PCCSE : Prisma Certified Cloud Security Engineer : Part 03
-
Which method should be used to authenticate to Prisma Cloud Enterprise programmatically?
- single sign-on
- SAML
- basic authentication
- access key
Explanation:
Reference:
https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin/get-started-with-prisma-cloud/access-the-prisma-cloud-api.html
-
Which option shows the steps to install the Console in a Kubernetes Cluster?
- Download the Console and Defender image
Generate YAML for Defender
Deploy Defender YAML using kubectl - Download and extract release tarball
Generate YAML for Console
Deploy Console YAML using kubectl - Download the Console and Defender image
Download YAML for Defender from the document site
Deploy Defender YAML using kubectl - Download and extract release tarball
Download the YAML for Console
Deploy Console YAML using kubectl
- Download the Console and Defender image
-
A customer has a requirement to automatically protect all Lambda functions with runtime protection.
What is the process to automatically protect all the Lambda functions?
- Configure a function scan policy from the Defend/Vulnerabilities/Functions page.
- Configure serverless radar from the Defend/Compliance/Cloud Platforms page.
- Configure a manually embedded Lambda Defender.
- Configure a serverless auto-protect rule for the functions.
Explanation:Reference:https://blog.paloaltonetworks.com/prisma-cloud/protect-serverless-functions/ -
Which statement accurately characterizes SSO Integration on Prisma Cloud?
- Prisma Cloud supports IdP initiated SSO, and its SAML endpoint supports the POST and GET methods.
- Okta, Azure Active Directory, PingID, and others are supported via SAML.
- An administrator can configure different Identity Providers (IdP) for all the cloud accounts that Prisma Cloud monitors.
- An administrator who needs to access the Prisma Cloud API can use SSO after configuration.
Explanation:Reference:https://docs-new.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin/manage-prisma-cloud-administrators/setup-sso-integration-on-prisma-cloud -
DRAG DROP
Match the service on the right that evaluates each exposure type on the left.
(Select your answer from the pull-down list. Answers may be used more than once or not at all.)
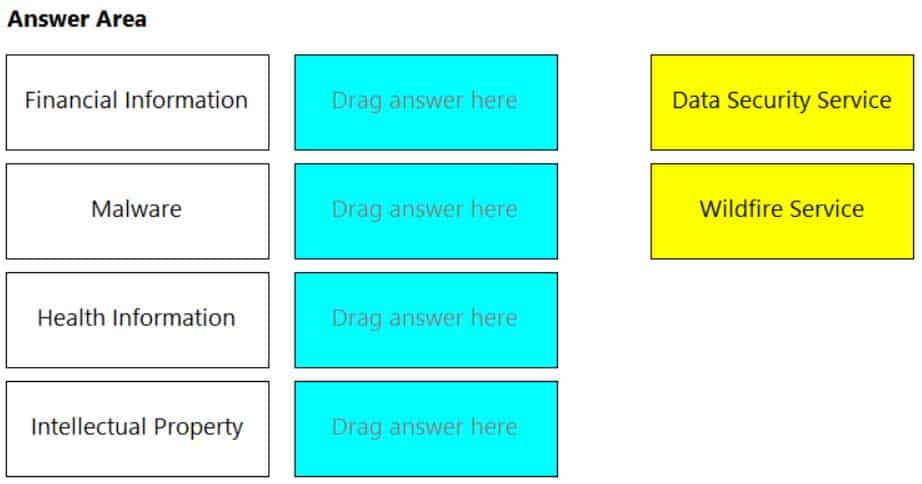
PCCSE Prisma Certified Cloud Security Engineer Part 03 Q05 003 Question 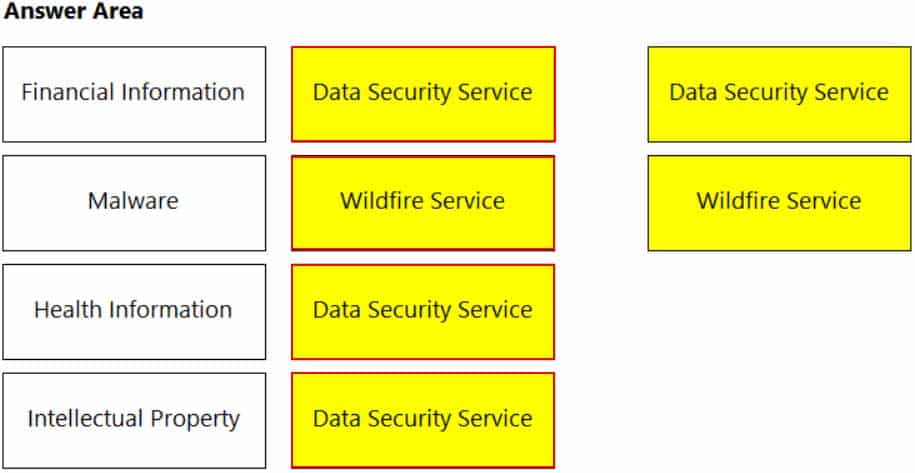
PCCSE Prisma Certified Cloud Security Engineer Part 03 Q05 003 Answer Explanation:Reference:
https://www.paloaltonetworks.com/prisma/cloud/cloud-data-security -
What are two ways to scan container images in Jenkins pipelines? (Choose two.)
- twistcli
- Jenkins Docker plugin
- Compute Jenkins plugin
- Compute Azure DevOps plugin
- Prisma Cloud Visual Studio Code plugin with Jenkins integration
-
A customer wants to harden its environment from misconfiguration.
Prisma Cloud Compute Compliance enforcement for hosts covers which three options? (Choose three.)
- Docker daemon configuration files
- Docker daemon configuration
- Host cloud provider tags
- Host configuration
- Hosts without Defender agents
-
A Prisma Cloud administrator is tasked with pulling a report via API. The Prisma Cloud tenant is located on app2.prismacloud.io.
What is the correct API endpoint?
- https://api.prismacloud.io
- https://api2.eu.prismacloud.io
- httsp://api.prismacloud.cn
- https://api2.prismacloud.io
-
A customer has Defenders connected to Prisma Cloud Enterprise. The Defenders are deployed as a DaemonSet in OpenShift.
How should the administrator get a report of vulnerabilities on hosts?
- Navigate to Monitor > Vulnerabilities > CVE Viewer
- Navigate to Defend > Vulnerabilities > VM Images
- Navigate to Defend > Vulnerabilities > Hosts
- Navigate to Monitor > Vulnerabilities > Hosts
-
DRAG DROP
Order the steps involved in onboarding an AWS Account for use with Data Security feature.
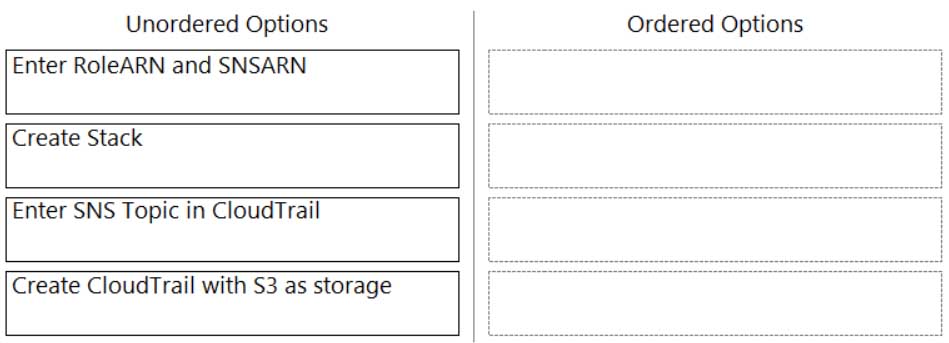
PCCSE Prisma Certified Cloud Security Engineer Part 03 Q10 004 Question 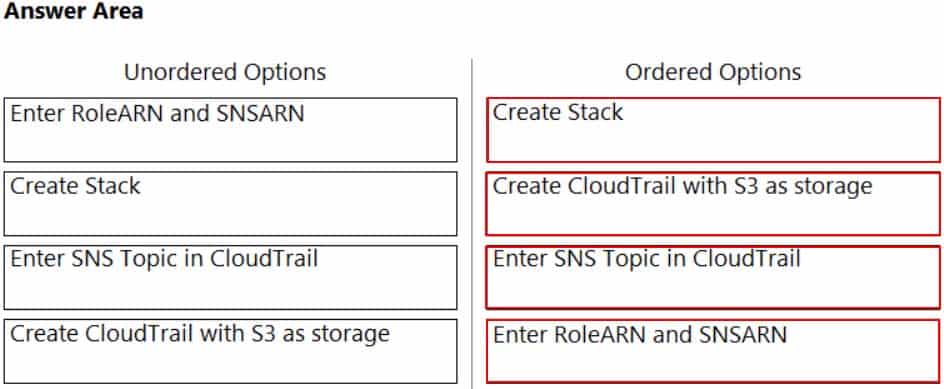
PCCSE Prisma Certified Cloud Security Engineer Part 03 Q10 004 Answer -
A customer has a requirement to scan serverless functions for vulnerabilities.
Which three settings are required to configure serverless scanning? (Choose three.)
- Defender Name
- Region
- Credential
- Console Address
- Provider
Explanation:Reference:https://docs.paloaltonetworks.com/prisma/prisma-cloud/21-04/prisma-cloud-compute-edition-admin/vulnerability_management/serverless_functions.html -
You are tasked with configuring a Prisma Cloud build policy for Terraform.
What type of query is necessary to complete this policy?
- YAML
- JSON
- CloudFormation
- Terraform
Explanation:Reference:https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin/prisma-cloud-policies/create-a-policy/prisma-cloud-create-config-build-policy.html -
You have onboarded a public cloud account into Prisma Cloud Enterprise. Configuration Resource ingestion is visible in the Asset Inventory for the onboarded account, but no alerts are being generated for the configuration assets in the account.
Config policies are enabled in the Prisma Cloud Enterprise tenant, with those policies associated to existing alert rules. ROL statements on the investigate matching those policies return config resource results successfully.
Why are no alerts being generated?
- The public cloud account is not associated with an alert notification.
- The public cloud account does not have audit trail ingestion enabled.
- The public cloud account does not access to configuration resources.
- The public cloud account is not associated with an alert rule.
-
The security team wants to target a CNAF policy for specific running Containers.
How should the administrator scope the policy to target the Containers?
- scope the policy to Image names.
- scope the policy to namespaces.
- scope the policy to Defender names.
- scope the policy to Host names.
-
The InfoSec team wants to be notified via email each time a Security Group is misconfigured.
Which Prisma Cloud tab should you choose to complete this request?
- Notifications
- Policies
- Alert Rules
- Events
Explanation:Reference:https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin/manage-prisma-cloud-alerts/configure-prisma-cloud-to-automatically-remediate-alerts.html -
An administrator has access to a Prisma Cloud Enterprise.
What are the steps to deploy a single container Defender on an ec2 node?
- Pull the Defender image to the ec2 node, copy and execute the curl | bash script, and start the Defender to ensure it is running.
- Execute the curl | bash script on the ec2 node.
- Configure the cloud credential in the console and allow cloud discovery to auto-protect the ec2 node.
- Generate DaemonSet file and apply DaemonSet to the twistlock namespace.
Explanation:Reference:https://docs.twistlock.com/docs/compute_edition/install/install_kubernetes.html -
A customer wants to turn on Auto Remediation.
Which policy type has the built-in CLI command for remediation?
- Anomaly
- Audit Event
- Network
- Config
Explanation:Reference:https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin/prisma-cloud-policies/create-a-policy.html -
A customer is deploying Defenders to a Fargate environment. It wants to understand the vulnerabilities in the image it is deploying.
How should the customer automate vulnerability scanning for images deployed to Fargate?
- Set up a vulnerability scanner on the registry
- Embed a Fargate Defender to automatically scan for vulnerabilities
- Designate a Fargate Defender to serve a dedicated image scanner
- Use Cloud Compliance to identify misconfigured AWS accounts
Explanation:Reference:https://blog.paloaltonetworks.com/prisma-cloud/securing-aws-fargate-tasks/ -
Which container image scan is constructed correctly?
-
twistcli images scan --docker-address https://us-west1.cloud.twistlock.com/us-3-123456789 myimage/latest
-
twistcli images scan --address https://us-west1.cloud.twistlock.com/us-3-123456789 myimage/latest
-
twistcli images scan --address https://us-west1.cloud.twistlock.com/us-3-123456789 --container myimage/latest -
twistcli images scan --address https://us-west1.cloud.twistlock.com/us-3-123456789 --container myimage/latest --details
Explanation:Reference:https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin-compute/tools/twistcli_scan_images -
-
DRAG DROP
An administrator has been tasked with creating a custom service that will download any existing compliance report from a Prisma Cloud Enterprise tenant.
In which order will the APIs be executed for this service?
(Drag the steps into the correct order of occurrence, from the first step to the last.)
PCCSE Prisma Certified Cloud Security Engineer Part 03 Q20 005 Question 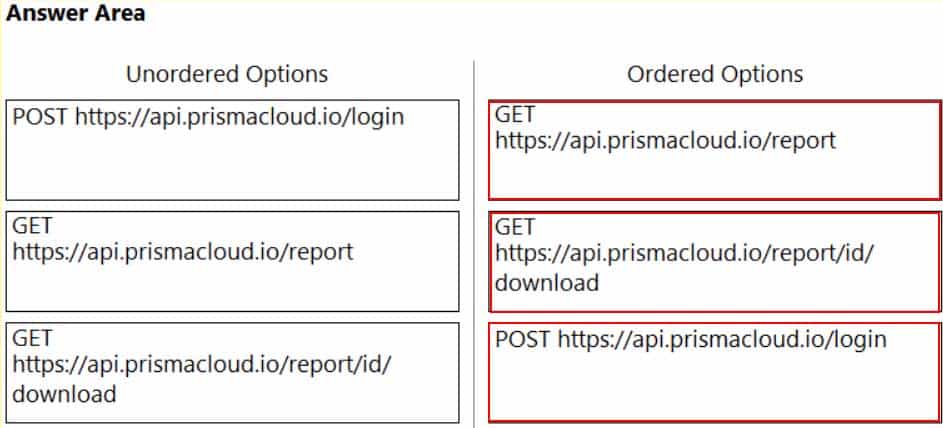
PCCSE Prisma Certified Cloud Security Engineer Part 03 Q20 005 Answer