PCCSE : Prisma Certified Cloud Security Engineer : Part 02
-
The security team wants to protect a web application container from an SQLi attack.
Which type of policy should the administrator create to protect the container?
- CNAF
- Runtime
- Compliance
- CNNF
Explanation:
Reference:
https://docs.paloaltonetworks.com/prisma/prisma-cloud/20-09/prisma-cloud-compute-edition-admin/firewalls/waas
-
An S3 bucket within AWS has generated an alert by violating the Prisma Cloud Default policy “AWS S3 buckets are accessible to public”. The policy definition follows:
config where cloud.type = 'aws' AND api.name='aws-s3api-get-bucket-acl' AND json.rule="((((acl.grants[?(@.grantee=='AllUsers')] size > 0) or policyStatus.isPublic is true) and publicAccessBlockConfiguration does not exist) or ((acl.grants[?(@.grantee=='AllUsers')] size > 0) and publicAccessBlockConfiguration.ignorePublicAcis is false) or (policyStatus.isPublic is true and publicAccessBlockConfiguration.restrictPublicBuckets is false)) and websiteConfiguration does not exist"
Why did this alert get generated?
- an event within the cloud account
- network traffic to the S3 bucket
- configuration of the S3 bucket
- anomalous behaviors
-
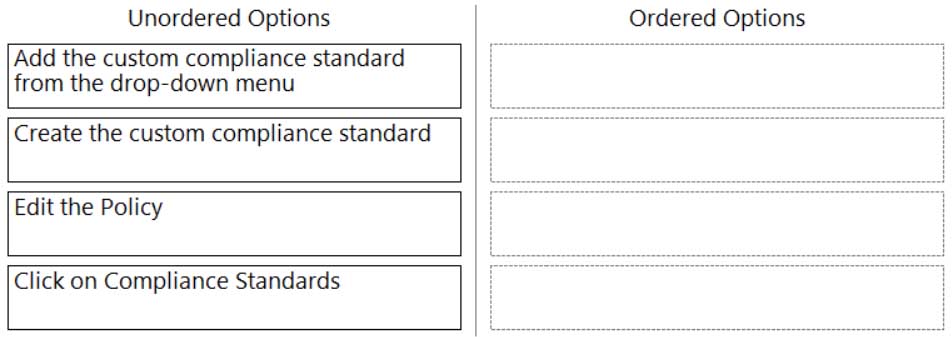
DRAG DROP
Which order of steps map a policy to a custom compliance standard?
(Drag the steps into the correct order of occurrence, from the first step to the last.)
PCCSE Prisma Certified Cloud Security Engineer Part 02 Q03 001 Question 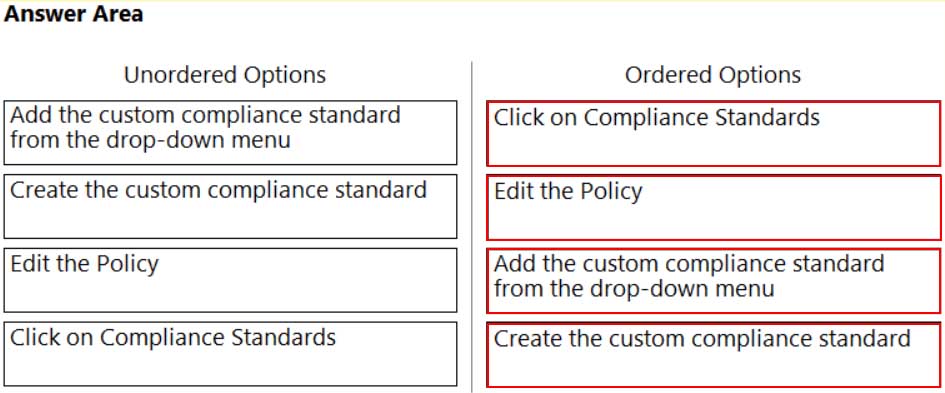
PCCSE Prisma Certified Cloud Security Engineer Part 02 Q03 001 Answer -
A customer is interested in PCI requirements and needs to ensure that no privilege containers can start in the environment.
Which action needs to be set for “do not use privileged containers”?
- Prevent
- Alert
- Block
- Fail
Explanation:Reference: https://docs.paloaltonetworks.com/content/dam/techdocs/en_US/pdf/prisma/prisma-cloud/prisma-cloud-policy-reference/prisma-cloud-policy-reference.pdf (133) -
Given an existing ECS Cluster, which option shows the steps required to install the Console in Amazon ECS?
- The console cannot natively run in an ECS cluster.
A onebox deployment should be used. - Download and extract the release tarball
Ensure that each node has its own storage for Console data
Create the Console task definition
Deploy the task definition - Download and extract release tarball
Download task from AWS
Create the Console task definition
Deploy the task definition - Download and extract the release tarball
Create an EFS file system and mount to each node in the cluster
Create the Console task definition
Deploy the task definition
Explanation:Reference:https://docs.paloaltonetworks.com/prisma/prisma-cloud/19-11/prisma-cloud-compute-edition-admin/install/install_amazon_ecs.html - The console cannot natively run in an ECS cluster.
-
Which options show the steps required to upgrade Console when using projects?
- Upgrade all Supervisor Consoles
Upgrade Central Console - Upgrade Central Console
Upgrade Central Console Defenders - Upgrade Defender
Upgrade Central Console
Upgrade Supervisor Consoles - Upgrade Central Console
Upgrade all Supervisor Consoles
Explanation:Reference:https://docs.paloaltonetworks.com/prisma/prisma-cloud/20-09/prisma-cloud-compute-edition-admin/upgrade/upgrade_process.html - Upgrade all Supervisor Consoles
-
A customer has Prisma Cloud Enterprise and host Defenders deployed.
What are two options that allow an administrator to upgrade Defenders? (Choose two.)
- with auto-upgrade, the host Defender will auto-upgrade.
- auto deploy the Lambda Defender.
- click the update button in the web-interface.
- generate a new DaemonSet file.
-
Which intensity setting for anomaly alerts is used for the measurement of 100 events over 30 days?
- High
- Medium
- Low
- Very High
Explanation:Reference:https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin/manage-prisma-cloud-administrators/define-prisma-cloud-enterprise-settings.html -
Given this information:
– The Console is located at https://prisma-console.mydomain.local
– The username is: cluster
– The password is: password123
– The image to scan is: myimage:latestWhich twistcli command should be used to scan a Container for vulnerabilities and display the details about each vulnerability?
-
twistcli images scan --console-address https://prisma-console.mydomain.local -u cluster -p password123 --details myimage:latest
-
twistcli images scan --console-address prisma-console.mydomain.local -u cluster -p password123 --vulnerability-details myimage:latest
-
twistcli images scan --address prisma-console.mydomain.local -u cluster -p password123 --vulnerability-details myimage:latest -
twistcli images scan --address https://prisma-console.mydomain.local -u cluster -p password123 --details myimage:latest
Explanation:Reference:https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin-compute/tools/twistcli_scan_images -
-
The development team wants to block Cross Site Scripting attacks from pods in its environment.
How should the team construct the CNAF policy to protect against this attack?
- create a Host CNAF policy, targeted at a specific resource, check the box for XSS attack protection, and set the action to “prevent”.
- create a Container CNAF policy, targeted at a specific resource, check the box for XSS attack protection, and set the action to alert.
- create a Container CNAF policy, targeted at a specific resource, check the box for XSS protection, and set the action to prevent.
- create a Container CNAF policy, targeted at a specific resource, and they should set “Explicitly allowed inbound IP sources” to the IP address of the pod.
-
The Prisma Cloud administrator has configured a new policy.
Which steps should be used to assign this policy to a compliance standard?
- Edit the policy, go to step 3 (Compliance Standards), click + at the bottom, select the compliance standard, fill in the other boxes, and then click Confirm.
- Create the Compliance Standard from Compliance tab, and then select Add to Policy.
- Open the Compliance Standards section of the policy, and then save.
- Custom policies cannot be added to existing standards.
Explanation:Reference:https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin/prisma-cloud-policies/create-a-policy.html -
An administrator wants to install the Defenders to a Kubernetes cluster. This cluster is running the console on the default service endpoint and will be exporting to YAML.
– Console Address: $CONSOLE_ADDRESS
– Websocket Address: $WEBSOCKET_ADDRESS
– User: $ADMIN_USERWhich command generates the YAML file for Defender install?
-
<PLATFORM>/twistcli defender \ --address $CONSOLE_ADDRESS \ --user $ADMIN_USER \ --cluster-address $CONSOLE_ADDRESS
-
<PLATFORM>/twistcli defender export kubernetes \ --address $WEBSOCKET_ADDRESS \ --user $ADMIN_USER \ --cluster-address $CONSOLE_ADDRESS
-
<PLATFORM>/twistcli defender YAML kubernetes \ --address $CONSOLE_ADDRESS \ --user $ADMIN_USER \ --cluster-address $WEBSOCKET_ADDRESS
-
<PLATFORM>/twistcli defender export kubernetes \ --address $CONSOLE_ADDRESS \ --user $ADMIN_USER \ --cluster-address $WEBSOCKET_ADDRESS
Explanation:Reference:https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin-compute/install/install_kubernetes.html -
-
Which options show the steps required after upgrade of Console?
- Uninstall Defenders
Upgrade Jenkins Plugin
Upgrade twistcli where applicable
Allow the Console to redeploy the Defender - Update the Console image in the Twistlock hosted registry
Update the Defender image in the Twistlock hosted registry
Uninstall Defenders - Upgrade Defenders
Upgrade Jenkins Plugin
Upgrade twistcli where applicable - Update the Console image in the Twistlock hosted registry
Update the Defender image in the Twistlock hosted registry
Redeploy Console
- Uninstall Defenders
-
An organization wants to be notified immediately to any “High Severity” alerts for the account group “Clinical Trials” via Slack.
Which option shows the steps the organization can use to achieve this goal?
- 1. Configure Slack Integration
2. Create an alert rule and select “Clinical Trials” as the account group
3. Under the “Select Policies” tab, filter on severity and select “High”
4. Under the Set Alert Notification tab, choose Slack and populate the channel
5. Set Frequency to “As it Happens” - 1. Create an alert rule and select “Clinical Trials” as the account group
2. Under the “Select Policies” tab, filter on severity and select “High”
3. Under the Set Alert Notification tab, choose Slack and populate the channel
4. Set Frequency to “As it Happens”
5. Set up the Slack Integration to complete the configuration - 1. Configure Slack Integration
2. Create an alert rule
3. Under the “Select Policies” tab, filter on severity and select “High”
4. Under the Set Alert Notification tab, choose Slack and populate the channel
5. Set Frequency to “As it Happens” - 1. Under the “Select Policies” tab, filter on severity and select “High”
2. Under the Set Alert Notification tab, choose Slack and populate the channel
3. Set Frequency to “As it Happens”
4. Configure Slack Integration
5. Create an Alert rule
- 1. Configure Slack Integration
-
A business unit has acquired a company that has a very large AWS account footprint. The plan is to immediately start onboarding the new company’s AWS accounts into Prisma Cloud Enterprise tenant immediately. The current company is currently not using AWS Organizations and will require each account to be onboarded individually.
The business unit has decided to cover the scope of this action and determined that a script should be written to onboard each of these accounts with general settings to gain immediate posture visibility across the accounts.
Which API endpoint will specifically add these accounts into the Prisma Cloud Enterprise tenant?
- https://api.prismacloud.io/cloud/
- https://api.prismacloud.io/account/aws
- https://api.prismacloud.io/cloud/aws
- https://api.prismacloud.io/accountgroup/aws
-
A security team has a requirement to ensure the environment is scanned for vulnerabilities.
What are three options for configuring vulnerability policies? (Choose three.)
- individual actions based on package type
- output verbosity for blocked requests
- apply policy only when vendor fix is available
- individual grace periods for each severity level
- customize message on blocked requests
Explanation:Reference:https://docs.paloaltonetworks.com/prisma/prisma-cloud/19-11/prisma-cloud-compute-edition-admin/vulnerability_management/vuln_management_rules.html -
The Unusual protocol activity (Internal) network anomaly is generating too many alerts. An administrator has been asked to tune it to the option that will generate the least number of events without disabling it entirely.
Which strategy should the administrator use to achieve this goal?
- Disable the policy
- Set the Alert Disposition to Conservative
- Change the Training Threshold to Low
- Set Alert Disposition to Aggressive
Explanation:Reference:https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin/prisma-cloud-policies/anomaly-policies.html -
What is the behavior of Defenders when the Console is unreachable during upgrades?
- Defenders continue to alert, but not enforce, using the policies and settings most recently cached before upgrading the Console.
- Defenders will fail closed until the web-socket can be re-established.
- Defenders will fail open until the web-socket can be re-established.
- Defenders continue to alert and enforce using the policies and settings most recently cached before upgrading the Console.
Explanation:Reference:https://docs.paloaltonetworks.com/prisma/prisma-cloud/20-09/prisma-cloud-compute-edition-admin/upgrade/upgrade_process.html -
How are the following categorized?
– Backdoor account access
– Hijacked processes
– Lateral movement
– Port scanning
- audits
- incidents
- admission controllers
- models
-
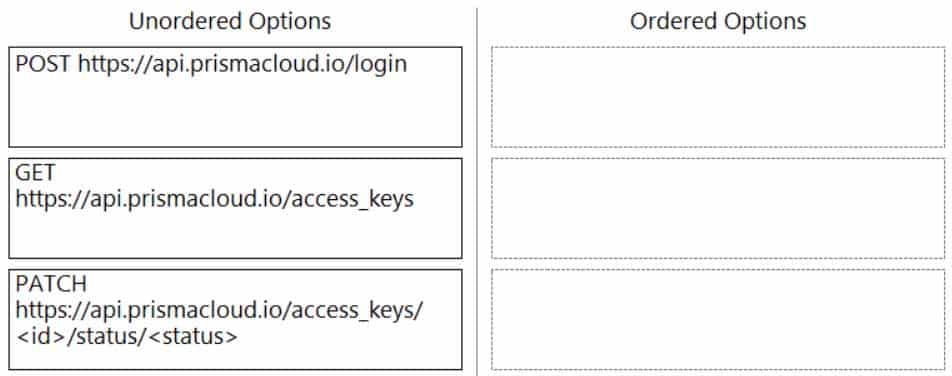
DRAG DROP
An administrator needs to write a script that automatically deactivates access keys that have not been used for 30 days.
In which order should the API calls be used to accomplish this task?
(Drag the steps into the correct order from the first step to the last.)
PCCSE Prisma Certified Cloud Security Engineer Part 02 Q20 002 Question 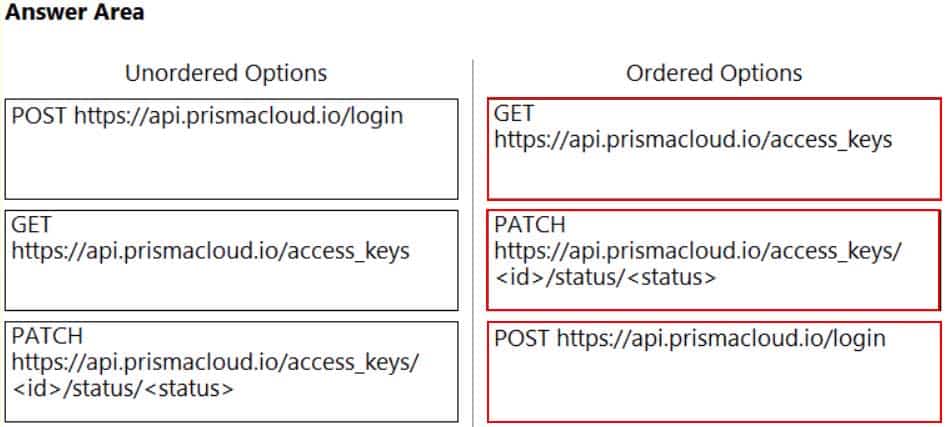
PCCSE Prisma Certified Cloud Security Engineer Part 02 Q20 002 Answer