PCCSE : Prisma Certified Cloud Security Engineer : Part 04
-
Which two processes ensure that builds can function after a Console upgrade? (Choose two.)
- allowing Jenkins to automatically update the plugin
- updating any build environments that have twistcli included to use the latest version
- configuring build pipelines to download twistcli at the start of each build
- creating a new policy that allows older versions of twistcli to connect the Console
-
The compliance team needs to associate Prisma Cloud policies with compliance frameworks.
Which option should the team select to perform this task?
- Custom Compliance
- Policies
- Compliance
- Alert Rules
Explanation:
Reference: https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin/prisma-cloud-compliance/compliance-dashboard.html
-
Review this admission control policy:
match[{"msg": msg}] { input.request.operation == "CREATE" input.request.kind.kind == "Pod" input.request.resource.resource == "pods" input.request.object.spec.containers[_].securityContext.privileged msg := "Privileged" }Which response to this policy will be achieved when the effect is set to “block”?
- The policy will block all pods on a Privileged host.
- The policy will replace Defender with a privileged Defender.
- The policy will alert only the administrator when a privileged pod is created.
- The policy will block the creation of a privileged pod.
-
Per security requirements, an administrator needs to provide a list of people who are receiving e-mails for Prisma Cloud alerts.
Where can the administrator locate this list of e-mail recipients?
- Target section within an Alert Rule.
- Notification Template section within Alerts.
- Users section within Settings.
- Set Alert Notification section within an Alert Rule.
-
A customer wants to scan a serverless function as part of a build process.
Which twistcli command can be used to scan serverless functions?
-
twistcli function scan <SERVERLESS_FUNCTION.ZIP>
-
twistcli scan serverless <SERVERLESS_FUNCTION.ZIP>
-
twistcli serverless AWS <SERVERLESS_FUNCTION.ZIP>
-
twiscli serverless scan <SERVERLESS_FUNCTION.ZIP>
Explanation:Reference: https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin-compute/vulnerability_management/serverless_functions -
-
A customer has a development environment with 50 connected Defenders. A maintenance window is set for Monday to upgrade 30 stand-alone Defenders in the development environment, but there is no maintenance window available until Sunday to upgrade the remaining 20 stand-alone Defenders.
Which recommended action manages this situation?
- Go to Manage > Defender > Manage, then click Defenders, and use the Scheduler to choose which Defenders will be automatically upgraded during the maintenance window.
- Find a maintenance window that is suitable to upgrade all stand-alone Defenders in the development environment.
- Upgrade a subset of the Defenders by clicking the individual Actions > Upgrade button in the row that corresponds to the Defender that should be upgraded during the maintenance window.
- Open a support case with Palo Alto Networks to arrange an automatic upgrade.
-
What is an example of an outbound notification within Prisma Cloud?
- AWS Inspector
- Qualys
- Tenable
- PagerDuty
-
A security team has been asked to create a custom policy.
Which two methods can the team use to accomplish this goal? (Choose two.)
- add a new policy
- clone an existing policy
- disable an out-of-the-box policy
- edit the query in the out-of-the-box policy
Explanation:Reference: https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin/prisma-cloud-policies/manage-prisma-cloud-policies -
The security auditors need to ensure that given compliance checks are being run on the host.
Which option is a valid host compliance policy?
- Ensure functions are not overly permissive.
- Ensure host devices are not directly exposed to containers.
- Ensure images are created with a non-root user.
- Ensure compliant Docker daemon configuration.
-
DRAG DROP
Match the correct scanning mode for each given operation.
(Select your answer from the pull-down list. Answers may be used more than once or not at all.)
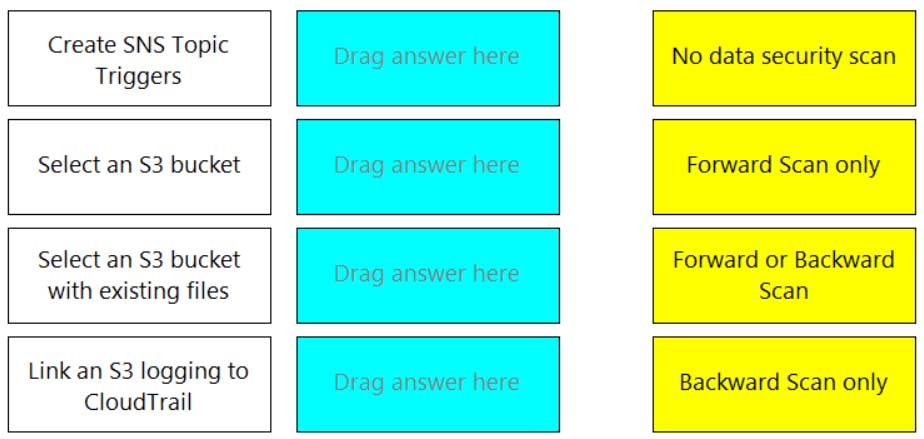
PCCSE Prisma Certified Cloud Security Engineer Part 04 Q10 006 Question 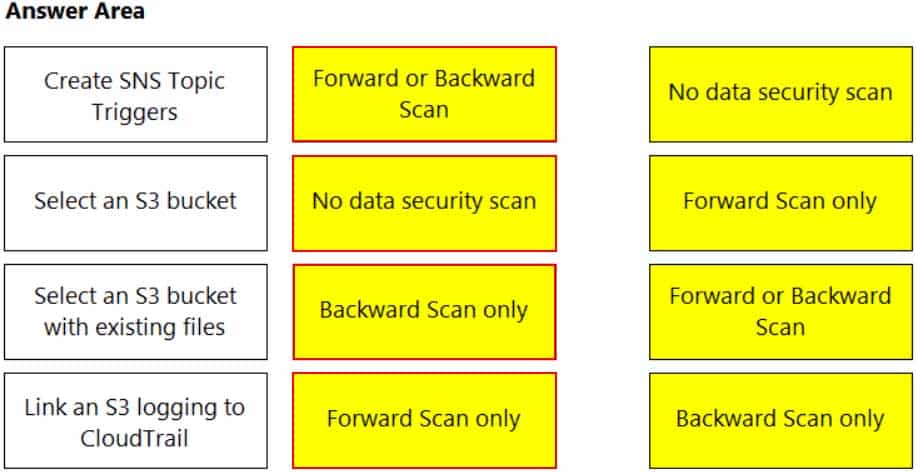
PCCSE Prisma Certified Cloud Security Engineer Part 04 Q10 006 Answer -
A customer wants to be notified about port scanning network activities in their environment.
Which policy type detects this behavior?
- Network
- Port Scan
- Anomaly
- Config
-
A security team is deploying Cloud Native Application Firewall (CNAF) on a containerized web application. The application is running an NGINX container. The container is listening on port 8080 and is mapped to host port 80.
Which port should the team specify in the CNAF rule to protect the application?
- 443
- 80
- 8080
- 8888
Explanation:Reference:https://docs.paloaltonetworks.com/prisma/prisma-cloud/19-11/prisma-cloud-compute-edition-admin/firewalls/deploy_cnaf.html -
Which three types of buckets exposure are available in the Data Security module? (Choose three.)
- Public
- Private
- International
- Differential
- Conditional
-
The administrator wants to review the Console audit logs from within the Console.
Which page in the Console should the administrator use to review this data, if it can be reviewed at all?
- Navigate to Monitor > Events > Host Log Inspection
- The audit logs can be viewed only externally to the Console
- Navigate to Manage > Defenders > View Logs
- Navigate to Manage > View Logs > History
Explanation:Reference: https://docs.twistlock.com/docs/compute_edition/howto/review_debug_logs.html -
DRAG DROP
What is the order of steps in a Jenkins pipeline scan?
(Drag the steps into the correct order of occurrence, from the first step to the last.)
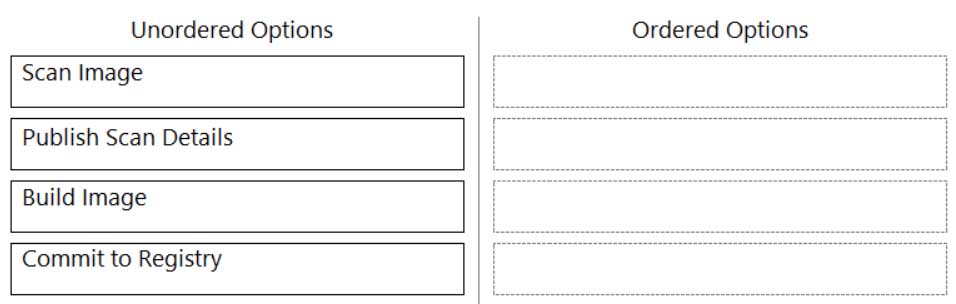
PCCSE Prisma Certified Cloud Security Engineer Part 04 Q15 007 Question 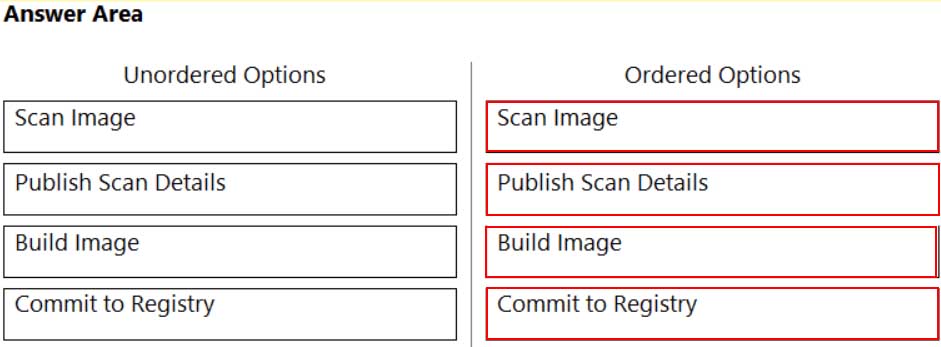
PCCSE Prisma Certified Cloud Security Engineer Part 04 Q15 007 Answer -
DRAG DROP
What is the order of steps to create a custom network policy?
(Drag the steps into the correct order of occurrence, from the first step to the last.)
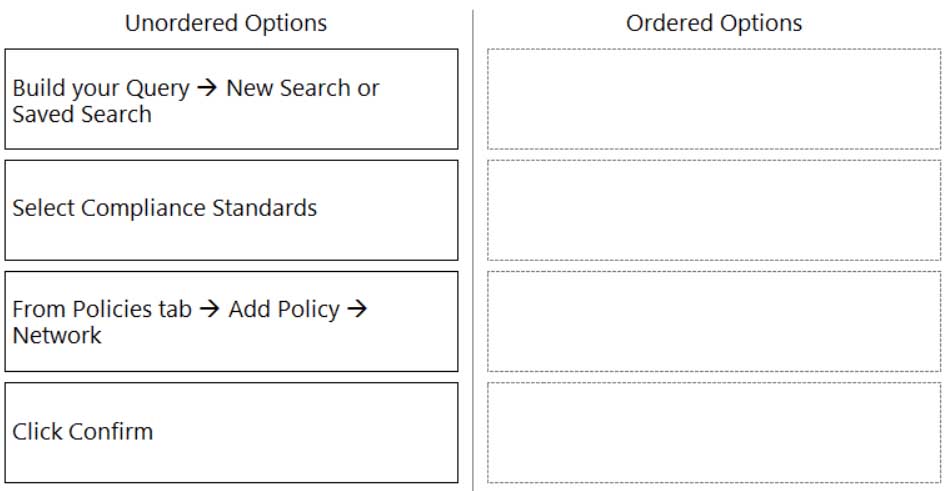
PCCSE Prisma Certified Cloud Security Engineer Part 04 Q16 008 Question 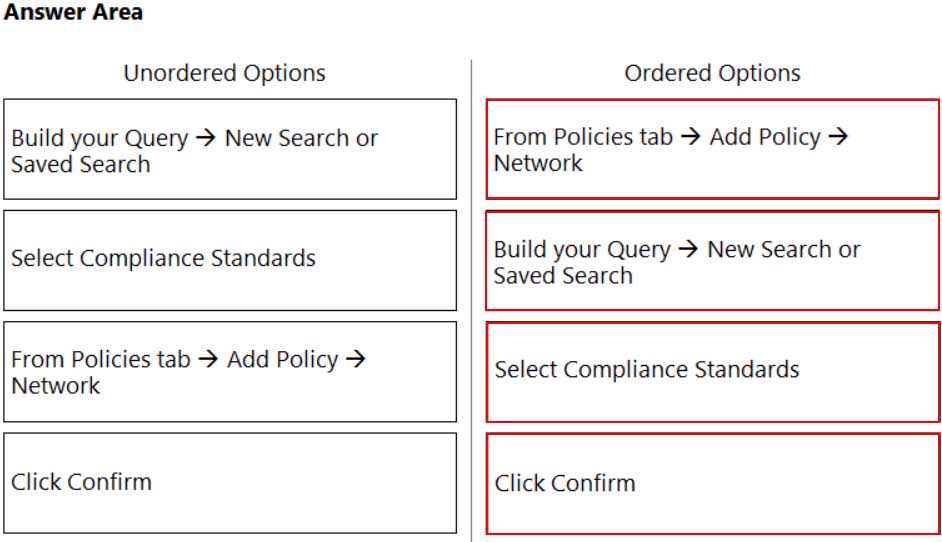
PCCSE Prisma Certified Cloud Security Engineer Part 04 Q16 008 Answer Explanation:Reference:
https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin/prisma-cloud-policies/create-a-policy.html -
DRAG DROP
You wish to create a custom policy with build and run subtypes.
Match the query types for each example.
(Select your answer from the pull-down list. Answers may be used more than once or not at all.)
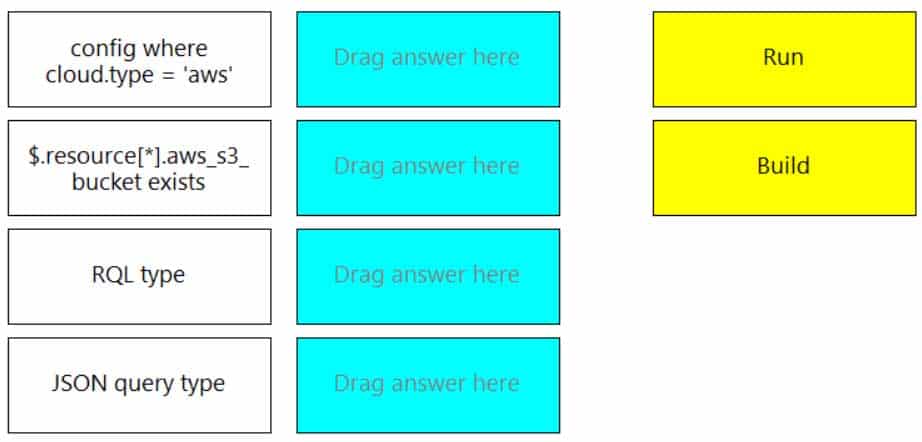
PCCSE Prisma Certified Cloud Security Engineer Part 04 Q17 009 Question 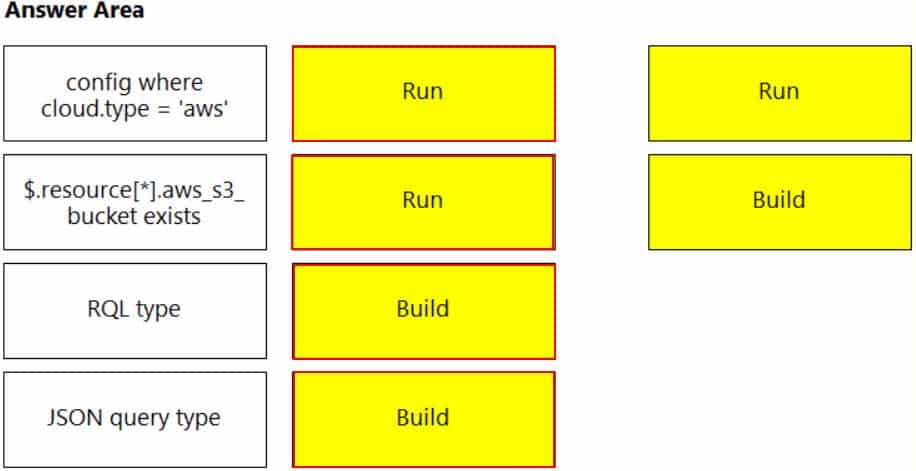
PCCSE Prisma Certified Cloud Security Engineer Part 04 Q17 009 Answer Explanation:Reference:
https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin/prisma-cloud-policies/create-a-policy.html -
Which statement is true regarding CloudFormation templates?
- Scan support does not currently exist for nested references, macros, or intrinsic functions.
- A single template or a zip archive of template files cannot be scanned with a single API request.
- Request-Header-Field ‘cloudformation-version’ is required to request a scan.
- Scan support is provided for JSON, HTML and YAML formats.
Explanation:Reference:https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin/prisma-cloud-devops-security/use-the-prisma-cloud-iac-scan-rest-api.html -
A customer has a large environment that needs to upgrade Console without upgrading all Defenders at one time.
What are two prerequisites prior to performing a rolling upgrade of Defenders? (Choose two.)
- manual installation of the latest twistcli tool prior to the rolling upgrade
- all Defenders set in read-only mode before execution of the rolling upgrade
- a second location where you can install the Console
- additional workload licenses are required to perform the rolling upgrade
- an existing Console at version n-1
-
An administrator sees that a runtime audit has been generated for a Container. The audit message is “DNS resolution of suspicious name wikipedia.com. type A”.
Why would this message appear as an audit?
- The DNS was not learned as part of the Container model or added to the DNS allow list.
- This is a DNS known to be a source of malware.
- The process calling out to this domain was not part of the Container model.
- The Layer7 firewall detected this as anomalous behavior.
-
Which “kind” of Kubernetes object is configured to ensure that Defender is acting as the admission controller?
- MutatingWebhookConfiguration
- DestinationRules
- ValidatingWebhookConfiguration
- PodSecurityPolicies
Explanation:Reference:https://docs.paloaltonetworks.com/prisma/prisma-cloud/21-04/prisma-cloud-compute-edition-admin/access_control/open_policy_agent.html -
Which three options are selectable in a CI policy for image scanning with Jenkins or twistcli? (Choose three.)
- Scope – Scans run on a particular host
- Credential
- Apply rule only when vendor fixes are available
- Failure threshold
- Grace Period
-
Which component(s), if any, will Palo Alto Networks host and run when a customer purchases Prisma Cloud Enterprise Edition?
- Defenders
- Console
- Jenkins
- twistcli
-
Which port should a security team use to pull data from Console’s API?
- 53
- 25
- 8084
- 8083
-
You are an existing customer of Prisma Cloud Enterprise. You want to onboard a public cloud account and immediately see all of the alerts associated with this account based off ALL of your tenant’s existing enabled policies. There is no requirement to send alerts from this account to a downstream application at this time.
Which option shows the steps required during the alert rule creation process to achieve this objective?
- Ensure the public cloud account is assigned to an account group
Assign the confirmed account group to alert rule
Select “select all policies” checkbox as part of the alert rule
Confirm the alert rule - Ensure the public cloud account is assigned to an account group
Assign the confirmed account group to alert rule
Select one or more policies checkbox as part of the alert rule
Confirm the alert rule - Ensure the public cloud account is assigned to an account group
Assign the confirmed account group to alert rule
Select one or more policies as part of the alert rule
Add alert notifications
Confirm the alert rule - Ensure the public cloud account is assigned to an account group
Assign the confirmed account group to alert rule
Select “select all policies” checkbox as part of the alert rule
Add alert notifications
Confirm the alert rule
- Ensure the public cloud account is assigned to an account group