servers all over the web. In this case the browser is considered the client, whereas the device that is responsible for answering the request is considered the server.
-
What is a disadvantage of deploying a peer-to-peer network model?
- difficulty of setup
- lack of centralized administration
- high degree of complexity
- high cost
Answers Explanation & Hints: The simplest peer-to-peer network consists of two computers that are directly connected to each other through the use of a wired or wireless connection. The primary disadvantages of a peer-to-peer network are its lack of central administration, minimal security, and its lack of scalability.
-
Which type of network component can be used to share an attached printer to the network?
- personal computer
- peripheral
- access point
- network media
Answers Explanation & Hints: A peripheral is a device that is not directly connected to a network. In order to be made available on a network, a host is responsible for sharing the peripheral across the network.
-
A wireless network was recently installed in a coffee shop and customer mobile devices are not receiving network configuration information. What should be done to correct the problem?
- Check the connection of the DNS server to the Internet.
- Provide peripheral devices to customers.
- Make sure the DHCP server is functional.
- Ensure that the default gateway device is working properly.
Answers Explanation & Hints: End-user devices can request an address from a pool of addresses that are maintained by a DHCP server.
-
Which network device is used to translate a domain name to the associated IP address?
- router
- DNS server
- DHCP server
- default gateway
Answers Explanation & Hints: A DNS server is a network device that is used to translate a domain name to its IP address. A user will identify a website using a domain name, such as www.cisco.com and a DNS server will translate it to an associated IP address.
-
If you were drawing a physical topology of your school network, what type of information would you include?
- how devices are connected
- the location of devices in the building
- the path that data takes to reach destinations
- the IP addresses of all devices on the network
Answers Explanation & Hints: A physical topology is a diagram that shows where all the devices are physically located in the building.
-
Refer to the exhibit. An instructor wants to show a few prebuilt Packet Tracer sample labs in class. Which menu option would the instructor use to access a sample lab?
Modules 1 – 4 Internet Connection Getting Online Group Exam Answers 01 - File
- Edit
- Options
- View
- Tools
- Extensions
Answers Explanation & Hints: Use the File > Open Samples menu option to browse for the samples provided with Packet Tracer.
-
When authenticating within Packet Tracer, which two items could you use? (Choose two.)
- a previously configured PIN
- a previously configured pattern
- a username associated with NetAcad
- a username associated with a specific school
- an email address found in the NetAcad profile
Answers Explanation & Hints: When Packet Tracer first opens, an authentication screen appears. Use the email address in the NetAcad profile or a username associated with NetAcad.
-
Refer to the exhibit. A student has started a Packet Tracer network that includes a home wireless router to be used for both wired and wireless devices. The router and laptop have been placed within the logical workspace. The student clicks on the laptop and the window that opens is shown in the exhibit. What is the purpose of the modules on the left?
Modules 1 – 4 Internet Connection Getting Online Group Exam Answers 02 - This is the list of modules currently installed in the laptop.
- These are optional modules that can be installed into the module slot if it is currently empty.
- These are modules that can be used by double-clicking on one module so that it automatically installs into the laptop.
- This is a list of modules available from the manufacturer that can be clicked on and “purchased.”
Answers Explanation & Hints: Modules on the left can be installed into the shown device, in this case a laptop. Be sure to power the device off before installing any option.
-
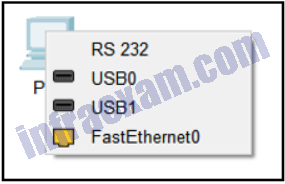
Refer to the exhibit. A student is creating a wired and wireless network in Packet Tracer. After inserting a router, switch, and PC, the student chooses a straight-through cable to connect the PC to the switch. Which connection would be the best port for the student to choose on the PC?
Modules 1 – 4 Internet Connection Getting Online Group Exam Answers 04 - RS 232
- USB0
- USB1
- FastEthernet0
Answers Explanation & Hints: A PC to switch connection is through an Ethernet cable. Connect FastEthernet0 on the PC to any Ethernet port on the switch.
-
Refer to the exhibit. Which menu item would be used to bring up a command prompt environment to be able to ping another network device?
Modules 1 – 4 Internet Connection Getting Online Group Exam Answers 03 - Physical
- Config
- Desktop
- Programming
- Attributes
Answers Explanation & Hints: The Desktop menu item is used to access common application
-
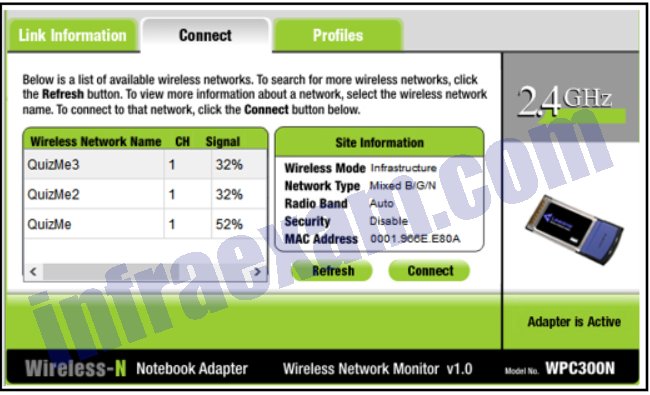
Refer to the exhibit. A home wireless network is being configured within Packet Tracer. The user adds a wireless router, a PC, and three laptops. The user is reviewing the wireless connection on one of the laptops. What can be determined?
Modules 1 – 4 Internet Connection Getting Online Group Exam Answers 05 - Because the password is not enabled, the laptop cannot connect to the wireless router.
- All three laptops are connected to the wireless network successfully.
- The laptop is connected to a wireless network.
- The laptop must have a different wireless NIC installed before being able to connect to the wireless router.
Answers Explanation & Hints: A home wireless router could be configured for a 2.4 GHz and multiple 5 GHz wireless networks, each with a unique SSID such as QuizMe3, QuizMe2, and QuizMe. The wireless NIC is active and connected to a wireless network as indicated by the words Adapter is Active. The wireless router has not been configured with wireless security.
-
Which type of network cable is commonly used to connect office computers to the local network?
- coaxial cable
- twisted-pair cable
- glass fiber-optic cable
- plastic fiber-optic cable
Answers Explanation & Hints: Twisted-pair is a type of copper cable used to interconnect devices on a local network.
-
Which criterion can be used to select the appropriate type of network media for a network?
- the types of data that need to be prioritized
- the cost of the end devices that are used in the network
- the number of intermediary devices that are installed in the network
- the environment where the selected medium is to be installed
Answers Explanation & Hints: Criteria for choosing a network medium are the distance across which the selected medium can successfully carry a signal, the environment in which the selected medium is to be installed, the amount of data and the speed at which the data must be transmitted, and the cost of the medium and its installation.
-
What are two sources of electromagnetic interference that can affect data transmissions? (Choose two.)
- LED monitor
- microwave oven
- infrared remote control
- cordless phone
- florescent light fixture
Answers Explanation & Hints: Electromagnetic interference or EMI is commonly caused by equipment such as microwave ovens and fluorescent light fixtures.
-
What are two advantages of using fiber-optic cabling to interconnect devices? (Choose two.)
- Fiber-optic cable is immune from EMI and RFI.
- Fiber-optic cables can extend several miles.
- Fiber-optic cables use extra shielding to protect copper wires.
- Fiber-optic cables are easy to install..
- Fiber-optic cables are commonly found in both homes and small businesses.
Answers Explanation & Hints: Fiber-optic cables provide immunity to both EMI and RFI and a single cable can extend for several miles before regeneration is needed.
-
Which type of network cable is used to connect the components that make up satellite communication systems?
- coaxial
- fiber-optic
- shielded twisted-pair
- unshielded twisted-pair
Answers Explanation & Hints: Coaxial cable is commonly used to connect the various components that make up satellite communication systems and cable TV.
-
Which statement describes the use of the ping command?
- The ping command tests end-to-end connectivity between two devices.
- The ping command can be used to determine the exact location of the problem when troubleshooting reachability issues.
- The ping command can be used to test reachability using the physical address of the device.
- The ping command shows current Layer 4 sessions.
Answers Explanation & Hints: The ping command is used to test end-to-end connectivity between the source and destination IP address. It measures the time it takes a test message to make a round trip between the two end points. However, if the message does not reach the destination, or in the case of delays, there is no way to determine where the problem is located.