PCNSA : Palo Alto Networks Certified Network Security Administrator : Part 02
-
Recently changes were made to the firewall to optimize the policies and the security team wants to see if those changes are helping.
What is the quickest way to reset the hit counter to zero in all the security policy rules?
- At the CLI enter the command reset rules and press Enter
- Highlight a rule and use the Reset Rule Hit Counter > Selected Rules for each rule
- Reboot the firewall
- Use the Reset Rule Hit Counter > All Rules option
Explanation:
Reference:
https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-web-interface-help/policies/policies-security/creating-and-managing-policies
-
Which two App-ID applications will you need to allow in your Security policy to use facebook-chat? (Choose two.)
- facebook-chat
- facebook-base
- facebook-email
Explanation:Reference:https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClV0CAK -
Which User-ID agent would be appropriate in a network with multiple WAN links, limited network bandwidth, and limited firewall management plane resources?
- Windows-based agent deployed on the internal network
- PAN-OS integrated agent deployed on the internal network
- Citrix terminal server deployed on the internal network
- Windows-based agent deployed on each of the WAN Links
-
Your company requires positive username attribution of every IP address used by wireless devices to support a new compliance requirement. You must collect IP –to-user mappings as soon as possible with minimal downtime and minimal configuration changes to the wireless devices themselves. The wireless devices are from various manufactures.
Given the scenario, choose the option for sending IP-to-user mappings to the NGFW.
- syslog
- RADIUS
- UID redistribution
- XFF headers
-
An administrator receives a global notification for a new malware that infects hosts. The infection will result in the infected host attempting to contact a command-and-control (C2) server.
Which two security profile components will detect and prevent this threat after the firewall’s signature database has been updated? (Choose two.)
- vulnerability protection profile applied to outbound security policies
- anti-spyware profile applied to outbound security policies
- antivirus profile applied to outbound security policies
- URL filtering profile applied to outbound security policies
Explanation:Reference:
https://docs.paloaltonetworks.com/pan-os/7-1/pan-os-admin/policy/create-best-practice-security-profiles -
At which stage of the Cyber-Attack Lifecycle would the attacker attach an infected PDF file to an email?
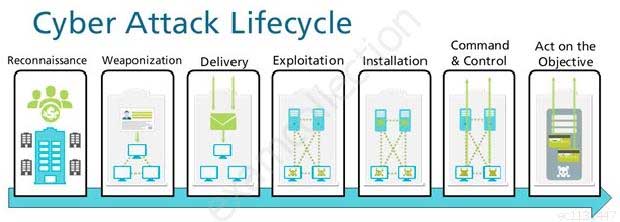
PCNSA Palo Alto Networks Certified Network Security Administrator Part 02 Q06 008 - Delivery
- Reconnaissance
- Command and Control
- Exploitation
-
Identify the correct order to configure the PAN-OS integrated USER-ID agent.
3. add the service account to monitor the server(s)
2. define the address of the servers to be monitored on the firewall
4. commit the configuration, and verify agent connection status
1. create a service account on the Domain Controller with sufficient permissions to execute the User- ID agent- 2-3-4-1
- 1-4-3-2
- 3-1-2-4
- 1-3-2-4
-
Users from the internal zone need to be allowed to Telnet into a server in the DMZ zone.
Complete the security policy to ensure only Telnet is allowed.
Security Policy: Source Zone: Internal to DMZ Zone __________services “Application defaults”, and action = Allow
- Destination IP: 192.168.1.123/24
- Application = “Telnet”
- Log Forwarding
- USER-ID = “Allow users in Trusted”
-
Based on the security policy rules shown, ssh will be allowed on which port?
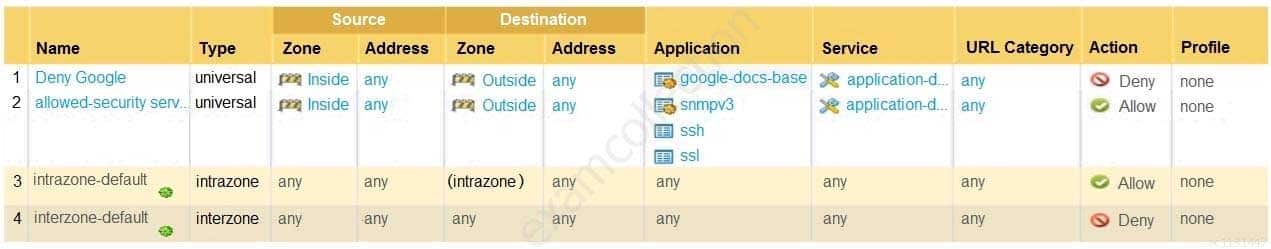
PCNSA Palo Alto Networks Certified Network Security Administrator Part 02 Q09 009 - 80
- 53
- 22
- 23
-
Which license must an Administrator acquire prior to downloading Antivirus Updates for use with the firewall?
- Threat Prevention
- WildFire
- Antivirus
- URL Filtering
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/getting-started/install-content-and-software-updates.html -
An administrator notices that protection is needed for traffic within the network due to malicious lateral movement activity. Based on the image shown, which traffic would the administrator need to monitor and block to mitigate the malicious activity?
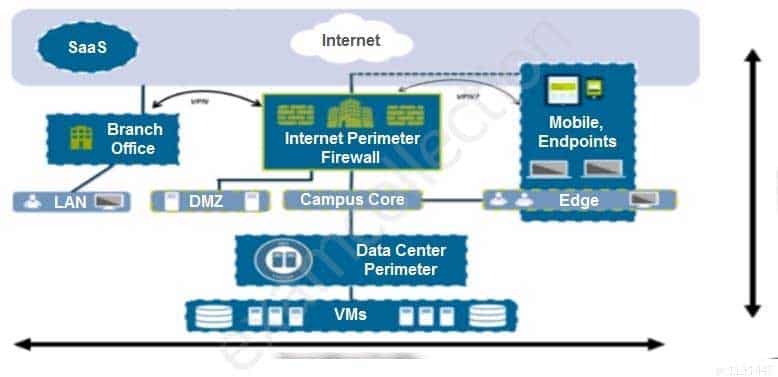
PCNSA Palo Alto Networks Certified Network Security Administrator Part 02 Q11 010 - branch office traffic
- north-south traffic
- perimeter traffic
- east-west traffic
-
Given the topology, which zone type should zone A and zone B to be configured with?
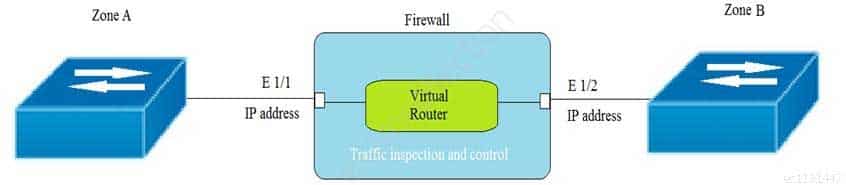
PCNSA Palo Alto Networks Certified Network Security Administrator Part 02 Q12 011 - Layer3
- Tap
- Layer2
- Virtual Wire
-
To use Active Directory to authenticate administrators, which server profile is required in the authentication profile?
- domain controller
- TACACS+
- LDAP
- RADIUS
-
Which interface type is used to monitor traffic and cannot be used to perform traffic shaping?
- Layer 2
- Tap
- Layer 3
- Virtual Wire
-
Which administrator type provides more granular options to determine what the administrator can view and modify when creating an administrator account?
- Root
- Dynamic
- Role-based
- Superuser
-
Which administrator type utilizes predefined roles for a local administrator account?
- Superuser
- Role-based
- Dynamic
- Device administrator
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/8-0/pan-os-cli-quick-start/get-started-with-the-cli/give-administrators-access-to-the-cli/administrative-privileges?PageSpeed=noscript -
Which two security profile types can be attached to a security policy? (Choose two.)
- antivirus
- DDoS protection
- threat
- vulnerability
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/8-0/pan-os-admin/policy/security-profiles -
The CFO found a USB drive in the parking lot and decide to plug it into their corporate laptop. The USB drive had malware on it that loaded onto their computer and then contacted a known command and control (CnC) server, which ordered the infected machine to begin Exfiltrating data from the laptop.
Which security profile feature could have been used to prevent the communication with the CnC server?
- Create an anti-spyware profile and enable DNS Sinkhole
- Create an antivirus profile and enable DNS Sinkhole
- Create a URL filtering profile and block the DNS Sinkhole category
- Create a security policy and enable DNS Sinkhole
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/7-1/pan-os-web-interface-help/objects/objects-security-profiles-anti-spyware-profile -
Which user mapping method could be used to discover user IDs in an environment with multiple Windows domain controllers?
- Active Directory monitoring
- Windows session monitoring
- Windows client probing
- domain controller monitoring
-
Which three statements describe the operation of Security policy rules and Security Profiles? (Choose three.)
- Security policy rules are attached to Security Profiles.
- Security Profiles are attached to Security policy rules.
- Security Profiles should be used only on allowed traffic.
- Security policy rules inspect but do not block traffic.
- Security policy rules can block or allow traffic.
Subscribe
0 Comments
Newest