PCNSA : Palo Alto Networks Certified Network Security Administrator : Part 05
-
Which two statements are true for the DNS Security service introduced in PAN-OS version 9.0? (Choose two.)
- It is automatically enabled and configured.
- It eliminates the need for dynamic DNS updates.
- It functions like PAN-DB and requires activation through the app portal.
- It removes the 100K limit for DNS entries for the downloaded DNS updates.
-
Which two features can be used to tag a username so that it is included in a dynamic user group? (Choose two.)
- GlobalProtect agent
- XML API
- User-ID Windows-based agent
- log forwarding auto-tagging
-
The CFO found a malware infected USB drive in the parking lot, which when inserted infected their corporate laptop. The malware contacted a known command-and-control server, which caused the infected laptop to begin exfiltrating corporate data.
Which security profile feature could have been used to prevent the communication with the command-and-control server?
- Create an anti-spyware profile and enable DNS Sinkhole feature.
- Create an antivirus profile and enable its DNS Sinkhole feature.
- Create a URL filtering profile and block the DNS Sinkhole URL category
- Create a Data Filtering Profiles and enable its DNS Sinkhole feature.
-
You must configure which firewall feature to enable a data-plane interface to submit DNS queries on behalf of the control plane?
- virtual router
- Admin Role profile
- DNS proxy
- service route
Explanation:
Reference: https://weberblog.net/palo-alto-dns-proxy-for-management-services/
-
Which component provides network security for mobile endpoints by inspecting traffic routed through gateways?
- Prisma SaaS
- GlobalProtect
- AutoFocus
- Panorama
Explanation:Reference: https://www.paloaltonetworks.com/resources/whitepapers/protecting-the-extended-perimeter-with-globalprotect-cloud-service-full -
For the firewall to use Active Directory to authenticate users, which Server Profile is required in the Authentication Profile?
- TACACS+
- RADIUS
- LDAP
- SAML
Explanation:Reference: https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/authentication/configure-an-authentication-profile-and-sequence -
Which operations are allowed when working with App-ID application tags?
- Predefined tags may be deleted.
- Predefined tags may be augmented by custom tags.
- Predefined tags may be modified.
- Predefined tags may be updated by WildFire dynamic updates.
-
Your company occupies one floor in a single building. You have two Active Directory domain controllers on a single network. The firewall’s management plane is only slightly utilized.
Which User-ID agent is sufficient in your network?
- Windows-based agent deployed on each domain controller
- PAN-OS integrated agent deployed on the firewall
- Citrix terminal server agent deployed on the network
- Windows-based agent deployed on the internal network a domain member
Explanation:Reference: https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/user-id/map-ip-addresses-to-users/configure-user-mapping-using-the-windows-user-id-agent/configure-the-windows-based-user-id-agent-for-user-mapping.html -
Which type of administrative role must you assign to a firewall administrator account, if the account must include a custom set of firewall permissions?
- Role-based
- Multi-Factor Authentication
- Dynamic
- SAML
Explanation:Reference: https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/firewall-administration/manage-firewall-administrators/administrative-role-types.html -
Which statement is true regarding a Heatmap report?
- When guided by authorized sales engineer, it helps determine the areas of greatest security risk
- It runs only on firewalls.
- It provides a set of questionnaires that help uncover security risk prevention gaps across all areas of network and security architecture.
- It provides a percentage of adoption for each assessment area.
Explanation:Reference: https://live.paloaltonetworks.com/t5/best-practice-assessment-blogs/the-best-practice-assessment-bpa-tool-for-ngfw-and-panorama/ba-p/248343 -
Based on the screenshot presented, which column contains the link that when clicked, opens a window to display all applications matched to the policy rule?
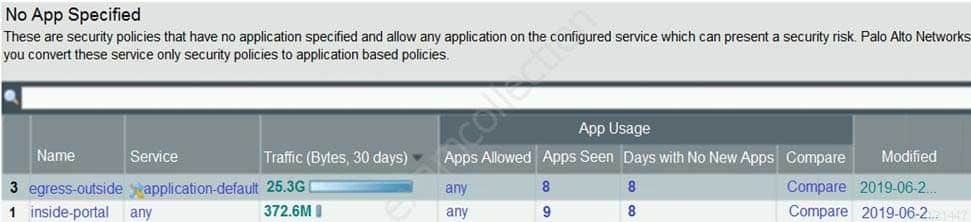
PCNSA Palo Alto Networks Certified Network Security Administrator Part 05 Q11 019 - Apps Allowed
- Service
- Name
- Apps Seen
-
Access to which feature requires the PAN-OS Filtering license?
- PAN-DB database
- DNS Security
- Custom URL categories
- URL external dynamic lists
Explanation:Reference: https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/getting-started/activate-licenses-and-subscriptions.html -
Based on the screenshot, what is the purpose of the Included Groups?
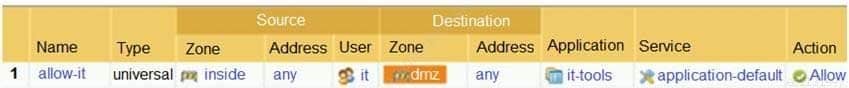
PCNSA Palo Alto Networks Certified Network Security Administrator Part 05 Q13 020 - They are groups that are imported from RADIUS authentication servers.
- They are the only groups visible based on the firewall’s credentials.
- They contain only the users you allow to manage the firewall.
- They are used to map users to groups.
Explanation:Reference: https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/user-id/map-users-to-groups.html -
Based on the graphic, which statement accurately describes the output shown in the Server Monitoring panel?
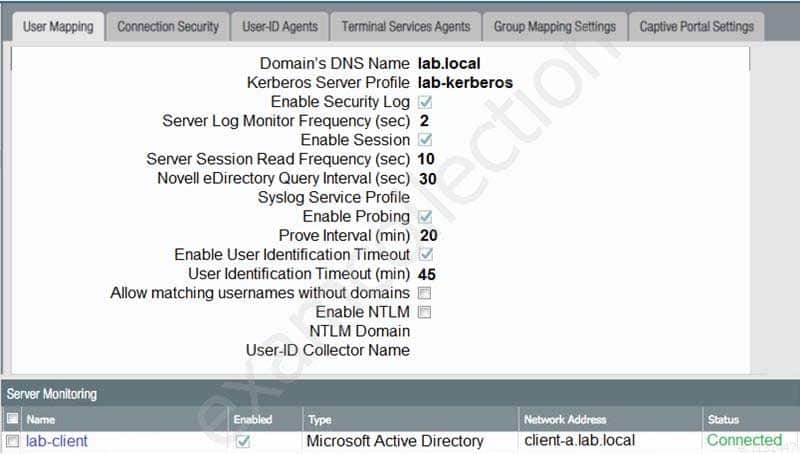
PCNSA Palo Alto Networks Certified Network Security Administrator Part 05 Q14 021 - The User-ID agent is connected to a domain controller labeled lab-client.
- The host lab-client has been found by the User-ID agent.
- The host lab-client has been found by a domain controller.
- The User-ID agent is connected to the firewall labeled lab-client.
-
Which action results in the firewall blocking network traffic without notifying the sender?
- Drop
- Deny
- Reset Server
- Reset Client
-
What do Dynamic User Groups help you to do?
- create a policy that provides auto-remediation for anomalous user behavior and malicious activity
- create a dynamic list of firewall administrators
- create a QoS policy that provides auto-remediation for anomalous user behavior and malicious activity
- create a policy that provides auto-sizing for anomalous user behavior and malicious activity
Explanation:Reference: https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-new-features/user-id-features/dynamic-user-groups -
Which type of security policy rule will match traffic that flows between the Outside zone and inside zone, but would not match traffic that flows within the zones?
- global
- intrazone
- interzone
- universal
-
You notice that protection is needed for traffic within the network due to malicious lateral movement activity. Based on the image shown, which traffic would you need to monitor and block to mitigate the malicious activity?
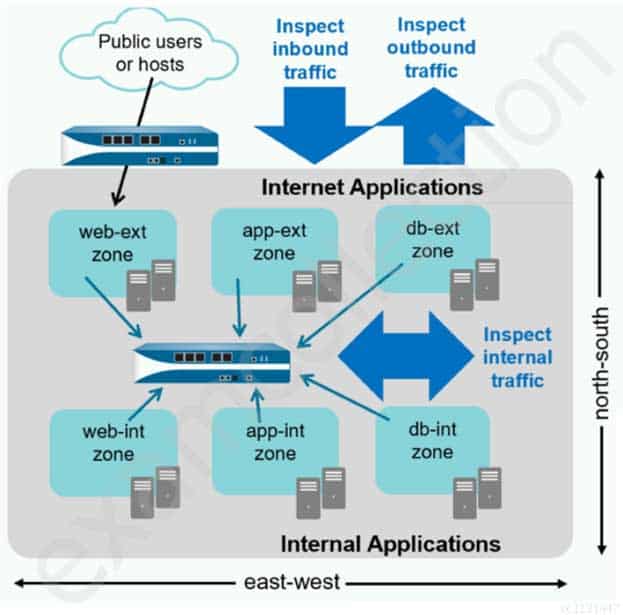
PCNSA Palo Alto Networks Certified Network Security Administrator Part 05 Q18 022 - branch office traffic
- north-south traffic
- perimeter traffic
- east-west traffic
-
DRAG DROP
Match each feature to the DoS Protection Policy or the DoS Protection Profile.
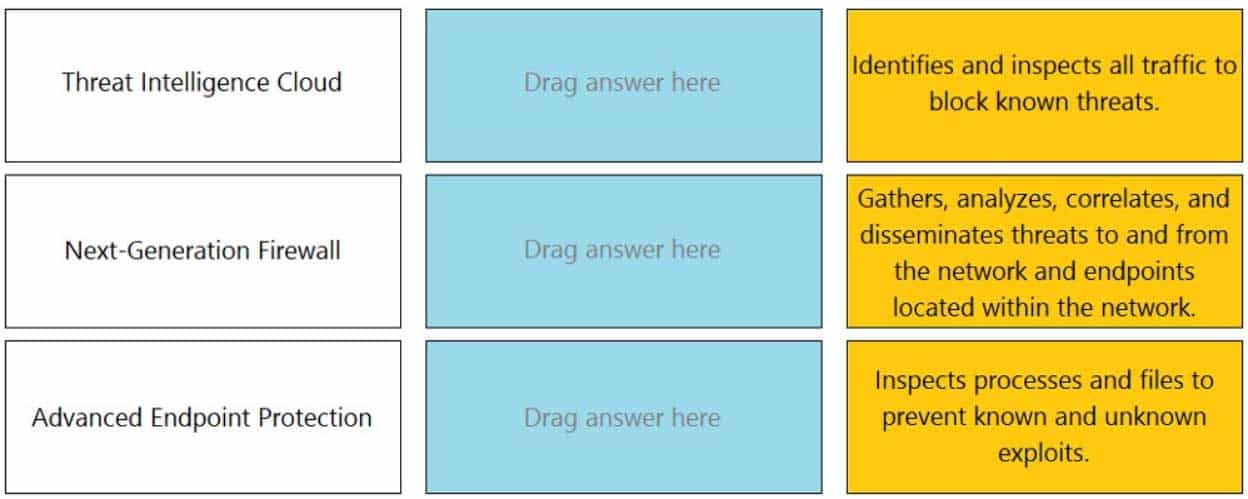
PCNSA Palo Alto Networks Certified Network Security Administrator Part 05 Q19 023 Question 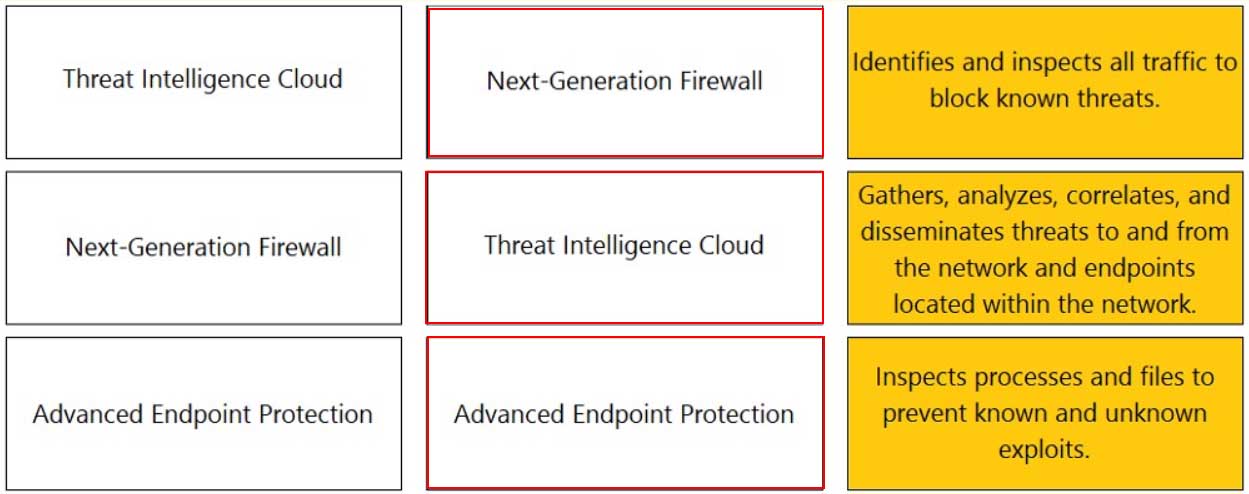
PCNSA Palo Alto Networks Certified Network Security Administrator Part 05 Q19 023 Answer -
Which type of administrator account cannot be used to authenticate user traffic flowing through the firewall’s data plane?
- Kerberos user
- SAML user
- local database user
- local user
Subscribe
0 Comments
Newest