PCCET : Palo Alto Networks Certified Cybersecurity Entry-level Technician : Part 04
-
In SecOps, what are two of the components included in the identify stage? (Choose two.)
- Initial Research
- Change Control
- Content Engineering
- Breach Response
-
Data Loss Prevention (DLP) and Cloud Access Security Broker (CASB) fall under which Prisma access service layer?
- Network
- Management
- Cloud
- Security
-
In which two cloud computing service models are the vendors responsible for vulnerability and patch management of the underlying operating system? (Choose two.)
- SaaS
- PaaS
- On-premises
- IaaS
-
SecOps consists of interfaces, visibility, technology, and which other three elements? (Choose three.)
- People
- Accessibility
- Processes
- Understanding
- Business
-
Which IoT connectivity technology is provided by satellites?
- 4G/LTE
- VLF
- L-band
- 2G/2.5G
-
What does Palo Alto Networks Cortex XDR do first when an endpoint is asked to run an executable?
- run a static analysis
- check its execution policy
- send the executable to WildFire
- run a dynamic analysis
-
What is the key to “taking down” a botnet?
- prevent bots from communicating with the C2
- install openvas software on endpoints
- use LDAP as a directory service
- block Docker engine software on endpoints
-
How does Prisma SaaS provide protection for Sanctioned SaaS applications?
- Prisma SaaS connects to an organizations internal print and file sharing services to provide protection and sharing visibility
- Prisma SaaS does not provide protection for Sanctioned SaaS applications because they are secure
- Prisma access uses Uniform Resource Locator (URL) Web categorization to provide protection and sharing visibility
- Prisma SaaS connects directly to sanctioned external service providers SaaS application service to provide protection and sharing visibility
-
Which type of Software as a Service (SaaS) application provides business benefits, is fast to deploy, requires minimal cost and is infinitely scalable?
- Benign
- Tolerated
- Sanctioned
- Secure
-
How does DevSecOps improve the Continuous Integration/Continuous Deployment (CI/CD) pipeline?
- DevSecOps improves pipeline security by assigning the security team as the lead team for continuous deployment
- DevSecOps ensures the pipeline has horizontal intersections for application code deployment
- DevSecOps unites the Security team with the Development and Operations teams to integrate security into the CI/CD pipeline
- DevSecOps does security checking after the application code has been processed through the CI/CD pipeline
-
Which type of LAN technology is being displayed in the diagram?
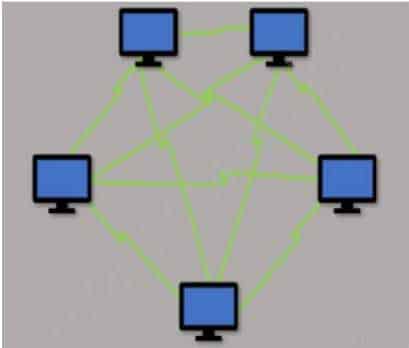
PCCET Palo Alto Networks Certified Cybersecurity Entry-level Technician Part 04 Q11 009 - Star Topology
- Spine Leaf Topology
- Mesh Topology
- Bus Topology
-
An Administrator wants to maximize the use of a network address. The network is 192.168.6.0/24 and there are three subnets that need to be created that can not overlap. Which subnet would you use for the network with 120 hosts?
Requirements for the three subnets:
Subnet 1: 3 host addresses
Subnet 2: 25 host addresses
Subnet 3: 120 host addresses- 192.168.6.168/30
- 192.168.6.0/25
- 192.168.6.160/29
- 192.168.6.128/27
-
Which two network resources does a directory service database contain? (Choose two.)
- Services
- /etc/shadow files
- Users
- Terminal shell types on endpoints
-
Which model would a customer choose if they want full control over the operating system(s) running on their cloud computing platform?
- SaaS
- DaaS
- PaaS
- IaaS
-
What is a key advantage and key risk in using a public cloud environment?
- Multi-tenancy
- Dedicated Networks
- Dedicated Hosts
- Multiplexing
Subscribe
0 Comments
Newest