PCCET : Palo Alto Networks Certified Cybersecurity Entry-level Technician : Part 01
-
Which analysis detonates previously unknown submissions in a custom-built, evasion-resistant virtual environment to determine real-world effects and behavior?
- Dynamic
- Pre-exploit protection
- Bare-metal
- Static
-
What is required for a SIEM to operate correctly to ensure a translated flow from the system of interest to the SIEM data lake?
- connectors and interfaces
- infrastructure and containers
- containers and developers
- data center and UPS
-
Which type of Wi-Fi attack depends on the victim initiating the connection?
- Evil twin
- Jasager
- Parager
- Mirai
-
Which term describes data packets that move in and out of the virtualized environment from the host network or a corresponding traditional data center?
- North-South traffic
- Intrazone traffic
- East-West traffic
- Interzone traffic
-
Which organizational function is responsible for security automation and eventual vetting of the solution to help ensure consistency through machine-driven responses to security issues?
- NetOps
- SecOps
- SecDevOps
- DevOps
-
DRAG DROP
Given the graphic, match each stage of the cyber-attack lifecycle to its description.
PCCET Palo Alto Networks Certified Cybersecurity Entry-level Technician Part 01 Q06 001 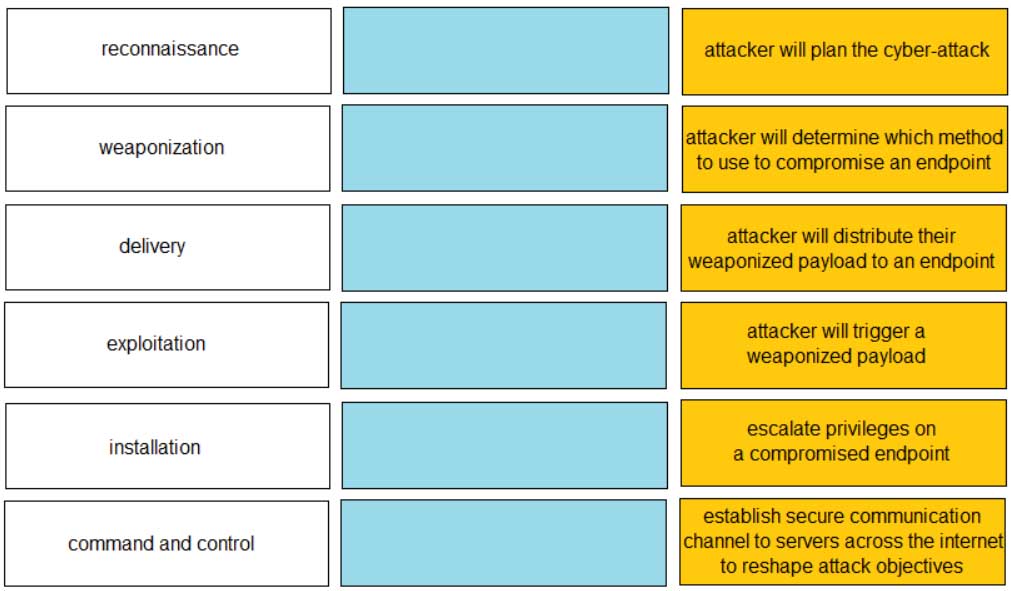
PCCET Palo Alto Networks Certified Cybersecurity Entry-level Technician Part 01 Q06 002 Question 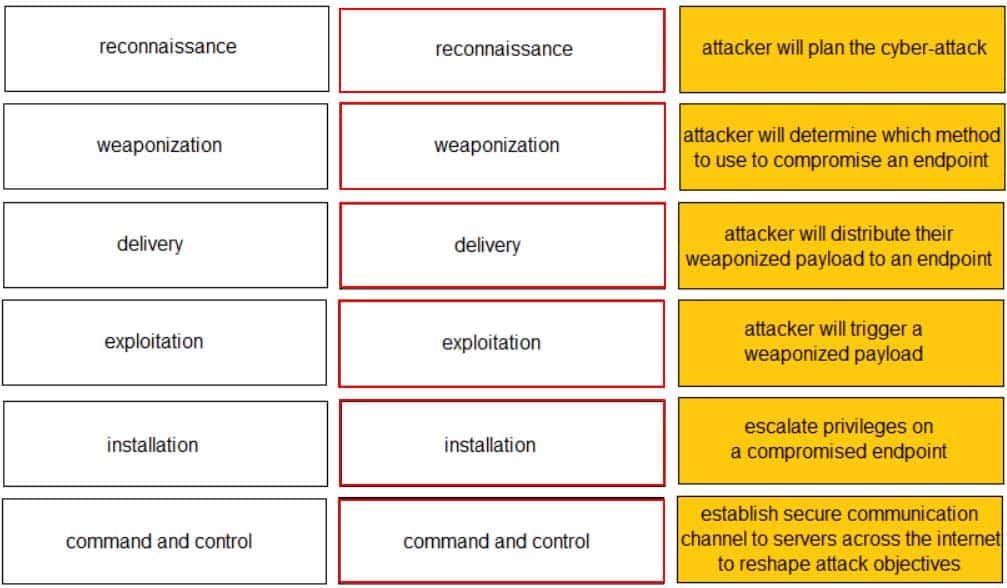
PCCET Palo Alto Networks Certified Cybersecurity Entry-level Technician Part 01 Q06 002 Answer -
DRAG DROP
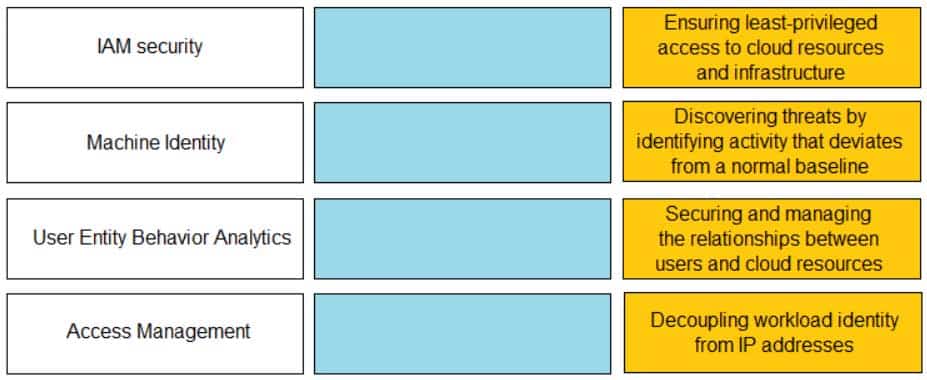
Match the Identity and Access Management (IAM) security control with the appropriate definition.
PCCET Palo Alto Networks Certified Cybersecurity Entry-level Technician Part 01 Q07 003 Question 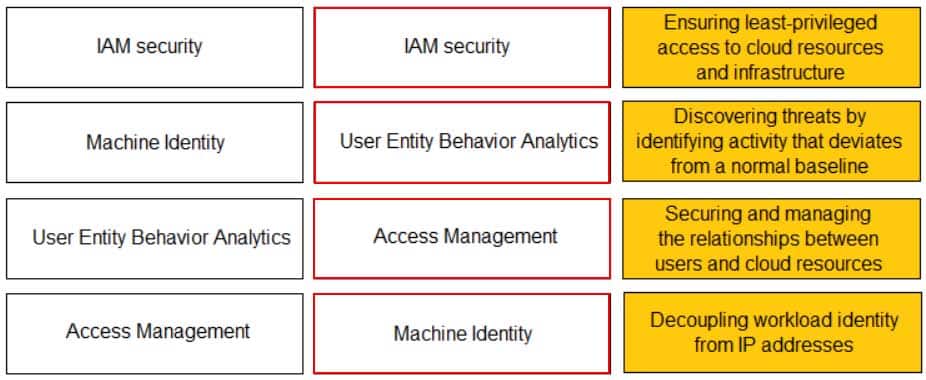
PCCET Palo Alto Networks Certified Cybersecurity Entry-level Technician Part 01 Q07 003 Answer -
On an endpoint, which method should you use to secure applications against exploits?
- endpoint-based firewall
- strong user passwords
- full-disk encryption
- software patches
-
Which not-for-profit organization maintains the common vulnerability exposure catalog that is available through their public website?
- Department of Homeland Security
- MITRE
- Office of Cyber Security and Information Assurance
- Cybersecurity Vulnerability Research Center
-
Which Palo Alto Networks tools enable a proactive, prevention-based approach to network automation that accelerates security analysis?
- MineMeld
- AutoFocus
- WildFire
- Cortex XDR
-
Which endpoint product from Palo Alto Networks can help with SOC visibility?
- STIX
- Cortex XDR
- WildFire
- AutoFocus
-
Which technique changes protocols at random during a session?
- use of non-standard ports
- port hopping
- hiding within SSL encryption
- tunneling within commonly used services
-
What is the primary security focus after consolidating data center hypervisor hosts within trust levels?
- control and protect inter-host traffic using routers configured to use the Border Gateway Protocol (BGP) dynamic routing protocol
- control and protect inter-host traffic by exporting all your traffic logs to a sysvol log server using the User Datagram Protocol (UDP)
- control and protect inter-host traffic by using IPv4 addressing
- control and protect inter-host traffic using physical network security appliances
-
Which product from Palo Alto Networks extends the Security Operating Platform with the global threat intelligence and attack context needed to accelerate analysis, forensics, and hunting workflows?
- Global Protect
- WildFire
- AutoFocus
- STIX
-
DRAG DROP
Match the description with the VPN technology.
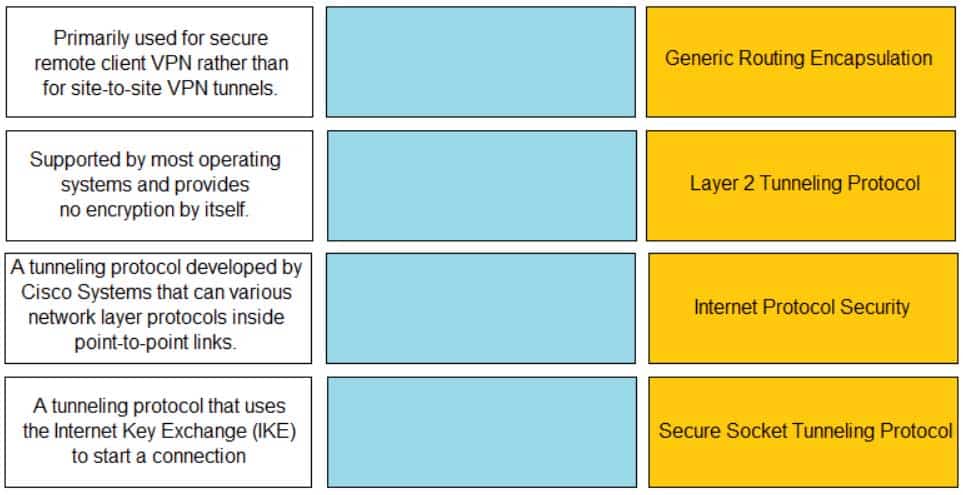
PCCET Palo Alto Networks Certified Cybersecurity Entry-level Technician Part 01 Q15 004 Question 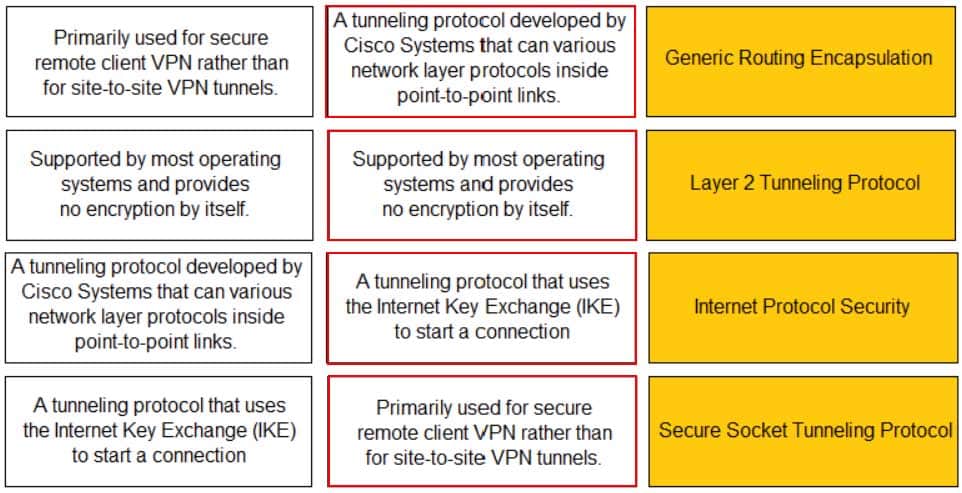
PCCET Palo Alto Networks Certified Cybersecurity Entry-level Technician Part 01 Q15 004 Answer -
Which characteristic of serverless computing enables developers to quickly deploy application code?
- Uploading cloud service autoscaling services to deploy more virtual machines to run their application code based on user demand
- Uploading the application code itself, without having to provision a full container image or any OS virtual machine components
- Using cloud service spot pricing to reduce the cost of using virtual machines to run their application code
- Using Container as a Service (CaaS) to deploy application containers to run their code.
-
Which key component is used to configure a static route?
- router ID
- enable setting
- routing protocol
- next hop IP address
-
A native hypervisor runs:
- with extreme demands on network throughput
- only on certain platforms
- within an operating system’s environment
- directly on the host computer’s hardware
-
Which Palo Alto Networks product provides playbooks with 300+ multivendor integrations that help solve any security use case?
- Cortex XSOAR
- Prisma Cloud
- AutoFocus
- Cortex XDR
-
Which activities do local organization security policies cover for a SaaS application?
- how the data is backed up in one or more locations
- how the application can be used
- how the application processes the data
- how the application can transit the Internet