PCCET : Palo Alto Networks Certified Cybersecurity Entry-level Technician : Part 03
-
Which endpoint tool or agent can enact behavior-based protection?
- AutoFocus
- Cortex XDR
- DNS Security
- MineMeld
-
Which tool supercharges security operations center (SOC) efficiency with the world’s most comprehensive operating platform for enterprise security?
- Prisma SAAS
- WildFire
- Cortex XDR
- Cortex XSOAR
-
During the OSI layer 3 step of the encapsulation process, what is the Protocol Data Unit (PDU) called when the IP stack adds source (sender) and destination (receiver) IP addresses?
- Frame
- Segment
- Packet
- Data
-
Which core component is used to implement a Zero Trust architecture?
- VPN Concentrator
- Content Identification
- Segmentation Platform
- Web Application Zone
-
In addition to local analysis, what can send unknown files to WildFire for discovery and deeper analysis to rapidly detect potentially unknown malware?
- Cortex XDR
- AutoFocus
- MineMild
- Cortex XSOAR
-
On an endpoint, which method is used to protect proprietary data stored on a laptop that has been stolen?
- operating system patches
- full-disk encryption
- periodic data backups
- endpoint-based firewall
-
Why have software developers widely embraced the use of containers?
- Containers require separate development and production environments to promote authentic code.
- Containers share application dependencies with other containers and with their host computer.
- Containers simplify the building and deploying of cloud native applications.
- Containers are host specific and are not portable across different virtual machine hosts.
-
When signature-based antivirus software detects malware, what three things does it do to provide protection? (Choose three.)
- decrypt the infected file using base64
- alert system administrators
- quarantine the infected file
- delete the infected file
- remove the infected file’s extension
-
Which option is a Prisma Access security service?
- Compute Security
- Firewall as a Service (FWaaS)
- Virtual Private Networks (VPNs)
- Software-defined wide-area networks (SD-WANs)
-
Which pillar of Prisma Cloud application security addresses ensuring that your cloud resources and SaaS applications are correctly configured?
- visibility, governance, and compliance
- network protection
- dynamic computing
- compute security
-
Which item accurately describes a security weakness that is caused by implementing a “ports first” data security solution in a traditional data center?
- You may have to use port numbers greater than 1024 for your business-critical applications.
- You may have to open up multiple ports and these ports could also be used to gain unauthorized entry into your datacenter.
- You may not be able to assign the correct port to your business-critical applications.
- You may not be able to open up enough ports for your business-critical applications which will increase the attack surface area.
-
DRAG DROP
Match each description to a Security Operating Platform key capability.
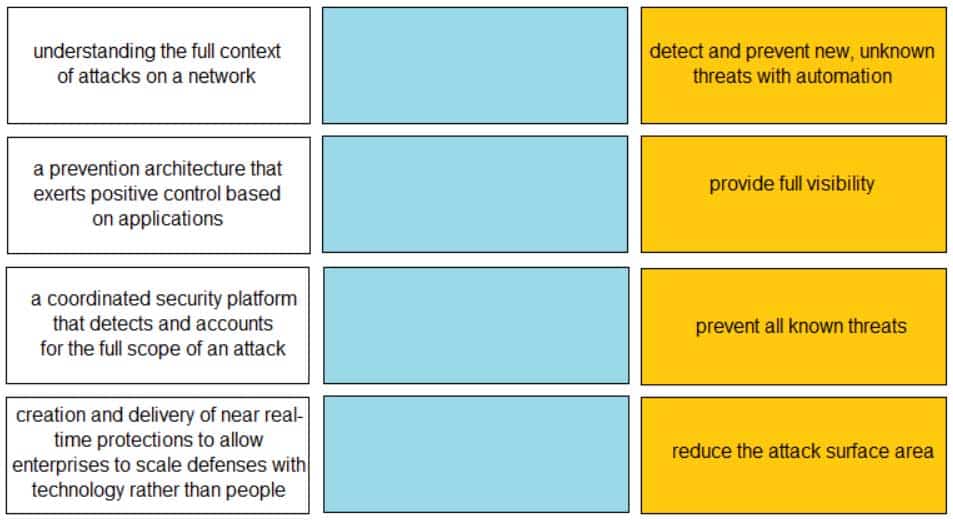
PCCET Palo Alto Networks Certified Cybersecurity Entry-level Technician Part 03 Q12 006 Question 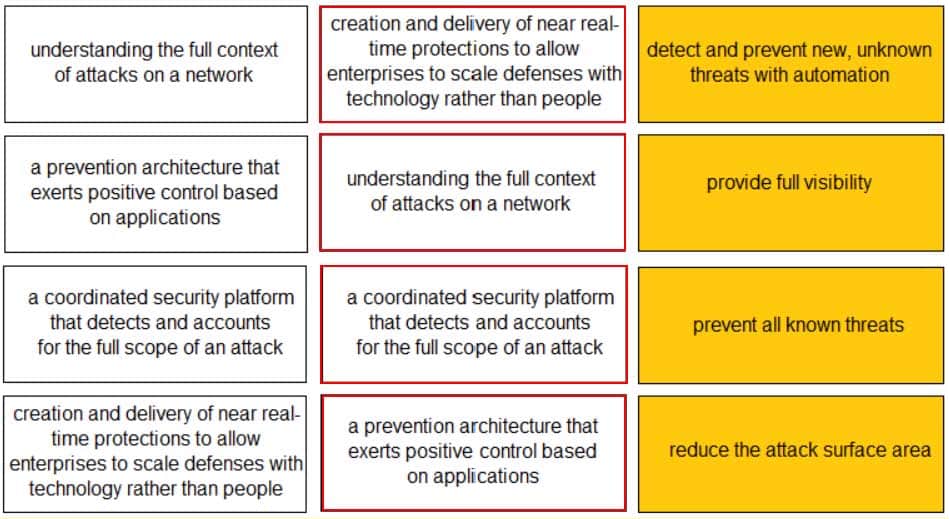
PCCET Palo Alto Networks Certified Cybersecurity Entry-level Technician Part 03 Q12 006 Answer -
Which statement describes DevOps?
- DevOps is its own separate team
- DevOps is a set of tools that assists the Development and Operations teams throughout the software delivery process
- DevOps is a combination of the Development and Operations teams
- DevOps is a culture that unites the Development and Operations teams throughout the software delivery process
-
Which product from Palo Alto Networks enables organizations to prevent successful cyberattacks as well as simplify and strengthen security processes?
- Expedition
- AutoFocus
- MineMeld
- Cortex XDR
-
Which network firewall operates up to Layer 4 (Transport layer) of the OSI model and maintains information about the communication sessions which have been established between hosts on trusted and untrusted networks?
- Group policy
- Stateless
- Stateful
- Static packet-filter
-
Which subnet does the host 192.168.19.36/27 belong?
- 192.168.19.0
- 192.168.19.16
- 192.168.19.64
- 192.168.19.32
-
DRAG DROP
Order the OSI model with Layer7 at the top and Layer1 at the bottom.
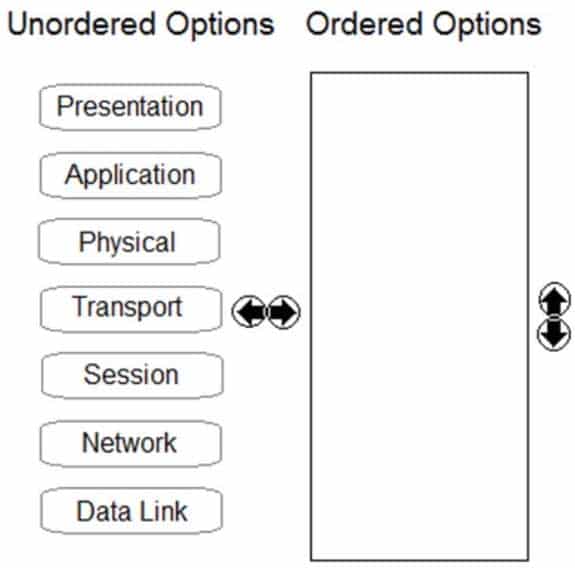
PCCET Palo Alto Networks Certified Cybersecurity Entry-level Technician Part 03 Q17 007 Question 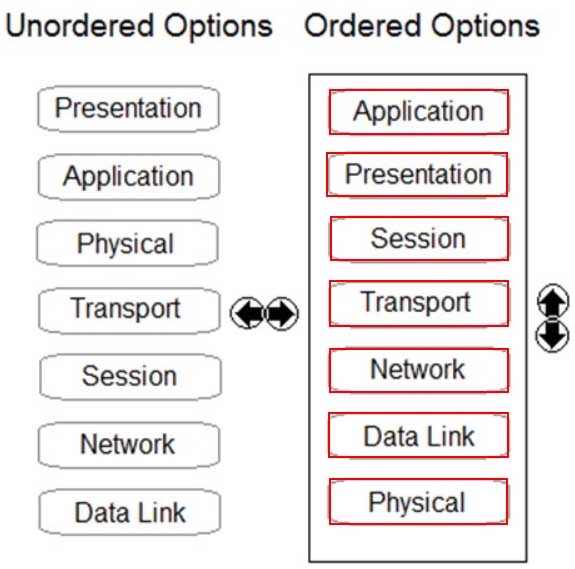
PCCET Palo Alto Networks Certified Cybersecurity Entry-level Technician Part 03 Q17 007 Answer -
How does adopting a serverless model impact application development?
- costs more to develop application code because it uses more compute resources
- slows down the deployment of application code, but it improves the quality of code development
- reduces the operational overhead necessary to deploy application code
- prevents developers from focusing on just the application code because you need to provision the underlying infrastructure to run the code
-
In addition to integrating the network and endpoint components, what other component does Cortex integrate to speed up IoC investigations?
- Computer
- Switch
- Infrastructure
- Cloud
-
In the attached network diagram, which device is the switch?
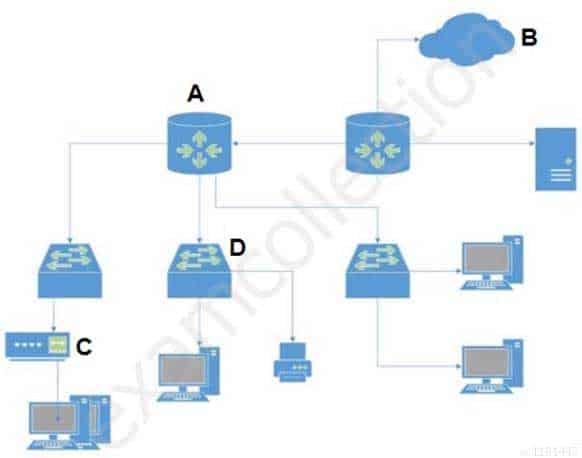
PCCET Palo Alto Networks Certified Cybersecurity Entry-level Technician Part 03 Q20 008 - A
- B
- C
- D
Subscribe
0 Comments
Newest