PCNSA : Palo Alto Networks Certified Network Security Administrator : Part 04
-
Which Security Profile mitigates attacks based on packet count?
- zone protection profile
- URL filtering profile
- antivirus profile
- vulnerability profile
-
Which interface type uses virtual routers and routing protocols?
- Tap
- Layer3
- Virtual Wire
- Layer2
-
Which URL Filtering Profile action does not generate a log entry when a user attempts to access a URL?
- Override
- Allow
- Block
- Continue
Explanation:
Reference: https://docs.paloaltonetworks.com/pan-os/8-0/pan-os-admin/url-filtering/url-filtering-concepts/url-filtering-profile-actions
-
An internal host needs to connect through the firewall using source NAT to servers of the internet.
Which policy is required to enable source NAT on the firewall?
- NAT policy with internal zone and internet zone specified
- post-NAT policy with external source and any destination address
- NAT policy with no internal or internet zone selected
- pre-NAT policy with external source and any destination address
-
Which Security Profile can provide protection against ICMP floods, based on individual combinations of a packet’s source and destination IP addresses?
- DoS protection
- URL filtering
- packet buffering
- anti-spyware
-
Which path in PAN-OS 9.0 displays the list of port-based security policy rules?
- Policies> Security> Rule Usage> No App Specified
- Policies> Security> Rule Usage> Port only specified
- Policies> Security> Rule Usage> Port-based Rules
- Policies> Security> Rule Usage> Unused Apps
-
Which two components are utilized within the Single-Pass Parallel Processing architecture on a Palo Alto Networks Firewall? (Choose two.)
- Layer-ID
- User-ID
- QoS-ID
- App-ID
Explanation:Reference: http://www.firewall.cx/networking-topics/firewalls/palo-alto-firewalls/1152-palo-alto-firewall-single-pass-parallel-processing-hardware-architecture.html -
Which path is used to save and load a configuration with a Palo Alto Networks firewall?
- Device>Setup>Services
- Device>Setup>Management
- Device>Setup>Operations
- Device>Setup>Interfaces
-
DRAG DROP
Match the network device with the correct User-ID technology.
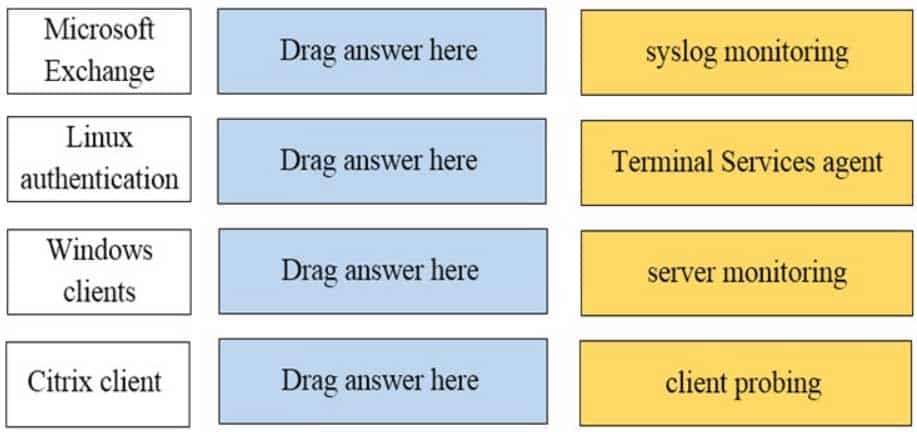
PCNSA Palo Alto Networks Certified Network Security Administrator Part 04 Q09 017 Question 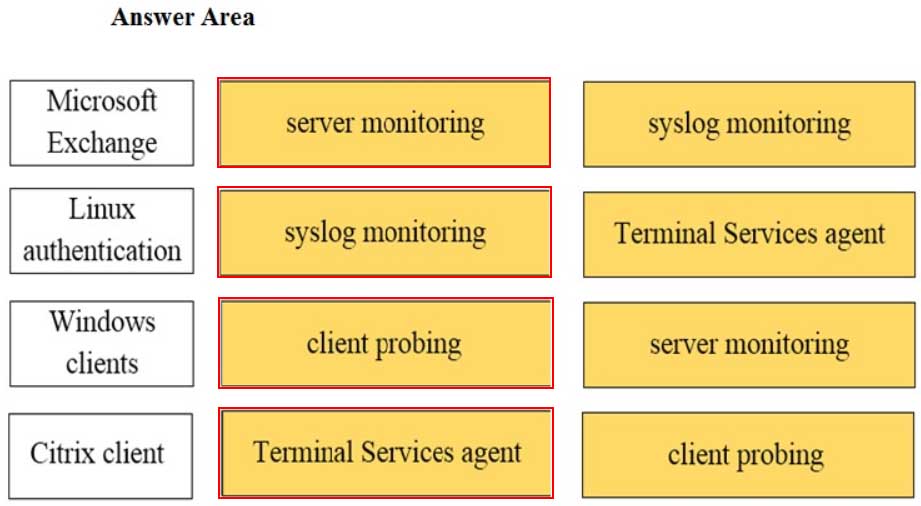
PCNSA Palo Alto Networks Certified Network Security Administrator Part 04 Q09 017 Answer -
Which action related to App-ID updates will enable a security administrator to view the existing security policy rule that matches new application signatures?
- Review Policies
- Review Apps
- Pre-analyze
- Review App Matches
Explanation:Reference: https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/app-id/manage-new-app-ids-introduced-in-content-releases/review-new-app-id-impact-on-existing-policy-rules -
How do you reset the hit count on a Security policy rule?
- Select a Security policy rule, and then select Hit Count > Reset.
- Reboot the data-plane.
- First disable and then re-enable the rule.
- Type the CLI command reset hitcount <POLICY-NAME>.
-
Given the topology, which zone type should you configure for firewall interface E1/1?
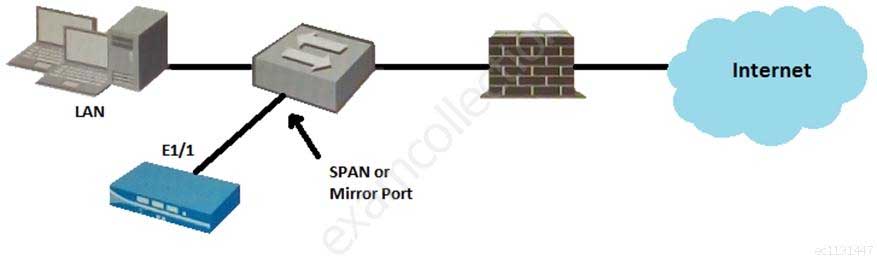
PCNSA Palo Alto Networks Certified Network Security Administrator Part 04 Q12 018 - Tap
- Tunnel
- Virtual Wire
- Layer3
-
Which interface type is part of a Layer 3 zone with a Palo Alto Networks firewall?
- Management
- High Availability
- Aggregate
- Aggregation
-
Which security policy rule would be needed to match traffic that passes between the Outside zone and Inside zone, but does not match traffic that passes within the zones?
- intrazone
- interzone
- universal
- global
-
Four configuration choices are listed, and each could be used to block access to a specific URL. If you configured each choice to block the same URL then which choice would be the last to block access to the URL?
- EDL in URL Filtering Profile
- Custom URL category in URL Filtering Profile
- Custom URL category in Security policy rule
- PAN-DB URL category in URL Filtering Profile
-
Which data flow direction is protected in a zero-trust firewall deployment that is not protected in a perimeter-only firewall deployment?
- north-south
- inbound
- outbound
- east-west
-
Which protocol is used to map usernames to user groups when User-ID is configured?
- TACACS+
- SAML
- LDAP
- RADIUS
Explanation:Reference: https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/user-id/map-users-to-groups.html -
Which definition describes the guiding principle of the zero-trust architecture?
- trust, but verify
- always connect and verify
- never trust, never connect
- never trust, always verify
Explanation:Reference: https://www.paloaltonetworks.com/cyberpedia/what-is-a-zero-trust-architecture -
All users from the internal zone must be allowed only Telnet access to a server in the DMZ zone.
Complete the two empty fields in the Security policy rules that permits only this type of access.
Source Zone: Internal
Destination Zone: DMZ Zone
Application: _________?
Service: ____________?
Action: allow(Choose two.)
- Service = “application-default”
- Service = “service-telnet”
- Application = “Telnet”
- Application = “any”
-
In which profile should you configure the DNS Security feature?
- Anti-Spyware Profile
- Zone Protection Profile
- Antivirus Profile
- URL Filtering Profile
Explanation:Reference: https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/threat-prevention/dns-security/enable-dns-security.html
Subscribe
0 Comments
Newest