PCCET : Palo Alto Networks Certified Cybersecurity Entry-level Technician : Part 02
-
Which Palo Alto Networks subscription service complements App-ID by enabling you to configure the next-generation firewall to identify and control access to websites and to protect your organization from websites hosting malware and phishing pages?
- Threat Prevention
- DNS Security
- WildFire
- URL Filtering
-
Which option would be an example of PII that you need to prevent from leaving your enterprise network?
- Credit card number
- Trade secret
- National security information
- A symmetric encryption key
-
Which network analysis tool can be used to record packet captures?
- Smart IP Scanner
- Wireshark
- Angry IP Scanner
- Netman
-
Systems that allow for accelerated incident response through the execution of standardized and automated playbooks that work upon inputs from security technology and other data flows are known as what?
- XDR
- STEP
- SOAR
- SIEM
-
Which Palo Alto Networks tool is used to prevent endpoint systems from running malware executables such as viruses, trojans, and rootkits?
- Expedition
- Cortex XDR
- AutoFocus
- App-ID
-
What does SIEM stand for?
- Security Infosec and Event Management
- Security Information and Event Management
- Standard Installation and Event Media
- Secure Infrastructure and Event Monitoring
-
DRAG DROP
Match the IoT connectivity description with the technology.
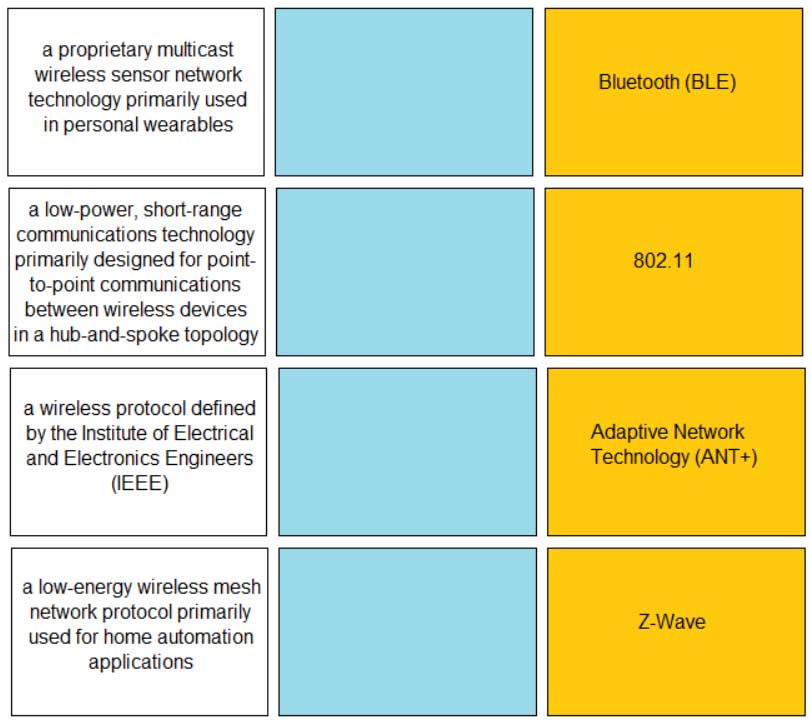
PCCET Palo Alto Networks Certified Cybersecurity Entry-level Technician Part 02 Q07 005 Question 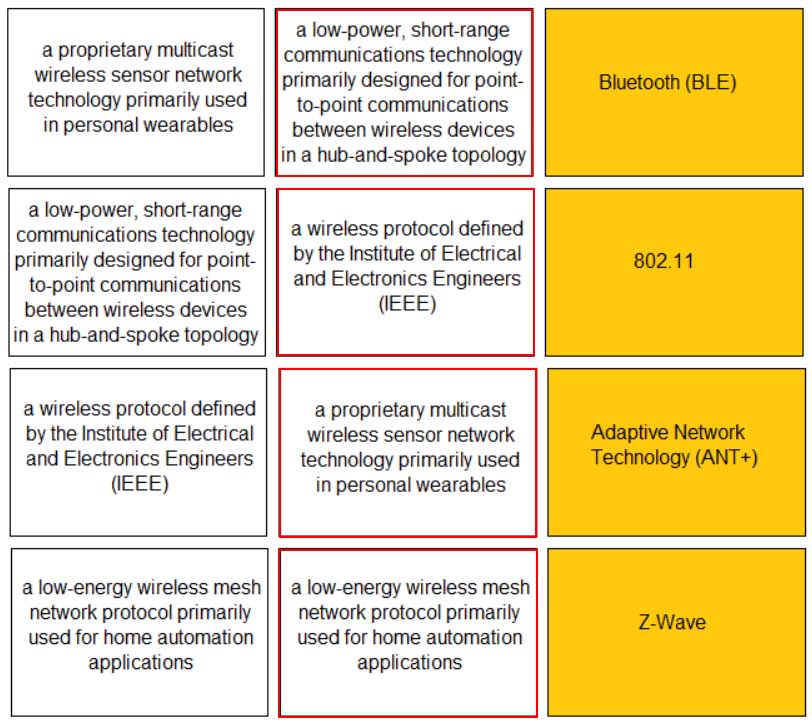
PCCET Palo Alto Networks Certified Cybersecurity Entry-level Technician Part 02 Q07 005 Answer -
Which option is an example of a North-South traffic flow?
- Lateral movement within a cloud or data center
- An internal three-tier application
- Client-server interactions that cross the edge perimeter
- Traffic between an internal server and internal user
-
Which aspect of a SaaS application requires compliance with local organizational security policies?
- Types of physical storage media used
- Data-at-rest encryption standards
- Acceptable use of the SaaS application
- Vulnerability scanning and management
-
Which option describes the “selective network security virtualization” phase of incrementally transforming data centers?
- during the selective network security virtualization phase, all intra-host communication paths are strictly controlled
- during the selective network security virtualization phase, all intra-host traffic is forwarded to a Web proxy server
- during the selective network security virtualization phase, all intra-host traffic is encapsulated and encrypted using the IPSEC protocol
- during the selective network security virtualization phase, all intra-host traffic is load balanced
-
Which TCP/IP sub-protocol operates at the Layer7 of the OSI model?
- UDP
- MAC
- SNMP
- NFS
-
Anthem server breaches disclosed Personally Identifiable Information (PII) from a number of its servers. The infiltration by hackers was attributed to which type of vulnerability?
- an intranet-accessed contractor’s system that was compromised
- exploitation of an unpatched security vulnerability
- access by using a third-party vendor’s password
- a phishing scheme that captured a database administrator’s password
-
Routing Information Protocol (RIP), uses what metric to determine how network traffic should flow?
- Shortest Path
- Hop Count
- Split Horizon
- Path Vector
-
Why is it important to protect East-West traffic within a private cloud?
- All traffic contains threats, so enterprises must protect against threats across the entire network
- East-West traffic contains more session-oriented traffic than other traffic
- East-West traffic contains more threats than other traffic
- East-West traffic uses IPv6 which is less secure than IPv4
-
Which IPsec feature allows device traffic to go directly to the Internet?
- Split tunneling
- Diffie-Hellman groups
- d.Authentication Header (AH)
- IKE Security Association
-
Which attacker profile uses the internet to recruit members to an ideology, to train them, and to spread fear and include panic?
- cybercriminals
- state-affiliated groups
- hacktivists
- cyberterrorists
-
What are two key characteristics of a Type 1 hypervisor? (Choose two.)
- is hardened against cyber attacks
- runs without any vulnerability issues
- runs within an operating system
- allows multiple, virtual (or guest) operating systems to run concurrently on a single physical host computer
-
The customer is responsible only for which type of security when using a SaaS application?
- physical
- platform
- data
- infrastructure
-
Which Palo Alto subscription service identifies unknown malware, zero-day exploits, and advanced persistent threats (APTs) through static and dynamic analysis in a scalable, virtual environment?
- DNS Security
- URL Filtering
- WildFire
- Threat Prevention
-
In which step of the cyber-attack lifecycle do hackers embed intruder code within seemingly innocuous files?
- weaponization
- reconnaissance
- exploitation
- delivery
Subscribe
0 Comments
Newest