PCNSA : Palo Alto Networks Certified Network Security Administrator : Part 08
-
Which component is a building block in a Security policy rule?
- decryption profile
- destination interface
- timeout (min)
- application
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-web-interface-help/policies/policies-security/building-blocks-in-a-security-policy-rule.html -
You have been tasked to configure access to a new web server located in the DMZ.
Based on the diagram what configuration changes are required in the NGFW virtual router to route traffic from the 10.1.1.0/24 network to 192.168.1.0/24?
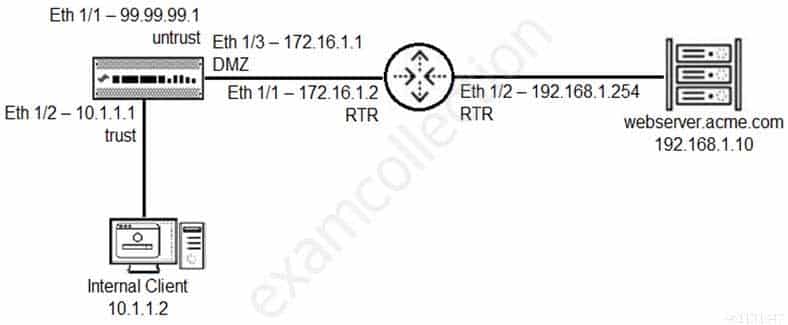
PCNSA Palo Alto Networks Certified Network Security Administrator Part 08 Q02 039 - Add a route with the destination of 192.168.1.0/24 using interface Eth 1/2 with a next-hop of 172.16.1.2.
- Add a route with the destination of 192.168.1.0/24 using interface Eth 1/3 with a next-hop of 192.168.1.10
- Add a route with the destination of 192.168.1.0/24 using interface Eth 1/3 with a next-hop of 172.16.1.2.
- Add a route with the destination of 192.168.1.0/24 using interface Eth 1/3 with a next-hop of 192.168.1.254.
-
An administrator would like to use App-ID’s deny action for an application and would like that action updated with dynamic updates as new content becomes available.
Which security policy action causes this?
- Reset server
- Reset both
- Deny
- Drop
-
Selecting the option to revert firewall changes will replace what settings?
- the candidate configuration with settings from the running configuration
- dynamic update scheduler settings
- the running configuration with settings from the candidate configuration
- the device state with settings from another configuration
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/firewall-administration/manage-configuration-backups/revert-firewall-configuration-changes.html -
An administrator has configured a Security policy where the matching condition includes a single application, and the action is deny.
If the application’s default deny action is reset-both, what action does the firewall take?
- It silently drops the traffic.
- It silently drops the traffic and sends an ICMP unreachable code.
- It sends a TCP reset to the server-side device.
- It sends a TCP reset to the client-side and server-side devices.
-
Which three types of authentication services can be used to authenticate user traffic flowing through the firewall’s data plane? (Choose three.)
- SAML 2.0
- Kerberos
- TACACS
- TACACS+
- SAML 1.0
-
Which objects would be useful for combining several services that are often defined together?
- application filters
- service groups
- shared service objects
- application groups
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-web-interface-help/objects/objects-services.html -
Given the screenshot, what two types of route is the administrator configuring? (Choose two.)
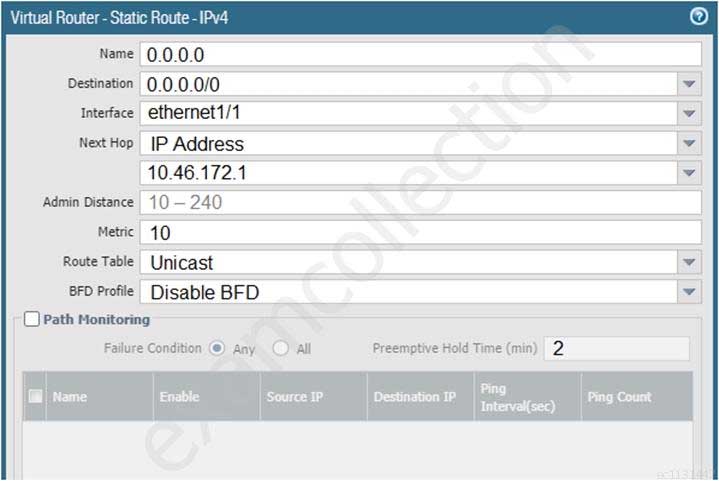
PCNSA Palo Alto Networks Certified Network Security Administrator Part 08 Q08 040 - BGP
- static route
- default route
- OSPF
-
Which rule type is appropriate for matching traffic both within and between the source and destination zones?
- interzone
- shadowed
- intrazone
- universal
-
An administrator would like to override the default deny action for a given application, and instead would like to block the traffic and send the ICMP code “communication with the destination is administratively prohibited”.
Which security policy action causes this?
- Drop
- Drop, send ICMP Unreachable
- Reset both
- Reset server
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/policy/security-policy/security-policy-actions.html -
You receive notification about new malware that infects hosts through malicious files transferred by FTP.
Which Security profile detects and protects your internal networks from this threat after you update your firewall’s threat signature database?
- URL Filtering profile applied to inbound Security policy rules.
- Data Filtering profile applied to outbound Security policy rules.
- Antivirus profile applied to inbound Security policy rules.
- Vulnerability Protection profile applied to outbound Security policy rules.
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/policy/security-profiles -
An administrator wants to prevent access to media content websites that are risky.
Which two URL categories should be combined in a custom URL category to accomplish this goal? (Choose two.)
- recreation-and-hobbies
- streaming-media
- known-risk
- high-risk
-
Which dynamic update type includes updated anti-spyware signatures?
- PAN-DB
- Applications and Threats
- GlobalProtect Data File
- Antivirus
-
An administrator would like to silently drop traffic from the internet to a ftp server.
Which Security policy action should the administrator select?
- Drop
- Deny
- Block
- Reset-server
-
Which object would an administrator create to block access to all high-risk applications?
- HIP profile
- Vulnerability Protection profile
- application group
- application filter
Explanation:Reference:https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClKECA0 -
Which option is part of the content inspection process?
- Packet forwarding process
- IPsec tunnel encryption
- SSL Proxy re-encrypt
- Packet egress process
Explanation:Reference:http://live.paloaltonetworks.com//t5/image/serverpage/image-id/12862i950F549C7D4E6309 -
How does an administrator schedule an Applications and Threats dynamic update while delaying installation of the update for a certain amount of time?
- Disable automatic updates during weekdays
- Automatically “download and install” but with the “disable new applications” option used
- Automatically “download only” and then install Applications and Threats later, after the administrator approves the update
- Configure the option for “Threshold”
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/7-1/pan-os-admin/threat-prevention/best-practices-for-application-and-threat-content-updates#
Subscribe
0 Comments
Newest