PCNSA : Palo Alto Networks Certified Network Security Administrator : Part 03
-
Given the image, which two options are true about the Security policy rules. (Choose two.)
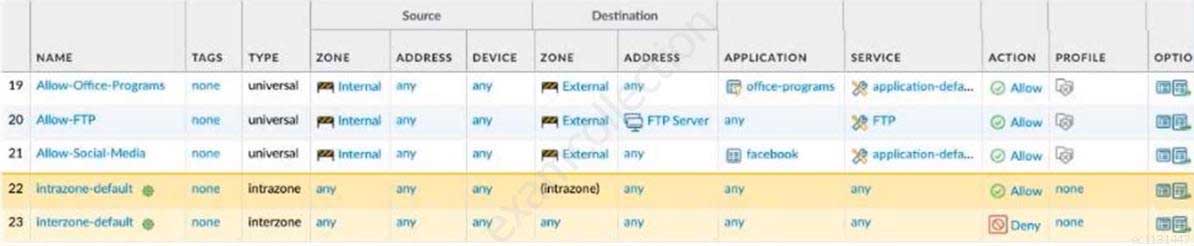
PCNSA Palo Alto Networks Certified Network Security Administrator Part 03 Q01 012 - The Allow Office Programs rule is using an Application Filter
- In the Allow FTP to web server rule, FTP is allowed using App-ID
- The Allow Office Programs rule is using an Application Group
- In the Allow Social Networking rule, allows all of Facebook’s functions
-
Which type of Security policy rule would match traffic flowing between the Inside zone and Outside zone, within the Inside zone, and within the Outside zone?
- global
- intrazone
- interzone
- universal
Explanation:
Reference:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClomCAC
-
Which Palo Alto Networks firewall security platform provides network security for mobile endpoints by inspecting traffic deployed as internet gateways?
- GlobalProtect
- AutoFocus
- Aperture
- Panorama
-
Which two statements are correct regarding multiple static default routes when they are configured as shown in the image? (Choose two.)
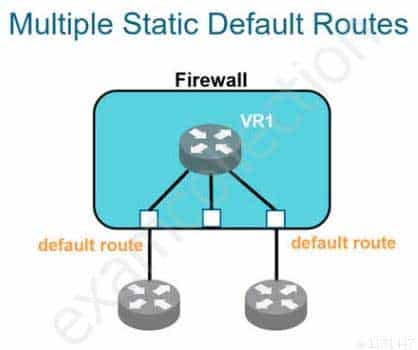
PCNSA Palo Alto Networks Certified Network Security Administrator Part 03 Q04 013 - Path monitoring does not determine if route is useable.
- Route with highest metric is actively used.
- Path monitoring determines if route is useable.
- Route with lowest metric is actively used.
-
Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can run malicious code against a targeted machine.
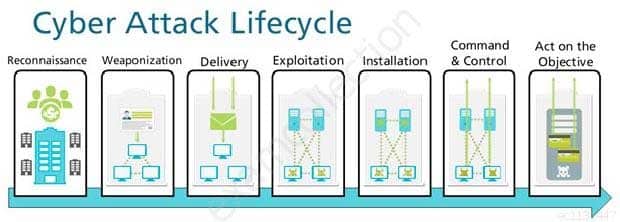
PCNSA Palo Alto Networks Certified Network Security Administrator Part 03 Q05 014 - Exploitation
- Installation
- Reconnaissance
- Act on Objective
-
Which file is used to save the running configuration with a Palo Alto Networks firewall?
- running-config.xml
- run-config.xml
- running-configuration.xml
- run-configuration.xml
-
In the example security policy shown, which two websites would be blocked? (Choose two.)
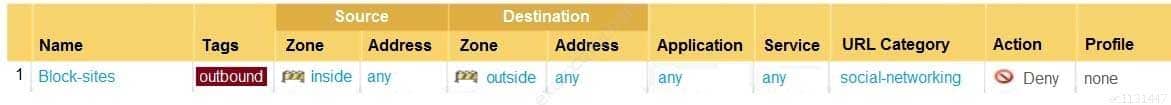
PCNSA Palo Alto Networks Certified Network Security Administrator Part 03 Q07 015 - YouTube
- Amazon
-
Which Palo Alto Networks component provides consolidated policy creation and centralized management?
- GlobalProtect
- Panorama
- Prisma SaaS
- AutoFocus
Explanation:Reference: https://www.paloaltonetworks.com/resources/datasheets/panorama-centralized-management-datasheet -
Which statement is true regarding a Prevention Posture Assessment?
- The Security Policy Adoption Heatmap component filters the information by device groups, serial numbers, zones, areas of architecture, and other categories
- It provides a set of questionnaires that help uncover security risk prevention gaps across all areas of network and security architecture
- It provides a percentage of adoption for each assessment area
- It performs over 200 security checks on Panorama/firewall for the assessment
Explanation:Reference: https://docs.paloaltonetworks.com/best-practices/8-1/data-center-best-practices/data-center-best-practice-security-policy/use-palo-alto-networks-assessment-and-review-tools -
Which five Zero Trust concepts does a Palo Alto Networks firewall apply to achieve an integrated approach to prevent threats? (Choose five.)
- User identification
- Filtration protection
- Vulnerability protection
- Antivirus
- Application identification
- Anti-spyware
-
The PowerBall Lottery has reached a high payout amount and a company has decided to help employee morale by allowing employees to check the number, but doesn’t want to unblock the gambling URL category.
Which two methods will allow the employees to get to the PowerBall Lottery site without the company unlocking the gambling URL category? (Choose two.)
- Add all the URLs from the gambling category except powerball.com to the block list and then set the action for the gambling category to allow.
- Manually remove powerball.com from the gambling URL category.
- Add *.powerball.com to the allow list
- Create a custom URL category called PowerBall and add *.powerball.com to the category and set the action to allow.
-
Which service protects cloud-based applications such as Dropbox and Salesforce by administering permissions and scanning files for sensitive information?
- Aperture
- AutoFocus
- Panorama
- GlobalProtect
-
An administrator receives a global notification for a new malware that infects hosts. The infection will result in the infected host attempting to contact and command-and-control (C2) server.
Which security profile components will detect and prevent this threat after the firewall’s signature database has been updated?
- antivirus profile applied to outbound security policies
- data filtering profile applied to inbound security policies
- data filtering profile applied to outbound security policies
- vulnerability profile applied to inbound security policies
-
Which update option is not available to administrators?
- New Spyware Notifications
- New URLs
- New Application Signatures
- New Malicious Domains
- New Antivirus Signatures
-
A server-admin in the USERS-zone requires SSH-access to all possible servers in all current and future Public Cloud environments. All other required connections have already been enabled between the USERS- and the OUTSIDE-zone. What configuration-changes should the Firewall-admin make?
- Create a custom-service-object called SERVICE-SSH for destination-port-TCP-22. Create a security-rule between zone USERS and OUTSIDE to allow traffic from any source IP-address to any destination IP-address for SERVICE-SSH
- Create a security-rule that allows traffic from zone USERS to OUTSIDE to allow traffic from any source IP-address to any destination IP-address for application SSH
- In addition to option a, a custom-service-object called SERVICE-SSH-RETURN that contains source-port-TCP-22 should be created. A second security-rule is required that allows traffic from zone OUTSIDE to USERS for SERVICE-SSH-RETURN for any source-IP-address to any destination-Ip-address
- In addition to option c, an additional rule from zone OUTSIDE to USERS for application SSH from any source-IP-address to any destination-IP-address is required to allow the return-traffic from the SSH-servers to reach the server-admin
-
How often does WildFire release dynamic updates?
- every 5 minutes
- every 15 minutes
- every 60 minutes
- every 30 minutes
Explanation:Reference: https://docs.paloaltonetworks.com/pan-os/7-1/pan-os-new-features/wildfire-features/five-minute-wildfire-updates -
What is the minimum frequency for which you can configure the firewall to check for new WildFire antivirus signatures?
- every 30 minutes
- every 5 minutes
- every 24 hours
- every 1 minute
Explanation:Reference: https://docs.paloaltonetworks.com/pan-os/7-1/pan-os-new-features/wildfire-features/five-minute-wildfire-updates -
Your company has 10 Active Directory domain controllers spread across multiple WAN links. All users authenticate to Active Directory. Each link has substantial network bandwidth to support all mission-critical applications. The firewall’s management plane is highly utilized.
Given the scenario, which type of User-ID agent is considered a best practice by Palo Alto Networks?
- Windows-based agent on a domain controller
- Captive Portal
- Citrix terminal server agent with adequate data-plane resources
- PAN-OS integrated agent
-
DRAG DROP
Arrange the correct order that the URL classifications are processed within the system.
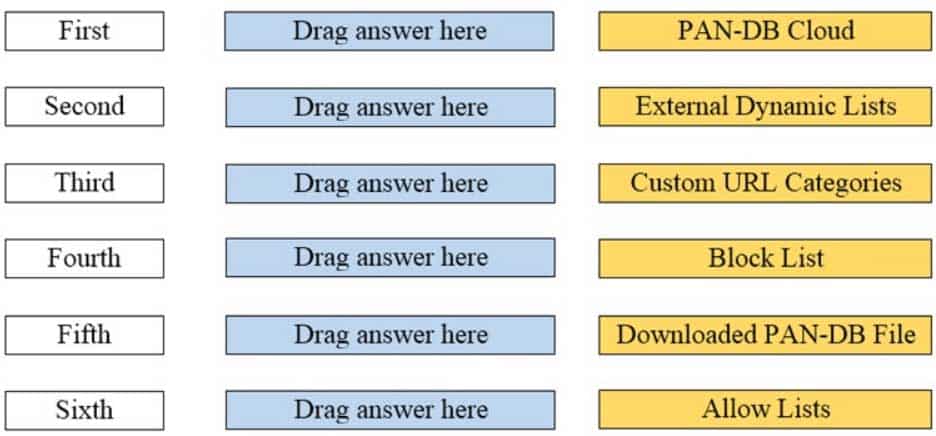
PCNSA Palo Alto Networks Certified Network Security Administrator Part 03 Q19 016 Question 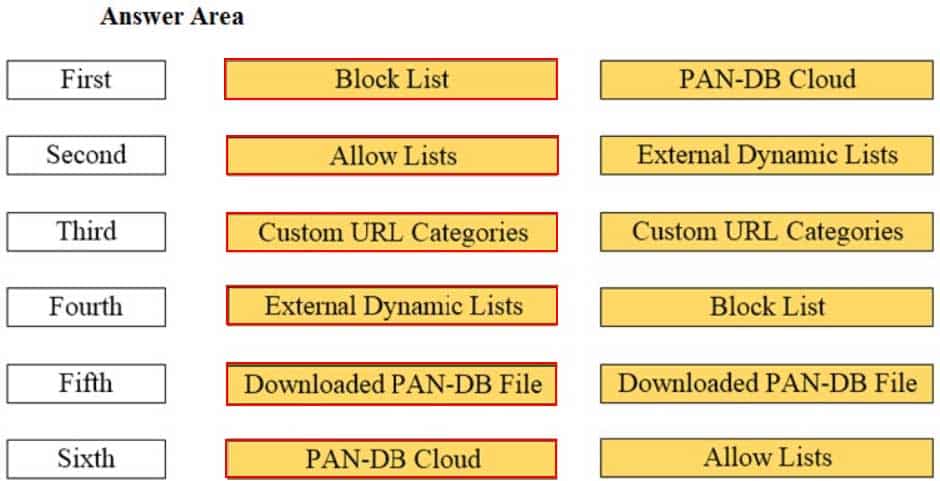
PCNSA Palo Alto Networks Certified Network Security Administrator Part 03 Q19 016 Answer -
What must you configure to enable the firewall to access multiple Authentication Profiles to authenticate a non-local account?
- authentication sequence
- LDAP server profile
- authentication server list
- authentication list profile
Explanation:Reference: https://docs.paloaltonetworks.com/content/dam/techdocs/en_US/pdf/framemaker/pan-os/7-1/pan-os-admin.pdf page 144
Subscribe
0 Comments
Newest