PCNSA : Palo Alto Networks Certified Network Security Administrator : Part 06
-
How frequently can WildFire updates be made available to firewalls?
- every 15 minutes
- every 30 minutes
- every 60 minutes
- every 5 minutes
Explanation:
Reference: https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/software-and-content-updates/dynamic-content-updates.html#:~:text=WildFire%20signature%20updates%20are%20made,within%20a%20minute%20of%20availability.
-
Starting with PAN-OS version 9.1, which new type of object is supported for use within the User field of a Security policy rule?
- remote username
- dynamic user group
- static user group
- local username
-
Which link in the web interface enables a security administrator to view the Security policy rules that match new application signatures?
- Review App Matches
- Review Apps
- Pre-analyze
- Review Policies
-
Based on the shown security policy, which Security policy rule would match all FTP traffic from the inside zone to the outside zone?
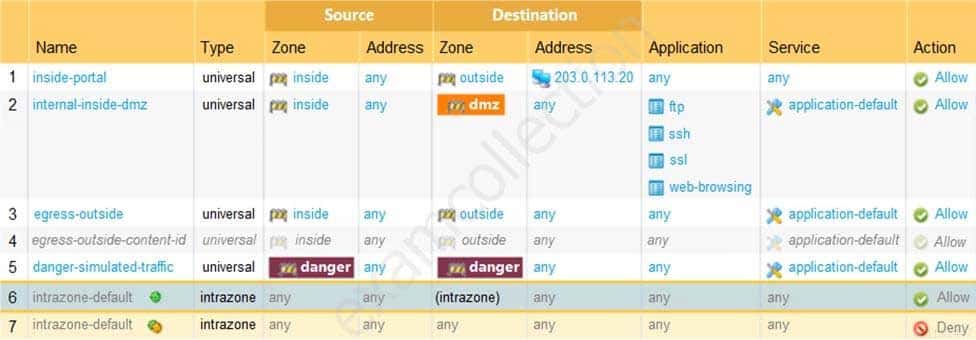
PCNSA Palo Alto Networks Certified Network Security Administrator Part 06 Q04 024 - interzone-default
- internal-inside-dmz
- inside-portal
- egress-outside
-
Which type of firewall configuration contains in-progress configuration changes?
- backup
- candidate
- running
- committed
-
Which three configuration settings are required on a Palo Alto Network firewall management interface? (Choose three.)
- hostname
- netmask
- default gateway
- auto-negotiation
- IP address
Explanation:Reference: https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClN7CAK -
What is an advantage for using application tags?
- They are helpful during the creation of new zones.
- They help content updates automate policy updates.
- They help with the creation of interfaces.
- They help with the design of IP address allocations in DHCP.
-
At which point in the App-ID update process can you determine if an existing policy rule is affected by an App-ID update?
- after clicking Check Now in the Dynamic Update window
- after committing the firewall configuration
- after installing the update
- after downloading the update
Explanation:Reference: https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-web-interface-help/device/device-dynamic-updates -
You receive notification about a new malware that infects hosts. An infection results in the infected host attempting to contact a command-and-control server.
Which Security Profile detects and prevents this threat from establishing a command-and-control connection?
- Vulnerability Protection Profile applied to outbound Security policy rules.
- Anti-Spyware Profile applied to outbound security policies.
- Antivirus Profile applied to outbound Security policy rules
- Data Filtering Profile applied to outbound Security policy rules.
-
Which statement is true regarding a Best Practice Assessment?
- It runs only on firewalls.
- It shows how current configuration compares to Palo Alto Networks recommendations.
- When guided by an authorized sales engineer, it helps determine the areas of greatest risk where you should focus prevention activities.
- It provides a set of questionnaires that help uncover security risk prevention gaps across all areas of network and security architecture.
-
The PowerBall Lottery has reached an unusually high value this week. Your company has decided to raise morale by allowing employees to access the PowerBall Lottery website (www.powerball.com) for just this week. However, the company does not want employees to access any other websites also listed in the URL filtering “gambling” category.
Which method allows the employees to access the PowerBall Lottery website but without unblocking access to the “gambling” URL category?
- Add just the URL www.powerball.com to a Security policy allow rule.
- Manually remove powerball.com from the gambling URL category.
- Add *.powerball.com to the URL Filtering allow list.
- Create a custom URL category, add *.powerball.com to it and allow it in the Security Profile.
-
Which Palo Alto Networks service protects cloud-based applications such as Dropbox and Salesforce by monitoring permissions and shares and scanning files for sensitive information?
- Prisma SaaS
- AutoFocus
- Panorama
- GlobalProtect
-
In a Security policy, what is the quickest way to reset all policy rule hit counters to zero?
- Highlight each rule and use the Reset Rule Hit Counter > Selected Rules
- Reboot the firewall
- Use the Reset Rule Hit Counter > All Rules option
- Use the CLI enter the command reset rules all
Explanation:Reference: https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-web-interface-help/policies/policies-security/creating-and-managing-policies -
Based on the Security policy rules shown, SSH will be allowed on which port?
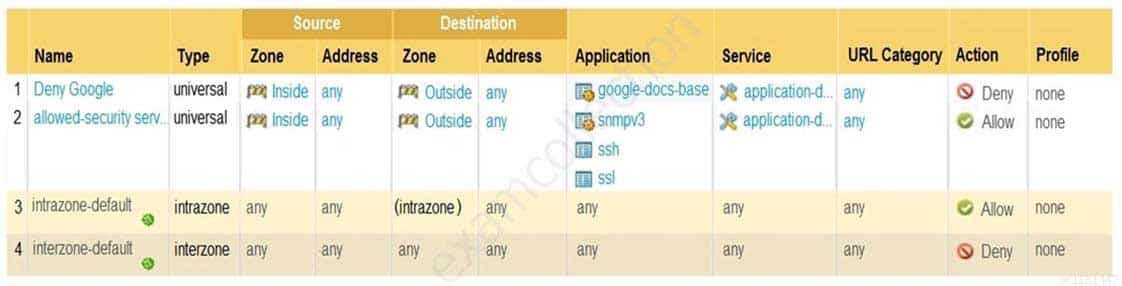
PCNSA Palo Alto Networks Certified Network Security Administrator Part 06 Q14 025 - the default port
- only ephemeral ports
- any port
- same port as ssl and snmpv3
-
You receive notification about new malware that is being used to attack hosts. The malware exploits a software bug in common application.
Which Security Profile detects and blocks access to this threat after you update the firewall’s threat signature database?
- Data Filtering Profile applied to outbound Security policy rules
- Antivirus Profile applied to outbound Security policy rules
- Data Filtering Profile applied to inbound Security policy rules
- Vulnerability Protection Profile applied to inbound Security policy rules
-
Palo Alto Networks firewall architecture accelerates content inspection performance while minimizing latency using which two components? (Choose two.)
- Network Processing Engine
- Policy Engine
- Parallel Processing Hardware
- Single Stream-based Engine
-
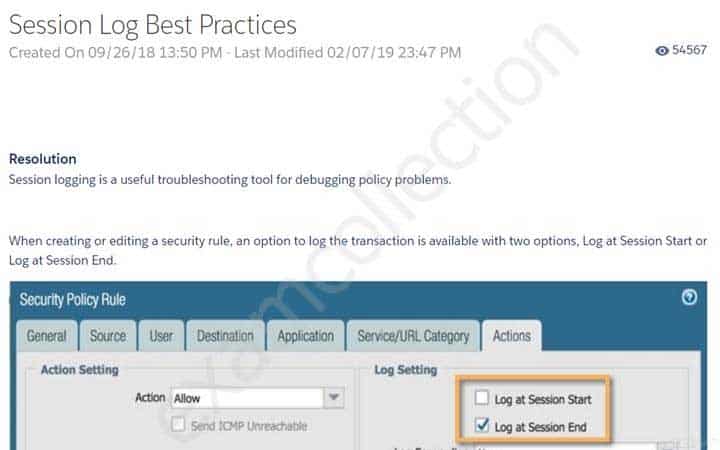
An administrator is reviewing another administrator’s Security policy log settings.
Which log setting configuration is consistent with best practices for normal traffic?
- Log at Session Start and Log at Session End both enabled
- Log at Session Start enabled, Log at Session End disabled
- Log at Session Start disabled, Log at Session End enabled
- Log at Session Start and Log at Session End both disabled
-
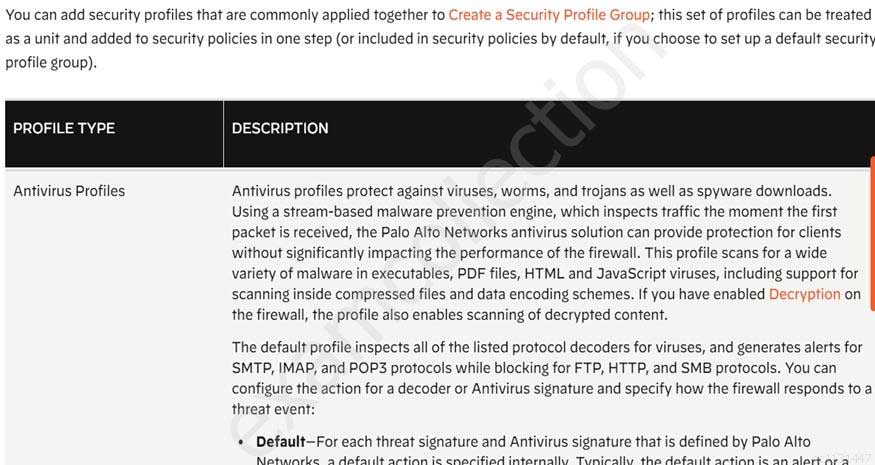
Which Security profile would you apply to identify infected hosts on the protected network using DNS traffic?
- URL traffic
- vulnerability protection
- anti-spyware
- antivirus
-
Given the topology, which zone type should zone A and zone B to be configured with?
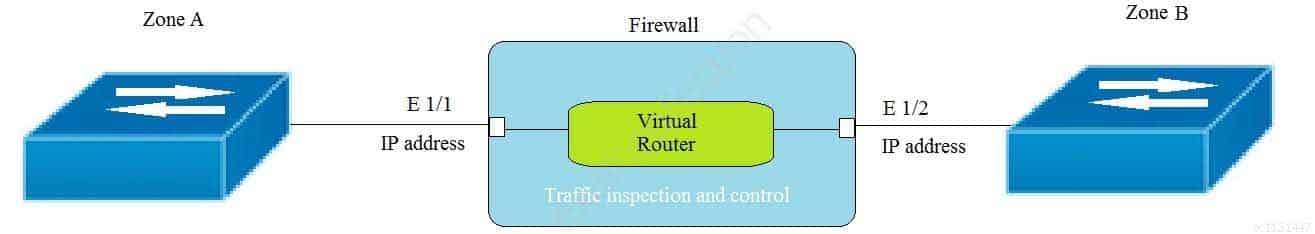
PCNSA Palo Alto Networks Certified Network Security Administrator Part 06 Q19 028 - Layer3
- Ethernet
- Layer2
- Virtual Wire
-
Assume a custom URL Category Object of “NO-FILES” has been created to identify a specific website?
How can file uploading/downloading be restricted for the website while permitting general browsing access to that website?
- Create a Security policy with a URL Filtering profile that references the site access setting of block to NO-FILES.
- Create a Security policy that references NO-FILES as a URL Category qualifier with an appropriate File Blocking profile.
- Create a Security policy with a URL Filtering profile that references the site access setting of continue to NO-FILES.
- Create a Security policy that references NO-FILES as a URL Category qualifier with an appropriate Data Filtering profile.
Explanation:Reference: https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/threat-prevention/set-up-file-blocking
Subscribe
0 Comments
Newest