PCNSA : Palo Alto Networks Certified Network Security Administrator : Part 01
-
DRAG DROP
Match the Palo Alto Networks Security Operating Platform architecture to its description.
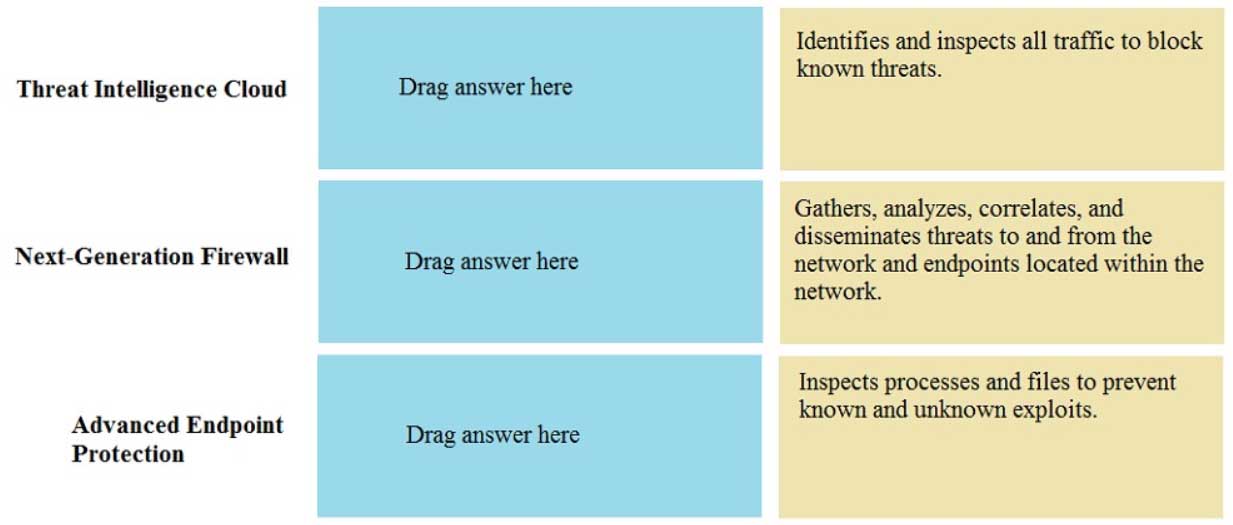
PCNSA Palo Alto Networks Certified Network Security Administrator Part 01 Q01 001 Question 
PCNSA Palo Alto Networks Certified Network Security Administrator Part 01 Q01 001 Answer -
Which plane on a Palo Alto Networks Firewall provides configuration, logging, and reporting functions on a separate processor?
- management
- network processing
- data
- security processing
-
A security administrator has configured App-ID updates to be automatically downloaded and installed. The company is currently using an application identified by App-ID as SuperApp_base.
On a content update notice, Palo Alto Networks is adding new app signatures labeled SuperApp_chat and SuperApp_download, which will be deployed in 30 days.
Based on the information, how is the SuperApp traffic affected after the 30 days have passed?
- All traffic matching the SuperApp_chat, and SuperApp_download is denied because it no longer matches the SuperApp-base application
- No impact because the apps were automatically downloaded and installed
- No impact because the firewall automatically adds the rules to the App-ID interface
- All traffic matching the SuperApp_base, SuperApp_chat, and SuperApp_download is denied until the security administrator approves the applications
-
How many zones can an interface be assigned with a Palo Alto Networks firewall?
- two
- three
- four
- one
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-web-interface-help/network/network-zones/security-zone-overview -
Which two configuration settings shown are not the default? (Choose two.)
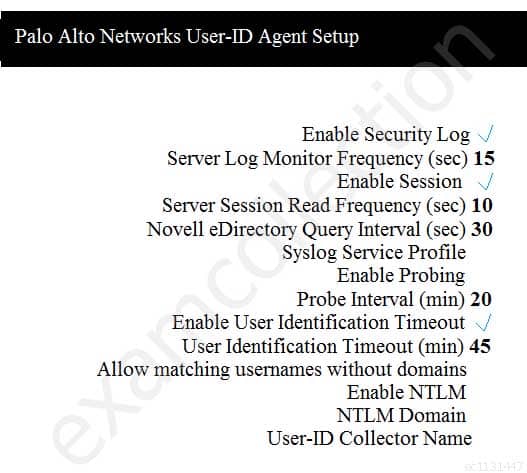
PCNSA Palo Alto Networks Certified Network Security Administrator Part 01 Q05 002 - Enable Security Log
- Server Log Monitor Frequency (sec)
- Enable Session
- Enable Probing
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/8-0/pan-os-web-interface-help/user-identification/device-user-identification-user-mapping/enable-server-monitoring -
Which dataplane layer of the graphic shown provides pattern protection for spyware and vulnerability exploits on a Palo Alto Networks Firewall?
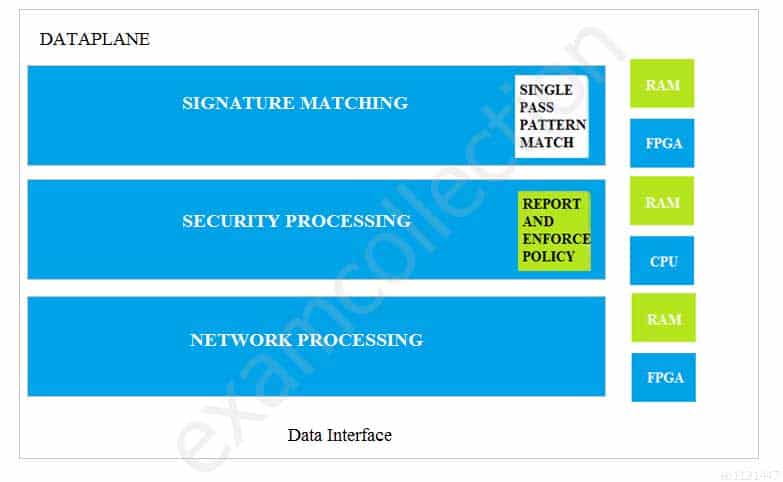
PCNSA Palo Alto Networks Certified Network Security Administrator Part 01 Q06 003 - Signature Matching
- Network Processing
- Security Processing
- Data Interfaces
-
Which option shows the attributes that are selectable when setting up application filters?
- Category, Subcategory, Technology, and Characteristic
- Category, Subcategory, Technology, Risk, and Characteristic
- Name, Category, Technology, Risk, and Characteristic
- Category, Subcategory, Risk, Standard Ports, and Technology
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/7-1/pan-os-web-interface-help/objects/objects-application-filters -
Actions can be set for which two items in a URL filtering security profile? (Choose two.)
- Block List
- Custom URL Categories
- PAN-DB URL Categories
- Allow List
Explanation & Hints: - Block List: A block list, also known as a blacklist, is a set of URLs or domains that are explicitly prohibited or blocked by the URL filtering security profile. When a user attempts to access a website on the block list, the security profile blocks access, preventing the user from reaching the site. This is commonly used to block known malicious or inappropriate websites, preventing users from inadvertently accessing harmful content.
- Allow List: An allow list, also known as a whitelist, is a set of URLs or domains that are explicitly permitted or allowed by the URL filtering security profile. When a user attempts to access a website, the security profile checks if the website is on the allow list. If it is, the access is permitted; if not, access is denied. Allow lists are often used to ensure that users can only access approved websites, reducing the risk of exposure to malicious or inappropriate content and enhancing security.
These two mechanisms provide administrators with granular control over web access within their network, allowing them to tailor browsing policies to align with their organization’s security requirements and objectives.
-
DRAG DROP
Match the Cyber-Attack Lifecycle stage to its correct description.
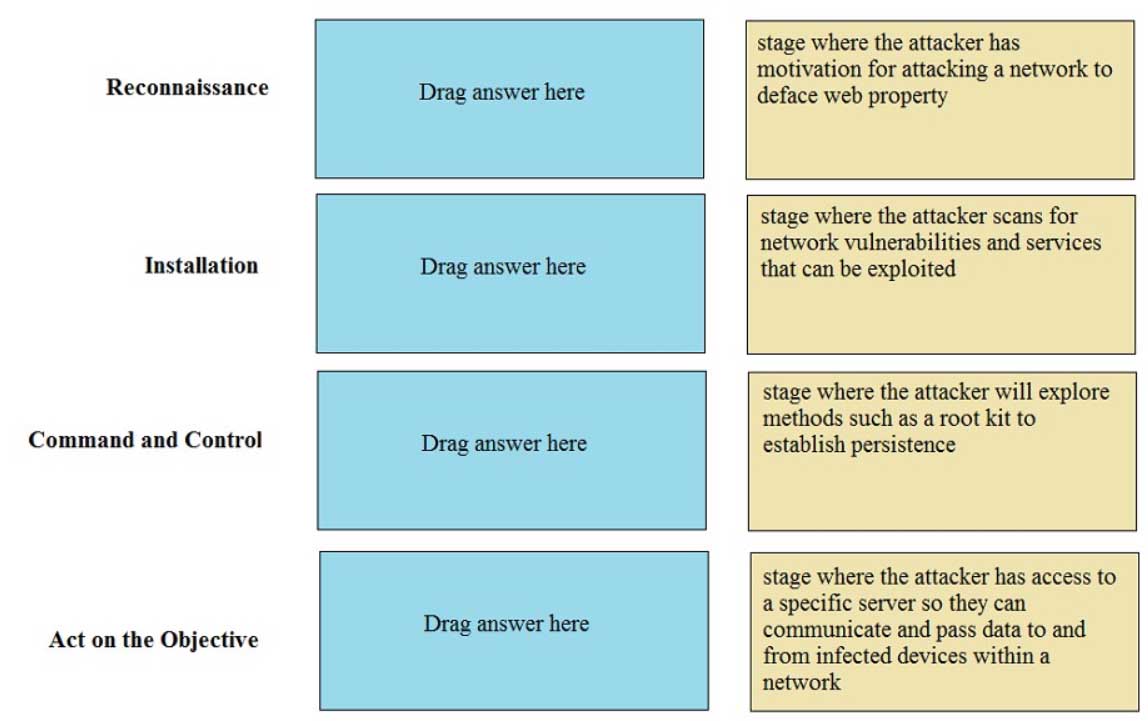
PCNSA Palo Alto Networks Certified Network Security Administrator Part 01 Q09 004 Question 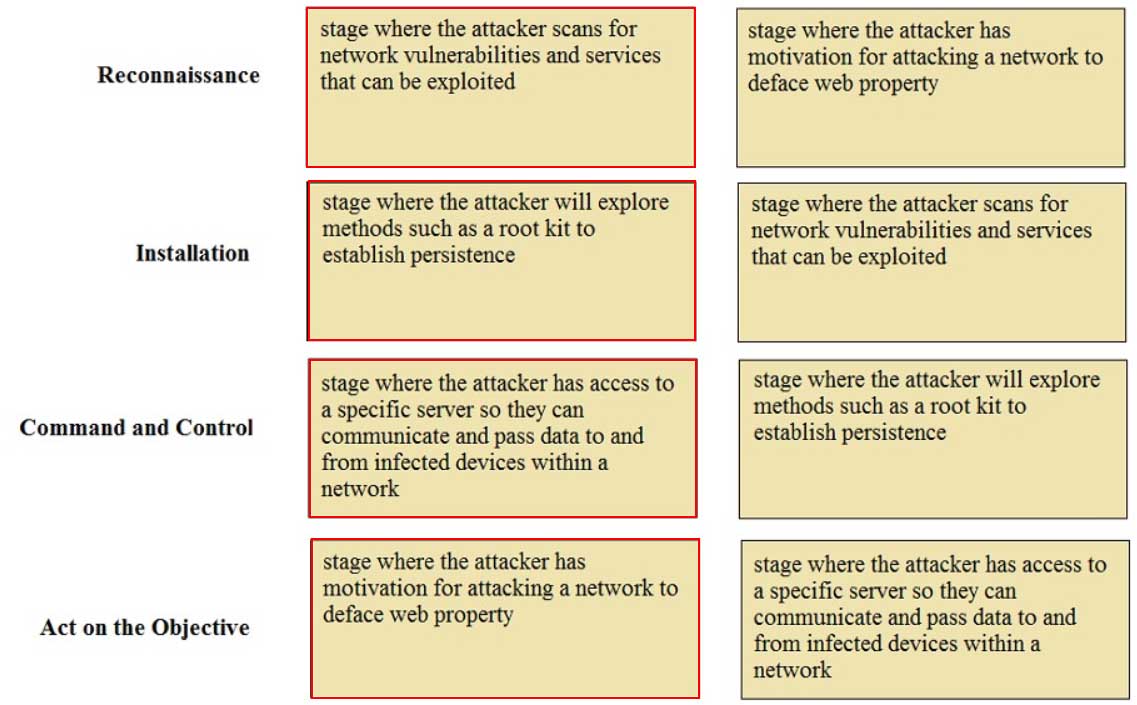
PCNSA Palo Alto Networks Certified Network Security Administrator Part 01 Q09 004 Answer -
Which two statements are correct about App-ID content updates? (Choose two.)
- Updated application content might change how Security policy rules are enforced.
- After an application content update, new applications must be manually classified prior to use.
- Existing security policy rules are not affected by application content updates.
- After an application content update, new applications are automatically identified and classified.
-
Which User-ID mapping method should be used for an environment with users that do not authenticate to Active Directory?
- Windows session monitoring
- passive server monitoring using the Windows-based agent
- Captive Portal
- passive server monitoring using a PAN-OS integrated User-ID agent
-
An administrator needs to allow users to use their own office applications. How should the administrator configure the firewall to allow multiple applications in a dynamic environment?
- Create an Application Filter and name it Office Programs, then filter it on the business-systems category, office-programs subcategory
- Create an Application Group and add business-systems to it
- Create an Application Filter and name it Office Programs, then filter it on the business-systems category
- Create an Application Group and add Office 365, Evernote, Google Docs, and Libre Office
-
Which statement is true regarding a Best Practice Assessment?
- The BPA tool can be run only on firewalls
- It provides a percentage of adoption for each assessment area
- The assessment, guided by an experienced sales engineer, helps determine the areas of greatest risk where you should focus prevention activities
- It provides a set of questionnaires that help uncover security risk prevention gaps across all areas of network and security architecture
Explanation:Reference:https://docs.paloaltonetworks.com/best-practices/8-1/data-center-best-practices/data-center-best-practice-security-policy/use-palo-alto-networks-assessment-and-review-tools -
Employees are shown an application block page when they try to access YouTube. Which security policy is blocking the YouTube application?
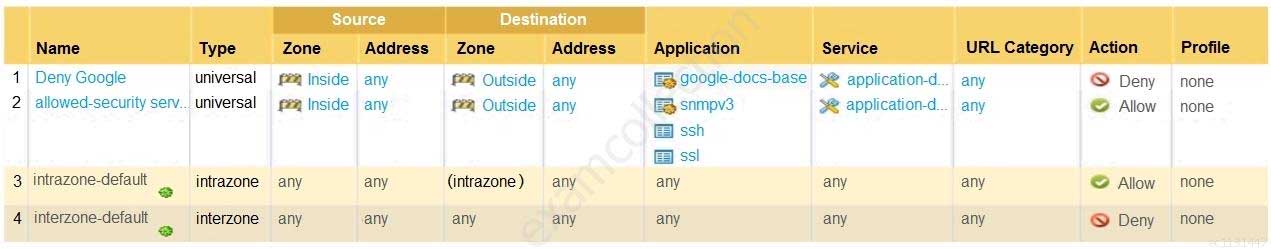
PCNSA Palo Alto Networks Certified Network Security Administrator Part 01 Q14 005 - intrazone-default
- Deny Google
- allowed-security services
- interzone-default
-
Choose the option that correctly completes this statement. A Security Profile can block or allow traffic ____________.
- on either the data place or the management plane.
- after it is matched by a security policy rule that allows traffic.
- before it is matched to a Security policy rule.
- after it is matched by a security policy rule that allows or blocks traffic.
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/policy/security-policy.html -
When creating a Source NAT policy, which entry in the Translated Packet tab will display the options Dynamic IP and Port, Dynamic, Static IP, and None?
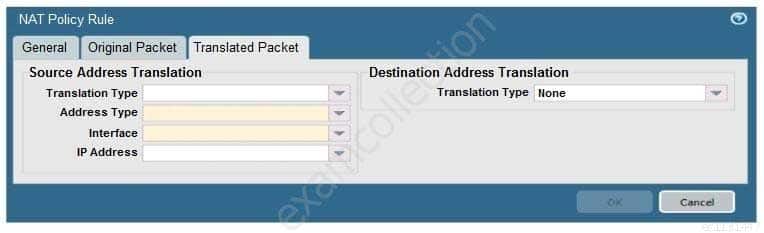
PCNSA Palo Alto Networks Certified Network Security Administrator Part 01 Q16 006 - Translation Type
- Interface
- Address Type
- IP Address
-
Which interface does not require a MAC or IP address?
- Virtual Wire
- Layer3
- Layer2
- Loopback
-
A company moved its old port-based firewall to a new Palo Alto Networks NGFW 60 days ago. Which utility should the company use to identify out-of-date or unused rules on the firewall?
- Rule Usage Filter > No App Specified
- Rule Usage Filter >Hit Count > Unused in 30 days
- Rule Usage Filter > Unused Apps
- Rule Usage Filter > Hit Count > Unused in 90 days
-
DRAG DROP
Order the steps needed to create a new security zone with a Palo Alto Networks firewall.
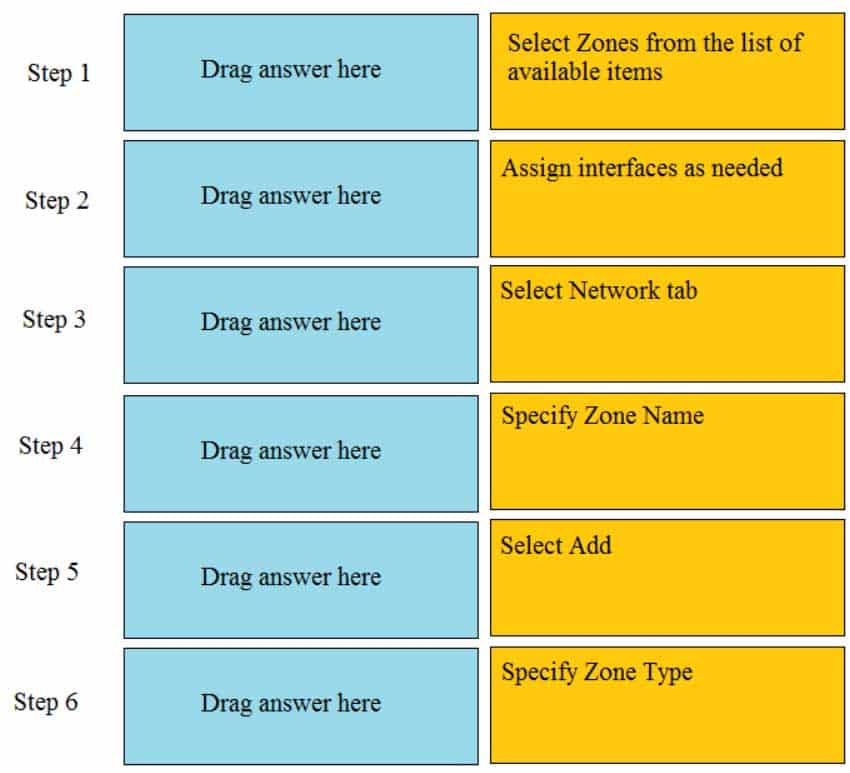
PCNSA Palo Alto Networks Certified Network Security Administrator Part 01 Q19 007 Question 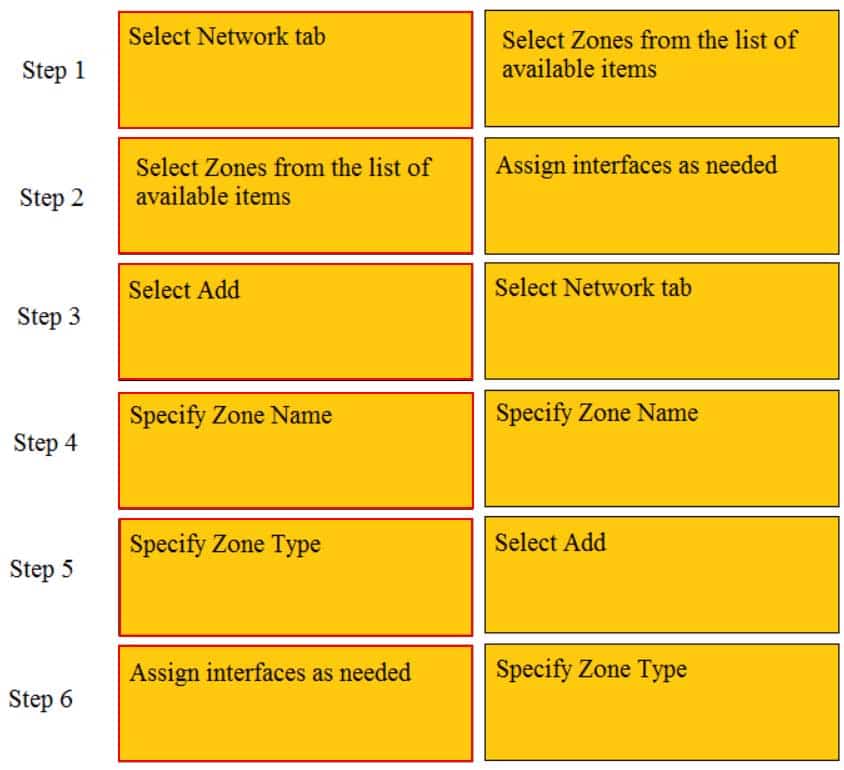
PCNSA Palo Alto Networks Certified Network Security Administrator Part 01 Q19 007 Answer -
What are two differences between an implicit dependency and an explicit dependency in App-ID? (Choose two.)
- An implicit dependency does not require the dependent application to be added in the security policy
- An implicit dependency requires the dependent application to be added in the security policy
- An explicit dependency does not require the dependent application to be added in the security policy
- An explicit dependency requires the dependent application to be added in the security policy
Subscribe
0 Comments
Newest