PCNSA : Palo Alto Networks Certified Network Security Administrator : Part 07
-
Which URL Filtering profile action would you set to allow users the option to access a site only if they provide a URL admin password?
- authorization
- continue
- authentication
- override
-
How are Application Filters or Application Groups used in firewall policy?
- An Application Group is a static way of grouping applications and cannot be configured as a nested member of Application Group.
- An Application Group is a dynamic way of grouping applications and can be configured as a nested member of an Application Group.
- An Application Filter is a dynamic way to group applications and can be configured as a nested member of an Application Group.
- An Application Filter is a static way of grouping applications and can be configured as a nested member of an Application Group.
-
Which tab would an administrator click to create an address object?
- Objects
- Monitor
- Device
- Policies
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-web-interface-help/objects/objects-addresses -
An administrator wishes to follow best practices for logging traffic that traverses the firewall.
Which log setting is correct?
- Enable Log at Session Start
- Disable all logging
- Enable Log at both Session Start and End
- Enable Log at Session End
Explanation:Reference:https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000Clt5CAC -
Which two firewall components enable you to configure SYN flood protection thresholds? (Choose two.)
- QoS profile
- DoS Protection profile
- Zone Protection profile
- DoS Protection policy
-
An administrator would like to see the traffic that matches the interzone-default rule in the traffic logs.
What is the correct process to enable this logging?
- Select the interzone-default rule and click Override; on the Actions tab, select Log at Session End and click OK.
- Select the interzone-default rule and edit the rule; on the Actions tab, select Log at Session End and click OK.
- Select the interzone-default rule and edit the rule; on the Actions tab, select Log at Session Start and click OK.
- This rule has traffic logging enabled by default; no further action is required.
-
The Palo Alto Networks NGFW was configured with a single virtual router named VR-1.
What changes are required on VR-1 to route traffic between two interfaces on the NGFW?
- Add static routes to route between the two interfaces
- Add interfaces to the virtual router
- Add zones attached to interfaces to the virtual router
- Enable the redistribution profile to redistribute connected routes
-
An administrator wants to prevent users from submitting corporate credentials in a phishing attack.
Which Security profile should be applied?
- antivirus
- anti-spyware
- URL-filtering
- vulnerability protection
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/threat-prevention/prevent-credential-phishing/set-up-credential-phishing-prevention.html#idc77030dc-6022-4458-8c50-1dc0fe7cffe4 -
Which two rule types allow the administrator to modify the destination zone? (Choose two.)
- interzone
- shadowed
- intrazone
- universal
-
What is the main function of Policy Optimizer?
- reduce load on the management plane by highlighting combinable security rules
- migrate other firewall vendors’ security rules to Palo Alto Networks configuration
- eliminate “Log at Session Start” security rules
- convert port-based security rules to application-based security rules
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-new-features/app-id-features/policy-optimizer.html -
Based on the screenshot, what is the purpose of the group in User labelled “it”?
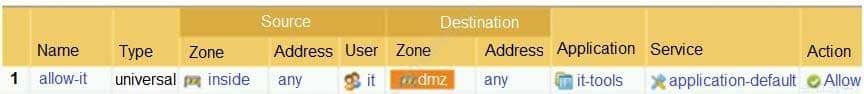
PCNSA Palo Alto Networks Certified Network Security Administrator Part 07 Q11 031 - Allows “any” users to access servers in the DMZ zone.
- Allows users to access IT applications on all ports.
- Allow users in group “it” to access IT applications.
- Allow users in group “DMZ” to access IT applications.
-
Which action results in the firewall blocking network traffic without notifying the sender?
- Drop
- Deny
- No notification
- Reset Client
-
Assume that traffic matches a Security policy rule but the attached Security Profiles is configured to block matching traffic.
Which statement accurately describes how the firewall will apply an action to matching traffic?
- If it is a block rule, then Security Profile action is applied last.
- If it is an allow rule, then the Security policy rule is applied last.
- If it is a block rule, then the Security policy rule action is applied last.
- If it is an allowed rule, then the Security Profile action is applied last.
-
Which Security profile can you apply to protect against malware such as worms and Trojans?
- antivirus
- data filtering
- vulnerability protection
- anti-spyware
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/policy/security-profiles#:~:text=Antivirus%20profiles%20protect%20against%20viruses,as%20well%20as%20spyware%20downloads. -
Given the network diagram, traffic should be permitted for both Trusted and Guest users to access general Internet and DMZ servers using SSH, web-browsing and SSL applications.
Which policy achieves the desired results?
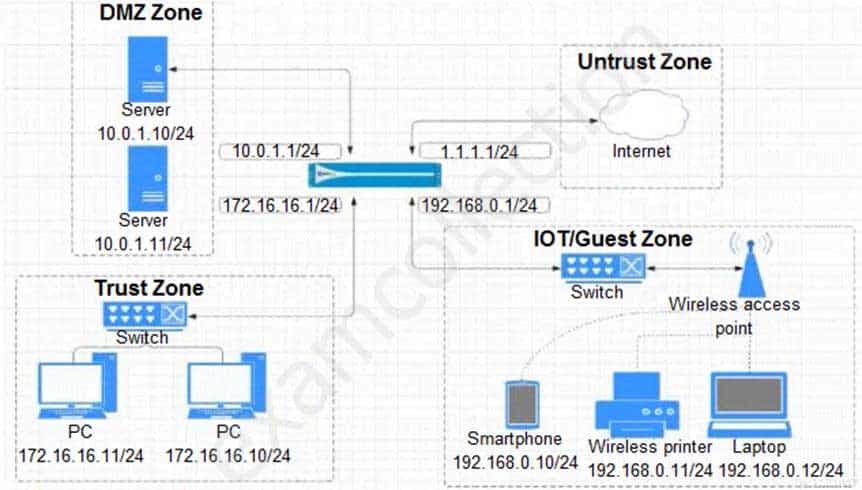
PCNSA Palo Alto Networks Certified Network Security Administrator Part 07 Q15 032 -
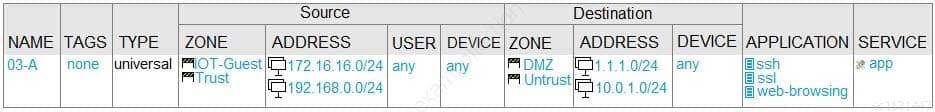
PCNSA Palo Alto Networks Certified Network Security Administrator Part 07 Q15 033 -
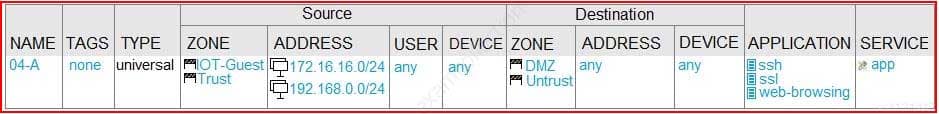
PCNSA Palo Alto Networks Certified Network Security Administrator Part 07 Q15 034 -
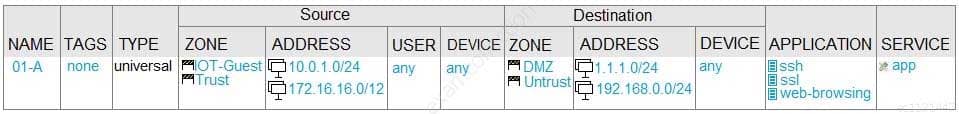
PCNSA Palo Alto Networks Certified Network Security Administrator Part 07 Q15 035 -
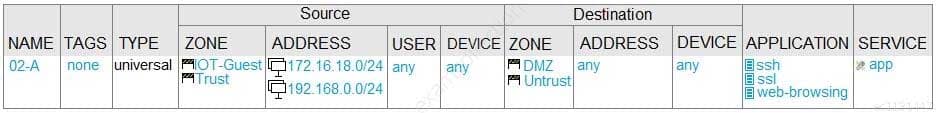
PCNSA Palo Alto Networks Certified Network Security Administrator Part 07 Q15 036
-
-
Which license is required to use the Palo Alto Networks built-in IP address EDLs?
- DNS Security
- Threat Prevention
- WildFire
- SD-Wan
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/policy/use-an-external-dynamic-list-in-policy/built-in-edls.html#:~:text=With%20an%20active%20Threat%20Prevention,to%20protect%20against%20malicious%20hosts -
Which statement is true about Panorama managed devices?
- Panorama automatically removes local configuration locks after a commit from Panorama.
- Local configuration locks prohibit Security policy changes for a Panorama managed device.
- Security policy rules configured on local firewalls always take precedence.
- Local configuration locks can be manually unlocked from Panorama.
Explanation:Reference: -
A Security Profile can block or allow traffic at which point?
- on either the data plane or the management plane
- after it is matched to a Security policy rule that allows or blocks traffic
- after it is matched to a Security policy rule that allows traffic
- before it is matched to a Security policy rule
-
DRAG DROP
Place the following steps in the packet processing order of operations from first to last.
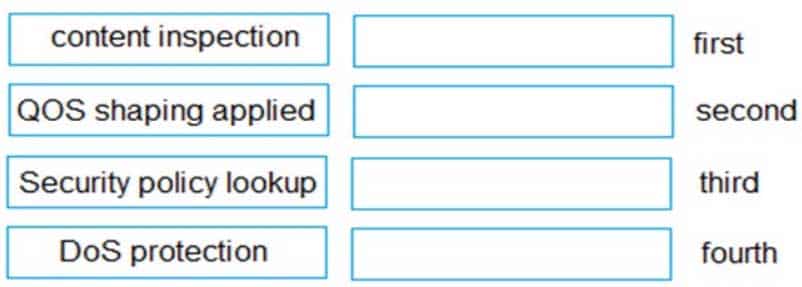
PCNSA Palo Alto Networks Certified Network Security Administrator Part 07 Q19 038 Question 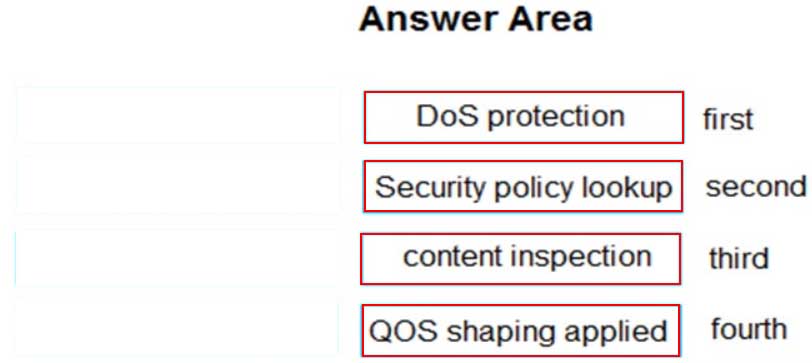
PCNSA Palo Alto Networks Certified Network Security Administrator Part 07 Q19 038 Answer Explanation:Reference:https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClVHCA0 -
Which type of address object is “10.5.1.1/0.127.248.2”?
- IP netmask
- IP subnet
- IP wildcard mask
- IP range
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/10-0/pan-os-admin/policy/use-address-object-to-represent-ip-addresses/create-an-address-object.html
Subscribe
0 Comments
Newest